Security in WebLogic Platform 8.1
Using an External Store for User Information
As an administrator, one of your basic tasks is to create and manage information about the users of your deployment. This chapter gives an overview of the following topics:
- Basic concepts about the WebLogic Security Service related to user information that is useful to understand
- Tasks you need to perform to create and manage user information, and to customize how it is stored and used
- Back up and restore user information, on either the same or a different configuration
- Work with user information that is stored in an external LDAP server
The following topics are included:
Note: User information is defined to encompass users, groups, roles, and security policies. However, this chapter focuses specifically on users, groups, and roles. For information about security policies, see Security Policies in Securing WebLogic Resources.
Where User Information Is Stored
User information consists of the following:
- User names and passwords
- Groups
- Security roles
- Security policies
By default, whenever you create a domain, user information (with one exception) is stored in the embedded WebLogic LDAP server.
Note: The exception is user profiles. For details, see Managing User Profile Information.
User information stored in the embedded LDAP server is always available to every component of WebLogic Platform; it can also be managed, modified, and deleted by any component, regardless of which administration console was used for the initial creation of the user information.
After you modify user information in the administration console for one component, you can display the modified information in the administration console for another component, as long as display of the latter administration console has been refreshed.
Figure 3-1 shows the embedded LDAP server that is shared by all component administration consoles.
Figure 3-1 Embedded LDAP Server Stores WebLogic Platform Security Information Centrally
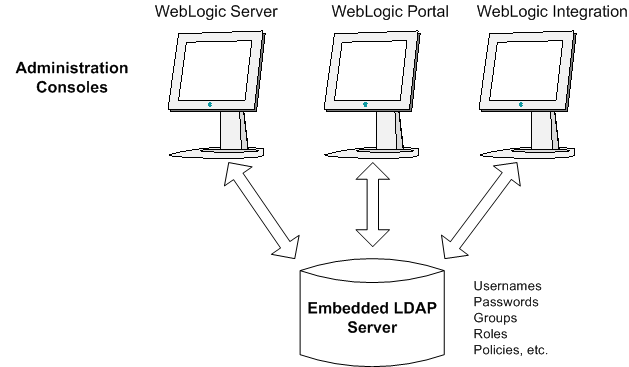
Table 3-1 summarizes the user information that you can create, modify, and remove in each administration console available in WebLogic Platform, and also lists the security provider and storage repository associated by default with each category of user information.
Table 3-1 also lists the default security provider and data store associated with each piece of user information. If later on you choose to customize the store used for user information, you need to customize the associated security provider. (Customizing the data store is described in Using an External LDAP Server.)
Table 3-1 User Information You Can Enter, Modify, and Remove in WebLogic Platform
|
User Information
|
Console Used to Create and Manage Information
|
Associated Security Provider
|
Default Storage Repository
|
|
Usernames and passwords
|
Administration console for any WebLogic Platform component
|
WebLogic Authentication provider
|
Embedded LDAP
|
|
Groups
|
Administration console for any WebLogic Platform component
|
WebLogic Authentication provider
|
Embedded LDAP
|
|
Security Roles
|
Administration console for any WebLogic Platform component
|
WebLogic Role Mapping provider
|
Embedded LDAP
|
|
Portal user profiles
|
WebLogic Administration Portal Console
|
N/A
|
RDBMS
|
|
Trading partner profiles
|
WebLogic Integration Administration Console
|
N/A
|
RDBMS
|
The sections that follow give additional information about the two security providers and the default storage repositories listed in Table 3-1.
Security Providers Associated with User Information
Table 3-1 lists the following security providers that coordinate security functions associated with users, passwords, groups, and roles:
- Authentication provider
Authentication providers are used to prove the identity of users or system processes. Authentication providers also remember, transport, and make identity information available to various components of a system when needed.
- Role Mapping provider
Role Mapping providers obtain a set of security roles granted to a requestor for a given resource at run time, and then supply Authorization providers with this role information so that the Authorization provider can determine if access is allowed to the requested WebLogic resource.
The WebLogic Security Service also provides additional security providers that work with user information, but these two providers are of special importance when backing up or migrating user information, or for customizing how user information is stored.
Default Repositories for User Information
As shown in Table 3-1, the following user information is maintained by default in the embedded LDAP server:
- User names
- Passwords
- Groups
- Security roles
User profiles are created in the RDBMS that is used for storing WebLogic Platform data in a given domain. By default, WebLogic Platform domains use the PointBase RDBMS. For more information about user profiles, see Managing User Profile Information.
Customizing the User Information Data Stores
Table 3-2 shows a sample configuration that uses Netscape iPlanet 4.1.3 LDAP server for storing user and group information, and Oracle 8.1.7 as an RDBMS that is used with WebLogic Platform and WebLogic Portal.
Table 3-2 Using External Data Stores for User Information
|
User Information
|
Console Used to Create and Manage Information
|
Associated Security Provider
|
External Storage Repository
|
|
Usernames and passwords
|
Netscape iPlanet administration server
|
Netscape iPlanet Authentication provider1
|
Netscape iPlanet 4.1.3 LDAP server
|
|
Groups
|
Netscape iPlanet administration server
|
Netscape iPlanet Authentication provider1
|
Netscape iPlanet 4.1.3 LDAP server
|
|
Security Roles
|
Administration console for any WebLogic Platform component
|
WebLogic Role Mapping provider
|
Embedded LDAP
|
|
Portal user profiles
|
WebLogic Administration Portal Console
|
N/A
|
Oracle 8.1.7
|
|
Trading partner profiles
|
WebLogic Integration Administration Console
|
N/A
|
Oracle 8.1.7
|
1.
The WebLogic Platform distribution includes an out-of-the-box authentication provider that can be used with the Netscape iPlanet LDAP server.
Using an External LDAP Server
WebLogic Platform provides tools that make it easy to configure Authentication and Role Mapping providers to work with user information stored in an external LDAP server. This section provides high-level notes about using an external LDAP server and provides links to appropriate topics in the WebLogic Server documentation set that describe the tools and give the steps for migrating user information to and using an external LDAP server.
Note: When you use an external LDAP server, you can use that server to store user and group information. You use the console for that LDAP server to manage the user information stored on it. However, roles, policies, and additional security information remain stored in the embedded LDAP server and are managed from the WebLogic administration consoles.
LDAP Servers You Can Use with WebLogic Platform
WebLogic Platform can be used with any LDAP server that works with WebLogic Server. The following external LDAP servers have been tested with WebLogic Server:
- Netscape iPlanet version 4.1.3
- Active Directory shipped as part of Windows 2000
- Open LDAP version 2.0.7
- Novell NDS version 8.5.1
Note that if you do use an external LDAP server:
- You manage user names, passwords, and groups from the console for that LDAP server.
- From any WebLogic Platform administration console, you can view the user name, password, and group information stored in the external LDAP server, but the access is read-only if you use an out-of-the-box Authentication provider with that server. (You do have the option of creating a custom Authentication provider that has write-access to that information, however.)
For more information about external LDAP server support, see the following topics in Managing WebLogic Security:
Using a Custom or Third Party Authentication Provider
If you choose to store user information in an external LDAP server, you need to configure an Authentication provider that works with that server. WebLogic Platform includes out-of-the-box Authentication providers that have been tested with the LDAP servers listed in the preceding section.
You can also create a custom Authentication provider. Any Authentication provider compatible with the WebLogic Server Security SPI can interact with the users, groups, roles, entitlements, and resources configured for WebLogic Platform. In addition, any such Authentication provider is not restricted in the number of groups and users you configure.
Note: Currently, WebLogic Platform does not offer an authentication provider that can work with user information stored in an RDBMS.
Using Custom or Third-Party Authentication Providers with WebLogic Portal or WebLogic Integration
If you are using a custom or third-party authentication provider with WebLogic Portal or WebLogic Integration, note the following:
- WebLogic Portal and WebLogic Integration support multiple authentication providers, including all the standard providers supported by WebLogic Server.
- WebLogic Portal and WebLogic Integration support the management of users and groups from custom or third-party authentication providers. Note, however, the following limitation: Even though you can use custom or third-party authentication providers, such as the out-of-the-box third-party authentication providers included with WebLogic Platform, only read access to those providers is available from the WebLogic Platform administration consoles by default. Therefore, the WebLogic Portal and WebLogic Integration administration consoles and tools do not support create, delete, and modify operations for user and group management in custom or third-party authentication providers by default. Although the default implementation of the out-of-the-box third-party providers included with WebLogic Platform is read-only, you can configure the provider's MBean to support full create, delete, and modify operations. (Full management access to users and groups is provided by WebLogic Server's embedded LDAP server.)
- New in WebLogic Platform 8.1 Service Pack 3, WebLogic Portal supports multiple authentication providers. You configure, deploy, and undeploy authentication providers via the WebLogic Server Administration Console; and you can use those authentication providers for the management of users, groups, personalization, Delegated Administration, and visitor entitlements directly from the WebLogic Administration Portal.
Note the following regarding the use of multiple authentication providers in WebLogic Portal:
- The WebLogic Administration Portal now includes new pages for building the User Group Resource tree for each configured authentication provider and viewing the read and write permissions for that provider.
- The amount and granularity of information you can manage using a particular custom or third-party authentication provider depends on the set of optional security MBeans that are implemented in the provider.
- The Workshop Portal Extensions have been enhanced to let you specify the authentication provider to use in any development task involving users and groups.
Note that in Service Pack 3, the WebLogic Administration Portal has added the Authentication Hierarchy Service, which you can use for building in-memory group resource trees for each configured authentication provider. This new service gives portal administrators a visual representation of the groups associated with each authentication provider, providing a convenient visual mode for user and group management and increasing the access speed to the users and groups in those providers.
For more information about managing multiple authentication providers in the WebLogic Administration Portal, see Using Multiple Authentication Providers with WebLogic Portal.
For more information about using multiple authentication providers in WebLogic Portal application development, see Using Multiple Authentication Providers in Portal Development.
For More Information About Custom Authentication Providers
If you are using a custom or third-party authentication provider with WebLogic Server, see the following topics in Developing Security Providers for WebLogic Server:
If you want to configure an out-of-the-box authentication provider for an external LDAP server, see "Configuring an LDAP Authentication Provider" in Configuring Security Providers in Managing WebLogic Security.
Using a Custom Role Mapping Provider
The Role Mapping provider included with WebLogic Platform supports the deployment and undeployment of security roles within the system. This provider uses the same security policy engine as the WebLogic Authorization provider. If you want to use a role mapping mechanism that already exists within your organization, however, you can create a custom Role Mapping provider to tie into that system.
Consider an environment that uses a large project database that contains the information required to determine role information. Because the WebLogic Role Mapping provider works only with role information stored in the embedded LDAP server, a custom Role Mapping provider would need to be created that can work with this externally-stored role information.
In WebLogic Platform 8.1 Service Pack 3, the WebLogic Portal administration tools now support the federating of roles from custom or third-party Role Mapping providers. This enables you to create visitor entitlements that are based on roles that are maintained by Role Mapping providers that have been configured in addition to the WebLogic Role Mapping provider.
For information about how to create a custom Role Mapping provider, see "How to Develop a Custom Role Mapping Provider" in Role Mapping Providers in Developing Security Providers for WebLogic Server.
Managing User Profile Information
WebLogic Integration and WebLogic Portal also allow you to add profiles that can be associated with users. By default, user profiles are visible only on the administration console from which they are created. WebLogic Integration and WebLogic Portal store profiles in the WebLogic Integration and WebLogic Portal repositories, respectively, which exist on the RDBMS that has been configured for the WebLogic Platform domain. (By default, this RDBMS is PointBase.)
For example, in WebLogic Integration you can create trading partner profiles. A trading partner profile consists of a user name, a password, and other data that is specific to B2B applications, such as the trading partner's address, business, and other relevant data. The user name associated with a trading partner profile is stored and maintained as a regular WebLogic user in the configured Authentication provider. However, the additional trading partner profile data is stored in the WebLogic Integration repository. WebLogic Integration has an internal mechanism that maps each trading partner profile in its repository with the corresponding user name.
WebLogic Portal also has the notion of a user profile. Like a trading partner profile, a WebLogic Portal user profile:
- Associates a user with the profile, and maintains the corresponding user name and password in the configured Authentication provider. The data in a user profile includes data that is collected about the associated user, such as portal preferences.
- Maintains the additional data in the user profile in the WebLogic Portal repository
By default, trading partner profile information can be viewed only from the WebLogic Integration Administration Console, and Portal user profiles can be viewed only from the WebLogic Administration Portal. However, the users associated with trading partner profiles and Portal user profiles can be viewed in any WebLogic administration console.
Note: Profiles of users created in the WebLogic Integration and WebLogic Portal administration consoles are stored on an RDBMS. Usernames and passwords, however, are maintained by the authentication provider configured for your application domain. They are stored in the LDAP server configured with that provider.
Removing User Profiles
Note the following about removing user profiles:
- When you remove a portal user from any of the WebLogic Platform administration consoles, the profile information associated with that user is no longer accessible from the WebLogic Administration Portal.
- Removing a trading partner from the WebLogic Integration is a two step process:
- Remove the trading partner from the WebLogic Integration Administration Console. This removes the corresponding user profile from the WebLogic Integration repository.
- Remove the corresponding WebLogic Server user from the WebLogic Server Administration Console.
If you perform step a without performing step b, the WebLogic Server user remains in the environment. Likewise, simply removing the WebLogic Server user does not cause the corresponding user profile to be removed from the WebLogic Integration repository.
Users, Groups, and Roles Preconfigured in a Platform Domain
This section lists and describes the users, groups, and roles that are preconfigured when you create a platform domain using the Configuration Wizard. The user information listed in this section is provided for informational purposes only. You may find it useful for the purposes of tracking the users, groups, and security roles that need to be protected, backed up, deleted, or migrated, depending on your software environment and the preconfigured user information that you use.
Default Users Created in a Platform Domain
Table 3-3 lists and describes the users that are created by default in a platform domain.
Table 3-3 Default WebLogic Platform Users
|
User Name
|
Description
|
|
weblogic
|
Default username for the administrator of a domain. This user has system-administrator privileges.
Note that weblogic is the default password for this username in the sample application domains provided out-of-the-box for all WebLogic Platform components.
|
|
portaladmin
|
Default username for the Portal administrator. This user belongs to the Administrators and PortalSystemAdministrators groups. By default, the password for this user is portaladmin. If you are not using the Administration Portal, it is safe to remove this user from any WebLogic Platform administration console.
Note: We strongly recommend that you change this password after you create your domain, especially if the domain is meant to be used in a production environment.
|
|
yahooadmin
|
Default username for the administrator for the My Yahoo! Enterprise Edition portlet. This user belongs to the Administrators group. The yahooadmin name activates support for anonymous users of the My Yahoo! Enterprise Edition portlets. By default, the password for this user is yahooadmin. If you are not using the Administration Portal, it is safe to remove this user from any WebLogic Platform administration console.
Note: We strongly recommend that you change this password after you create your domain, especially if the domain is meant to be used in a production environment.
|
Default WebLogic Server Roles and Groups
Table 3-4 and Table 3-5 list and describe the default WebLogic Server roles and groups created in a platform domain.
Table 3-4 Default Roles in WebLogic Server
|
Role
|
Description
|
|
Anonymous
|
All users (the group everyone) are granted this global role.
|
|
Admin
|
Has the privilege to:
Deploy enterprise applications, startup and shutdown classes, and Web Application, EJB, J2EE Connector, and Web Service modules.
|
|
Deployer
|
Has the privilege to:
Deploy enterprise applications, startup and shutdown classes, and Web Application, EJB, J2EE Connector, and Web Service modules.
|
|
Operator
|
Has the privilege to:
|
|
Monitor
|
Has the privilege to view the server configuration, except for encrypted attributes.
|
Table 3-5 Default Groups in WebLogic Server
|
Group
|
Description
|
|
users
|
Users, when they log in (for example, through a Web page).
|
|
everyone
|
Every user is a member of this group.
|
|
Administrators
|
By default, this group contains:
Any user assigned to the Administrators group is granted the Administrator security role by default and has full administrator privileges for all WebLogic Platform components, including WebLogic Integration and WebLogic Portal.
|
|
Deployers
|
By default, this group is empty. Any user assigned to the Deployers group is granted the Deployer security role by default.
|
|
Operators
|
By default, this group is empty. Any user assigned to the Operators group is granted the Operator security role by default.
|
|
Monitors
|
By default, this group is empty. Any user assigned to the Monitors group is granted the Monitor security role by default.
|
Default WebLogic Integration Security Roles and Groups
Table 3-6 and Table 3-7 lists and describes the default WebLogic Integration roles and groups created in a platform domain.
Table 3-6 Default WebLogic Integration Security Roles
|
Role
|
Description
|
|
IntegrationAdmin
|
WebLogic Integration administrator role. This role has full privileges to all servers in the cluster. This role can create additional roles using the administration console.
|
|
IntegrationDeployer
|
WebLogic Integration deployer role. This role has full privileges to all servers in the cluster. This role can create additional roles using the administration console.
|
|
IntegrationOperator
|
The WebLogic Integration operator role. This role has nearly all the privileges of the IntegrationAdministrator role. For example, a user in the IntegrationOperator role cannot configure certain security properties, but can otherwise modify resources.
|
|
IntegrationMonitor
|
The WebLogic Integration monitor role. This role has read-only access to the WebLogic Integration Administration Console.
|
|
IntegrationUser
|
The default WebLogic Integration user role. When first created, all users are assigned to the IntegrationUser role.
|
|
TaskCreationRole
|
Optional role that you can authorize to create Worklist Tasks, as described in "Configuring the Worklist Task Creation Role" in System Configuration in Managing WebLogic Integration Solutions.
If you configure this role to be authorized to create Worklist Tasks, any user assigned to the TaskCreationGroup would have this privilege. However, by default, the TaskCreationRole does not have any special privileges until explicitly configured to have them.
|
Table 3-7 Default Groups in WebLogic Integration
|
Group
|
Description
|
|
IntegrationAdministrators
|
The WebLogic Integration administrator group. This group is assigned to the role IntegrationAdmin, and all members inherit the that role.
|
|
IntegrationDeployers
|
The WebLogic Integration deployer group. This group is assigned to the role IntegrationDeployer, and all members inherit the that role.
|
|
IntegrationUsers
|
The WebLogic Integration user group. This group is assigned to the role IntegrationUser, and all members inherit the that role.
|
|
IntegrationMonitors
|
The WebLogic Integration monitor group. This group is assigned to the role IntegrationMonitor, and all members inherit the that role.
|
|
IntegrationOperators
|
The WebLogic Integration operator group. This group is assigned to the role IntegrationOperator, and all members inherit the that role.
|
|
TaskCreationGroup
|
The WebLogic Integration group containing users, in addition to Integration Administrators, that are authorized to create new Worklist Tasks. This group is assigned to the role TaskCreationRole.
|
Default WebLogic Portal Security Roles and Groups
Table 3-8 and Table 3-9 list and describe the default WebLogic Portal roles and groups created in a platform domain.
Table 3-8 Default Security Roles in WebLogic Portal
|
Role
|
Description
|
|
CustomerRole
|
Role associated with the wlcs_customer group, which is used with commerce services. You can safely remove this role if your portal applications do not use commerce services.
|
|
PortalSystemAdministrator
|
The default WebLogic Portal system administrator role. This role has full privileges to all servers in the cluster. This role can create additional roles using the administration console.
|
|
PortalSystemDelegator
|
Top-level role for establishing delegated administration. All users in the Administrators group are assigned to this role by default.
|
Table 3-9 Default Groups in WebLogic Portal
|
Group
|
Description
|
|
PortalSystemAdministrators
|
The WebLogic Portal administrator group. This group is assigned to the role PortalSystemAdministrator, and all members inherit the that role.
|
|
wlcs_customer
|
Group used in commerce services for distinguishing portal customers from portal users. This group exists for compatibility purposes with WebLogic Portal 7.0. You can safely remove this group if your portal applications do not use commerce services.
|