


|

|
|
|
|
Joining the ATMI Application
In a secure ATMI application, it is necessary to pass security information to the BEA Tuxedo system via a TPINIT buffer for C, or a TPINFDEF-REC record for COBOL. The TPINIT buffer is a special typed buffer used by a client program to pass client identification and authentication information to the system as the client attempts to join the ATMI application. The TPINFDEF-REC record serves the same purpose in a COBOL application.
TPINIT is defined in the atmi.h header file, and TPINFDEF-REC is defined in the COBOL COPY file. They have the following structures.
The fields in the TPINIT buffer/ TPINFDEF-REC record are described in the following table.
The client program calls tpalloc(3c) to allocate a TPINIT buffer. The following sample code prepares to pass eight bytes of application-specific data to tpinit() and enables the client to join an ATMI application.
Allocating a TPINIT Buffer and Joining an ATMI Application
.
.
.
TPINIT *tpinfo;
.
.
.
if ((tpinfo = (TPINIT *)tpalloc("TPINIT",(char *)NULL,
TPINITNEED(8))) == (TPINIT *)NULL){
Error Routine
}
.
.
.
tpinit(tpinfo) /* join an ATMI application */
.
.
.
When a Workstation client calls the tpinit() function or the TPINITIALIZE() routine to join an ATMI application, the following major events occur.
When a native client calls the tpinit() function or the TPINITIALIZE() routine to join an ATMI application, only authentication occurs. In essence, the native client authenticates with itself.
Transferring the Client Security Data
The following figure demonstrate the transfer of data from the TPINIT buffer for a Workstation client. The transfer of data from the TPINFDEF-REC record is similar to what is shown in the figure.
Transferring Data from the TPINIT Buffer for a Workstation Client
Note: The authorization procedure shown in the preceding figure is essentially the same for a native client attempting to join an ATMI application except that no network link or WSH is involved. A native client authenticates with itself. In the preceding diagram, notice that the information sent to the BEA Tuxedo system differs between default and custom authentication. For default authentication, the values of the cltname, grpname, and flags fields are delivered to the default authentication plug-in at the Workstation client by a means other than through the plug-in interface. However, for custom authentication, writers of client programs can include these values as well as any other values they so choose in the variable length data field. For a Workstation client and assuming default authentication, the authentication plug-in at the Workstation client uses the passwd/ PASSWD field to encrypt the information when transmitting the information over the network. The encryption algorithm used is 56-bit DES, where DES is an acronym for the Data Encryption Standard. The authentication plug-in at the target WSH uses the application password stored in the TUXCONFIG file to decrypt the information. For a native client, the system simply compares the passwd/ PASSWD field with the application password stored in the TUXCONFIG file. Note: At the Workstation client, the passwd/ PASSWD field is delivered to the authentication plug-in by a means other than through the authentication plug-in interface. At the WSH, the application password in the TUXCONFIG file is delivered to the authentication plug-in through the authentication plug-in interface during application booting. After a successful authentication of a Workstation client, the tpinit() function ends with the sending of another buffer to the WSH containing the values of the usrname, cltname, and flags fields, to ensure that the WSH receives this information for the authenticated Workstation client. Similarly, the TPINITIALIZE() routine ends with the sending of another buffer containing the same information. A custom authentication plug-in might not send this information to the WSH during the authentication procedure, and the WSH needs this information for reporting purposes, that is, during an invocation of the tmadmin(1) printclient (pclt) command. When a Workstation or native client passes the security check, it may initiate service requests and receive replies. Calling a Service Request Before Joining the ATMI Application If a client calls a service request (or any ATMI function) before invoking tpinit() or TPINITIALIZE() and assuming the SECURITY configuration for the target ATMI application is not set or is set to NONE, the BEA Tuxedo system automatically invokes tpinit()/ TPINITIALIZE() with a NULL parameter. This behavior has the following consequences: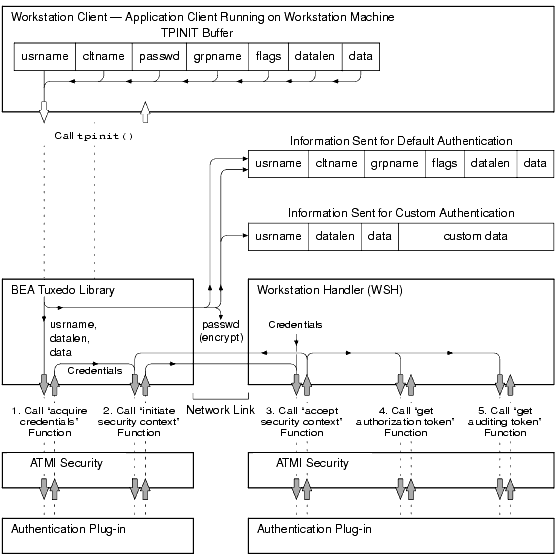
If a client calls a service request (or any ATMI function) before invoking tpinit() or TPINITIALIZE() and assuming the SECURITY configuration for the target ATMI application is set to APP_PW, USER_AUTH, ACL, or MANDATORY_ACL, the BEA Tuxedo system rejects the service request.
See Also

|
|
|
|
|
Copyright © 2001 BEA Systems, Inc. All rights reserved.
|