 To Configure the OpenSSO Enterprise Identity
Provider and Service Provider for SAML2 protocols
To Configure the OpenSSO Enterprise Identity
Provider and Service Provider for SAML2 protocols
For these configurations, you must have the following:
-
Identity Provider metadata
-
Identity Provider extended metadata
-
Service Provider metadata
-
Service Provider extended metadata
In Identity Provider, import Identity Provider metadata and Identity Provider extended metadata as hosted metadata. Import Service Provider metadata and Service Provider extended metadata as remote entity metadata.
Before You Begin
Before loading metadata, read through the following steps for the changes that you must make to the metadata. See the SAML2 samples for detailed instructions on how to setup SAML2, See the OpenSSO website for commands and syntax.
-
Edit the extended metadata XML element <EntityConfig>.
Change the hosted attribute from true to false.
-
Generate the metadata templates in both Identity Provider and Service Provider environments.
You can generate the metadata templates in one of two ways:
-
Use the browser-based URL http://host:port/opensso/famadm.jsp
-
Use the famadm command.
At the Identity Provider, where idp_meta_alias is /idp:
famadm create-metadata-templ -y idp_entity_id -u amadmin -f admin_password_file_name -m idp_standard_metadata -x idp_extended_metadata -i idp_meta_alias
At the Service Provider, where sp_meta_alias is /sp:
famadm create-metadata-templ -y sp_entity_id -u amadmin -f admin_password_file_name -msp_standard_metadata -x sp_extended_metadata -s sp_meta_alias
-
-
Customize the extended metadata at the Service Provider.
Add the Service Provider extended metadata as an attribute. This attribute is used by the SAML protocols to do any post-SSO Authentication process. In this example, the attribute is named spAdapter. In the architecture diagram, this is the SiteMinder Plug-In. The SiteMinder Plug-In uses the OpenSSO Enterprise session to authenticate against SiteMinder and to establish the SiteMinder session. The Service Provider metadata must have the following attributes:
<Attribute name="spAdapter"> <Value>com.sun.identity.saml2.plugins.SMAdapter</Value> </Attribute> <Attribute name="spAdapterEnv"> <Value>AgentIP=192.18.120.65</Value> <Value>AgentID=agent1</Value> <Value>PolicyServerIPAddress=192.18.120.65</Value> <Value>AuthorizationPort=44443</Value> <Value>AuthenticationPort=44442</Value> <Value>AccountingPort=44441</Value> <Value>AgentHostName=HostName.example.com</Value> <Value>ConnectionMinimum=2</Value> <Value>ConnectionMaximum=20</Value> <Value>ConnectionStep=2</Value> <Value>RequestTimeout=60</Value> <Value>FAMCookieName=iPlanetDirectoryPro</Value> <Value>SMCookieName=SMSESSION</Value> <Value>CookieDomain=.red.example.com</Value> <Value>Resource=/test/index.html</Value> <Value>SharedSecret={RC2}1r976MPOVq5JPpKzxFsXxIlut/YkgtUeklaceAoONCN mFJKDY+W8CkVpGY0to+x6apsIQAMPWLsgrm6NcdvyXv7K9Vf0vEALeWOy5BqLAhw fgKp4TbFRQspgv4w24ZOWsk57rwJ0N4kUJdM9lsLRu5hGKXArRJNpF80vS/U53TZ vM/qE5I3DcCOWKY4lJBZh</Value> </Attribute> -
Set the Service Provider extended metadata attribute transientUser to your anonymous user.
<Attribute name="transientUser"> <Value>anonymous</Value> </Attribute>Also verify that the OpenSSO Enterprise Service Provider is enabled for Anonymous authentication. See the OpenSSO Enterprise product documentation for more information.
-
Add the Circle of Trust through the OpenSSO Enterprise administration console.
Before loading, verify that the hosted attribute in the extended metadata has been changed to false.
-
Load the hosted metadata in both the Identity Provider and the Service Provider.
You can use the famadm command or the OpenSSO Enterprise administration console.
-
Exchange the Service Provider metadata with the Identity Provider.
-
Exchange the Identity Provider metadata with the Service Provider metadata.
-
Load the metadata.
-
After successful metadata exchange, verify through OpenSSO Enterprise administration console that metadata is properly configured.
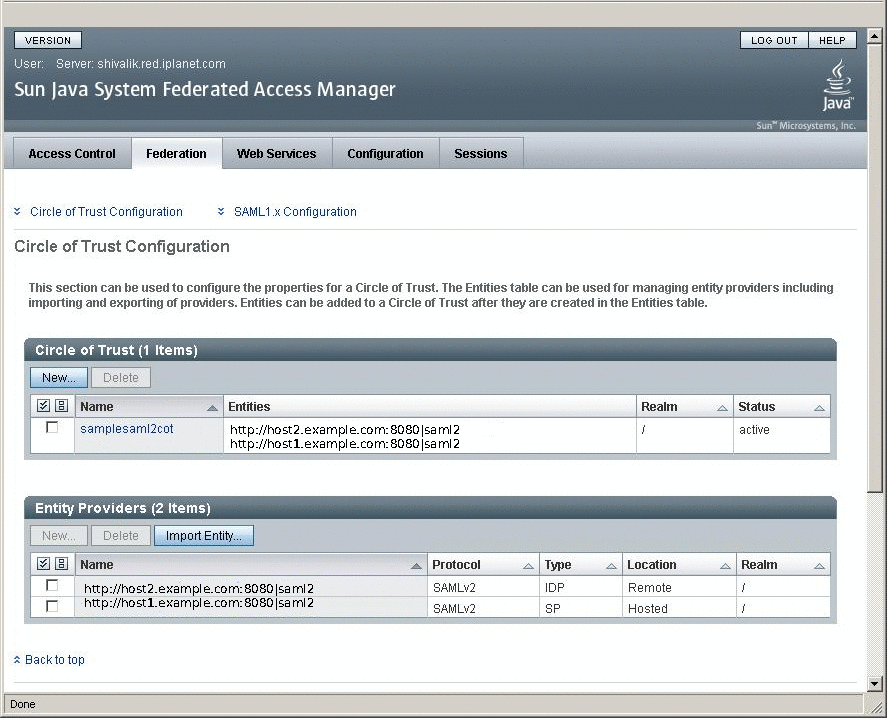
-
Verify that Single Sign-On works properly.
Access the enterprise application protected by SiteMinder Service Provider Agent. This should redirect to the OpenSSO Enterprise for authentication where the SAML2 SSO is initiated.
- © 2010, Oracle Corporation and/or its affiliates
