IPsec Packet Flow
Figure 18–1 shows how an IP addressed packet, as part of an IP datagram, proceeds when IPsec has been invoked on an outbound packet. The flow diagram illustrates where authentication header (AH) and encapsulating security payload (ESP) entities can be applied to the packet. How to apply these entities, as well as how to choose the algorithms, are described in subsequent sections.
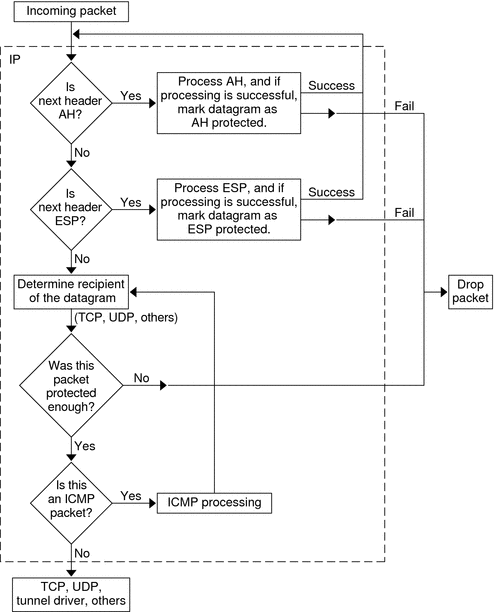
Figure 18–2 shows the IPsec inbound process.
Figure 18–1 IPsec Applied to Outbound Packet Process
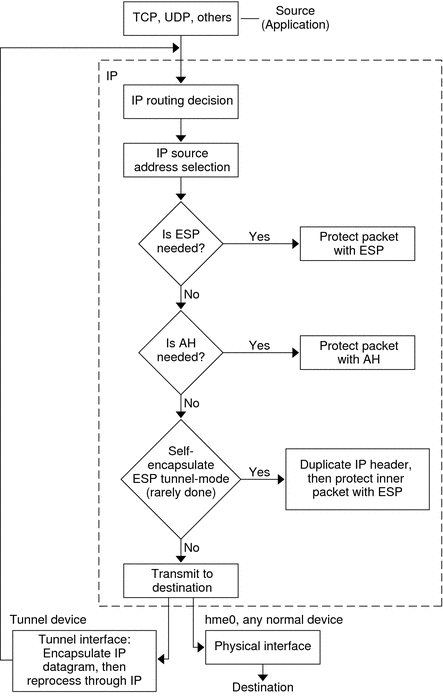
Figure 18–2 IPsec Applied to Inbound Packet Process
- © 2010, Oracle Corporation and/or its affiliates
