Chapter 13 Mail Services (Tasks)
This chapter describes how to set up and administer mail services. If you are not familiar with administering mail services, read Chapter 12, Mail Services (Overview) for an introduction to the components of mail services. This chapter also provides a description of a typical mail service configuration, as shown in Figure 12–1. The following list can help you find groups of related procedures that are covered in this chapter.
See Chapter 14, Mail Services (Reference) for a more detailed description of the components of mail services. This chapter also describes the mail service programs and files, the mail routing process, the interactions of sendmail with name services, and the features in version 8.13 of sendmail that are not fully described in the sendmail(1M) man page.
Task Map for Mail Services
The following table refers you to other task maps that focus on a specific group of procedures.
|
Task |
Description |
For Instructions |
|---|---|---|
|
Setting up mail services |
Use these procedures to set up each component of your mail service. Learn how to set up a mail server, a mail client, a mail host, a mail gateway, and a virtual host. Learn how to use DNS with sendmail. | |
|
Building a sendmail configuration file |
Use this procedure to modify your sendmail.cf file. See an example of how to enable domain masquerading. | |
|
Setting SMTP to use Transport Layer Security (TLS) |
Use this procedure to enable SMTP to have secure connections with TLS. | |
|
Managing mail delivery with an alternate configuration |
Use this procedure to prevent mail delivery problems that can occur if the master daemon is disabled. | |
|
Administering mail alias files |
Use these procedures to provide aliasing on your network. Learn how to manage entries in NIS+ tables. Also, learn how to set up an NIS map, a local mail alias, a keyed map file, and a postmaster alias. | |
|
Administering the mail queue |
Use these procedures to provide smooth queue processing. Learn how to display and move the mail queue, force mail queue processing, and run a subset of the mail queue. Also, learn how to run the old mail queue. | |
|
Administering .forward files |
Use these procedures to disable .forward files or change the search path of the .forward file. Also, learn how to permit users to use the .forward file by creating and populating /etc/shells. | |
|
Troubleshooting procedures and tips for mail services |
Use these procedures and tips to resolve problems with your mail service. Learn how to test the mail configuration, check mail aliases, test the sendmail rule sets, verify connections to other systems, and log messages. Also, learn where to look for other mail diagnostic information. |
Troubleshooting Procedures and Tips for Mail Services (Task Map) |
|
Resolving error messages |
Use the information in this section to resolve some mail-related error messages. |
Planning Your Mail System
The following list describes some concerns that should be part of your planning process.
-
Determine the type of mail configuration that meets your requirements. This section describes two basic types of mail configuration and briefly lists what you need to set up each configuration. If you need to set up a new mail system or if you are expanding an existing one, you might find this section useful. Local Mail Only describes the first configuration type, and Local Mail and a Remote Connection describes the second type.
-
As necessary, choose the systems that are to act as mail servers, mail hosts, and mail gateways.
-
Make a list of all the mail clients for which you are providing service and include the location of their mailboxes. This list can help you when you are ready to create mail aliases for your users.
-
Decide how to update aliases and forward mail messages. You might set up an aliases mailbox as a place for users to send requests for mail forwarding. Users could also use this mailbox to send requests for changes to their default mail alias. If your system uses NIS or NIS+, you can administer mail forwarding, rather than requiring users to manage mail forwarding. Administering Mail Alias Files (Task Map) provides a list of tasks that are related to aliasing. Administering .forward Files (Task Map) provides a list of tasks that are related to managing .forward files.
After you have completed the planning process, set up the systems on your site to perform the functions that are described in Setting Up Mail Services (Task Map). For other task information, refer to Task Map for Mail Services.
Local Mail Only
The simplest mail configuration, as shown in Figure 13–1, is two or more workstations that are connected to one mail host. Mail is completely local. All the clients store mail on their local disks, and the clients act as mail servers. Mail addresses are parsed by using the /etc/mail/aliases files.
Figure 13–1 Local Mail Configuration
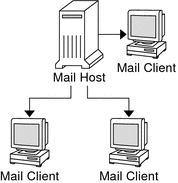
To set up this kind of mail configuration, you need the following.
-
The default /etc/mail/sendmail.cf file, which requires no editing, on each mail client system.
-
A server that is designated as the mail host. If you are running NIS or NIS+, you can make this designation by adding mailhost.domain-name to the /etc/hosts file on the mail host. If you are running another name service, such as DNS or LDAP, you must provide additional information in the /etc/hosts file. See How to Set Up a Mail Host.
-
If you are using a name service other than NIS or NIS+, you need matching /etc/mail/aliases files on any system that has a local mailbox.
-
Enough space in /var/mail on each mail client system to hold the mailboxes.
For task information about setting up your mail service, refer to Setting Up Mail Services. If you are looking for a particular procedure that is related to setting up your mail service, refer to Setting Up Mail Services (Task Map).
Local Mail and a Remote Connection
The most common mail configuration in a small network is shown in Figure 13–2. One system includes the mail server, the mail host, and the mail gateway that provides the remote connection. Mail is distributed by using the /etc/mail/aliases files on the mail gateway. No name service is required.
Figure 13–2 Local Mail Configuration With a UUCP Connection
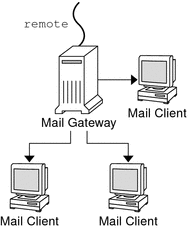
In this configuration, you can assume that the mail clients mount their mail files from /var/mail on the mail host. To set up this kind of mail configuration, you need the following.
-
The default /etc/mail/sendmail.cf file on each mail client system. This file does not require any editing.
-
A server that is designated as the mail host. If you are running NIS or NIS+, you can make this designation by adding mailhost.domain-name to the /etc/hosts file on the mail host. If you are running another name service, such as DNS or LDAP, you must provide additional information in the /etc/hosts file. See How to Set Up a Mail Host.
-
If you are using a name service other than NIS or NIS+, you need matching /etc/mail/aliases files on any system that has a local mailbox.
-
Enough space in /var/mail on the mail server to hold the client mailboxes.
For task information about setting up your mail service, refer to Setting Up Mail Services. If you are looking for a particular procedure that is related to setting up your mail service, refer to Setting Up Mail Services (Task Map).
Setting Up Mail Services (Task Map)
The following table describes the procedures for setting up mail services.
|
Task |
Description |
For Instructions |
|---|---|---|
|
Setting up a mail server |
Steps to enable a server to route mail | |
|
Setting up a mail client |
Steps to enable a user to receive mail | |
|
Setting up a mail host |
Steps to establish a mail host that can resolve email addresses | |
|
Setting up a mail gateway |
Steps to manage communication with networks outside your domain | |
|
Using DNS with sendmail |
Steps to enable DNS host lookups | |
|
Setting up a virtual host |
Steps to assign more than one IP address to a host |
Setting Up Mail Services
You can readily set up a mail service if your site does not provide connections to email services outside your company or if your company is in a single domain.
Mail requires two types of configurations for local mail. Refer to Figure 13–1 in Local Mail Only for a representation of these configurations. Mail requires two more configurations for communication with networks outside your domain. Refer to Figure 12–1 in Overview of the Hardware Components or Figure 13–2 in Local Mail and a Remote Connection for a representation of these configurations. You can combine these configurations on the same system or provide these configurations on separate systems. For example, if your mail host and mail server functions are on the same system, follow the directions in this section for setting up that system as a mail host. Then, follow the directions in this section for setting up the same system as a mail server.
Note –
The following procedures for setting up a mail server and mail client apply when mailboxes are NFS mounted. However, mailboxes typically are maintained in locally mounted /var/mail directories, which eliminates the need for the following procedures.
Refer to the following:
 How to Set Up a Mail Server
How to Set Up a Mail Server
No special steps are required to set up a mail server that is only serving mail for local users. The user must have an entry in the password file or in the namespace. Also, for mail to be delivered, the user should have a local home directory for checking the ~/.forward file. For this reason, home directory servers are often set up as the mail server. Hardware Components in Chapter 14, Mail Services (Reference) provides more information about the mail server.
The mail server can route mail for many mail clients. This type of mail server must have adequate spooling space for client mailboxes.
Note –
The mail.local program automatically creates mailboxes in the /var/mail directory the first time a message is delivered. You do not need to create individual mailboxes for your mail clients.
For clients to access their mailboxes, the /var/mail directory should be available for remote mounting. Alternately, a service such as Post Office Protocol (POP) or Internet Message Access Protocol (IMAP) should be available from the server. The following task shows you how to set up a mail server by using the /var/mail directory. To provide configuration guidelines for POP or IMAP is beyond the scope of this document.
For the following task, ensure that the /etc/dfs/dfstab file shows that the /var/mail directory is exported.
-
Become superuser or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Stop sendmail.
# svcadm disable -t network/smtp:sendmail
-
Check if the /var/mail directory is available for remote access.
# share
If the /var/mail directory is listed, proceed to step 5.
If the /var/mail directory is not listed or if no list appears, continue with the appropriate substep.
-
(Optional) If no list appears, start NFS services.
Follow the procedure, How to Set Up Automatic File-System Sharing, to use the /var/mail directory to start NFS services.
-
(Optional) If the /var/mail directory is not included in the list, add the directory to /etc/dfs/dfstab.
Add the following command line to the /etc/dfs/dfstab file.
share -F nfs -o rw /var/mail
-
-
Make the file system available for mounting.
# shareall
-
Ensure that your name service has been started.
-
(Optional) If you are running NIS, use this command.
# ypwhich
For more information, refer to the ypwhich(1) man page.
-
(Optional) If you are running NIS+, use this command.
# nisls
For more information, refer to the nisls(1) man page.
-
(Optional) If you are running DNS, use this command.
# nslookup hostname
- hostname
-
Use your host name.
For more information, refer to the nslookup(1M) man page.
-
(Optional) If you are running LDAP, use this command.
# ldaplist
For more information, refer to the ldaplist(1) man page.
-
-
Restart sendmail.
# svcadm enable network/smtp:sendmail
 How to Set Up a Mail Client
How to Set Up a Mail Client
A mail client is a user of mail services with a mailbox on a mail server. Additionally, the mail client has a mail alias in the /etc/mail/aliases file that points to the location of the mailbox.
Note –
You can also perform the task of setting up a mail client by using a service such as Post Office Protocol (POP) or Internet Message Access Protocol (IMAP). However, to provide configuration guidelines for POP or IMAP is beyond the scope of this document.
-
Become superuser on the mail client's system or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Stop sendmail.
# svcadm disable -t network/smtp:sendmail
-
Ensure that a /var/mail mount point exists on the mail client's system.
The mount point should have been created during the installation process. You can use ls to ensure that the file system exists. The following example shows the response that you receive if the file system has not been created.
# ls -l /var/mail /var/mail not found
-
Ensure that no files are in the /var/mail directory.
If mail files do exist in this directory, you should move them so that they are not covered when the /var/mail directory is mounted from the server.
-
Mount the /var/mail directory from the mail server.
You can mount the mail directory automatically or at boot time.
-
(Optional) Mount /var/mail automatically.
Add an entry such as the following to the /etc/auto_direct file.
/var/mail -rw,hard,actimeo=0 server:/var/mail
- server
-
Use the assigned server name.
-
(Optional) Mount /var/mail at boot time.
Add the following entry to the /etc/vfstab file. This entry permits the /var/mail directory on the mail server that is specified to mount the local /var/mail directory.
server:/var/mail - /var/mail nfs - no rw,hard,actimeo=0
The client's mailbox is automatically mounted whenever the system is rebooted. If you are not rebooting the system, type the following command to mount the client mailbox.
# mountall
 Caution –
Caution – For mailbox locking and mailbox access to work properly, you must include the actimeo=0 option when mounting mail from an NFS server.
-
-
Update /etc/hosts.
Edit the /etc/hosts file and add an entry for the mail server. This step is not required if you are using a name service.
# cat /etc/hosts # # Internet host table # .. IP-address mailhost mailhost mailhost.example.com
- IP-address
-
Use the assigned IP addresses.
- example.com
-
Use the assigned domain.
- mailhost
-
Use the assigned mailhost.
For more information, refer to the hosts(4) man page.
-
Add an entry for the client to one of the alias files.
Refer to Administering Mail Alias Files (Task Map) for a task map about administering mail alias files. Note that the mail.local program automatically creates mailboxes in the /var/mail directory the first time a message is delivered. You do not need to create individual mailboxes for your mail clients.
-
Restart sendmail.
# svcadm enable network/smtp:sendmail
 How to Set Up a Mail Host
How to Set Up a Mail Host
A mail host resolves email addresses and reroutes mail within your domain. A good candidate for a mail host is a system that provides your network with a remote connection or connects your network to a parent domain. The following procedure shows you how to set up a mail host.
-
Become superuser on the mail host system or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Stop sendmail.
# svcadm disable -t network/smtp:sendmail
-
Verify the host-name configuration.
Run the check-hostname script to verify that sendmail can identify the fully qualified host name for this server.
% /usr/sbin/check-hostname hostname phoenix OK: fully qualified as phoenix.example.com
If this script is not successful in identifying the fully qualified host name, you need to add the fully qualified host name as the first alias for the host in /etc/hosts.
-
Update the /etc/hosts file.
Choose the step that is appropriate for you.
-
(Optional) If you are using NIS or NIS+, edit the /etc/hosts file on the system that is to be the new mail host.
Add the word mailhost and mailhost.domain after the IP address and system name of the mail host system.
IP-address mailhost mailhost mailhost.domain loghost
- IP-address
-
Use the assigned IP address.
- mailhost
-
Use the system name of the mail host system.
- domain
-
Use the expanded domain name.
The system is now designated as a mail host. The domain should be identical to the string that is given as the subdomain name in the output of the following command.
% /usr/lib/sendmail -bt -d0 </dev/null Version 8.13.1+Sun Compiled with: LDAPMAP MAP_REGEX LOG MATCHGECOS MIME7TO8 MIME8TO7 NAMED_BIND NDBM NETINET NETINET6 NETUNIX NEWDB NIS NISPLUS QUEUE SCANF SMTP USERDB XDEBUG ============ SYSTEM IDENTITY (after readcf) ============ (short domain name) $w = phoenix (canonical domain name) $j = phoenix.example.com (subdomain name) $m = example.com (node name) $k = phoenix ========================================================See the following example of how the hosts file should look after these changes.
# cat /etc/hosts # # Internet host table # 172.31.255.255 localhost 192.168.255.255 phoenix mailhost mailhost.example.com loghost
-
(Optional) If you are not using NIS or NIS+, edit the /etc/hosts file on each system in the network. Create the following entry.
IP-address mailhost mailhost mailhost.domain loghost
-
-
Restart sendmail.
# svcadm enable network/smtp:sendmail
-
Test your mail configuration.
See How to Test the Mail Configuration for instructions.
Note –For further information about mail hosts, refer to Hardware Components in Chapter 14, Mail Services (Reference).
 How to Set Up a Mail Gateway
How to Set Up a Mail Gateway
A mail gateway manages communication with networks outside your domain. The mailer on the sending mail gateway can match the mailer on the receiving system.
A good candidate for a mail gateway is a system that is attached to Ethernet and phone lines. Another good candidate is a system that is configured as a router to the Internet. You can configure the mail host or another system as the mail gateway. You might choose to configure more than one mail gateway for your domain. If you have UNIX-to-UNIX Copy Program (UUCP) connections, you should configure the system (or systems) with UUCP connections as the mail gateway.
-
Become superuser on the mail gateway or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Stop sendmail.
# svcadm disable -t network/smtp:sendmail
-
Verify the host-name configuration.
Run the check-hostname script to verify that sendmail can identify the fully qualified host name for this server.
# /usr/sbin/check-hostname hostname phoenix OK: fully qualified as phoenix.example.com
If this script is not successful in identifying the fully qualified host name, you need to add the fully qualified host name as the first alias for the host in /etc/hosts. If you need help with this step, refer to Step 4 of How to Set Up a Mail Host.
-
Ensure that your name service has been started.
-
(Optional) If you are running NIS, use this command.
# ypwhich
For more information, refer to the ypwhich(1) man page.
-
(Optional) If you are running NIS+, use this command.
# nisls
For more information, refer to the nisls(1) man page.
-
(Optional) If you are running DNS, use this command.
# nslookup hostname
- hostname
-
Use your host name.
For more information, refer to the nslookup(1M) man page.
-
(Optional) If you are running LDAP, use this command.
# ldaplist
For more information, refer to the ldaplist(1) man page.
-
-
Restart sendmail.
# svcadm enable network/smtp:sendmail
-
Test your mail configuration.
See How to Test the Mail Configuration for instructions.
Note –For more information about the mail gateway, refer to Hardware Components in Chapter 14, Mail Services (Reference).
 How to Use DNS With sendmail
How to Use DNS With sendmail
The DNS name service does not support aliases for individuals. This name service does support aliases for hosts or domains that use Mail Exchanger (MX) records and CNAME records. You can specify host names, domain names, or both names in the DNS database. For more information about sendmail and DNS, see Interactions of sendmail With Name Services in Chapter 14, Mail Services (Reference), or see the System Administration Guide: Naming and Directory Services (DNS, NIS, and LDAP).
-
Become superuser or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Enable DNS host lookups (NIS+ only).
Edit the /etc/nsswitch.conf file and remove the # from the hosts definition that includes the dns flag. The host entry must include the dns flag, as the following example shows, in order for the DNS host aliases to be used.
# grep hosts /etc/nsswitch.conf #hosts: nisplus [NOTFOUND=return] files hosts: dns nisplus [NOTFOUND=return] files
-
Check for a mailhost and mailhost.domain entry.
Use nslookup to ensure that an entry exists for mailhost and mailhost.domain in the DNS database. For more information, refer to the nslookup(1M) man page.
Setting Up a Virtual Host
If you need to assign more than one IP address to a host, see this Web site: http://www.sendmail.org/tips/virtual-hosting.php. This site provides complete instructions about how to use sendmail to set up a virtual host. However, in the “Sendmail Configuration” section, do not perform step 3b, as shown in the following.
# cd sendmail-VERSION/cf/cf # ./Build mailserver.cf # cp mailserver.cf /etc/mail/sendmail.cf |
Instead, for the Solaris operating system, perform the following steps.
# cd /etc/mail/cf/cf # make mailserver.cf # cp mailserver.cf /etc/mail/sendmail.cf |
- mailserver
-
Use the name of the .cf file.
Building the sendmail.cf Configuration File outlines the same three steps as part of the build process.
After you have generated your /etc/mail/sendmail.cf file, you can continue with the next steps to create a virtual user table.
Building the sendmail.cf Configuration File
How to Build a New sendmail.cf File shows you how to build the configuration file. Although you can still use older versions of sendmail.cf files, the best practice is to use the new format.
For more details, refer to the following.
-
/etc/mail/cf/README provides a complete description of the configuration process.
-
http://www.sendmail.org provides online information about sendmail configuration.
-
Versions of the Configuration File and sendmail Configuration File, in Chapter 14, Mail Services (Reference), provide some guidance.
-
Additional and Revised m4 Configuration Macros From Version 8.12 of sendmail is also helpful.
 How to Build a New sendmail.cf File
How to Build a New sendmail.cf File
The following procedure shows you how to build a new configuration file.
Note –
/usr/lib/mail/cf/main-v7sun.mc is now /etc/mail/cf/cf/main.mc.
-
Become superuser or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Stop sendmail.
# svcadm disable -t network/smtp:sendmail
-
Make a copy of the configuration files that you are changing.
# cd /etc/mail/cf/cf # cp sendmail.mc myhost.mc
- myhost
-
Select a new name for your .mc file.
-
Edit the new configuration files (for example, myhost.mc), as necessary.
For example, add the following command line to enable domain masquerading.
# cat myhost.mc .. MASQUERADE_AS(`host.domain')
- host.domain
-
Use the desired host name and domain name.
In this example, MASQUERADE_AS causes sent mail to be labeled as originating from host.domain, rather than $j.
-
Build the configuration file by using m4.
# make myhost.cf
-
Test the new configuration file by using the -C option to specify the new file.
# /usr/lib/sendmail -C myhost.cf -v testaddr </dev/null
While this command displays messages, it sends a message to testaddr. Only outgoing mail can be tested without restarting the sendmail service on the system. For systems that are not handling mail yet, use the full testing procedure in How to Test the Mail Configuration.
-
Install the new configuration file after making a copy of the original.
# cp /etc/mail/sendmail.cf /etc/mail/sendmail.cf.save # cp myhost.cf /etc/mail/sendmail.cf
-
Restart the sendmail service.
# svcadm enable network/smtp:sendmail
Setting SMTP to Use TLS
Starting in the Solaris 10 1/06 release, SMTP can use Transport Layer Security (TLS) in version 8.13 of sendmail. This service to SMTP servers and clients provides private, authenticated communications over the Internet, as well as protection from eavesdroppers and attackers. Note that this service is not enabled by default.
 How to Set SMTP to Use TLS
How to Set SMTP to Use TLS
The following procedure uses sample data to show you how to set up the certificates that enable sendmail to use TLS. For more information, see Support for Running SMTP With TLS in Version 8.13 of sendmail.
-
Become superuser or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Stop sendmail.
# svcadm disable -t network/smtp:sendmail
-
Set up the certificates that enable sendmail to use TLS.
-
Complete the following:
# cd /etc/mail # mkdir -p certs/CA # cd certs/CA # mkdir certs crl newcerts private # echo "01" > serial # cp /dev/null index.txt # cp /etc/sfw/openssl/openssl.cnf .
-
Use your preferred text editor to change the dir value in the openssl.cnf file from /etc/sfw/openssl to /etc/mail/certs/CA.
-
Use the openssl command-line tool to implement TLS.
Note that the following command line generates interactive text.
# openssl req -new -x509 -keyout private/cakey.pem -out cacert.pem -days 365 \ -config openssl.cnf Generating a 1024 bit RSA private key .....................................++++++ .....................................++++++ writing new private key to 'private/cakey.pem' Enter PEM pass phrase: Verifying - Enter PEM pass phrase: ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) []:US State or Province Name (full name) []:California Locality Name (eg, city) []:Menlo Park Organization Name (eg, company) [Unconfigured OpenSSL Installation]:Sun Microsystems Organizational Unit Name (eg, section) []:Solaris Common Name (eg, YOUR name) []:somehost.somedomain.example.com Email Address []:someuser@example.com
- req
-
This command creates and processes certificate requests.
- -new
-
This req option generates a new certificate request.
- -x509
-
This req option creates a self-signed certificate.
- -keyout private/cakey.pem
-
This req option enables you to assign private/cakey.pem as the file name for your newly created private key.
- -out cacert.pem
-
This req option enables you to assign cacert.pem as your output file.
- -days 365
-
This req option enables you to certify the certificate for 365 days. The default value is 30.
- -config openssl.cnf
-
This req option enables you to specify openssl.cnf as the configuration file.
Note that this command requires that you provide the following:
-
Country Name, such as US.
-
State or Province Name, such as California.
-
Locality Name, such as Menlo Park.
-
Organization Name, such as Sun Microsystems.
-
Organizational Unit Name, such as Solaris.
-
Common Name, which is the machine's fully qualified host name. For more information, see the check-hostname(1M) man page.
-
Email Address, such as someuser@example.com.
-
-
(Optional) If you need a new secure connection, make a new certificate and sign the new certificate with the certificate authority.
-
Make a new certificate.
# cd /etc/mail/certs/CA # openssl req -nodes -new -x509 -keyout newreq.pem -out newreq.pem -days 365 \ -config openssl.cnf Generating a 1024 bit RSA private key ..............++++++ ..............++++++ writing new private key to 'newreq.pem' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) []:US State or Province Name (full name) []:California Locality Name (eg, city) []:Menlo Park Organization Name (eg, company) [Unconfigured OpenSSL Installation]:Sun Microsystems Organizational Unit Name (eg, section) []:Solaris Common Name (eg, YOUR name) []:somehost.somedomain.example.com Email Address []:someuser@example.com
This command requires that you provide the same information that you provided in step 3c.
Note that in this example, the certificate and private key are in the file newreq.pem.
-
Sign the new certificate with the certificate authority.
# cd /etc/mail/certs/CA # openssl x509 -x509toreq -in newreq.pem -signkey newreq.pem -out tmp.pem Getting request Private Key Generating certificate request # openssl ca -config openssl.cnf -policy policy_anything -out newcert.pem -infiles tmp.pem Using configuration from openssl.cnf Enter pass phrase for /etc/mail/certs/CA/private/cakey.pem: Check that the request matches the signature Signature ok Certificate Details: Serial Number: 1 (0x1) Validity Not Before: Jun 23 18:44:38 2005 GMT Not After : Jun 23 18:44:38 2006 GMT Subject: countryName = US stateOrProvinceName = California localityName = Menlo Park organizationName = Sun Microsystems organizationalUnitName = Solaris commonName = somehost.somedomain.example.com emailAddress = someuser@example.com X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: 93:D4:1F:C3:36:50:C5:97:D7:5E:01:E4:E3:4B:5D:0B:1F:96:9C:E2 X509v3 Authority Key Identifier: keyid:99:47:F7:17:CF:52:2A:74:A2:C0:13:38:20:6B:F1:B3:89:84:CC:68 DirName:/C=US/ST=California/L=Menlo Park/O=Sun Microsystems/OU=Solaris/\ CN=someuser@example.com/emailAddress=someuser@example.com serial:00 Certificate is to be certified until Jun 23 18:44:38 2006 GMT (365 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated # rm -f tmp.pemIn this example the file newreq.pem contains the unsigned certificate and private key. The file newcert.pem contains the signed certificate.
- x509 utility
-
Displays certificate information, converts certificates to various forms, and signs certificate requests
- ca application
-
Used to sign certificate requests in a variety of forms and to generate CRLs (certificate revocation lists)
-
-
Enable sendmail to use the certificates by adding the following lines to your .mc file.
define(`confCACERT_PATH', `/etc/mail/certs')dnl define(`confCACERT', `/etc/mail/certs/CAcert.pem')dnl define(`confSERVER_CERT', `/etc/mail/certs/MYcert.pem')dnl define(`confSERVER_KEY', `/etc/mail/certs/MYkey.pem')dnl define(`confCLIENT_CERT', `/etc/mail/certs/MYcert.pem')dnl define(`confCLIENT_KEY', `/etc/mail/certs/MYkey.pem')dnl
For more information, see Configuration File Options for Running SMTP With TLS.
-
Rebuild and install your sendmail.cf file in your /etc/mail directory.
For detailed instructions, see Building the sendmail.cf Configuration File.
-
Create symbolic links from the files you created with openssl to the files you defined in your .mc file.
# cd /etc/mail/certs # ln -s CA/cacert.pem CAcert.pem # ln -s CA/newcert.pem MYcert.pem # ln -s CA/newreq.pem MYkey.pem
-
For added security, deny read permission to group and others for MYkey.pem.
# chmod go-r MYkey.pem
-
Use a symbolic link to install CA certs in the directory assigned to confCACERT_PATH.
# C=CAcert.pem # ln -s $C `openssl x509 -noout -hash < $C`.0
-
For secure mail with other hosts, install their host certificates.
-
Copy the file defined by the other host's confCACERT option to /etc/mail/certs/host.domain.cert.pem.
Replace host.domain with the other host's fully qualified host name.
-
Use a symbolic link to install CA certs in the directory assigned to confCACERT_PATH.
# C=host.domain.cert.pem # ln -s $C `openssl x509 -noout -hash < $C`.0
Replace host.domain with the other host's fully qualified host name.
-
-
Restart sendmail.
# svcadm enable network/smtp:sendmail
Example 13–1 Received: Mail Header
The following is an example of a Received: header for secure mail with TLS.
Received: from his.example.com ([IPv6:2001:db8:3c4d:15::1a2f:1a2b])
by her.example.com (8.13.4+Sun/8.13.4) with ESMTP id j2TNUB8i242496
(version=TLSv1/SSLv3 cipher=DHE-RSA-AES256-SHA bits=256 verify=OK)
for <janepc@her.example.com>; Tue, 29 Mar 2005 15:30:11 -0800 (PST)
Received: from her.example.com (her.city.example.com [192.168.0.0])
by his.example.com (8.13.4+Sun/8.13.4) with ESMTP id j2TNU7cl571102
version=TLSv1/SSLv3 cipher=DHE-RSA-AES256-SHA bits=256 verify=OK)
for <janepc@her.example.com>; Tue, 29 Mar 2005 15:30:07 -0800 (PST)
|
Note that the value for verify is OK, which means that the authentication was successful. For more information, see Macros for Running SMTP With TLS.
See Also
The following OpenSSL man pages:
Managing Mail Delivery by Using an Alternate Configuration
To facilitate the transport of inbound mail and outbound mail, the new default configuration of sendmail uses a daemon and a client queue runner. If you have disabled your daemon, you should perform the following task. For a detailed explanation, refer to submit.cf Configuration File From Version 8.12 of sendmail.
 How to Manage Mail Delivery by Using an Alternate
Configuration of sendmail.cf
How to Manage Mail Delivery by Using an Alternate
Configuration of sendmail.cf
In the default configuration of sendmail, the client queue runner must be able to submit mail to the daemon on the local SMTP port. If the daemon is not listening on the SMTP port, the mail remains in the queue. To avoid this problem, perform the following task. For more information about the daemon and client queue runner and to understand why you might have to use this alternate configuration, refer to submit.cf Configuration File From Version 8.12 of sendmail.
This procedure ensures that your daemon runs only to accept connections from the local host.
-
Become superuser or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Stop sendmail.
# svcadm disable -t network/smtp:sendmail
-
Make a copy of the configuration file that you are changing.
# cd /etc/mail/cf/cf # cp sendmail.mc myhost.mc
- myhost
-
Select a new name for your .mc file.
-
Edit the new configuration file (for example, myhost.mc).
Add the following line before the MAILER() lines.
# cat myhost.mc .. FEATURE(`no_default_msa')dnl DAEMON_OPTIONS(`NAME=NoMTA4, Family=inet, Addr=127.0.0.1')dnl DAEMON_OPTIONS(`Name=MSA4, Family=inet, Addr=127.0.0.1, Port=587, M=E')dnl
Note –Use these configuration macros on machines that only have configured addresses for IPv4.
-
(Optional) If your host has an IPv6 local host address that is enabled, edit the new configuration file as follows.
Add the following lines before the MAILER() lines.
# cat myhost.mc .. FEATURE(`no_default_msa')dnl DAEMON_OPTIONS(`NAME=NoMTA4, Family=inet, Addr=127.0.0.1')dnl DAEMON_OPTIONS(`Name=MSA4, Family=inet, Addr=127.0.0.1, Port=587, M=E')dnl DAEMON_OPTIONS(`NAME=NoMTA6, Family=inet6, Addr=::1')dnl DAEMON_OPTIONS(`Name=MSA6, Family=inet6, Addr=::1, Port=587, M=E')dnl
 Caution –
Caution – To add these configuration macros, you must have configured addresses for IPv4 and IPv6.
-
(Optional) To see if your host has an IPv6 local host address that is enabled, run the following command.
# /usr/sbin/ifconfig -a
If IPv6 is enabled, you should see output that is similar to the following.
lo0: flags=2000849<UP,LOOPBACK,RUNNING,MULTICAST,IPv6> mtu 8252 index 1 inet6 ::1/128
-
-
Build the configuration file by using m4.
# make myhost.cf
-
Install the new configuration file after making a copy of the original.
# cp /etc/mail/sendmail.cf /etc/mail/sendmail.cf.save # cp myhost.cf /etc/mail/sendmail.cf
-
Restart the sendmail service.
# svcadm enable network/smtp:sendmail
Administering Mail Alias Files (Task Map)
The following table describes the procedures for administering mail alias files. For more information about this topic, refer to Mail Alias Files in Chapter 14, Mail Services (Reference).
|
Task |
Description |
For Instructions |
|---|---|---|
|
Managing alias entries in an NIS+ mail_aliases table |
If your name service is NIS+, use these procedures to manage the contents of your mail_aliases table. Initiate an NIS+ mail_aliases table. | |
|
List the contents of the NIS+ mail_aliases table. This procedure includes examples of how to list individual entries and how to list partial matches. | ||
|
Add aliases to the NIS+ mail_aliases table from the command line. |
How to Add Aliases to the NIS+ mail_aliases Table From the Command Line |
|
|
Add entries by editing an NIS+ mail_aliases table. | ||
|
Edit entries in an NIS+ mail_aliases table. This procedure includes an example of how to delete an entry. | ||
|
Setting up an NIS mail.aliases map |
If your name service is NIS, follow these instructions to facilitate aliasing with a mail.aliases map. | |
|
Setting up a local mail alias file |
If you are not using a name service (such as NIS or NIS+), follow these instructions to facilitate aliasing with the /etc/mail/aliases file. | |
|
Creating a keyed map file |
Use these steps to facilitate aliasing with a keyed map file. | |
|
Setting up the postmaster alias |
Use the procedures in this section to manage the postmaster alias. You must have this alias. |
Administering Mail Alias Files
Mail aliases must be unique within the domain. This section provides the procedures for administering mail alias files. Alternately, you can use the Mailing List feature in the Solaris Management Console to perform these tasks on the aliases database.
In addition, you can create database files for the local mail host by using makemap. Refer to the makemap(1M) man page. The use of these database files does not provide all of the advantages of using a name service such as NIS or NIS+. However, you should be able to retrieve the data from these local database files faster because no network lookups are involved. For more information, refer to Interactions of sendmail With Name Services and Mail Alias Files in Chapter 14, Mail Services (Reference).
Choose from the following procedures:
 How to Initiate an NIS+ mail_aliases Table
How to Initiate an NIS+ mail_aliases Table
You can use the aliasadm command to manage entries in an NIS+ table. To create a table, follow these instructions. For more information, refer to the aliasadm(1M) man page.
-
Either be a member of the NIS+ group that owns the table, or become root on the mail server, or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Initiate an NIS+ table.
# aliasadm -I
-
Add entries to the table.
-
To add two or three aliases, refer to How to Add Aliases to the NIS+ mail_aliases Table From the Command Line.
-
To add more than two or three aliases, refer to How to Add Entries by Editing an NIS+ mail_aliases Table.
-
 How to List the Contents of the NIS+ mail_aliases Table
How to List the Contents of the NIS+ mail_aliases Table
To see a complete list of the contents of the table, follow these instructions.
-
Either be a member of the NIS+ group that owns the table, or become root on the mail server, or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
List all of the entries in alphabetical order by alias.
# aliasadm -1
For more information, refer to the aliasadm(1M) man page.
Example 13–2 Listing an Individual Entry From the NIS+ mail_aliases Table
Alternately, you can use the aliasadm command to list individual entries. After you complete the first step in this procedure, type the following:
# aliasadm -m ignatz ignatz: ignatz@saturn # Alias for Iggy Ignatz |
The command matches only the complete alias name, not partial strings. You cannot use metacharacters, such as * and ?, with aliasadm -m.
Example 13–3 Listing Partial Matches From the NIS+ mail_aliases Table
Also, you can use the aliasadm command to list partial matches. After you complete the first step in this procedure, type the following:
# aliasadm -l | grep partial-string |
Replace partial-string with the desired string for your search.
 How to Add Aliases to the NIS+ mail_aliases Table From the Command Line
How to Add Aliases to the NIS+ mail_aliases Table From the Command Line
To add two or three aliases to the table, follow the following instructions. If you are adding more than two or three aliases, see How to Add Entries by Editing an NIS+ mail_aliases Table.
-
Compile a list of each of your mail clients, the locations of their mailboxes, and the names of the mail server systems.
-
Either be a member of the NIS+ group that owns the table, or become root on the mail server, or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
(Optional) If necessary, initiate an NIS+ table.
If you are creating a completely new NIS+ mail_aliases table, you must first initiate the table. To complete this task, refer to How to Initiate an NIS+ mail_aliases Table.
-
Add aliases to the table.
See this example of a typical entry.
# aliasadm -a iggy iggy.ignatz@saturn "Iggy Ignatz"
The following list describes the input from the preceding example.
- -a
-
The option for adding an alias
- iggy
-
The short form of the alias name
- iggy.ignatz@saturn
-
The expanded alias name
- "Iggy Ignatz"
-
The name for the alias in quotation marks
-
Display the entry that you created and ensure that the entry is correct.
# aliasadm -m alias
- alias
-
The entry that you created
For more information, refer to the aliasadm(1M) man page.
 How to Add Entries by Editing an NIS+ mail_aliases Table
How to Add Entries by Editing an NIS+ mail_aliases Table
You can use the aliasadm command to manage entries in an NIS+ table. To add more than two or three aliases to the table, follow these instructions.
-
Compile a list of each of your mail clients, the locations of their mailboxes, and the names of the mail server systems.
-
Either be a member of the NIS+ group that owns the table, or become root on the mail server, or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Display and edit the aliases table.
# aliasadm -e
This command displays the table and enables you to edit the table. The editor that you use has been set with the $EDITOR environment variable. If this variable is not set, vi is the default editor.
-
Use the following format to type each alias on a separate line.
alias: expanded-alias # ["option" # "comments"]
- alias
-
This column is for the short form of the alias name.
- expanded-alias
-
This column is for the expanded alias name.
- option
-
This column is reserved for future use.
- comments
-
This column is used for comments about the individual alias, such as a name for the alias.
If you leave the option column blank, type an empty pair of quotation marks ("") and add the comments.
The order of the entries is not important to the NIS+ mail_aliases table. The aliasadm -l command sorts the list and displays the entries in alphabetical order.
For more information, refer to Mail Alias Files and the aliasadm(1M) man page.
 How to Edit Entries in an NIS+ mail_aliases Table
How to Edit Entries in an NIS+ mail_aliases Table
To edit entries in the table, follow these instructions.
-
Either be a member of the NIS+ group that owns the table, or become root on the mail server, or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Display the alias entry.
# aliasadm -m alias
Replace alias with the assigned alias name.
-
Edit the alias entry, as necessary.
# aliasadm -c alias expanded-alias [options comments]
- alias
-
If necessary, edit the alias name.
- expanded-alias
-
If necessary, edit the expanded alias name.
- options
-
If necessary, edit the option.
- comments
-
If necessary, edit the comment for this entry.
For more information, refer to the aliasadm(1M) man page, as well as Mail Alias Files.
-
Display the entry that you have edited and ensure that the entry is correct.
# aliasadm -m alias
For more information, refer to the aliasadm(1M) man page.
Example 13–4 Deleting Entries From an NIS+ mail_aliases Table
To delete entries from the table, use the following syntax after you complete the first step in this procedure:
# aliasadm -d alias |
Replace alias with the alias name for the entry that you are deleting.
 How to Set Up an NIS mail.aliases Map
How to Set Up an NIS mail.aliases Map
Use the following procedure to facilitate aliasing with an NIS mail.aliases map.
-
Compile a list of each of your mail clients, the locations of their mailboxes, and the names of the mail server systems.
-
Become root on the NIS master server or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Edit the /etc/mail/aliases file, and make the following entries.
-
Add an entry for each mail client.
# cat /etc/mail/aliases .. alias:expanded-alias
- alias
-
Use the short alias name.
- expanded-alias
-
Use the expanded alias name (user@host.domain.com).
-
Ensure that you have a Postmaster: root entry.
# cat /etc/mail/aliases .. Postmaster: root
-
Add an alias for root. Use the mail address of the person who is designated as the postmaster.
# cat /etc/mail/aliases .. root: user@host.domain.com
- user@host.domain.com
-
Use the assigned address of the designated postmaster.
-
-
Ensure that the NIS master server is running a name service to resolve the host names on each mail server.
-
Change to the /var/yp directory.
# cd /var/yp
-
Apply the make command.
# make
The changes in the /etc/hosts and /etc/mail/aliases files are propagated to NIS slave systems. The changes are active in only a few minutes, at most.
 How to Set Up a Local Mail Alias File
How to Set Up a Local Mail Alias File
Use the following procedure to resolve aliases with a local mail alias file.
-
Compile a list of each of your users and the locations of their mailboxes.
-
Become root on the mail server or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Edit the /etc/mail/aliases file and make the following entries.
-
Add an entry for each user.
user1: user2@host.domain
- user1
-
Use the new alias name.
- user2@host.domain
-
Use the actual address for the new alias.
-
Ensure that you have a Postmaster: root entry.
# cat /etc/mail/aliases .. Postmaster: root
-
Add an alias for root. Use the mail address of the person who is designated as the postmaster.
# cat /etc/mail/aliases .. root: user@host.domain.com
- user@host.domain.com
-
Use the assigned address of the designated postmaster.
-
-
Rebuild the alias database.
# newaliases
The configuration of the AliasFile option in /etc/mail/sendmail.cf determines whether this command generates in binary form either the single file, /etc/mail/aliases.db, or the pair of files, /etc/mail/aliases.dir and /etc/mail/aliases.pag.
-
Perform one of the following steps to copy the file or files that were generated.
-
(Optional) Copy the /etc/mail/aliases, the /etc/mail/aliases.dir, and the/etc/mail/aliases.pag files to each of the other systems.
You can copy the three files by using the rcp or rdist commands. Refer to the rcp(1) man page or the rdist(1) man page for more information. Alternately, you can create a script for this purpose.
When you copy these files, you do not need to run the newaliases command on each of the other systems. However, remember that you must update all the /etc/mail/aliases files each time you add or remove a mail client.
-
(Optional) Copy the /etc/mail/aliases and the /etc/mail/aliases.db files to each of the other systems.
You can copy these files by using the rcp or rdist commands. Refer to the rcp(1) man page or the rdist(1) man page for more information. Alternately, you can create a script for this purpose.
When you copy these files, you do not need to run the newaliases command on each of the other systems. However, remember that you must update all the /etc/mail/aliases files each time you add or remove a mail client.
-
 How to Create a Keyed Map File
How to Create a Keyed Map File
To create a keyed map file, follow these instructions.
-
Become superuser or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Entries can have the following syntax.
old-name@newdomain.com new-name@newdomain.com old-name@olddomain.com error:nouser No such user here @olddomain.com %1@newdomain.com
- old_name@newdomain.com
-
Use the user name that was previously assigned with the domain that is newly assigned.
- new_name@newdomain.com
-
Use the address that is newly assigned.
- old_name@olddomain.com
-
Use the user name that was previously assigned with the domain that was previously assigned.
- olddomain.com
-
Use the domain that was previously assigned.
- newdomain.com
-
Use the domain that is newly assigned.
The first entry redirects mail to a new alias. The next entry creates a message when an incorrect alias is used. The last entry redirects all incoming mail from olddomain to newdomain.
-
Create the database file.
# /usr/sbin/makemap maptype newmap < newmap
- maptype
-
Select a database type, such as dbm, btree, or hash.
- newmap
-
Use the name of the input file and the first part of the name of the database file. If the dbm database type is selected, then the database files are created by using a .pag and a .dir suffix. For the other two database types, the file name is followed by .db.
Managing the postmaster Alias
Every system must be able to send mail to a postmaster mailbox. You can create an NIS or NIS+ alias for postmaster, or you can create the alias in each local /etc/mail/aliases file. Refer to these procedures.
-
How to Create a postmaster Alias in Each Local /etc/mail/aliases File
-
How to Add the postmaster Mailbox to the Aliases in the /etc/mail/aliases File
 How to Create a postmaster Alias
in Each Local /etc/mail/aliases File
How to Create a postmaster Alias
in Each Local /etc/mail/aliases File
If you are creating the postmaster alias in each local /etc/mail/aliases file, follow these instructions.
-
Become superuser or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
View the /etc/mail/aliases entry.
# cat /etc/mail/aliases # Following alias is required by the mail protocol, RFC 2821 # Set it to the address of a HUMAN who deals with this system's # mail problems. Postmaster: root
-
Edit each system's /etc/mail/aliases file.
Change root to the mail address of the person who is designated as the postmaster.
Postmaster: mail-address
- mail-address
-
Use the assigned address for the person who is designated as the postmaster.
-
(Optional) Create a separate mailbox for the postmaster.
You can create a separate mailbox for the postmaster to keep postmaster mail separate from personal mail. If you create a separate mailbox, use the mailbox address instead of the postmaster's personal mail address when you edit the /etc/mail/aliases files. For details, refer to How to Create a Separate Mailbox for postmaster.
 How to Create a Separate Mailbox for postmaster
How to Create a Separate Mailbox for postmaster
If you are creating a separate mailbox for postmaster, follow these instructions.
-
Become superuser or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Create a user account for the person who is designated as postmaster. Put an asterisk (*) in the password field.
For details about adding a user account, refer to Chapter 5, Managing User Accounts and Groups (Tasks), in System Administration Guide: Basic Administration.
-
After mail has been delivered, enable the mail program to read and write to the mailbox name.
# mail -f postmaster
- postmaster
-
Use the assigned address.
 How to Add the postmaster Mailbox
to the Aliases in the /etc/mail/aliases File
How to Add the postmaster Mailbox
to the Aliases in the /etc/mail/aliases File
If you are adding a postmaster mailbox to the aliases in the /etc/mail/aliases file, follow these instructions.
-
Become superuser or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Add an alias for root. Use the mail address of the person who is designated as the postmaster.
# cat /etc/mail/aliases .. root: user@host.domain.com
- user@host.domain.com
-
Use the assigned address of the person who is designated as postmaster.
-
On the postmaster's local system, create an entry in the /etc/mail/aliases file that defines the name of the alias. sysadmin is an example. Also, include the path to the local mailbox.
# cat /etc/mail/aliases .. sysadmin: /usr/somewhere/somefile
- sysadmin
-
Create a name for a new alias.
- /usr/somewhere/somefile
-
Use the path to the local mailbox.
-
Rebuild the alias database.
# newaliases
Administering the Queue Directories (Task Map)
The following table describes the procedures for administering the mail queue.
|
Task |
Description |
For Instructions |
|---|---|---|
|
Displaying the contents of the mail queue, /var/spool/mqueue |
Use this procedure to see how many messages are in the queue and how fast the messages are being cleared from the queue. |
How to Display the Contents of the Mail Queue, /var/spool/mqueue |
|
Forcing mail queue processing for the mail queue, /var/spool/mqueue |
Use this procedure to process messages to a system that previously was unable to receive messages. |
How to Force Mail Queue Processing in the Mail Queue, /var/spool/mqueue |
|
Running a subset of the mail queue, /var/spool/mqueue |
Use this procedure to force a substring of an address, such as a host name, to be processed. Also, use this procedure to force a particular message out of the queue. | |
|
Moving the mail queue, /var/spool/mqueue |
Use this procedure to move the mail queue. | |
|
Running the old mail queue, /var/spool/omqueue |
Use this procedure to run an old mail queue. |
Administering the Queue Directories
This section describes some helpful tasks for queue administration. For information about the client-only queue, refer to submit.cf Configuration File From Version 8.12 of sendmail. For other related information, you can refer to Additional Queue Features From Version 8.12 of sendmail.
Refer to the following:
-
How to Display the Contents of the Mail Queue, /var/spool/mqueue
-
How to Force Mail Queue Processing in the Mail Queue, /var/spool/mqueue
 How to Display the Contents of the Mail Queue, /var/spool/mqueue
How to Display the Contents of the Mail Queue, /var/spool/mqueue
-
Show how many messages are in the queue and how fast they are being cleared from the queue.
Type the following:
# /usr/bin/mailq | more
This command provides the following information.
-
The queue IDs
-
The size of the message
-
The date that the message entered the queue
-
The message status
-
The sender and the recipients
Additionally, this command now checks for the authorization attribute, solaris.admin.mail.mailq. If the check is successful, the equivalent of specifying the -bp flag with sendmail is executed. If the check fails, an error message is printed. By default, this authorization attribute is enabled for all users. The authorization attribute can be disabled by modifying the user entry in prof_attr. For more information, refer to the man pages for prof_attr(4) and mailq(1).
-
 How to Force Mail Queue Processing in the
Mail Queue, /var/spool/mqueue
How to Force Mail Queue Processing in the
Mail Queue, /var/spool/mqueue
Use this procedure, for example, to process messages to a system that was previously unable to receive messages.
-
Become superuser or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Force queue processing and display the progress of the jobs as the queue is cleared.
# /usr/lib/sendmail -q -v
 How to Run a Subset of the Mail Queue, /var/spool/mqueue
How to Run a Subset of the Mail Queue, /var/spool/mqueue
Use this procedure, for example, to force a substring of an address, such as a host name, to be processed. Also, use this procedure to force a particular message from the queue.
-
Become superuser or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Run a subset of the mail queue at any time with -qRstring.
# /usr/lib/sendmail -qRstring
- string
-
Use a recipient's alias or a substring of user@host.domain, such as a host name.
Alternately, you can run a subset of the mail queue with -qInnnnn.
# /usr/lib/sendmail -qInnnnn
- nnnnn
-
Use a queue ID.
 How to Move the Mail Queue, /var/spool/mqueue
How to Move the Mail Queue, /var/spool/mqueue
If you are moving the mail queue, follow these instructions.
-
Become root on the mail host or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Kill the sendmail daemon.
# svcadm disable network/smtp:sendmail
Now sendmail is no longer processing the queue directory.
-
Change to the /var/spool directory.
# cd /var/spool
-
Move the directory, mqueue, and all its contents to the omqueue directory. Then create a new empty directory that is named mqueue.
# mv mqueue omqueue; mkdir mqueue
-
Set the permissions of the directory to read/write/execute by owner, and read/execute by group. Also, set the owner and group to daemon.
# chmod 750 mqueue; chown root:bin mqueue
-
Start sendmail.
# svcadm enable network/smtp:sendmail
 How to Run the Old Mail Queue, /var/spool/omqueue
How to Run the Old Mail Queue, /var/spool/omqueue
To run an old mail queue, follow these instructions.
-
Become root or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Run the old mail queue.
# /usr/lib/sendmail -oQ/var/spool/omqueue -q
The -oQ flag specifies an alternate queue directory. The -q flag says to run every job in the queue. Use the -v flag if you are displaying the verbose output on the screen.
-
Remove the empty directory.
# rmdir /var/spool/omqueue
Administering .forward Files (Task Map)
The following table describes the procedures for administering .forward files. For more information, refer to .forward Files in Chapter 14, Mail Services (Reference).
|
Task |
Description |
For Instructions |
|---|---|---|
|
Disabling .forward files |
Use this procedure if, for example, you want to prevent automated forwarding. | |
|
Changing the .forward file search path |
Use this procedure if, for example, you want to move all .forward files into a common directory. | |
|
Creating and populating /etc/shells |
Use this procedure to enable users to use the .forward file to forward mail to a program or to a file. |
Administering .forward Files
This section contains several procedures that are related to .forward file administration. Because these files can be edited by users, the files can cause problems. For more information, refer to .forward Files in Chapter 14, Mail Services (Reference).
Refer to the following:
 How to Disable .forward Files
How to Disable .forward Files
This procedure, which prevents automated forwarding, disables the .forward file for a particular host.
-
Become superuser or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Make a copy of /etc/mail/cf/domain/solaris-generic.m4 or your site-specific domain m4 file.
# cd /etc/mail/cf/domain # cp solaris-generic.m4 mydomain.m4
-
Add the following line to the file that you just created.
define(`confFORWARD_PATH',`')dnl
If a value for confFORWARD_PATH already exists in the m4 file, replace the value with this null value.
-
Build and install a new configuration file.
If you need help with this step, refer to How to Build a New sendmail.cf File.
Note –When you edit the .mc file, remember to change DOMAIN(`solaris-generic') to DOMAIN(`mydomain').
 How to Change the .forward–File
Search Path
How to Change the .forward–File
Search Path
If, for example, you want to put all .forward files in a common directory, follow these instructions.
-
Become superuser or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Make a copy of /etc/mail/cf/domain/solaris-generic.m4 or your site-specific domain m4 file.
# cd /etc/mail/cf/domain # cp solaris-generic.m4 mydomain.m4
-
Add the following line to the file that you just created.
define(`confFORWARD_PATH',`$z/.forward:/var/forward/$u')dnl
If a value for confFORWARD_PATH already exists in the m4 file, replace the value with this new value.
-
Build and install a new configuration file.
If you need help with this step, refer to How to Build a New sendmail.cf File.
Note –When you edit the .mc file, remember to change DOMAIN(`solaris-generic') to DOMAIN(`mydomain').
 How to Create and Populate /etc/shells
How to Create and Populate /etc/shells
This file is not included in the standard release. You must add the file if users are to be allowed to use .forward files to forward mail to a program or to a file. You can create the file manually by using grep to identify all of the shells that are listed in your password file. You can then type the shells into the file. However, the following procedure, which employs a script that can be downloaded, is easier to use.
-
Download the script.
-
Become root or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services. To configure a role with the Primary Administrator profile, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
To generate a list of shells, run the gen-etc-shells script.
# ./gen-etc-shells.sh > /tmp/shells
This script uses the getent command to collect the names of shells that are included in the password file sources that are listed in /etc/nsswitch.conf.
-
Inspect and edit the list of shells in /tmp/shells.
With the editor of your choice, remove any shells that you are not including.
-
Move the file to /etc/shells.
# mv /tmp/shells /etc/shells
Troubleshooting Procedures and Tips for Mail Services (Task Map)
The following table describes troubleshooting procedures and tips for mail services.
|
Task |
Description |
For Instructions |
|---|---|---|
|
Testing mail configuration |
Steps for testing changes to the sendmail configuration file | |
|
Checking mail aliases |
A step to confirm that mail can or cannot be delivered to a specified recipient | |
|
Testing the rule sets |
Steps for checking the input and returns of the sendmail rule sets | |
|
Verifying connections to other systems |
Tips for verifying connections to other systems | |
|
Logging messages by using the syslogd program |
Tips for gathering error message information | |
|
Checking other sources for diagnostic information |
Tips for getting diagnostic information from other sources |
Troubleshooting Procedures and Tips for Mail Services
This section provides some procedures and tips that you can use for troubleshooting problems with mail services.
 How to Test the Mail Configuration
How to Test the Mail Configuration
To test the changes that you make to your configuration file, follow these instructions.
-
Restart sendmail on any system that has a revised configuration file.
# svcadm refresh network/smtp:sendmail
-
Send test messages from each system.
# /usr/lib/sendmail -v names </dev/null
- names
-
Specify a recipient's email address.
This command sends a null message to the specified recipient and displays the message activity on your monitor.
-
Send mail to yourself or other people on the local system by addressing the message to a regular user name.
-
(Optional) If you are connected to a network, send mail in three directions to someone on another system.
-
From the main system to a client system
-
From a client system to the main system
-
From a client system to another client system
-
-
(Optional) If you have a mail gateway, send mail from the mail host to another domain to ensure that the relay mailer and host are configured properly.
-
(Optional) If you have set up a UUCP connection on your phone line to another host, send mail to someone at that host. Have that person send mail back or call you when the message is received.
-
Ask someone to send mail to you over the UUCP connection.
The sendmail program cannot detect whether the message is delivered because the program passes the message to UUCP for delivery.
-
From different systems, send a message to postmaster and ensure that the message is delivered to your postmaster's mailbox.
How to Check Mail Aliases
The following example shows you how to verify an alias.
% mconnect connecting to host localhost (127.0.0.1), port 25 connection open 220 your.domain.com ESMTP Sendmail 8.13.6+Sun/8.13.6; Tue, 12 Sep 2004 13:34:13 -0800 (PST) expn sandy 250 2.1.5 <sandy@phoenix.example.com> quit 221 2.0.0 your.domain.com closing connection % |
In this example, the mconnect program opened a connection to a mail server on a local host and enabled you to test that connection. The program runs interactively, so you can issue various diagnostic commands. For a complete description, see the mconnect(1) man page. The entry, expn sandy, provided the expanded address, sandy@phoenix.example.com. Thus, you have verified that mail can be delivered when using the alias sandy.
Remember to avoid loops and inconsistent databases when both local and domain-wide aliases are used. Be especially careful to avoid the creation of alias loops when you move a user from one system to another system.
 How to Test the sendmail Rule
Sets
How to Test the sendmail Rule
Sets
To check the input and returns of the sendmail rule sets, follow these instructions.
-
Change to address test mode.
# /usr/lib/sendmail -bt
-
Test a mail address.
Provide the following numbers and address at the last prompt (>).
> 3,0 mail-sraddress
- mail-address
-
Use the mail address that you are testing.
-
End the session.
Press Control-d.
Example 13–5 Address Test Mode Output
The following is an example of the output from the address test mode.
% /usr/lib/sendmail -bt
ADDRESS TEST MODE (ruleset 3 NOT automatically invoked)
Enter <ruleset> <address>
> 3,0 sandy@phoenix
canonify input: sandy @ phoenix
Canonify2 input: sandy < @ phoenix >
Canonify2 returns: sandy < @ phoenix . example . com . >
canonify returns: sandy < @ phoenix . example . com . >
parse input: sandy < @ phoenix . example . com . >
Parse0 input: sandy < @ phoenix . example . com . >
Parse0 returns: sandy < @ phoenix . example . com . >
ParseLocal input: sandy < @ phoenix . example . com . >
ParseLocal returns: sandy < @ phoenix . example . com . >
Parse1 input: sandy < @ phoenix . example . com . >
MailerToTriple input: < mailhost . phoenix . example . com >
sandy < @ phoenix . example . com . >
MailerToTriple returns: $# relay $@ mailhost . phoenix . example . com
$: sandy < @ phoenix . example . com . >
Parse1 returns: $# relay $@ mailhost . phoenix . example . com
$: sandy < @ phoenix . example . com . >
parse returns: $# relay $@ mailhost . phoenix . example . com
$: sandy < @ phoenix . example . com . >
|
How to Verify Connections to Other Systems
The mconnect program opens a connection to a mail server on a host that you specify and enables you to test that connection. The program runs interactively, so you can issue various diagnostic commands. See the mconnect(1) man page for a complete description. The following example verifies that mail to the user name sandy is deliverable.
% mconnect phoenix connecting to host phoenix (172.31.255.255), port 25 connection open 220 phoenix.example.com ESMTP Sendmail 8.13.1+Sun/8.13.1; Sat, 4 Sep 2004 3:52:56 -0700 expn sandy 250 2.1.5 <sandy@phoenix.example.com> quit |
If you cannot use mconnect to connect to an SMTP port, check these conditions.
-
Is the system load too high?
-
Is the sendmail daemon running?
-
Does the system have the appropriate /etc/mail/sendmail.cf file?
-
Is port 25, the port that sendmail uses, active?
Logging Error Messages
Your mail service logs most error messages by using the syslogd program. By default, the syslogd program sends these messages to a system that is called loghost, which is specified in the /etc/hosts file. You can define loghost to hold all logs for an entire NIS domain. If no loghost is specified, error messages from syslogd are not reported.
The /etc/syslog.conf file controls where the syslogd program forwards messages. You can change the default configuration by editing the /etc/syslog.conf file. You must restart the syslog daemon for any changes to become active. To gather information about mail, you can add the following selections to the file.
-
mail.alert – Messages about conditions that should be fixed now
-
mail.crit – Critical messages
-
mail.warning – Warning messages
-
mail.notice – Messages that are not errors, but might need attention
-
mail.info – Informational messages
-
mail.debug – Debugging messages
The following entry in the /etc/syslog.conf file sends a copy of all critical, informational, and debug messages to /var/log/syslog.
mail.crit;mail.info;mail.debug /var/log/syslog |
Each line in the system log contains a timestamp, the name of the system that generated the line, and a message. The syslog file can log a large amount of information.
The log is arranged in a succession of levels. At the lowest level, only unusual occurrences are logged. At the highest level, even the most mundane and uninteresting events are recorded. As a convention, log levels under 10 are considered “useful.” Log levels that are higher than 10 are usually used for debugging. See Customizing System Message Logging in System Administration Guide: Advanced Administration for information about loghost and the syslogd program.
Other Sources for Mail Diagnostic Information
For other diagnostic information, check the following sources.
-
Look at the Received lines in the header of the message. These lines trace the route that the message took as the message was relayed. Remember to consider time–zone differences.
-
Look at the messages from MAILER-DAEMON. These messages typically report delivery problems.
-
Check the system log that records delivery problems for your group of systems. The sendmail program always records its activities in the system log. You might want to modify the crontab file to run a shell script nightly. The script searches the log for SYSERR messages and mails any messages that it finds to the postmaster.
-
Use the mailstats program to test mail types and determine the number of incoming messages and outgoing messages.
Resolving Error Messages
This section describes how you can resolve some sendmail–related error messages. You can also refer to http://www.sendmail.org/faq/.
The following error messages contain two or more of the following types of information.
-
Cause: What might have happened to cause the message
-
Description: What the user was doing when the error message occurred
-
Solution: What you can do to fix the problem or to continue with your work
451 timeout waiting for input during source
Cause:When sendmail reads from any source that might time out, such as an SMTP connection, the program sets a timer to the value of various Timeout options before reading begins. If the read is not completed before the timer expires, this message appears and reading stops. Usually, this situation occurs during RCPT. The mail message is then queued for later delivery.
Solution:If you see this message often, increase the value of various Timeout options in the /etc/mail/sendmail.cf file. If the timer is already set to a large number, look for hardware problems, such as poor network cabling or connections.
550 hostname... Host unknown
Cause:This sendmail message indicates that the destination host machine, which is specified by the portion of the address after the at sign (@), was not found during domain name system (DNS) lookup.
Solution:Use the nslookup command to verify that the destination host exists in that domain or other domains, perhaps with a slightly different spelling. Otherwise, contact the intended recipient and ask for a proper address.
550 username... User unknown
Cause:This sendmail message indicates that the intended recipient, who is specified by the portion of the address before the at sign (@), could not be located on the destination host machine.
Solution:Check the email address and try again, perhaps with a slightly different spelling. If this remedy does not work, contact the intended recipient and ask for a proper address.
554 hostname... Local configuration error
Cause:This sendmail message usually indicates that the local host is trying to send mail to itself.
Solution:Check the value of the $j macro in the /etc/mail/sendmail.cf file to ensure that this value is a fully qualified domain name.
Description:When the sending system provides its host name to the receiving system in the SMTP HELO command, the receiving system compares its name to the sender's name. If these names are the same, the receiving system issues this error message and closes the connection. The name that is provided in the HELO command is the value of the $j macro.
For additional information, refer to http://www.sendmail.org/faq/section4.html#4.5.
config error: mail loops back to myself.
Cause:This error message occurs if you set up an MX record and make host bar the mail exchanger for domain foo. However, you fail to configure host bar to know that it is the mail exchanger for domain foo.
Also, another possibility is that both the sending system and the receiving system are identifying as the same domain.
Solution:For instructions, refer to http://www.sendmail.org/faq/section4.html#4.5.
host name configuration error
Description:This is an old sendmail message, which replaced I refuse to talk to myself and is now replaced by the Local configuration error message.
Solution:Follow the instructions that were provided for resolving this error message, 554 hostname... Local configuration error.
user unknown
Cause:When you try to send mail to a user, the error Username... user unknown is displayed. The user is on the same system.
Solution:Check for a typographical error in the entered email address. Otherwise, the user could be aliased to a nonexistent email address in /etc/mail/aliases or in the user's .mailrc file. Also, check for uppercase characters in the user name. Preferably, email addresses should not be case sensitive.
For additional information, refer to http://www.sendmail.org/faq/section4.html#4.17.
- © 2010, Oracle Corporation and/or its affiliates
