Operational Affinity Algorithm for Load Balancing
In the operational affinity algorithm for load balancing, all requests are allocated a hash value according to the request type and request properties. Each hash value is allocated to an attached data source. The number of hash values that are allocated to a data source is proportional to the weight of the data source.
When a request is received, Directory Proxy Server examines the hash table to determine whether a request with that hash value has already been distributed. If the hash value already exists in the hash table, Directory Proxy Server sends the request to the data source with that hash value. If the hash value does not exist in the hash table, the request is distributed by using the proportional algorithm for load balancing.
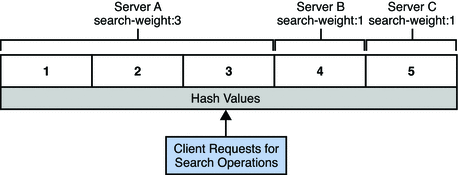
Figure 16–3 shows an example with three attached data sources. Data source A has a weight of 3 for search operations, the other data sources have a weight of 1 for search operations. The hash table allocates 3/5ths of the hash values to data source A, 1/5th to data source B, and 1/5th to data source C.
If requests have a normal range of diversity, data source A would receive three times more requests than data source B or data source C. If there is a disproportionate number of requests with identical properties, the ratio of requests between the three data sources is disturbed. For example, if a client make repeated BIND requests on the same DN, the BIND must always be serviced by the same data source.
Figure 16–3 Distribution of Requests According to the Operational Affinity Algorithm for Load Balancing
The use of the operational affinity algorithm for load balancing is beneficial for the following features:
-
Global account lockout
-
Cache optimization in Directory Server
Disadvantage of Using the Operational Affinity Algorithm for Load Balancing
The operational affinity algorithm for load balancing does not ensure an evenly distributed work load across data sources.
A hash value is allocated to a request according to the type of request and the properties of the request. A range of hash values represents an arbitrary group of unrelated requests. It is possible for one range of hash values to represent many more operations than another range of hash values. A given range of hash values might represent requests that are made frequently, another range of hash values might represents requests that are almost never made.
Operational Affinity Algorithm for Global Account Lockout
By using the operational affinity algorithm for load balancing, you can ensure that the same data source always responds to bind requests from a given client. In this way, you can ensure that a client is locked out after the maximum number of failed bind attempts. If the same data source does not respond to bind requests from a given client, the client can exceed the maximum number of failed bind attempts.
When a client binds, a hash value for the request is allocated according to the bind credentials. Directory Proxy Server consults the hash table and distributes the request to the data source for that hash value. No matter how many times the client binds, the hash value is always the same. The request is always distributed to the same data source.
If a client requests a bind without the appropriate credentials, the data source rejects the bind request. If the client makes a second or third bind request, the same data source rejects the bind request. When the client exceeds the maximum number of allowed bind attempts, Directory Server locks the client out.
For an example of how configure the operational affinity algorithm for global account lockout, see To Configure the Operational Affinity Algorithm for Global Account Lockout in Sun Directory Server Enterprise Edition 7.0 Administration Guide.
Operational Affinity Algorithm for Cache Optimization
By using the operational affinity algorithm for load balancing, searches from the same client to the same entry can always be distributed to the same data source. When a data source responds to a request, the targeted entry is stored in the cache. If the same data source responds repeatedly to the same request, the data source can benefit from using the cached data.
For an example of how configure the operational affinity algorithm for cache optimization, see To Configure Operational Affinity Algorithm for Cache Optimization in Sun Directory Server Enterprise Edition 7.0 Administration Guide.
- © 2010, Oracle Corporation and/or its affiliates
