Related Access Procedures
This section provides other procedures related to accessing the Trusted Solaris environment, concerning:
-
Leaving the Trusted Solaris environment
-
Changing passwords
-
Enabling logins when logins are disabled
Leaving the Trusted Solaris Environment
If you leave your logged-on terminal unattended, you create a security risk. Make a habit of securing your terminal before leaving it; either lock the screen or log out. If you plan to return shortly, lock your screen. In most facilities, the screen times out after a specified period of idleness and automatically locks. If you expect to be gone for a while or you expect someone else to use your terminal, log out.
To Lock and Unlock Your Screen
-
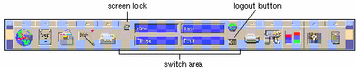
To lock your screen, click on the screen lock icon in the switch area of the front panel (see Figure 2-6).
Figure 2-6 Front Panel Switch Area
The screen turns black and the dialog box shown in Figure 2-7 is displayed.
Figure 2-7 Lock Screen Dialog Box
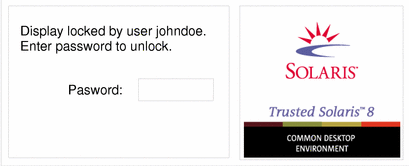
Note -The Trusted Stripe should not be displayed when the screen is locked. If it does appear, notify your security administrator immediately.
-
To unlock your screen, type your password in the password entry field and press Enter.
To Log Out of the Trusted Solaris Environment
-
Click on the EXIT icon in the switch area of the front panel (see Figure 2-6).
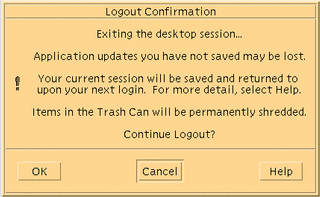
The confirmation dialog box shown in Figure 2-8 is displayed. It tells you to save application updates, reminds you that the current session will be saved, and warns you that any items in the Trash Can will be permanently shredded.
-
Click OK to continue the logout process.
Figure 2-8 Logout Confirmation Dialog Box
To Shut Down Your System (for authorized users only)
Logging out is the normal way to end a Trusted Solaris session. If you need to turn off your machine (and you are authorized for shutting down your system), you should use the Shut Down command and then turn off your power. If you do shut down your machine, it may require rebooting by an user with additional authorization depending on your security policy.
-
Select Shut Down from the Trusted Path menu.
This causes a confirmation dialog box to be displayed.
-
Select OK if you definitely want to shut down your system or Cancel if you want to reconsider.
Note -The keyboard combination Stop-A (L1-A) is not available in the Trusted Solaris environment unless specially configured by your security administrator.
Enabling Logins When Logins Are Disabled
As a security measure, your administrator can configure your site so that all logins are disabled after a reboot. If a reboot has occurred and you are not authorized to enable logins, the dialog box shown in Figure 2-9 appears; you must notify your Trusted Solaris 8 administrator to help you log in. If you are authorized to enable logins, the dialog box shown in Figure 2-10 appears.
Figure 2-9 Disabled Logins Dialog Box for Users Unauthorized to Enable Logins
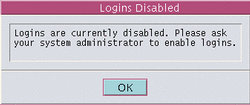
Figure 2-10 Disabled Logins Dialog Box for Users Authorized to Enable Logins
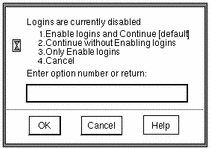
To Enable Logins After a Reboot
-
Enter the appropriate Enable logins option (see Figure 2-10):
-
Enter 1 to enable logins for all users and then log in, or 3 to enable logins for all users without logging in.
You should first check your site's security policy to ensure that enabling logins does not cause a security breach.
-
Enter 2 to leave other logins disabled and then log in, or 4 to leave other logins disabled and not log in.
Do this if you are not ready to enable logins.
-
-
Click OK to enable or leave disabled the logins as specified or click Cancel to leave logins in their current state.
Both options dismiss the dialog box and reset logins as specified.
Fixing a Bad Desktop Profile
If you have customized your shell initialization files (.cshrc, .login, etc.) and cannot log in, you can use the failsafe login feature to log in and correct the situation. In a standard login, the shell initialization files are sourced at startup to provide features customized for your environment. In a failsafe login, the default values are applied to your environment and no shell initialization files are sourced. This guarantees your ability to log in and permits you to fix any problems in shell initialization files.
To Perform a Failsafe Login
-
Type your username in the text field in the username dialog box (see Figure 2-2).
-
Click the Options button and choose Failsafe Session from the Session submenu.
-
Click the OK button (or press Enter) and perform the rest of the steps in a standard login.
-
Edit the shell initialization file(s) where you think the problem may be occurring.
- © 2010, Oracle Corporation and/or its affiliates
