3 Using Oracle Audit Vault Reports
This chapter contains:
3.1 What Are Oracle Audit Vault Reports?
The Oracle Audit Vault reports are automatically generated reports that describe the state of audited activities. They reflect audited data collected from the Oracle Database, Microsoft SQL Server, Sybase ASE, and IBM DB2 source databases that connect to the Audit Vault Server. For all of these products, they track the audit events described in Appendix A through Appendix D.
The default reports are organized into various categories, such as access reports and management reports. You can create user-defined reports that focus on specific areas or audited events.
Any user who has been granted the AV_AUDITOR role can view and modify the reports.
3.2 Accessing the Oracle Audit Vault Audit Reports
To access the Oracle Audit Vault audit reports:
-
Log in to the Oracle Audit Vault Console as a user who has been granted the
AV_AUDITORrole, as explained in Section 1.4.The Dashboard page appears.
-
Click the Audit Reports tab in the upper-right corner of the window.
-
Do one of the following:
-
To view and work with reports: Click the appropriate secondary tab to find the report you want to view (Default Reports, Compliance Reports, Custom Reports, or Generated Reports). To view the report (for example, Data Access under the Access Reports category), click its link.
-
To schedule and send to another user a PDF report: Click the Report Schedules secondary tab. See Section 3.6.
-
To annotate and attest a report: Click the Generated Reports secondary tab, select the report, and then click the Details button. See Section 3.7.
-
To view snapshots of audit data in the entitlement reports: Click Entitlement Snapshots secondary tab. See Section 3.8.
-
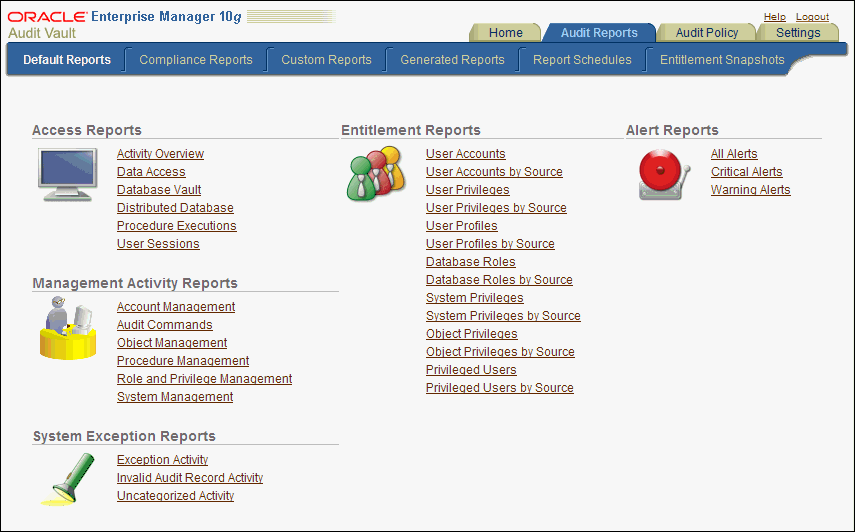
3.3 Using the Default Reports
This section contains:
3.3.1 About the Default Reports
The default reports are predefined reports that cover commonly required audit data.
Figure 3-1 shows the Default Reports page.
3.3.2 Using the Default Access Reports
This section contains:
3.3.2.1 About the Default Access Reports
The default access reports track general database access activities such as audited SQL statements, Oracle Database Vault activities, application access activities, and user login activities. These reports display the following kinds of information: source database name, source database type, host name for the source database, version of the source database, IP address of the source database, audit time, Audit Vault category, the event itself (such as LOGIN statements), current and previous values of the event, user and host client information, the event status (such as failure), and the time the event took place.
You can create user-defined custom reports from the reports. See Section 3.9 and Section 3.11.
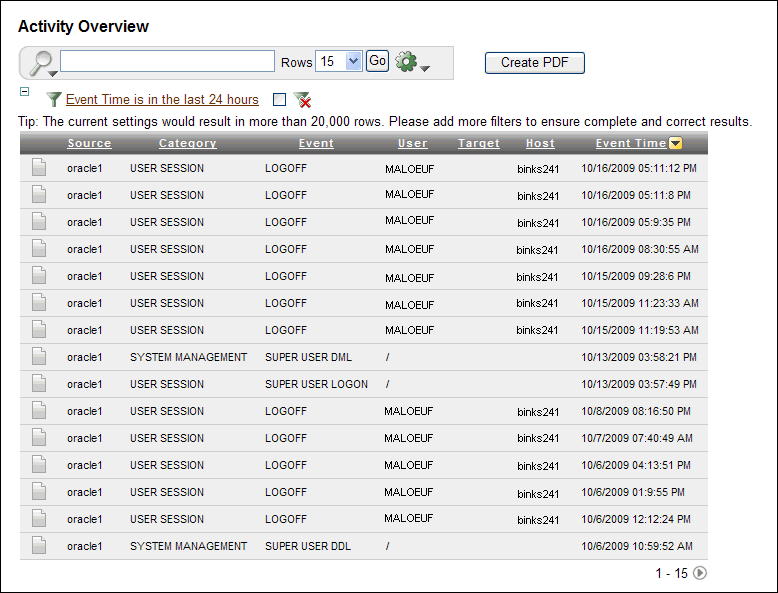
3.3.2.2 Activity Overview Report
The Activity Overview page displays all audit trail records. Audit records appear based on their audit event time in descending order (newest record first). This report can be very large, but you can create a user-defined version that filters specific audit data. By default, 15 audit records are displayed on each page.
If you suspect that the Audit Vault data warehouse is not being refreshed with the latest audit data, then check the Activity Overview Report. If you find that the audit data that you want is not listed in this report, then ask your Audit Vault administrator to check the server-side log files (alert and trace logs) for errors. If there are errors, then contact Oracle Support.
Figure 3-2 shows the Activity Dashboard page.
3.3.2.3 Data Access Report
The Data Access Report displays audited SQL statements, such as Oracle Database data manipulation language (DML) activities (for example, all SELECT, INSERT, UPDATE, or DROP SQL statements).
See Also:
-
Section A.5 for Oracle Database audit events
-
Section B.5 for SQL Server audit events
-
Section C.5 for Sybase Adaptive Server Enterprise audit events
-
Section D.5 for IBM DB2 audit events
-
Section 3.4.5.9 if you want to use the Program Change Report to track changes to row data from
INSERTorUPDATEstatements
3.3.2.4 Database Vault Report
The Database Vault Report displays audited Oracle Database Vault activity. These audit records are collected from the Oracle Database Vault audit trail.
If the Database Vault Report does not show data, then Oracle Database Vault may not be enabled. To check that Oracle Database Vault is enabled, log in to SQL*Plus and then query the V$OPTION table. Any user can query this table. If Oracle Database Vault is enabled, the query returns TRUE; otherwise, it returns FALSE. Remember that you must enter the parameter value, Oracle Database Vault, using case-sensitive letters, as in the following example:
SQL> SELECT * FROM V$OPTION WHERE PARAMETER = 'Oracle Database Vault'; PARAMETER VALUE ----------------------------- ----------------------- Oracle Database Vault TRUE
See also Section A.6 for a listing of the Oracle Database Vault audit events.
3.3.2.5 Distributed Database Report
The Distributed Database Report displays audited distributed database activity, such as Oracle Database CREATE DATABASE LINK or DROP DATABASE LINK statements. (Note that the associated audit events are called peer association events.)
See Also:
-
Section A.10 for Oracle Database audit events
-
Section B.9 for SQL Server audit events
-
Section C.9 for Sybase Adaptive Server Enterprise audit events
-
Section D.9 for IBM DB2 audit events
3.3.2.6 Procedure Executions Report
The Procedure Executions Report displays audited application access activity, such as the execution of SQL procedures or functions. (Note that the associated audit events are called service and application utilization events.)
See Also:
-
Section A.12 for Oracle Database audit events
-
Section B.11 for SQL Server audit events
-
Section C.11 for Sybase Adaptive Server Enterprise audit events
-
Section D.11 for IBM DB2 audit events
-
Section 3.3.3.5 for information about the Procedure Management Report
3.3.2.7 User Sessions Report
The User Sessions Report displays audited authentication events for users who log in to the database. This includes the time the user logged in, the login event, and how the user was authenticated.
See Also:
-
Section A.15 for Oracle Database audit events
-
Section B.14 for SQL Server audit events
-
Section C.14 for Sybase Adaptive Server Enterprise audit events
-
Section D.14 for IBM DB2 audit events
3.3.3 Using the Default Management Activity Reports
This section contains:
3.3.3.1 About the Default Management Activity Reports
The default management activity reports track the use of AUDIT SQL statements, changes to user accounts, actions performed on the underlying packages for applications, actions performed on database objects, roles and privileges, and system management activities such as database shutdowns and startups. These reports display the following kinds of information: source database name, source database type, host name for the source database, version of the source database, IP address of the source database, audit time, Audit Vault category, the event itself (such as GRANT statements), current and previous values of the event, user and host client information, the event status (such as failure), and the time the event took place.
You can create user-defined reports from the reports. See Section 3.9 and Section 3.11.
3.3.3.2 Account Management Report
The Account Management Report displays account management activity of the user's audited SQL statements. This includes audited changes to user accounts and profiles (setting limits on database resources), for example, when user accounts are created, altered, or deleted, and when database schemas are created.
See Also:
-
Section A.2 for Oracle Database audit events
-
Section B.2 for SQL Server audit events
-
Section C.2 for Sybase Adaptive Server Enterprise audit events
-
Section D.2 for IBM DB2 audit events
3.3.3.3 Audit Commands Report
The Audit Commands Report displays the use of audit commands, such as Oracle Database AUDIT SQL statements for other SQL statements and database objects. For example, for Oracle Database, this page tracks AUDIT ALL, AUDIT SELECT ON table_name statements, NOAUDIT statements, and so on.
See Also:
-
Section A.4 for Oracle Database audit events
-
Section B.4 for SQL Server audit events
-
Section C.4 for Sybase Adaptive Server Enterprise audit events
-
Section D.4 for IBM DB2 audit events
3.3.3.4 Object Management Report
The Object Management Report displays audited actions performed on database objects. For example, these audit records are created for create, alter, or drop operations on database objects that are performed on a database table.
See Also:
-
Section A.9 for Oracle Database audit events
-
Section B.8 for SQL Server audit events
-
Section C.8 for Sybase Adaptive Server Enterprise audit events
-
Section D.8 for IBM DB2 audit events
3.3.3.5 Procedure Management Report
The Procedure Management Report displays audited actions that were performed on the underlying procedures or functions of system services and applications. For example, it lists the audit records that were created for Oracle Database ALTER FUNCTION, ALTER JAVA, or ALTER PACKAGE statements. (Note that the associated audit events are called application management events.)
See Also:
-
Section A.3 for Oracle Database audit events
-
Section B.3 for SQL Server audit events
-
Section C.3 for Sybase Adaptive Server Enterprise audit events
-
Section D.3 for IBM DB2 audit events
-
Section 3.3.2.6 for information about the Procedure Executions Report
3.3.3.6 Role and Privilege Management Report
The Role and Privilege Management Report lists audited role and privilege management activity, such as the creating, granting, revoking, and dropping of roles and privileges. It lists the name of the user performing the action, and the user to whom the action applies.
See Also:
-
Section A.11 for Oracle Database audit events
-
Section B.10 for SQL Server audit events
-
Section C.10 for Sybase Adaptive Server Enterprise audit events
-
Section D.10 for IBM DB2 audit events
3.3.3.7 System Management Report
The System Management Report displays audited system management activity. For example, it lists activities such as startup and shutdown operations on a database, enable and disable operations on all triggers, and rollback operations. It also lists user-related operations, such as unlocking a user account.
See Also:
-
Section A.13 for Oracle Database audit events
-
Section B.12 for SQL Server audit events
-
Section C.12 for Sybase Adaptive Server Enterprise audit events
-
Section D.12 for IBM DB2 audit events
3.3.4 Using the Default System Exception Reports
This section contains:
3.3.4.1 About the Default System Exception Reports
The default system exception reports track audit events, such as exceptions that occur and audit activities that Oracle Audit Vault cannot recognize or place into a category. These reports display the following kinds of information: source database name, source database type, host name for the source database, version of the source database, IP address of the source database, audit time, Audit Vault category, the event itself (such as network errors), current and previous values of the event, user and host client information, the event status (such as failure), and the time the event took place.
You can create user-defined reports from the reports. See Section 3.9 and Section 3.11.
3.3.4.2 Exception Activity Report
The Exception Activity Report displays audited error and exception activity, such as network errors.
See Also:
-
Section A.7 for Oracle Database audit events
-
Section B.6 for SQL Server audit events
-
Section C.6 for Sybase Adaptive Server Enterprise audit events
-
Section D.6 for IBM DB2 audit events
3.3.4.3 Invalid Audit Record Report
The Invalid Audit Record Report displays audited activity that Oracle Audit Vault cannot recognize, possibly due to a corrupted audit record.
See Also:
-
Section A.8 for Oracle Database audit events
-
Section B.7 for SQL Server audit events
-
Section C.7 for Sybase Adaptive Server Enterprise audit events
-
Section D.7 for IBM DB2 audit events
3.3.4.4 Uncategorized Activity Report
The Uncategorized Activity Report displays audited activity that cannot be categorized. For example, it lists events such as Oracle Database COMMENT, CREATE SUMMARY, or NO-OP events.
See Also:
-
Section A.14 for Oracle Database audit events
-
Section B.13 for SQL Server audit events
-
Section C.13 for Sybase Adaptive Server Enterprise audit events
-
Section D.13 for IBM DB2 audit events
3.3.5 Using the Default Entitlement Reports
This section contains:
-
System Privileges Report and System Privileges by Source Report
-
Object Privileges Report and Object Privileges by Source Report
-
Privileged Users Report and Privileged Users by Source Report
3.3.5.1 About the Default Entitlement Reports
An entitlement report describes the types of access that users have to an Oracle source database. It provides information about the user, role, profile, and privileges used in the source database. For example, the entitlement reports capture information such as access privileges to key data or privileges assigned to a particular user. These reports are useful for tracking unnecessary access to data, finding duplicate privileges, and simplifying privilege grants.
After you generate a default entitlement report, you can view a snapshot of the metadata that describes user, role, profile, and privilege information. This enables you to perform tasks such as comparing different snapshot labels to find how the entitlement information has changed over time. See Section 3.8.
See Also:
-
Section 3.8.6 for information about generating and viewing entitlement report data
-
Section 3.9 and Section 3.11 for information about creating user-defined reports from entitlement reports
3.3.5.2 User Accounts Report and User Accounts by Source Report
The User Accounts Report and User Accounts by Source Report show the following information about user accounts: source database in which the user account was created, user account name, account status (LOCKED or UNLOCKED), expiration date for the password, initial lock state (date the account will be locked), default tablespace, temporary tablespace, initial resource consumer group, when the user account was created, associated profile, and external name (the Oracle Enterprise User DN name, if one is used).
The difference between these reports is that the "by Source" report enables you to view snapshot data from a specific Oracle source database. The regular report includes snapshot label data from all Oracle source databases assigned to given labels.
3.3.5.3 User Privileges Report and User Privileges by Source Report
The User Privileges Report and User Privileges by Source Report show the following information about user privileges: source database in which the privilege was created, user name, privilege, schema owner, table name, column name, type of access (direct access or if through a role, the role name), whether the user privilege was created with the ADMIN option, whether the user can grant the privilege to other users, and who granted the privilege.
The difference between these reports is that the "by Source" report enables you to view snapshot data from a specific Oracle source database. The regular report includes snapshot label data from all Oracle source databases assigned to given labels.
3.3.5.4 User Profiles Report and User Profiles by Source Report
The User Profiles Report and User Profiles by Source Report show the following information about user profiles: source database in which the user profile was created, profile name, resource name, resource type (KERNEL, PASSWORD, or INVALID), and profile limit.
The difference between these reports is that the "by Source" report enables you to view snapshot data from a specific Oracle source database. The regular report includes snapshot label data from all Oracle source databases assigned to given labels.
3.3.5.5 Database Roles Report and Database Roles by Source Report
The Database Roles Report and Database Roles by Source Report lists names of database roles and application roles. If the role is a secure application role, then the Schema and Package columns of the report indicate the underlying PL/SQL package used to enable the role.
The difference between these reports is that the "by Source" report enables you to view snapshot data from a specific Oracle source database. The regular report includes snapshot label data from all Oracle source databases assigned to given labels.
3.3.5.6 System Privileges Report and System Privileges by Source Report
The System Privileges Report and System Privileges by Source Report show the following information about system privileges: source database in which the system privilege was created, user granted the system privilege, privilege name, type of access (direct access or if through a role, the role name), and whether it was granted with the ADMIN option.
The difference between these reports is that the "by Source" report enables you to view snapshot data from a specific Oracle source database. The regular report includes snapshot label data from all Oracle source databases assigned to given labels.
3.3.5.7 Object Privileges Report and Object Privileges by Source Report
The Object Privileges Report and Object Privileges by Source Report show the following information about object privileges: the source database in which the object was created, users granted the object privilege, schema owner, target name (which lists tables, packages, procedures, functions, sequences, and other objects), column name (that is, column-level privileges), privilege (object or system privilege, such as SELECT), type of access allowed the object (direct access or if through a role, the role name), whether the object privilege can be granted, and who the grantor was.
The difference between these reports is that the "by Source" report enables you to view snapshot data from a specific Oracle source database. The regular report includes snapshot label data from all Oracle source databases assigned to given labels.
3.3.5.8 Privileged Users Report and Privileged Users by Source Report
The Privileged Users Report and Privileged Users by Source Report show the following information about privileged users: source database in which the privileged user account was created, user name, privileges granted to the user, type of access (direct access or if through a role, the role name), and whether the privileged user was granted the ADMIN option.
The difference between these reports is that the "by Source" report enables you to view snapshot data from a specific Oracle source database. The regular report includes snapshot label data from all Oracle source databases assigned to given labels.
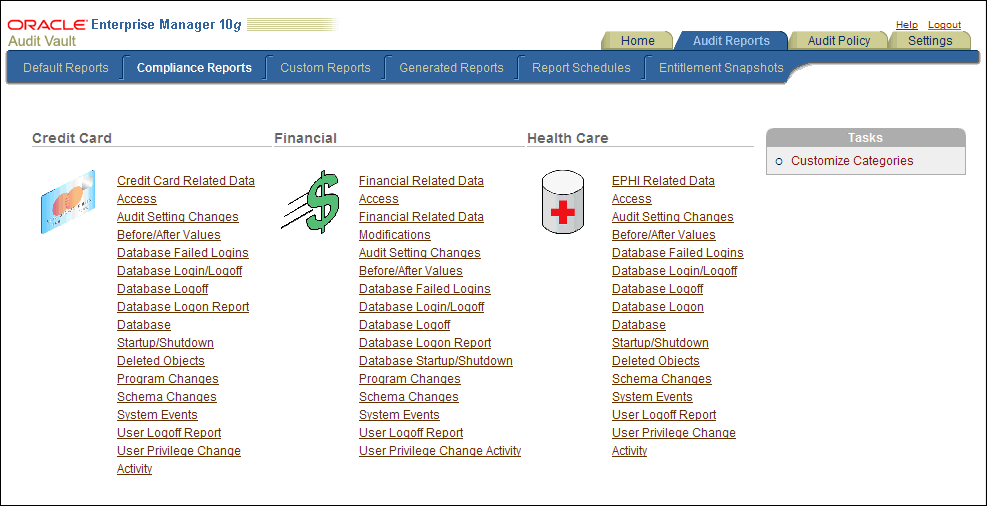
3.4 Using the Compliance Reports
This section contains:
-
Credit Card Compliance Report: Related Data Access Compliance Report
-
Health Care Compliance Report: EPHI Related Data Access Report
-
Common Credit Card, Financial, and Health Care Compliance Reports
See Also:
Section 3.9.4 for information about changing the default displayed contents of a compliance report3.4.1 About the Compliance Reports
The compliance reports provide out-of-the-box reports to help you meet regulations associated with credit card, financial, and health care related data. They track activities that are typically required to meet standard compliance regulations, such as changes to the database structure or its objects, failed logins, administrator activities, system events, and user logins or logoffs. Internal and external auditors request many of these reports to monitor security and compliance for your business.
The compliance reports have three categories: credit card, financial, and health care. For example, all three of the categories listed have a Database Logon Report, but each category determines the type of data shown in the report. To customize the display name, description, data output, and source database for a report, under Tasks, select the Customize Categories link.
To access the compliance reports, select the Audit Reports tab, then select Compliance Reports. You can create user-defined reports from the reports. See Section 3.9 and Section 3.11. To customize the displayed contents of the default report, see Section 3.9.4.
Figure 3-3 shows the Compliance Reports page.
3.4.2 Credit Card Compliance Report: Related Data Access Compliance Report
The Credit Card Related Data Access Report displays audited SQL statements, such as Oracle Database data manipulation language (DML) activities (for example, all SELECT, INSERT, UPDATE, or DELETE SQL statements).
For additional compliance reports that can be used for credit card audit data, see Section 3.4.5.
3.4.3 Financial Compliance Reports
The financial compliance reports are as follows:
3.4.3.1 Financial Related Data Access Report
The Financial Related Data Access Report displays audited SQL statements that were used to access financial data, such as SELECT SQL statements.
For additional compliance reports that can be used for financial audit data, see Section 3.4.5.
3.4.3.2 Financial Related Data Modifications Report
The Financial Related Data Modifications Report displays audited SQL statements that were used to modify financial data, such as Oracle Database data manipulation language (DML) activities (for example, all INSERT, UPDATE, or DELETE SQL statements).
For additional compliance reports that can be used for financial audit data, see Section 3.4.5.
3.4.4 Health Care Compliance Report: EPHI Related Data Access Report
The EPHI (Electronic Protected Health Information) Related Data Access Report displays audited SQL statements that were used to access or modify health care data, such as Oracle Database data manipulation language (DML) activities (for example, all INSERT, UPDATE, or DELETE SQL statements).
For additional compliance reports that can be used for health care audit data, see Section 3.4.5.
3.4.5 Common Credit Card, Financial, and Health Care Compliance Reports
The credit card, financial, and health care reports all have the following common reports:
3.4.5.1 Audit Setting Changes Report
The Audit Settings Changes Report displays audited activity of audit setting changes (for example, changes to the AUDIT ALL SQL statement). It captures data such as Oracle Database Vault rules, rule sets, and factors; original content; fine grained audit policies if any were used; and proxy session IDs.
3.4.5.2 Before/After Values Report
The Before/After Values Report displays a wide range of before and after values for events such as schema owners, events, event values, timing of the event changes, and which source databases they affect. It tracks information such as the IP address and client user connections. This report is designed for users who must capture specific before and after values of Oracle database tables using the REDO collector. Contact your Oracle Audit Vault administrator for more information about the REDO collector.
3.4.5.3 Database Failed Logins Report
The Database Failed Logins Report displays audited failed login attempts. These audit records are generated for failed login, proxy authentication only, and super user login attempts.
3.4.5.4 Database Login/Logoff Report
The Database Login/Logoff Report displays audited login and logoff operations of users. For example, these audit records are generated when you audit events, such as login, logoff, privileged user login, logoff by cleanup, and proxy authentication only.
3.4.5.5 Database Logoff Report
The Database Logoff Report displays information about user logoff operations, such as the user name, proxy session ID, client user information, and when the logoff operation took place.
3.4.5.6 Database Logon Report
Similar to the Database Logoff Report, the Database Logon Report shows information about user logon operations. It captures the same type of information the Database Logoff Report captures.
3.4.5.7 Database Startup/Shutdown Report
The Database Startup/Shutdown Report tracks when the source database was started and shut down, and includes information such as the user who performed the startup or shutdown operation.
3.4.5.8 Deleted Objects Report
The Deleted Objects Report displays audited SQL statements that were used to delete database objects, such as delete operations on a specific table. It tracks the user who deleted the object and the command the user used to delete the object.
3.4.5.9 Program Changes Report
The Program Changes Report displays changes to row data when an insert or update operation occurs in Oracle Database. It tracks data such as the user who performed the action the action itself, and when the action took place. This report is especially useful if you are using the redo collector to extract the before and after values of data updates.
3.4.5.10 Schema Changes Report
The Schema Changes Report displays audited data definition language (DDL) activities (for example, changes to the database schema that result from SQL ALTER, CREATE, or DROP statements). It tracks data such as the user who changed the schema, when the change took place, and the status of the change attempt.
3.4.5.11 System Events Report
The System Events Report displays audited system event activities. These audit records are generated when you audit local system processes. It tracks events such as the SQL text that caused the system event, the user responsible for it, the privilege required for the event, and when the event took place. Examples of a local system process are starting and shutting down a database or changing database parameters.
3.5 Using the Critical and Warning Alert Reports
The alert reports are as follows:
See Also:
-
Section 2.12 for information about creating and configuring alerts
-
Section 2.13 for information about responding to an alert
3.5.1 About the Critical and Warning Alert Reports
The critical and warning alert reports track critical and warning alerts. An alert is raised when data in a single audit record matches a predefined alert rule condition. Alerts are grouped by associated source, by event category, and by the severity level of the alert (either warning or critical). You can create user-defined reports from these alerts; see Section 3.9.
3.6 Scheduling and Creating PDF Reports
This section contains:
3.6.1 About Scheduling and Creating PDF Reports
You can schedule reports to be sent to other users in PDF format. You can run the report immediately, or you can create or select a schedule to run the report at a later time. In addition to setting a time to run the report, you can create the following components for the report:
-
A retention time for the data to be used in the report. For example, if you schedule a report to run once a month but you only want that month's audit data in the report, then you can set a retention time to store the data for each month the report runs, and then discard the data after each month. This way, the report recipients always receives the most recent month of audit data.
-
A list of users who should be notified when the report runs. You can notify other users of the report and either send them a notification or the report in an e-mail attachment.
-
A list of auditors who must attest to the report. You can select one or more auditors, including yourself, to attest to the report.
-
Formatting for the report. You can design the title to include certain components, such as the category and report names. You also can control the header and footer text for the report, as well as the orientation of the report.
3.6.2 Scheduling and Creating a PDF Report
To schedule and create a PDF report:
-
Log in to the Oracle Audit Vault Console as a user who has been granted the
AV_AUDITORrole, as explained in Section 1.4.The Dashboard page appears.
-
Select the Audit Reports tab.
-
Access the Create or Schedule PDF Report page using one of the following methods:
-
Select the report from the Default Reports, Compliance Reports, Custom Reports, or Generated Reports secondary tab, and then click the Create PDF button.
-
Select the Audit Reports tab, and then select the Report Schedules secondary tab. Then click the Create button.
The Create or Schedule PDF Report page appears.
-
-
In the Create or Schedule PDF Report page, if you had selected the Report Schedules secondary tab, then under Create or Schedule PDF Report, first select the category and then select the name of the report from the Category Name and Report Name lists.
-
Under Schedule, select a time to run the report:
-
Immediately if you want to run the report right away.
-
Specify Schedule if you want to create a schedule to run the report. From here, select how often the report should be run, the report run time and date, and the time zone offset to reflect the time zone in which the report should appear.
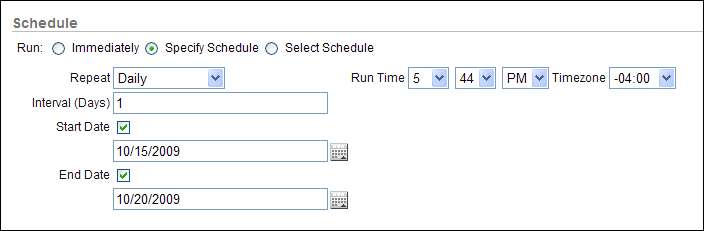
Description of the illustration create_sched.gif
-
Select Schedule if you want to select an existing schedule for the report. From here, select the schema in the Audit Vault Server database in which the schedule is stored, and the schedule name.
A database administrator can create this schedule by using the
DBMS_SCHEDULERPL/SQL package, assuming this user has theEXECUTEprivilege for this package. The Schema list displays schemas that containDBMS_SCHEDULERschedules. The Schedule list displays all theDBMS_SCHEDULERschedules in that schema. By default, Schema contains theSYSschema, which owns theDBMS_SCHEDULERpackage.
-
-
Under Retention, enter the retention period years and months to specify how long to keep the data in the report.
The retention period determines how long to keep the audit data in storage, based on times the report is run. For example, suppose you set the retention period to 6 months. Oracle Audit Vault will delete this audit data 6 months from the last time the report is run. If you specify the retention to be 0 years and 0 months, each night the reports clean up job deletes the PDF report. You can use this special 0 years, 0 months setting to create a PDF report for immediate viewing or printing.
-
Under Notification, select the following options, and then click Add to List to create a notification list:
-
For Send, select either Notification or Attachment. The Notification option sends the user an e-mail with a URL link to the report. The Attachment option attaches the PDF report to the user's e-mail.
-
From the Template list, select a report notification template.
-
From the Profile list, select a profile, which contains a list of default recipients who should receive the report.
-
If you want to send the report to additional recipients, enter their e-mail addresses in the To e-mail and Cc fields. Enter the full e-mail address. Separate multiple e-mail addresses with a comma.
-
-
Under Attestation, select one or more auditors who should attest to the report.
Optionally, you can set the order in which the auditors are listed in the Attestation area.
-
Under Report Formatting, specify the following:
-
For Title, select one or more of the following options: Category Name, Report Name, Generated Time, Filters, Timezone, and Custom. If you select Custom, then enter customized text for the report title.
-
For Header and Footer, select from these options: Report Name, Generated Time, Page #, and Custom Text. If you select Custom Text, then enter this text in the appropriate field. You can designate these elements to appear on the left, center, or right side of the page.
-
For Orientation, select either Portrait or Landscape.
-
-
Click the Create PDF button.
The PDF is stored in the database. To find and review the PDF, click the Generated Reports tab.
3.7 Annotating and Attesting Reports
This section contains:
3.7.1 About Annotating and Attesting Reports
After a report has been generated, auditors can annotate and attest to the report. This enables you to create a record of all notes and attestations for the report in one place, with the most recent note and attestation listed first. If you delete the report, its associated annotation and attestations are removed as well.
3.7.2 Annotating and Attesting a Report
To annotate and attest a report:
-
Log in to the Oracle Audit Vault Console as a user who has been granted the
AV_AUDITORrole, as explained in Section 1.4.The Dashboard page appears.
-
Access the list of reports to attest by using one of the following methods:
-
From the Dashboard page, select the number of the report from the Attestation Actions list.
-
Select the Audit Reports tab, and then select the Generated Reports secondary tab. Find the report that you want to annotate or attest and then click the report name. When you display the report, it appears in PDF format. Click the Details button to display the Details for Generated Report page.
You can quickly filter the reports if you want. See Section 3.9.3 for more information.
-
-
In the New Note field, enter a note for the report.
-
Perform one of the following actions:
-
To save the note only, click the Save button. The note appears in the Previous Notes area.
-
To save the note and attest to the report, click the Save & Attest button. The note appears in the Previous Notes area and the Attestation area is updated with your user name and the time that you attested to the report.
-
To return to the report, click the View Report button.
-
-
Click Done when you are finished.
The Generated Reports page appears.
3.8 Generating and Comparing Snapshots of Entitlement Audit Data
This section contains:
3.8.1 About Entitlement Report Snapshots and Labels
An entitlement snapshot captures the state of user entitlement information. The snapshot contains the metadata of users and roles that a user has to a database: system and other SQL privileges, object privileges, role privileges, and user profiles. Snapshots are created automatically whenever you retrieve the entitlement data, and only apply to Oracle Database source databases. Each snapshot is unique, and it is time-stamped in the following format:
MM/DD/YYYY HH:MM:SS AM/PM
The name for the snapshot is the time stamp assigned to it when the entitlement data was retrieved (for example, 9/22/2009 07:56:17 AM).
Each source database can only have one snapshot of a particular time stamp. In other words, you cannot have multiple snapshots entitled 9/22/2009 07:56:17 AM in one source database. If you retrieve entitlement audit data for all your source databases at the same time, then each source database gets its own 9/22/2009 07:56:17 AM snapshot.
Optionally, you can group snapshots from multiple source databases by assigning these snapshots to a label. For example, suppose the source databases payroll, sales, and hr each have a 9/22/2009 07:56:17 AM snapshot. You can create a label and then assign these three snapshots to that label. This enables you to compare the snapshot data from the three source databases at once, all in the same report.
You can filter a report to show the data from an earlier snapshot or label, or you can compare the audit data from two snapshots or two labels. This way, you can find changes that have occurred over time, from different entitlement audit data retrievals. For example, you can find how user privileges have been modified between two snapshots or labels.
The type of entitlement report determines whether you can view its audit data by snapshot or by label. The reports appended with "by Source" (for example, User Accounts by Source) provide snapshot data for specific source databases. The regular entitlement reports (such as User Accounts) enable you to view audit data across all the source databases or snapshots, based on a label.
3.8.2 General Steps for Using Entitlement Reports
The general steps that you must take to use entitlement reports are as follows:
-
Retrieve the entitlement audit data to create a snapshot.
See Section 3.8.3.
-
Optionally, organize the snapshots into a group and then assign them a label.
See Section 3.8.4.
-
Optionally, assign one or more snapshots to a label.
See Section 3.8.5.
-
View the entitlement snapshot and label data.
See Section 3.8.6. For a listing of entitlement reports, see Section 3.3.5.
3.8.3 Retrieving Entitlement Audit Data to Create the Snapshot
Each time you retrieve entitlement audit data, you create a snapshot.
To retrieve the entitlement audit data:
-
Log in to the Audit Vault Console as a user who has been granted the
AV_AUDITORrole.Section 1.4 explains how to start the Audit Vault Console. The Dashboard page appears.
-
In the Audit Vault Console, select the Audit Policy tab.
By default, the Audit Settings page appears.
-
From the Audit Source listing, select the check boxes for the source databases that you want.
To filter the list of audit sources, enter text in the Audit Source text field or click the flashlight icon to display the Search And Select: Audit Source page. If you make selections on the Search And Select: Audit Source page, when you return, the Audit Source column will be populated with your selections.
-
Select the User Entitlement option.
-
Click the Retrieve button.
Oracle Audit Vault displays a message letting you know that the user entitlement data is being retrieved. To check the status of the retrieval, click the Show Status button.
3.8.4 Creating an Entitlement Snapshot Label
If you want to organize the snapshots into a group, assign them to a label. The name LATEST is automatically assigned to the latest snapshot for each Oracle source database. Therefore, each source database has its own LATEST label for its most recent retrieval.
To create an entitlement snapshot label:
-
From the Home page, select the Audit Reports tab, and then select the Entitlement Snapshots tab.
-
Under Tasks, select Manage Snapshot Labels.
The Snapshot Labels page appears.
-
Click Create.
The Add Snapshot Label page appears.
-
Enter the following information:
-
Label Name: Enter a name for the label. Do not name the label
LATEST, which is a reserved word. Typically, label names are based on time, such as financial quarters. For example:Q1_2009
-
Description: Optionally, enter a brief description of the label. For example:
This label captures the snapshot 9/22/2009 07:56:17 AM data for the payroll, sales, and hr source databases.
-
-
Click Save.
The new label is listed in the Snapshot Labels page. From here, you can edit the label by selecting its name, or remove it by clicking the trash icon.
Later on, if you want to edit or remove a label, select Manage Snapshot Labels from the Entitlement Snapshots page. To edit the label, select the label name and then use the Edit Snapshot Label page to modify the label name and description. To remove the label, select its trash icon.
3.8.5 Assigning Snapshots to a Label
You only can assign one snapshot from each source database to a label.
To assign snapshots to a label:
-
From the Home page, select the Audit Reports tab, and then select the Entitlement Snapshots tab.
-
Select one or more source database snapshots to be assigned to a label.
-
Click the Assign Label button.
The Assign Label page appears. The following example shows two snapshots listed for a source database called
avsource.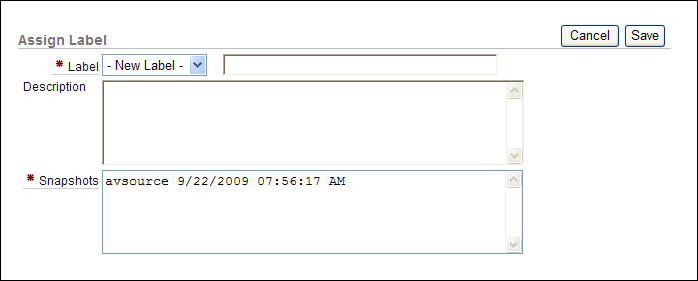
Description of the illustration assign_label.gif
-
Enter the following information:
-
Label: For a new label, enter the name in the Label field. To select an existing label, select the label name from the Label list.
-
Description: For a new label, optionally enter a brief description of the label.
-
Snapshots: Ensure that the snapshots listed are the correct snapshots. If they are incorrect, then click Cancel and then select the correct snapshots.
-
-
Click Save.
The label assignment appears in the Entitlement Snapshots page. From here, you can modify or move the label assignments for the snapshots.
3.8.6 Viewing Entitlement Snapshot and Label Audit Data
This section contains:
-
Checking Entitlement Reports for Individual Snapshot or Label Audit Data
-
Checking Entitlement Reports for Changes to Snapshot or Label Audit Data
3.8.6.1 About Viewing Entitlement Snapshot and Label Audit Data
After snapshots have been created and if you have created and assigned labels for them, then you are ready to check the entitlement reports.
3.8.6.2 Checking Entitlement Reports for Individual Snapshot or Label Audit Data
To check entitlement reports for individual snapshot or label audit data:
-
Log in to the Audit Vault Console as a user who has been granted the
AV_AUDITORrole.Section 1.4 explains how to start the Audit Vault Console. The Dashboard page appears.
-
Select the Audit Reports tab, and in the Default Reports page, under Entitlement Reports, select link for the entitlement report that you want.
-
In the entitlement report, do the following:
-
For a "by Source" report, from the Source list, select the source database for the snapshot that you want.
-
From the Snapshot or Label list, select the snapshot or label.
For example:
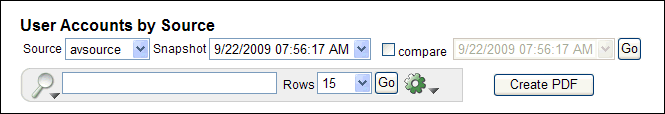
Description of the illustration snapshot_ind.gif
-
-
Click the Go button that is to the right of the compare list.
The entitlement report data appears. The generated report contains an additional column, either Snapshot or Label, indicating which snapshot or label was used for the report. From here, you can expand the Snapshot or Label column to filter its contents.
Figure 3-4 shows how the User Accounts by Source Report typically appears with generated snapshot audit data.
Figure 3-4 Showing Individual Snapshot or Label Audit Data
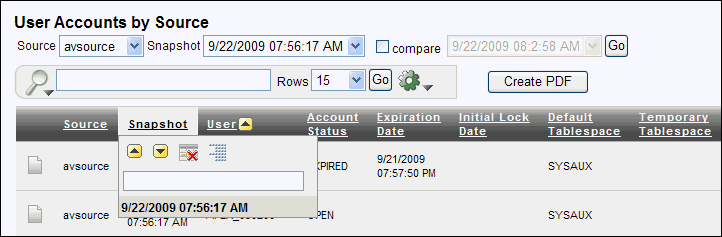
Description of "Figure 3-4 Showing Individual Snapshot or Label Audit Data"
3.8.6.3 Checking Entitlement Reports for Changes to Snapshot or Label Audit Data
To compare the audit data for two snapshots or labels:
-
Log in to the Audit Vault Console as a user who has been granted the
AV_AUDITORrole.Section 1.4 explains how to start the Audit Vault Console. The Dashboard page appears.
-
Select the Audit Reports tab, and in the Default Reports page, under Entitlement Reports, select the link for the entitlement report that you want.
-
In the report, do the following:
-
For a "by Source" report, from the Source list, select the source database for the snapshot that you want.
-
From the Snapshot or Label list, select the first snapshot or label.
-
Click the compare check box.
-
Select from the second snapshot or label list.
For example:
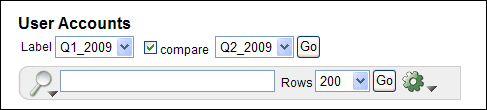
Description of the illustration snapshot1.gif
-
-
Click the Go button that is to the right of the compare list.
The entitlement report data appears. It contains an additional column entitled Change Category, and - Changes is appended to the name of the report. The Change Category column shows how the data has changed between the two snapshots or labels. From here, you can filter the data to show only MODIFIED, NEW, DELETED, or UNCHANGED data.
Figure 3-5 shows how the User Accounts - Changes Report typically appears with generated comparison data. No deletions have occurred in this label; otherwise, the Change Category column would include a DELETED category.
Figure 3-5 Comparing Entitlement Report Snapshot or Label Audit Data
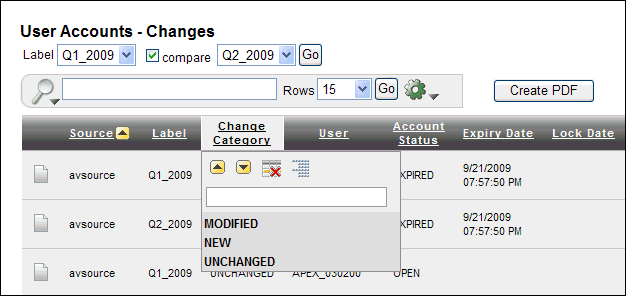
Description of "Figure 3-5 Comparing Entitlement Report Snapshot or Label Audit Data"
3.9 Controlling the Display of Data in a Report
-
Changing the Default Displayed Contents of a Compliance Report
-
Resetting the Report Display Values to Their Default Settings
See Also:
Section 3.8.6, which describes additional ways that you can view audit data in entitlement reports3.9.1 About Controlling the Display of Report Data
You can control the display of data in a default or user-defined report to focus on a particular set of data. Oracle Audit Vault automatically saves the report settings so that if you leave the page, the report settings are still in place when you return. Optionally, you can save the report to a user-defined report.
3.9.2 Hiding or Showing Columns in a Report
When you hide or show columns in a report, you still can perform operations on hidden columns, such as filtering data based on a column that you have hidden.
This section contains:
3.9.2.1 Hiding the Currently Selected Column
To hide the currently selected column:
-
In the report, select the column that you want to hide.
-
In the Column Heading menu, click the Hide Column button.
3.9.2.2 Hiding or Showing Any Column
To hide or show columns in a report:
-
Access the report that you want.
Section 3.2 explains how to access a report.
-
Select the Actions menu (gear) icon on the Search bar.
The Actions menu appears.
Description of the illustration actions_menu.gif
-
From the Actions menu, select Select Columns.
The Select Columns dialog field appears under the Search bar.
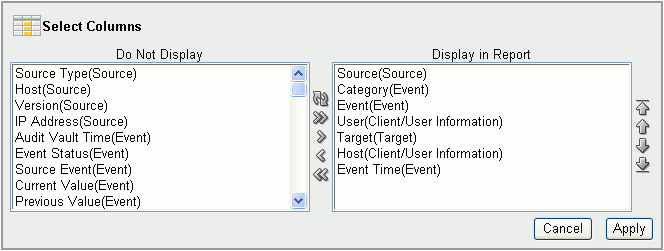
Description of the illustration select_cols.gif
-
To move column names between the Do Not Display and Display in Report boxes:
-
Select the column names to move and then click the left or right arrow between the column name boxes.
-
Move all columns left or right by using the >> and << buttons.
-
Use the top button (the arrows in a circle) to reset the columns to their original locations in the two boxes.
-
-
To set the order of appearance in the report for displayed columns, in the Display in Report box, select the column name, then click the up arrow or down arrow on the right side of the box to reorder its position in the list.
Report columns names are arranged in a report from left to right by their top-to-bottom order in the Display in Report box.
-
Click Apply.
3.9.3 Filtering Data in a Report
This section contains:
3.9.3.1 About Filtering Data in Reports
You can filter the report to show all rows based on a particular column, or a subset of of rows, using an expression.
If you must perform subquery, join, and AND SQL operations, you can create multiple filters as needed. For example, if you want to filter all SYS users who are being audited for the SUPER USER LOGON event, you would create one filter to catch all SYS users, and then a second filter to catch all SUPER USER LOGON events. If two or more of the filters for a report are enabled, then Oracle Audit Vault uses both or all of them (as in an AND operation). You can toggle specific filters on or off, depending on the results that you want.
See Also:
Section 3.9.4 for information about using filters to change the default definition of the contents of a compliance report3.9.3.2 Filtering All Rows Based on Data from the Currently Selected Column
This filtering method lets you filter data in all rows based on the currently selected column (for example, all rows that only contain SYS in the User column).
To filter all rows based on data from the current column:
-
Access the report that you want.
Section 3.2 explains how to access a report.
-
Under the report name, select the column that you want to use as a basis for the filter.
The Column Heading menu appears, showing the row data used in the selected column. For example, if you select the User column, it will list user names found in the source database for this column, such as users
APPS,OE, andSH.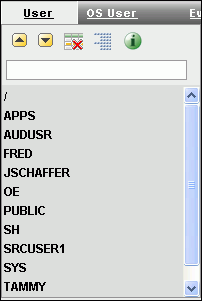
Description of the illustration filter_col.gif
-
In the Column Heading menu, select the row data on which you want to base the filter, or enter the row data item in the text area field.
For example, to show only rows for users
SYSandSYSTEM, select SYS and SYSTEM from the Column Heading menu. Oracle Audit Vault filters the display accordingly. The filter definitions for the current user session are added above the report columns.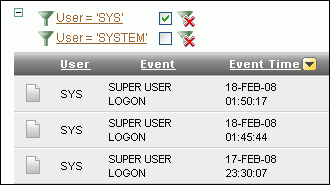
Description of the illustration filter_col2.gif
-
To enable or disable the display of the filtered data, select its corresponding check box. To remove a filter, click its Remove Filter icon.
3.9.3.3 Filtering Column and Row Data
You can use the Search bar to search for row data in one or all columns in the report (for example, all rows that contain the letters SYS, such as SYS and SYSTEM, in the User column).
To search for row data in one or all columns:
-
Access the report that you want.
Section 3.2 explains how to access a report.
-
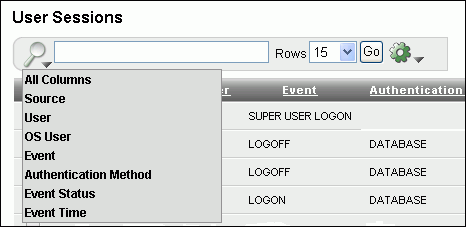
If you want to focus the search on a specific column, in the Search bar, use the Search icon to select from the list of available columns.
By default, Oracle Audit Vault searches all columns.
Description of the illustration filter_search.gif
-
In the Search bar text area, enter all or part of the text in the column row that you want.
For example, enter
SYSto find all user names that contain the lettersSYS.The search is not case-sensitive.
-
In the Rows list, select the number of rows that you want to appear on each page.
The default is 15 rows.
-
Click Go.
3.9.3.4 Filtering Row Data Using an Expression
This method lets you select all rows that meet a WHERE condition, such as all users who are not user SYS. You can create the expression for all columns in the source database table, even those that are not shown in the current report.
To filter row data using an expression:
-
Access the report that you want.
Section 3.2 explains how to access a report.
-
Select the Actions menu (gear) icon on the Search bar.
-
Select Filter.
The Filter dialog box appears under the Search bar.
-
Enter the following information:
-
Column: Select the name of the column from the list. Note that you can select all columns, including hidden columns.
-
Operator: Select a SQL operator from the list, for example, > for "greater than" or = for "equals."
-
Expression: Select an expression from the list. The expression lists the row data (for example, names of users found in the User column). If you type the expression in the Expression field, remember that the expression is case-sensitive. In most cases, use uppercase letters.
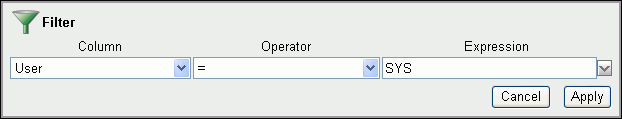
Description of the illustration filter_expr.gif
-
-
Click Apply.
Oracle Audit Vault filters the display of row data based on the expression you created, and then adds the filter definition before the report columns. From here, you can disable or enable the display of the filtered data, or remove the filter, if you want.
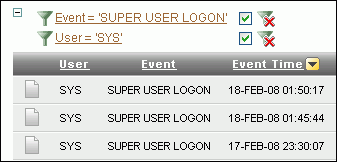
Description of the illustration filter_expr_mul.gif
3.9.4 Changing the Default Displayed Contents of a Compliance Report
Each compliance report has a hidden filter that controls the displayed contents of the default version of the report. You can display and then modify the definition of this filter if you want to customize the compliance report data. Alternatively, you can remove this filter and create new filters for further customization.
To change the definition of the default displayed contents of a compliance report:
-
Access the compliance report that you want.
Section 3.2 explains how to access a report.
-
Click the Change Definition button.
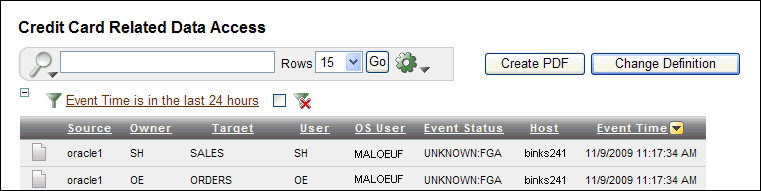
Description of the illustration change_definition.gif
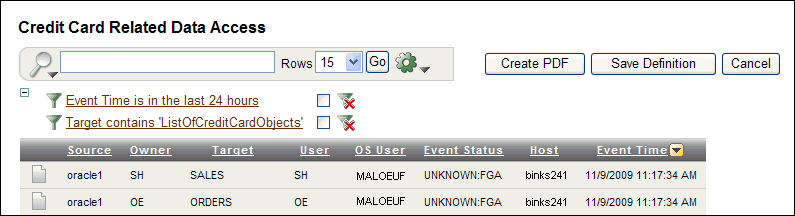
The report window changes to display the default, hidden filter for the compliance report. For example, for the Credit Card Related Data Access Report, this filter is ListOfCreditCardObjects.
Description of the illustration change_definition2.gif
-
Select the link for the hidden filter.
For the Credit Card Related Data Access Report, you would select the Target contains 'ListOfCreditCardObjects' link. Afterwards, the Filter region appears.
-
In the Filter region, modify the default filter definition.
See Section 3.9.3 for detailed information about filtering data in a report.
-
Click the Save Definition button.
3.9.5 Sorting Data in a Report
You can sort data in ascending or descending order for all columns at once, or sort data on a selected column.
This section contains:
3.9.5.1 Sorting Row Data for the Currently Selected Column
To sort row data for the current column:
-
Select the column on which you want to base the sort.
-
In the Column Heading menu, select either the Sort Ascending or Sort Descending icon.
3.9.5.2 Sorting Row Data for All Columns
To sort row data for all columns:
-
Access the report that you want.
Section 3.2 explains how to access a report.
-
Select the Actions menu (gear) icon on the Search bar.
-
In the Actions Menu, select Sort.
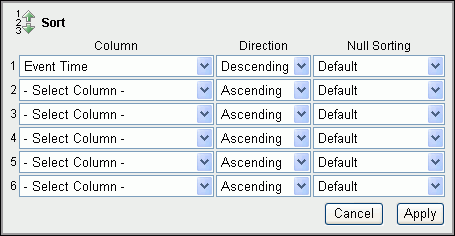
The Sort dialog box appears under the Search bar.
Description of the illustration sortrgb.gif
-
Enter the following information:
-
Column: For up to six columns, select the columns to sort. By default, the first sort column is Event Time, which is sorted in descending order.
-
Direction: Select either Ascending or Descending.
-
Null Sorting: Select the Null sorting rule for each column (Default, Nulls Always Last, or Nulls Always First). The default is to not sort nulls.
-
-
Click Apply.
3.9.6 Highlighting Rows in a Report
You can highlight specific rows in a report by assigning them colors. This enables anyone viewing the report to quickly find areas that are of particular interest.
To highlight rows in the report:
-
Access the report that you want.
Section 3.2 explains how to access a report.
-
Select the Actions menu (gear) icon on the Search bar.
-
In the Actions menu, select Highlight.
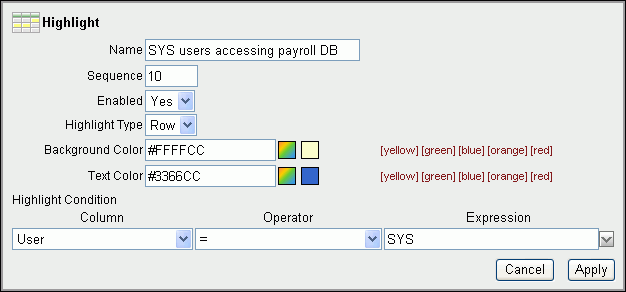
The Highlight dialog box appears under the Search bar.
-
Enter the following information:
-
Name: Enter a name for this highlight instance. (Optional)
-
Sequence: Enter a sequence number to determine the order in which the highlight filter rules are to be applied when two or more highlight filter rules are in effect. The default value is 10.
-
Enabled: Select Yes to enable the highlight or select No to disable it.
-
Highlight Type: Select Row to highlight a row or select Cell to highlight a cell.
-
Background Color: Select a background color for the row or cell. Click a color to display color options, or click the colored icon to the right of the color selection field to display a color selection box from which to choose a different color. Alternatively, you can manually enter the HTML code for a color.
-
Text Color: Select a text color for the row or cell using the same method you used for the background color. (Optional)
-
Highlight Condition: Edit the highlight filter rule expression by identifying the column, the operator, and the expression for each of the three fields in the highlight condition.
-
Column: Select any column name, including hidden columns.
-
Operator: Select an operator from a list of standard Oracle Database operators, such as
=,!=,NOT IN, andBETWEEN. -
Expression: Enter the comparison expression (without quotation marks) based on a known value for that column name to complete the filter expression. For example, entering the filter expression
EVENT=SUPER USER LOGONfilters for all values in the Event column that contain the valueSUPER USER LOGON.
-
Description of the illustration highlightrgb.gif
-
-
Click Apply.
3.9.7 Charting Data in a Report
You can select from four chart styles to chart data in a report. After you create the chart, you can access it whenever you access the report.
To chart data in a report:
-
Access the report that you want.
Section 3.2 explains how to access a report.
-
Select the Actions menu (gear) icon on the Search bar, and then select Chart.
The Chart dialog box appears under the Search bar.
-
Enter the following information:
-
Chart style: Select from one of the four chart styles: Horizontal Column, Vertical Column, Pie, and Line.
-
Label: Select from the list of columns for this report. You can include hidden columns as well as displayed columns.
-
Value: Select from the list of columns for this report, including hidden columns. If you select Count from the Function list, then you do not need to select a value.
-
Function: Select an aggregate function (Sum, Average, Minimum, Maximum, or Count) on which to aggregate the data values.
-
Sort: Select ascending or descending sorting for values and labels.
-
Axis Title for Label: Enter a name for the axis title.
-
Axis Title for Value: Enter a name for the axis value.
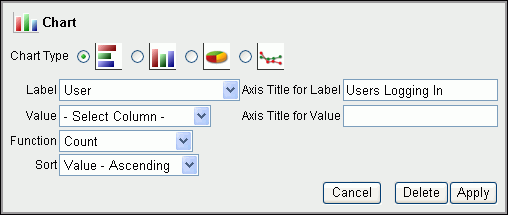
Description of the illustration chart.gif
-
-
Click Apply.
The chart appears, with the Edit Chart and View Report links under the Search bar. The following example displays a count of users who have logged in, clearly showing that user
JSCHAFFERhas been very, very busy.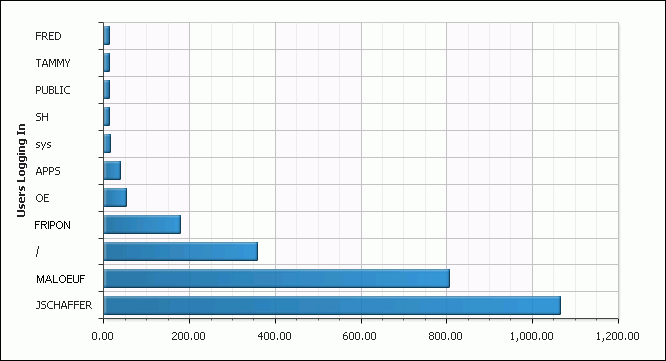
Description of the illustration charted_data.gif
3.9.8 Adding a Control Break to a Column in a Report
You can create a break group on the selected column. This pulls the column out of the report as a master record. A break group is a way of grouping all rows with the same value under a master record, thus creating groups of master records, with one master record for each column value. This is useful for filtering by multiple column values.
To add a control break in a column:
-
Access the report that you want.
Section 3.2 explains how to access a report.
-
Select the column to which you want to add a control break.
-
In the Column Heading menu, select the Control Break icon.
The control break is added to the column, and icons for enabling, disabling, and removing the control break are added before the column headings.
3.9.9 Resetting the Report Display Values to Their Default Settings
You can reset the report display values to their original default settings.
To reset the display settings to their defaults:
-
Access the report that you want.
Section 3.2 explains how to access a report.
-
Select the Actions menu (gear) icon on the Search bar, then select Reset.
3.10 Finding Information About Report Data
This section contains:
3.10.1 Finding Detailed Information About an Audit Record
You can find the following detailed information about an individual audit record: information about the source database, audited event, audited objects (such as tables or views), client/user information, the host computer on which the user is logged, audited SQL statements, the user session information, and miscellaneous information such as the audit record ID, instance number, and fine-grained audit policy name.
To find detailed information about an audit record:
-
Access the report that you want.
Section 3.2 explains how to access a report.
-
Use the methods described in Section 3.9 to find the audit record.
-
Select the Audit Record Details icon, which appears to the left of the first column in the report.
A detailed report for the audit record appears.
Description of the illustration single_row_view.gif
3.10.2 Finding Information About the Purpose of a Column
To find information about the purpose of a column:
-
Access the report that you want.
Section 3.2 explains how to access a report.
-
Select the column on which you want information.
-
In the Column Heading menu, select the Column Information icon.
3.11 Working with User-Defined Reports
This section contains:
3.11.1 About User-Defined Reports
You can create user-defined reports based on the default reports or other user-defined reports. You can create a category for the report independently or when you create the user-defined report.
3.11.2 Creating a Category for User-Defined Reports
Before you create a user-defined report, you may want to create a category in which to assign it. You can create and manage category names on the User-Defined Reports page.
This section contains:
3.11.2.1 Creating a Category Name
To create a category name for user-defined reports:
-
Under Tasks, click Manage Categories.
-
On the Categories page, click Create Category.
-
In the Category Name field, enter the name of the new category.
-
Click Create.
3.11.2.2 Alphabetizing the Category Name List
To alphabetize the category name list:
-
Click the Category Name column label name once.
This positions the direction pointer to point upward (category names appear in ascending order).
-
Click the Category Name column label name once again to position the direction pointer to point downward (category names appear in descending order).
3.11.2.3 Editing a Category Name
To edit a category name:
-
To edit a category name, click the Edit icon (pencil) to the left of the category name.
The Category page appears for the selected category name.
-
On the Category page, revise the category name by editing the text in the Category Name field.
-
Click Apply.
3.11.3 Creating a User-Defined Report
You can save the display settings that you have created to a user-defined report. User-defined reports are listed in the Custom Reports secondary tab of the Audit Reports tab. Oracle Audit Vault saves the report settings and makes the user-defined report available the next time you log in to Oracle Audit Vault.
When you save a user-defined report, you can save the report under a specific category that you select or create as you save the report. You can also make the user-defined report private or share it among other Oracle Audit Vault users as a public report.
To create a user-defined report:
-
Access the report that you want.
Section 3.2 explains how to access a report.
-
Use the methods described in Section 3.9 to design the display of data as needed.
-
Select the Actions menu (gear) icon on the Search bar, and then select Save Report.
The Save Report dialog box appears, under the Search bar.
-
Enter the following information:
-
Name: Enter a name for the report.
-
Category: Select from the list of available categories. If you select New Category, then enter a name for the new category.
If you must create a new category, see Section 3.11.2.
-
Description: Enter a brief description of the report.
-
Public: Select this check box to enable the report to be accessible to all Oracle Audit Vault users.
-
-
Click Apply.
3.11.4 Accessing a User-Defined Report
To access a user-defined report:
-
Log in to the Oracle Audit Vault Console as a user who has been granted the
AV_AUDITORrole, as explained in Section 1.4.The Dashboard page appears.
-
Select the Audit Reports tab, and then select the Custom Reports secondary tab.
-
In the Report Name column, select the link for the report that you want to access.
The report appears. Its report details icon and filter definitions appear after the Search bar. From here, you can click the Saved Report link to change the report settings, delete the report, or disable and enable the report filters.
Description of the illustration user_def_report.gif
3.12 Downloading a Report to a CSV File
You can download reports to a file that is in a comma-separated values (CSV) format. The CSV file format is a delimited data format with fields separated by the comma character and records separated by new-line characters.
To download a report to a CSV file:
-
Access the report that you want.
Section 3.2 explains how to access a report.
-
Select the Actions menu (gear) icon on the Search bar, and then select.
-
In the Download dialog box, select CSV.
-
In the File Download dialog box, enter a name for the file.
-
Click Save to save the file to a location in your file system.