Administering Hosts and Networks
To administer hosts and networks, you need to open the Computers and Networks tool collection. A typical collection is shown in the view pane of the following figure.
Figure 2-9 Computers and Networks Tool Collection
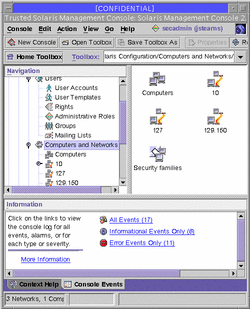
This gives you access to three tools:
-
Computers tool--When open, the host icons for all local networks are displayed in the view pane, which let you edit IP address, ethernet adress, and host alias information. A typical Computer properties dialog box is shown below.
Figure 2-10 Computer Properties Dialog Box
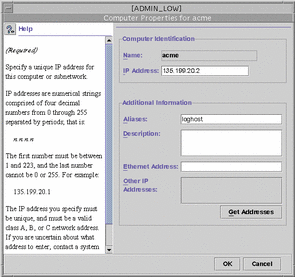
-
Subnetwork tool--This tool groups hosts by subnetwork and works the same as the Computers tool above. Its icon is displayed as two monitors connected by a cable, with a partial IP address as a caption.
-
Security families tool--Lets you add or modify network templates including the assignments of hosts to the templates. This tool is described in more detail below.
Security Families Tool Set
A security family is a group of workstations that use a common networking protocol and have the same security requirements. As a result, you can apply the same template of network security attributes to them for the purpose of receiving and transmitting data. Trusted networking and templates are explained in more detail in Chapter 3, Administering Trusted Networking.
When the Security Families tool is opened, all available templates display as icons. You can modify either the templates or the host assignments as follows:
-
If you double-click a template icon, all hosts in that security family, that is, those assigned to the selected template, are displayed as icons. Double-clicking a host icon (or selecting it and choosing Properties from the Action or popup menu) lets you modify its IP address or template assignment.
-
If you select a template icon and choose Properties from the Action or popup menu, the Modify Template dialog box is displayed, as illustrated in the following figure, and you can change the definition of the template.
Figure 2-11 Modify Template Dialog Box
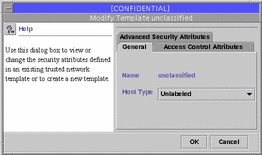
The tabs in the Modify Template dialog box are described in the following table.
Table 2-4 Template Dialog Box Summary|
Tab |
Description |
|---|---|
|
General |
Specifies templates, host types, and minimum/maximum labels. |
|
Access Control Attributes |
Specifies security attributes to be applied to incoming data from hosts to which this template is applied. The potential incoming security attributes include minimum label, maximum label, default label, and default clearance. |
|
Advanced Security Attributes |
Specifies security attributes to be applied to outgoing data to hosts to which this template is applied. The potential outgoing security attributes include DOI, IP label type, forced privileges, allowed privileges, RIPSO send class, RIPSO send PAF, RIPSO return PAF, and CIPSO domain. |
- © 2010, Oracle Corporation and/or its affiliates
