| C H A P T E R 6 |
|
Encryption and Authentication |
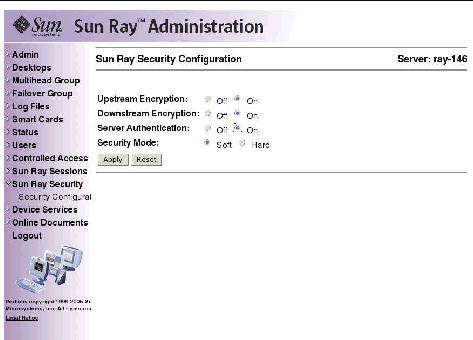
Sun Ray Server Software provides interconnect security. Two main aspects of this feature are:
In earlier versions of Sun Ray Server Software, data packets on the Sun Ray interconnect were sent in the clear. This made it easy to "snoop" the traffic and recover vital and private user information, which malicious users might misuse. To avoid this type of attack, Sun Ray Server Software allows administrators to enable traffic encryption. This feature is optional; the system or network administrator can configure it based on site requirements.
The ARCFOUR encryption algorithm, selected for its speed and relatively low CPU overhead, supports a higher level of security between Sun Ray services and Sun Ray desktop units. In the Sun Ray Server Software 2.0 release, only the X server traffic was encrypted.
Encryption alone does not provide complete security. It is still possible, if not necessarily easy, to spoof a Sun Ray server or a Sun Ray client and pose as either. This leads to the man-in-the- middle attack, in which an impostor claims to be the Sun Ray server for the clients and pretends to be client for the server. It then goes about intercepting all messages and having access to all secure data.
Client and server authentication can resolve this type of attack. This release offers server-side authentication only, through the pre-configured public-private key pairs in Sun Ray Server Software and firmware. The Digital Signature Algorithm (DSA) is used to verify that clients are communicating with a valid Sun Ray server. This authentication scheme is not completely foolproof, but it mitigates trivial man-in-the-middle attacks and makes it harder for attackers to spoof Sun Ray Server Software.
When configuring the security for a Sun Ray system, you should evaluate the security requirements. You may choose:
Additionally, you must decide whether to enable hard security mode. To configure your site, you can use the utcrypto command or the Sun Ray Administration Tool (Admin GUI).
Hard security mode ensures that every session is secure. If security requirements cannot be met, the session is refused. Soft security mode ensures that every client that requests a session gets one; if security requirements cannot be met, the session is granted but not secure.
For example, in hard security mode, if any Sun Ray DTU that does not support security features (for instance, because of old firmware) connects to a Sun Ray server, the server denies the session.
In soft security mode, given the above situation, the Sun Ray server grants the DTU a non-secure session. It is now up to the user to decide whether to continue using a non-secure session.
For more information, please see the man page for utcrypto or Administration Tool.
Use the utsession command to display session status. Its output has been modified to included security status for a session. The State column in utsession -p output now displays the encrypted/authenticated state of the session by using E for encrypted and A for authenticated session types. This information is not displayed for any session in the disconnected state.
In a multihead environment, there may be a case where the primary and the secondary servers have different firmware. For instance, if the secondary has version 1.3 or earlier firmware, it cannot support any of the security features. In this case, the lowest security setting is displayed. In other words, if the secondary server is configured with 1.3 firmware and the primary server with SRSS 2.0, 3.0, 3.1, or 3.1.1 firmware, and encryption and authentication are configured, then neither an E or an A is displayed.
# utsession -p Token ID Registered Name Unix ID Disp State Payflex.0000074500000202 ??? ??? 2 IEA Micropayflex.000003540004545 ??? ??? 3 D |
Once a connection has been successfully established between a client and a server, the user can determine whether the connection is secure at any time by pressing the three volume keys together (currently used to determine MAC address of the terminal).
One of the following icons is also displayed when a Sun Ray DTU connects to a session. Each icon displays information about connection security status.
There are several variations on the security icon:
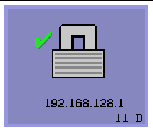
The server is authenticated to the client and the data link is encrypted.
The server is not authenticated to the client and the data link is encrypted.

The server is not authenticated to the client and the data link is not encrypted.
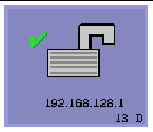
The server is authenticated to the client but the data link is not encrypted.
The following icons are displayed when there might be a security breach.
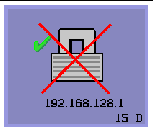
Definition: The client is refusing to connect to a server because it is unable to verify the validity of the Sun Ray server.
This error can occur only if an unknown Sun Ray server intercepts the messages and tries to emulate a valid Sun Ray server. This is a session security breach.

Definition: The server is refusing to grant a session to the client because the client is unable to fulfill the server's security requirements.
Copyright © 2006, Sun Microsystems, Inc. All Rights Reserved.