 How to Create a Rights Profile for Convenient
Authorizations
How to Create a Rights Profile for Convenient
Authorizations
Where site security policy permits, you might want to create a rights profile that contains authorizations for users who can perform tasks that require authorization. To enable every user of a particular system to be authorized, see How to Modify policy.conf Defaults.
Before You Begin
You must be in the Security Administrator role in the global zone.
-
Open a Trusted Extensions toolbox in the Solaris Management Console.
Use a toolbox of the appropriate scope. For details, see Initialize the Solaris Management Console Server in Trusted Extensions.
-
Under System Configuration, navigate to Rights.
A password prompt might be displayed.
-
Type the role password.
-
To add a rights profile, click Action –> Add Right.
-
Create a rights profile that contains one or more of the following authorizations.
For the step-by-step procedure, see How to Create or Change a Rights Profile in System Administration Guide: Security Services.
In the following figure, the Authorizations Included window shows the authorizations that might be convenient for users.
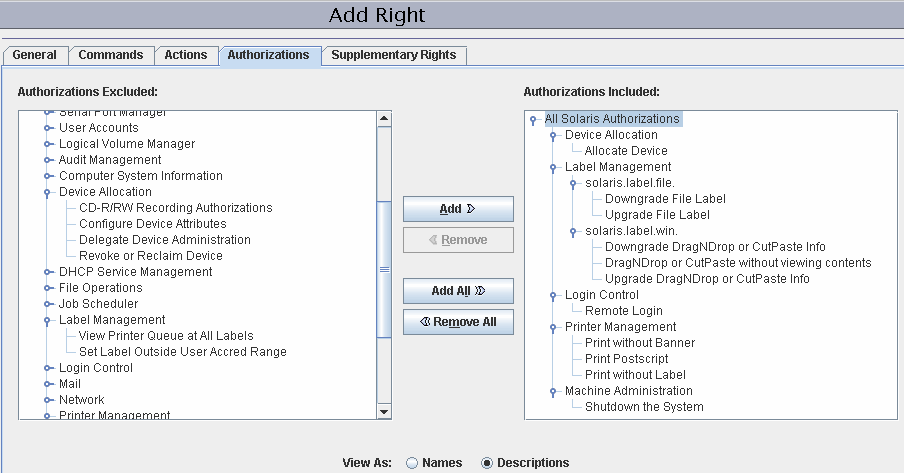
-
Allocate Device – Authorizes a user to allocate a peripheral device, such as a microphone.
By default, Solaris users can read and write to a CD-ROM. However, in Trusted Extensions, only users who can allocate a device can access the CD-ROM drive. To allocate the drive for use requires authorization. Therefore, to read and write to a CD-ROM in Trusted Extensions, a user needs the Allocate Device authorization.
-
Downgrade DragNDrop or CutPaste Info – Authorizes a user to select information from a higher-level file and place that information in a lower-level file.
-
Downgrade File Label – Authorizes a user to lower the security level of a file
-
DragNDrop or CutPaste without viewing contents – Authorizes a user to move information without viewing the information that is being moved.
-
Print Postscript – Authorizes a user to print PostScriptTM files.
-
Print without Banner - Authorizes a user to print hard copy without a banner page.
-
Print without Label – Authorizes a user to print hard copy that does not display labels.
-
Remote Login – Authorizes a user to remotely log in.
-
Shutdown the System – Authorizes a user to shut down the system and to shut down a zone.
-
Upgrade DragNDrop or CutPaste Info – Authorizes a user to select information from a lower-level file and place that information in a higher-level file.
-
Upgrade File Label – Authorizes a user to heighten the security level of a file.
-
-
Assign the rights profile to a user or a role.
For assistance, see the online help. For the step-by-step procedure, see How to Change the RBAC Properties of a User in System Administration Guide: Security Services.
Example 13–6 Assigning a Printing-Related Authorization to a Role
In the following example, the Security Administrator allows a role to print jobs without labels on body pages.
In the Solaris Management Console, the security administrator navigates to Administrative Roles. She views the rights profiles that are included in a particular role, then ensures that the print-related authorizations are contained in one of the role's rights profiles.
- © 2010, Oracle Corporation and/or its affiliates
