Developing Security Providers
Introduction to Developing Security Providers
About This Document
This document provides application developers with the information needed to develop custom security providers for use with BEA WebLogic Enterprise SecurityTM Security Service Modules. This document is organized as follows:
- Introduction to Developing Security Providers, which prepares you to learn more about developing security providers for use with WebLogic Enterprise Security. It specifies the audience and prerequisites for this guide, and provides an overview of the development process.
- Security Provider Concepts, which explains the concepts that you must understand to be able to develop custom security providers. This topic also includes a discussion about JAAS LoginModules.
- Design Considerations, describes the capabilities of the security providers shipped with BEA WebLogic Enterprise Security and the general architecture of a security provider, and provides background information about implementing Security Services Provider Interfaces (SSPIs) and generating MBean types. This section also suggests ways your custom security providers might work with databases that contain information security providers require.
- Developing Custom Security Providers, provides instructions for implementing each type of security provider.
- Auditing Events from Custom Security Providers, explains how to add auditing capabilities to the custom security providers that you develop.
- Code Examples for Developing Security Providers, demonstrates how to write the code when developing custom security providers.
- MBean Definition File Element Syntax, describes the attributes and syntax of the MBean Definition File.
Product Documentation on the dev2dev Web Site
BEA product documentation, along with other information about BEA software, is available from the BEA dev2dev web site:
http://dev2dev.bea.com
To view the documentation for a particular product, select that product from the Product Centers menu on the left side of the screen on the dev2dev page. Select More Product Centers. From the BEA Products list, choose WebLogic Enterprise Security 4.2. The home page for this product is displayed. From the Resources menu, choose Documentation 4.2. The home page for the complete documentation set for the product and release you have selected is displayed.
Related Information
The BEA corporate web site provides all documentation for BEA WebLogic Enterprise Security. Other BEA WebLogic Enterprise Security documents that may be of interest to the reader include:
- Introduction to WebLogic Enterprise Security—This document summarizes the features of the BEA WebLogic® Enterprise Security products and presents an overview of the architecture and capabilities of the security services. It provides a starting point for understanding the family of BEA WebLogic Enterprise Security products.
- BEA WebLogic Enterprise Security Administration Guide—This document provides a complete overview of the product and includes step-by-step instructions on how to perform various administrative tasks.
- Programming Security for Java Applications—This document describes how to implement security in Java applications. It includes descriptions of the Security Service Application Programming Interfaces and programming instructions for implementing security in Java applications.
- BEA WebLogic Enterprise Security Policy Managers Guide—This document defines the policy model used by BEA WebLogic Enterprise Security, and describes how to import and export policy data.
- Javadocs for Java API—This document provides reference documentation for the Java Application Programming Interfaces that are provided with and supported by this release of BEA WebLogic Enterprise Security.
- Javadocs for Security Service Provider Interfaces—This document provides reference documentation for the Security Service Provider Interfaces that are provided with and supported by this release of BEA WebLogic Enterprise Security.
The following sections prepare you to learn more about developing security providers:
Audience for This Guide
This book is designed for security and application developers who want to write their own security providers for use with BEA WebLogic Enterprise Security. It is assumed that those using this document are application developers who have a solid understanding of security concepts, and that no basic security concepts require explanation. It is also assumed that security and application developers are familiar with BEA WebLogic Enterprise Security and with Java programming.
Prerequisites for This Guide
Prior to reading this guide, you should read the Introduction to BEA WebLogic Enterprise Security. This document describes how the product works and provides conceptual information that is helpful to understanding the necessary installation components.
Additionally, BEA WebLogic Enterprise Security includes many unique terms and concepts that you need to understand. These terms and concepts—which you will encounter throughout the documentation—are defined in the Glossary.
Overview of the Development Process
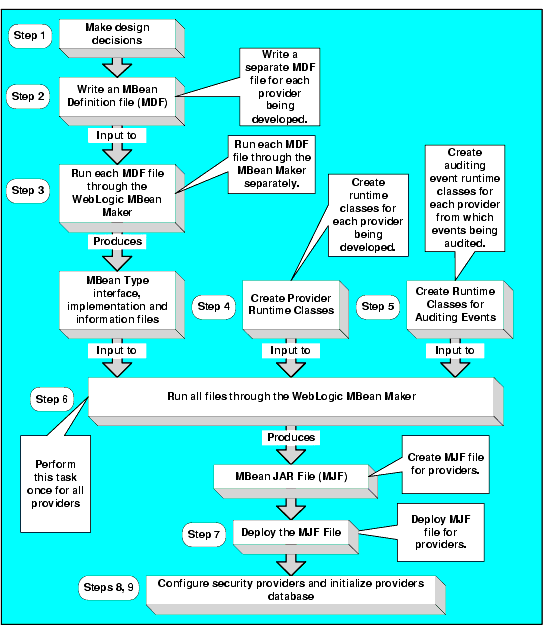
To develop a custom security provider, you perform the following tasks:
- Make security provider design decisions.
- Write an MBean Definition File for each security provider you want to develop.
- Run each MBean Definition File file through the WebLogic MBean Maker.
- Create the runtime classes for each security provider you want to develop.
- Create the auditing event classes for each security provider from which events are audited (optional).
- Run the files generated by the MBean Maker and the runtime class files through the WebLogic MBean Maker to produce an MBean JAR file.
Note: An MBean JAR file can contain multiple security providers, therefore you only need to run the MBean Maker once to produce the MBean JAR file.
- Deploy the MJF file to the BEA WebLogic Enterprise Security systems from which you want to use the providers.
Note: This includes copying the JAR file to both the Administration Application and the Security Service Module provider directories.
- Use the Administration Console to configure the security providers.
- Initialize the security provider databases.
Figure 1-1 illustrates the security provider development process. For detailed instructions for each of the development tasks, see Developing Custom Security Providers.
Figure 1-1 Developing Custom Security Provider Tasks
Types of Providers
You use the SSPI provided with the product to create runtime classes for custom security providers, which are located in the weblogic.security.spi package. For more information about this package, see Javadocs for Security Service Provider Interfaces.
Table 1-1 maps the types of security providers and their components with the SSPI and other interfaces you use to develop them.
Table 1-1 Security Providers, Components, and Corresponding SSPI
|
Type/Component
|
Interface
|
|
Authentication provider
|
AuthenticationProvider
|
|
LoginModule (JAAS)
|
LoginModule
|
|
Identity Assertion provider
|
AuthenticationProvider
|
|
Identity Asserter
|
IdentityAsserter
|
|
Principal Validation provider
|
PrincipalValidator
|
|
Authorization
|
AuthorizationProvider
|
|
Access Decision
|
AccessDecision
|
|
Adjudication provider
|
AdjudicationProvider
|
|
Adjudicator
|
Adjudicator
|
|
Role Mapping provider
|
RoleProvider
|
|
Role Mapper
|
RoleMapper
|
|
Auditing provider
|
AuditProvider
|
|
Audit Channel
|
AuditChannel
|
|
Credential Mapping provider
|
CredentialProvider
|
|
Credential Mapper
|
CredentialMapper
|