|
|
| Sun ONE Directory Server 5.2 Reference Manual |
Chapter 5 Plug-In Implemented Server Functionality
This chapter serves as a plug-in implemented server functionality reference and is divided into the following sections:
- Plug-In Overview
- Server Plug-In Functionality Reference
- Attributes Common to All Plug-Ins
- Attributes Allowed by Certain Plug-Ins
- Database Plug-In Attributes
- Chained Suffix Plug-In Attributes
- Frontend Plug-In Attributes
- Retro Changelog Plug-In Attributes
- Subtree Entry Counter Plug-In Attributes
Plug-In Overview
The configuration for each part of Directory Server plug-in functionality has its own separate entry and set of attributes under the subtree cn=plugins,cn=config. A second look at Code Example 3-2 (configuration entry for the Telephone Syntax plug-in) described in Chapter 3 "Core Server Configuration" shows some of the plug-in configuration attributes:
dn: cn=Telephone Syntax,cn=plugins,cn=config
objectclass: top
objectclass: extensibleObject
objectclass: nsSlapdPlugin
cn: Telephone Syntax
nsslapd-pluginPath: ServerRoot/lib/syntax-plugin.so
nsslapd-pluginInitfunc: tel_init
nsslapd-pluginType: syntax
nsslapd-pluginEnabled: on
Some of these attributes are common to all plug-ins while others may be particular to a specific plug-in. You can check which attributes are currently being used by a given plug-in by performing an ldapsearch on the cn=config subtree.
Object Classes for Plug-In Configuration
All plug-ins are instances of the nsSlapdPlugin object class, which in turn inherits from the extensibleObject object class. For plug-in configuration attributes to be taken into account by the server, both of these object classes (in addition to the top object class) must be present in the entry as shown in the following example:
dn:cn=ACL Plugin,cn=plugins,cn=config
objectclass:top
objectclass:extensibleObject
objectclass:nsSlapdPlugin
Server Plug-In Functionality Reference
The following tables provide an overview of the plug-ins provided with Sun ONE Directory Server 5.2, along with their configurable options, configurable arguments, default setting, dependencies, general performance related information, and further reading. These tables will enable you to compare plug-in performance gains and costs and choose the optimal settings for your deployment. A reference to additional information on the plug-ins is provided where this is available.
7-Bit Check Plug-In
ACL Plug-In
Plug-In Name
ACL Plugin
DN of Config Entry
cn=ACL Plugin,cn=plugins,cn=config
Description
ACL access check plug-in
Configurable Options
on | off
Default Setting
on
Configurable Arguments
None
Dependencies
None
Performance Related Information
It is recommended that you leave this plug-in running at all times.
Further Information
Chapter 6, "Managing Access Control" in the Sun ONE Directory Server Administration Guide.
ACL Preoperation Plug-In
Plug-In Name
ACL preoperation
DN of Config Entry
cn=ACL preoperation,cn=plugins,cn=config
Description
ACL access check plug-in.
Configurable Options
on | off
Default Setting
on
Configurable Arguments
None
Dependencies
Database
Performance Related Information
It is recommended that you leave this plug-in running at all times.
Further Information
Chapter 6, "Managing Access Control" in the Sun ONE Directory Server Administration Guide.
Binary Syntax Plug-In
Boolean Syntax Plug-In
Case Exact String Syntax Plug-In
Case Ignore String Syntax Plug-In
Chaining Database Plug-In
Plug-In Name
Chaining Database
DN of Config Entry
cn=Chaining database,cn=plugins,cn=config
Description
Syntax for handling DNs.
Configurable Options
on | off
Default Setting
on
Configurable Arguments
None
Dependencies
None
Performance Related Information
Do not modify the configuration of this plug-in. It is recommended that you leave this plug-in running at all times.
Further Information
"Creating Chained Suffixes" in Chapter 3 of the Sun ONE Directory Server Administration Guide.
Class of Service Plug-In
Plug-In Name
Class of Service
DN of Config Entry
cn=Class of Service,cn=plugins,cn=config
Description
Allows for sharing of attributes between entries.
Configurable Options
on | off
Default Setting
on
Configurable Arguments
None
Dependencies
None
Performance Related Information
Do not modify the configuration of this plug-in. It is recommended that you leave this plug-in running at all times.
Further Information
Chapter 5, "Advanced Entry Management" in the Sun ONE Directory Server Administration Guide.
Country String Syntax Plug-In
Distinguished Name Syntax Plug-In
DSML Frontend Syntax Plug-In
Generalized Time Syntax Plug-In
Integer Syntax Plug-In
Internationalization Plug-In
ldbm Database Plug-In
Plug-In Name
ldbm database plug-in
DN of Config Entry
cn=ldbm database plug-in,cn=plugins,cn=config
Description
Implements local databases.
Configurable Options
N/A
Default Setting
on
Configurable Arguments
None
Dependencies
None
Performance Related Information
See "Database Plug-In Attributes" on page 217 for further information on database configuration. It is recommended that you leave this plug-in running at all times.
Further Information
Chapter 2, "Creating Your Directory Tree" in the Sun ONE Directory Server Administration Guide.
Legacy Replication Plug-In
Plug-In Name
Legacy Replication plug-in
DN of Config Entry
cn=Legacy Replication plug-in,cn=plugins,cn=config
Description
Enables Sun ONE Directory Server 5.2 to be a consumer of a 4.x supplier.
Configurable Options
on | off
Default Setting
on
Configurable Arguments
None.
Dependencies
database
Performance Related Information
None
Further Information
This plug-in can be disabled if the server is not (and never will be) a consumer of a 4.x server. See Chapter 8, "Managing Replication" in the Sun ONE Directory Server Administration Guide for more information.
Multimaster Replication Plug-In
Plug-In Name
Multimaster Replication Plugin
DN of Config Entry
cn=Multimaster Replication plugin,cn=plugins,cn=config
Description
Enables replication between two 5.x Directory Servers.
Configurable Options
on | off
Default Setting
on
Configurable Arguments
None
Dependencies
database
Performance Related Information
N/A
Further Information
You can turn this plug-in off if you have only one server, which will never replicate. See Chapter 8, "Managing Replication" in the Sun ONE Directory Server Administration Guide for more information.
Octet String Syntax Plug-In
CLEAR Password Storage Plug-In
Plug-In Name
CLEAR
DN of Config Entry
cn=CLEAR,cn=Password Storage Schemes,cn=plugins,cn=config
Description
CLEAR password storage scheme used for password encryption.
Configurable Options
on | off
Default Setting
on
Configurable Arguments
None
Dependencies
None
Performance Related Information
Do not modify the configuration of this plug-in. It is recommended that you leave this plug-in running at all times.
Further Information
Chapter 7, "User Account Management" in the Sun ONE Directory Server Administration Guide.
CRYPT Password Storage Plug-In
Plug-In Name
CRYPT
DN of Config Entry
cn=CRYPT,cn=Password Storage Schemes,cn=plugins,cn=config
Description
CRYPT password storage scheme used for password encryption.
Configurable Options
on | off
Default Setting
on
Configurable Arguments
None
Dependencies
None
Performance Related Information
Do not modify the configuration of this plug-in. It is recommended that you leave this plug-in running at all times.
Further Information
Chapter 7, "User Account Management" in the Sun ONE Directory Server Administration Guide.
NS-MTA-MD5 Password Storage Scheme Plug-In
Plug-In Name
NS-MTA-MD5
DN of Config Entry
cn=NS-MTA-MD5,cn=Password Storage Schemes,cn=plugins,cn=config
Description
NS-MTA-MD5 password storage scheme for password encryption.
Configurable Options
on | off
Default Setting
on
Configurable Arguments
None
Dependencies
None
Performance Related Information
Do not modify the configuration of this plug-in. It is recommended that you leave this plug-in running at all times.
Further Information
You can no longer choose to encrypt passwords using the NS-MTA-MD5 password storage scheme. The storage scheme is still present, but for backward compatibility only (the data in your directory still contains passwords encrypted with the NS-MTA-MD5 password storage scheme.) See Chapter 7, "User Account Management" in the Sun ONE Directory Server Administration Guide.
SHA Password Storage Scheme Plug-In
Plug-In Name
SHA
DN of Config Entry
cn=SHA,cn=Password Storage Schemes,cn=plugins,cn=config
Description
SHA password storage scheme for password encryption.
Configurable Options
on | off
Default Setting
on
Configurable Arguments
None
Dependencies
None
Performance Related Information
If there are no passwords encrypted using the SHA password storage scheme, you may turn this plug-in off. If you want to encrypt your password with the SHA password storage scheme, we recommend that you choose SSHA instead, as SSHA is a far more secure option.
Further Information
Chapter 7, "User Account Management" in the Sun ONE Directory Server Administration Guide.
SSHA Password Storage Scheme Plug-In
Plug-In Name
SSHA
DN of Config Entry
cn=SSHA,cn=Password Storage Schemes,cn=plugins,cn=config
Description
SSHA password storage scheme for password encryption.
Configurable Options
on | off
Default Setting
on
Configurable Arguments
None
Dependencies
None
Performance Related Information
Do not modify the configuration of this plug-in. It is recommended that you leave this plug-in running at all times.
Further Information
Chapter 7, "User Account Management" in the Sun ONE Directory Server Administration Guide.
Postal Address String Syntax Plug-In
PTA Plug-In
Plug-In Name
Pass Through Authentication
DN of Config Entry
cn=Pass Through Authentication,cn=plugins,cn=config
Description
Enables pass-through authentication, the mechanism that allows one directory to consult another to authenticate bind requests.
Configurable Options
on | off
Default Setting
off
Configurable Arguments
The LDAP URL to the configuration directory.
nsslapd-pluginarg0: ldap://config.example.com/o=NetscapeRootDependencies
None
Further Information
Chapter 14, "Using the Pass-Through Authentication Plug-in" in the Sun ONE Directory Server Administration Guide.
Note that the PTA plug-in is not listed in Directory Server console or in the dse.ldif file if you use the same server instance for your user directory and your configuration directory
Referential Integrity Postoperation Plug-In
Plug-In Name
Referential Integrity Postoperation
DN of Config Entry
cn=Referential Integrity Postoperation,cn=plugins,cn=config
Description
Enables the server to ensure referential integrity.
Configurable Options
All configuration and on | off
Default Setting
off
Configurable Arguments
When enabled, the post operation Referential Integrity plug-in performs integrity updates on the member, uniquemember, owner and seeAlso attributes immediately after a delete or rename operation. You can reconfigure the plug-in to perform integrity checks on all other attributes.
The following arguments are configurable:
-1 = no check for referential integrity
0 = check for referential integrity is performed immediately
positive integer = request for referential integrity is queued and processed at a later stage. This positive integer serves as a wake-up call for the thread to process the request, at intervals corresponding to the integer specified.
Dependencies
Database
Limitations
Observe the following limitations when you use the referential integrity plug-in in a multi-master replication environment:
- Enable the referential integrity plug-in on all servers containing master replicas
- Enable the referential integrity plug-in with the same configuration on every master
Further Information
See "Maintaining Referential Integrity" in Chapter 2 of the Sun ONE Directory Server Administration Guide.
Retro Changelog Plug-In
Plug-In Name
Retro Changelog Plugin
DN of Config Entry
cn=Retro Changelog Plugin,cn=plugins,cn=config
Description
Used by LDAP clients for maintaining application compatibility with Directory Server 4.x versions. Maintains a log of all changes occurring in the Directory Server. The Retro Changelog offers the same functionality as the changelog in the 4.x versions of Directory Server.
Configurable Options
on | off
Default Setting
off
Configurable Arguments
See "Retro Changelog Plug-In Attributes" for further information on the two configuration attributes for this plug-in.
Dependencies
None
Performance Related Information
May slow down Directory Server performance.
Further Information
Chapter 8, "Managing Replication" in the Sun ONE Directory Server Administration Guide.
Roles Plug-In
Plug-In Name
Roles Plugin
DN of Config Entry
cn=Roles Plugin,cn=plugins,cn=config
Description
Enables the use of roles in Directory Server.
Configurable Options
on | off
Default Setting
on
Configurable Arguments
None
Dependencies
None
Performance Related Information
Do not modify the configuration of this plug-in. It is recommended that you leave this plug-in running at all times.
Further Information
Chapter 5, "Advanced Entry Management" in the Sun ONE Directory Server Administration Guide.
State Change Plug-In
Subtree Entry Counter Plug-Ins
Telephone Syntax Plug-In
UID Uniqueness Plug-In
Plug-In Name
UID Uniqueness
DN of Config Entry
cn=UID Uniqueness,cn=plugins,cn=config
Description
Checks that the values of specified attributes are unique each time a modification occurs on an entry.
Configurable Options
on | off
Default Setting
off
Configurable Arguments
Enter the following arguments:
uid
"DN"
"DN"...
to check for UID attribute uniqueness in all listed subtrees.
However, enter the following arguments:
attribute="uid"
MarkerObjectclass = "ObjectClassName"
and optionally
requiredObjectClass = "ObjectClassName"
to check for UID attribute uniqueness when adding or updating entries with the requiredObjectClass, starting from the parent entry containing the ObjectClass as defined by the MarkerObjectClass attribute.
Dependencies
N/A
Performance Related Information
Sun ONE Directory Server 5.2 provides the UID Uniqueness plug-in by default. To ensure unique values for other attributes, you can create instances of the UID Uniqueness plug-in for those attributes.
The UID Uniqueness plug-in may slow down Directory Server performance.
Further Information
Chapter 15, "Using the UID Uniqueness Plug-in" in the Sun ONE Directory Server Administration Guide.
URI Plug-In
Attributes Common to All Plug-Ins
This list provides a brief attribute description, the Entry DN, valid range, default value, syntax, and an example for each attribute.
nsslapd-pluginPath
Specifies the full path to the plug-in.
Property
Value
Entry DN
cn=plug-inName,cn=plugins,cn=config
Valid Range
Any valid path
Default Value
None
Syntax
DirectoryString
Example
nsslapd-pluginPath: ServerRoot/lib/uid-plugin.so
nsslapd-pluginInitfunc
Specifies the plug-in function to be initiated.
Property
Value
Entry DN
cn=plug-inName,cn=plugins,cn=config
Valid Range
Any valid plug-in function.
Default Value
None
Syntax
DirectoryString
Example
nsslapd-pluginInitfunc: NS7bitAttr_Init
nsslapd-pluginType
Specifies the plug-in type. See "nsslapd-plugin-depends-on-type" on page 216 for further information.
Property
Value
Entry DN
cn=plug-inName,cn=plugins,cn=config
Valid Range
Any valid plug-in type.
Default Value
None
Syntax
DirectoryString
Example
nsslapd-pluginType: preoperation
nsslapd-pluginEnabled
Specifies whether or not the plug-in is enabled. This attribute can be changed over protocol, but will only take effect when the server is next restarted.
Property
Value
Entry DN
cn=plug-inName,cn=plugins,cn=config
Valid Range
on | off
Default Value
on
Syntax
DirectoryString
Example
nsslapd-pluginEnabled: on
nsslapd-pluginId
Specifies the plug-in ID.
Property
Value
Entry DN
cn=plug-inName,cn=plugins,cn=config
Valid Range
Any valid plug-in ID.
Default Value
None
Syntax
DirectoryString
Example
nsslapd-pluginId: chaining database
nsslapd-pluginVersion
Specifies the plug-in version.
Property
Value
Entry DN
cn=plug-inName,cn=plugins,cn=config
Valid Range
Any valid plug-in version.
Default Value
Product version
Syntax
DirectoryString
Example
nsslapd-pluginVersion: 5.0b1
nsslapd-pluginVendor
Specifies the vendor of the plug-in.
nsslapd-pluginDescription
Provides a description of the plug-in.
Property
Value
Entry DN
cn=plug-inName,cn=plugins,cn=config
Valid Range
N/A
Default Value
None
Syntax
DirectoryString
Example
nsslapd-pluginDescription: acl access check plug-in
Attributes Allowed by Certain Plug-Ins
nsslapd-plugin-depends-on-type
Multi-valued attribute, used to ensure that plug-ins are called by the server in the correct order. Takes a value that corresponds to the type of a plug-in, contained in the attribute nsslapd-pluginType (see "nsslapd-pluginType" on page 214.) All plug-ins whose type value matches one of the values in the following valid range will be started by the server prior to this plug-in. The following example shows that the database plug-in will be started prior to the postoperation Referential Integrity plug-in.
Property
Value
Entry DN
cn=referential integrity postoperation,cn=plugins,cn=config
Valid Range
Database
Default Value
N/A
Syntax
DirectoryString
Example
nsslapd-plugin-depends-on-type: database
nsslapd-plugin-depends-on-named
Multi-valued attribute, used to ensure that plug-ins are called by the server in the correct order. Takes a value that corresponds to the cn value of a plug-in. The plug-in whose cn value matches one of the values below it will be started by the server prior to this plug-in. If the plug-in does not exist, the server will fail to start. The following example shows that the Class of Service plug-in will be started prior to the postoperation Referential Integrity plug-in. If the Class of Service plug-in does not exist, the server will fail to start.
Database Plug-In Attributes
The database plug-in is also organized in an information tree as shown in the following diagram:
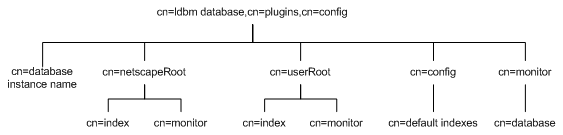
All plug-in technology used by the database instances is stored in the cn=ldbm database plug-in node. This section presents the additional attribute information for each of the nodes in bold in the cn=ldbm database,cn=plugins,cn=config information tree.
Database Configuration Attributes
Global configuration attributes common to all database instances are stored in the cn=config,cn=ldbm database,cn=plugins,cn=config tree node.
nsLookthroughLimit
This performance-related attribute specifies the maximum number of entries that Directory Server will check when examining candidate entries in response to a search request. If you bind as the directory manager DN, unlimited is set by default and overrides any other settings you may specify here.
Binder based resource limits work for this limit, which means that if a value for the operational attribute nsLookThroughlimit is present in the entry used to bind, the default limit is overridden. If you attempt to set a value that is not a number or is too big for a 64-bit signed integer, you will receive an LDAP_UNWILLING_TO_PERFORM error message with additional error information explaining the problem.
nsslapd-allidsthreshold
This performance-related attribute is present by default. It specifies the number of entry IDs that can be maintained for an index key, before the server sets the All IDs token and stops maintaining a list of IDs for that specific key. If you attempt to set a value that is not a number or is too big for a 64-bit signed integer, you will receive an LDAP_UNWILLING_TO_PERFORM error message with additional error information explaining the problem.
However, as tuning this attribute is a complex task and can severely degrade performance, it is advisable to keep the default value. For a more detailed explanation of the All IDs Threshold see Chapter 7,"Tuning Indexing" in the Sun ONE Directory Server Installation and Tuning Guide.
nsslapd-cache-autosize
This performance tuning related attribute is turned off by default. It specifies the percentage of free memory to use for all the combined caches. For example, if the value is set to 80, then 80 percent of the remaining free memory is claimed for the cache. If you plan to run other servers on the machine, then the value will be lower. Setting the value to 0 turns off the cache autosizing and uses the normal nsslapd-cachememsize and nsslapd-dbcachesize attributes.
Property
Value
Entry DN
cn=config,cn=ldbm database,cn=plugins,cn=config
Valid Range
0 (turns cache autosizing off) to 100
Default Value
0
Syntax
Integer
Example
nsslapd-cache-autosize: 80
nsslapd-cache-autosize-split
This performance-related attribute specifies the percentage of cache space to allocate to the database cache. For example, setting this to "60" would give the database cache 60 percent of the cache space and divide the remaining 40 percent between the backend entry caches. That is, if there were 2 databases, each of them would receive 20 percent. This attribute applies only when the nsslapd-cache-autosize attribute has a value of 0.
nsslapd-dbcachesize
This performance tuning related attribute specifies database cache size. Note that this is neither the index cache nor the entry cache. If you activate automatic cache resizing, you override this attribute, by replacing these values with its own guessed values at a later stage of the server startup.
If you attempt to set a value that is not a number or is too big for a 32-bit signed integer, you will receive an LDAP_UNWILLING_TO_PERFORM error message with additional error information explaining the problem.
nsslapd-db-checkpoint-interval
The amount of time in seconds after which the Directory Server sends a checkpoint entry to the database transaction log. The database transaction log contains a sequential listing of all recent database operations and is used for database recovery only. A checkpoint entry indicates which database operations have been physically written to the directory database. The checkpoint entries are used to determine where in the database transaction log to begin recovery after a system failure. The nsslapd-db-checkpoint-interval attribute is absent from dse.ldif. To change the checkpoint interval, you add the attribute to dse.ldif. This attribute can be dynamically modified using ldapmodify. For further information on modifying this attribute, see the section on "Transaction Logging" in the Sun ONE Directory Server Installation and Tuning Guide.
This attribute is provided only for system modification/diagnostics and should be changed only with the guidance of Sun ONE engineering staff and Sun ONE Professional Services. Inconsistent settings of this attribute and other configuration attributes may cause the Directory Server to be unstable.
Property
Value
Entry DN
cn=config,cn=ldbm database,cn=plugins,cn=config
Valid Range
10 to 300 seconds
Default Value
60
Syntax
Integer
Example
nsslapd-db-checkpoint-interval: 120
nsslapd-db-circular-logging
Specifies circular logging for the transaction log files. If this attribute is switched off, old transaction log files are not removed, and are kept renamed as old log transaction files. Turning circular logging off can severely degrade server performance. It should therefore only be modified with the guidance of Sun ONE engineering staff and Sun ONE Professional Services.
Property
Value
Entry DN
cn=config,cn=ldbm database,cn=plugins,cn=config
Valid Range
on or off
Default Value
on
Syntax
DirectoryString
Example
nsslapd-db-circular-logging: on
nsslapd-db-durable-transactions
Indicates whether database transaction log entries are immediately written to the disk. The database transaction log contains a sequential listing of all recent database operations and is used for database recovery only.
With durable transactions enabled, every directory change is physically recorded in the log file and is therefore able to be recovered in the event of a system failure. However, the durable transactions feature may also slow down the performance of the Directory Server. With durable transactions disabled, all transactions are logically written to the database transaction log but may not be physically written to disk immediately. If there is a system failure before a directory change is physically written to disk, that change is not recoverable.
For more information on database transaction logging, see Chapter 12, "Managing Log Files" in the Sun ONE Directory Server Administration Guide.
Property
Value
Entry DN
cn=config,cn=ldbm database,cn=plugins,cn=config
Valid Range
on | off
Default Value
on
Syntax
DirectoryString
Example
nsslapd-db-durable-transactions: on
nsslapd-db-home-directory
UNIX only. Used to fix a situation on UNIX platforms where the operating system endlessly flushes pages. This flushing can be so excessive that performance of the entire system is severely degraded.
This situation will occur only for certain combinations of the database cache size, the size of physical memory, and kernel tuning attributes. In particular, this situation should not occur if the database cache size is less than 100mb.
For example, if your Solaris host seems excessively slow and your database cache size is around 100mb or more, then you can use the iostat utility to diagnose the problem. Use iostat to monitor the activity of the disk where the Directory Server's database files are stored. If all of the following conditions are true:
- the disk is heavily used (more than 1mb per second of data transfer)
- there is a long service time (more than 100ms)
- there is mostly write activity
then you should use the nsslapd-db-home-directory attribute to specify a subdirectory of a tempfs type file system.
nsslapd-db-idl-divisor
Specifies the index block size in terms of the number of blocks per database page. The block size is calculated by dividing the database page size by the value of this attribute. A value of 1 makes the block size exactly equal to the page size. The default value of 0 sets the block size to the page size minus an estimated allowance for internal database overhead. Before modifying the value of this attribute export all databases using the db2ldif script. Once the modification has been made, reload the databases using the ldif2db script.
Property
Value
Entry DN
cn=config,cn=ldbm database,cn=plugins,cn=config
Valid Range
0 to 8
Default Value
0
Syntax
Integer
Example
nsslapd-db-idl-divisor: 2
nsslapd-db-locks
Specifies the number of locks that can be used by the database. Increase the value of this attribute if you observe the following error:
libdb: Lock table is out of available locks
The current number of locks being used, the number of locks configured, and the maximum number of locks reached during the life of the process can be checked using the attributes nsslapd-db-current-locks, nsslapd-db-configured-locks, and nsslapd-db-max-locks respectively, under the entry cn=database,cn=monitor,cn=ldbm dabatase,cn=plugins,cn=config.
Property
Value
Entry DN
cn=config,cn=ldbm database,cn=plugins,cn=config
Valid Range
1 to maximum integer
Default Value
20000
Syntax
Integer
Example
nsslapd-db-locks: 20000
nsslapd-db-logbuf-size
Specifies the log information buffer size. Log information is stored in memory until the buffer fills up or the transaction commit forces the buffer to be written to disk. Larger buffer sizes can significantly increase throughput in the presence of long running transactions, highly concurrent applications, or transactions producing large amounts of data. The nsslapd-db-logbuf-size attribute is only valid if the nsslapd-db-durable-transaction attribute is set to on.
nsslapd-db-logdirectory
The path to the directory containing the database transaction log. The database transaction log contains a sequential listing of all recent database operations and is used for database recovery only. By default, the database transaction log is stored in the same directory as the directory entries themselves:
/ServerRoot/slapd-serverID/db
For fault-tolerance and performance reasons, you may want to move this log file to another physical disk. The nsslapd-db-logdirectory attribute is absent from dse.ldif. To change the location of the database transaction log, add the attribute to dse.ldif. For more information on database transaction logging, see Chapter 12, "Managing Log Files" in the Sun ONE Directory Server Administration Guide.
nsslapd-db-logfile-size
Specifies the maximum size of a single file in the log in bytes. By default, or if the value is set to 0, a maximum size of 10 MB is used. The maximum size is an unsigned 4-byte value. The value of this attribute can have significant impact on performance, as it can be tuned to avoid extensive log switching in the event of heavy entries.
Property
Value
Entry DN
cn=config,cn=ldbm database,cn=plugins,cn=config
Valid Range
0 to unsigned 4-byte integer
Default Value
10 (MB)
Syntax
Integer
Example
nsslapd-db-logfile-size: 10
nsslapd-db-page-size
Specifies the size of the pages used to hold items in the database in bytes. The minimum size is 512 bytes and the maximum size is 64K bytes. If the page size is not explicitly set, Directory Server defaults to a page size of 8K bytes. Changing this default value can have significant performance impact. If the page size is too small, it results in extensive page splitting and copying, whereas if the page size is too large, it can waste disk space.
Note Before modifying the value of this attribute, export all databases using the db2ldif script. Once the modification has been made, reload the databases using the ldif2db script.
Property
Value
Entry DN
cn=config,cn=ldbm database,cn=plugins,cn=config
Valid Range
512 bytes to 64 KB
Default Value
8 (KB)
Syntax
Integer
Example
nsslapd-db-page-size: 8
nsslapd-db-transaction-batch-val
Specifies how many transactions will be batched before being committed. You can use this attribute to improve update performance when full transaction durability is not required. This attribute can be dynamically modified using ldapmodify.
If you do not define this attribute or set it to a value of 0, transaction batching will be turned off and it will be impossible to make remote modifications to this attribute via LDAP. However, setting this attribute to a value greater than 0 causes the server to delay committing transactions until the number of queued transactions is equal to the attribute value. A value greater than 0 also allows you to modify this attribute remotely via LDAP. A value of 1 for this attribute allows you to modify the attribute setting remotely via LDAP, but results in no batching behavior. A value of 1 at server startup is therefore useful for maintaining normal durability, while also allowing transaction batching to be turned on and off remotely when desired. Bear in mind that the value you choose for this attribute may require you to modify the nsslapd-db-logbuf-size attribute to ensure sufficient log buffer size for accommodating your batched transactions.
Note The nsslapd-db-transaction-batch-val attribute is only valid if the nsslapd-db-durable-transaction attribute is set to on.
For more information on database transaction logging, see Chapter 12, "Managing Log Files" in the Sun ONE Directory Server Administration Guide.
Property
Value
Entry DN
cn=config,cn=ldbm database,cn=plugins,cn=config
Valid Range
0 to 30
Default Value
0 (or turned off)
Syntax
Integer
Example
nsslapd-db-transaction-batch-val: 5
nsslapd-db-tx-max
Specifies the maximum number of concurrent transactions that can be handled by the database. Increase the value of this attribute if you observe the following error:
Serious Error---Failed in dblayer_txn_begin, err=12 (Not enough space)
Property
Value
Entry DN
cn=config,cn=ldbm database,cn=plugins,cn=config
Valid Range
1 to maximum integer
Default Value
200
Syntax
Integer
Example
nsslapd-db-tx-max: 200
nsslapd-dbncache
This attribute allows you to split the ldbm cache into equally sized separate pieces of memory. It is possible to specify caches that are large enough so that they cannot be allocated contiguously on some architectures. For example, some releases of Solaris limit the amount of memory that may be allocated contiguously by a process. If nsslapd-dbncache is 0 or 1, the cache will be allocated contiguously in memory. If it is greater than 1, the cache will be broken up into ncache equally sized separate pieces of memory.
This attribute is provided only for system modification/diagnostics and should be changed only with the guidance of Sun ONE engineering staff and Sun ONE Professional Services. Inconsistent settings of this attribute and other configuration attributes may cause the Directory Server to be unstable.
Property
Value
Entry DN
cn=config,cn=ldbm database,cn=plugins,cn=config
Valid Range
Positive integer or 0
Default Value
0
Syntax
Integer
Example
nsslapd-dbncache: 0
nsslapd-import-cachesize
This performance tuning related attribute determines the size of the database cache used in the bulk import process. By setting this attribute value so that the maximum available system physical memory is used for the database cache during bulk importing, you can optimize bulk import speed. If you attempt to set a value that is not a number or is too big for a 32-bit signed integer, you will receive an LDAP_UNWILLING_TO_PERFORM error message with additional error information explaining the problem.
nsslapd-mode
Specifies the permissions used for newly created index files.
nsslapd-exclude-from-export
Specifies a list of attributes that will be excluded when the database is exported.
nsslapd-disk-low-threshold
Specifies the "low" free space on the disk (in MB). When the available free space on any one of the disks used by a database instance falls below the value specified by this attribute, protocol updates on that instance are permitted only by the directory manager.
Property
Value
Entry DN
cn=config,cn=ldbm database,cn=plugins,cn=config
Valid Range
0 to unsigned 4-byte integer
Default Value
100
Syntax
Integer
Example
nsslapd-disk-low-threshold: 100
nsslapd-disk-full-threshold
When the minimum free space on the disk (in MB). When the available free space on any one of the disks used by a database instance falls below the value specified by this attribute, no updates are permitted and the server returns an LDAP_UNWILLING_TO_PERFORM error. Updates are allowed again as soon as free space rises above the threshold.
Property
Value
Entry DN
cn=config,cn=ldbm database,cn=plugins,cn=config
Valid Range
0 to unsigned 4-byte integer
Default Value
10
Syntax
Integer
Example
nsslapd-disk-full-threshold: 10
Database Monitoring Attributes
Table 5-1 lists the global read-only attributes containing database statistics for monitoring activity on databases. These attributes are stored under cn=monitor,cn=ldbm database,cn=plugins,cn=config. For more information on these monitoring read-only entries see Chapter 12, "Managing Log Files" in the Sun ONE Directory Server Administration Guide.
Database Configuration Attributes Under cn=NetscapeRoot and cn=UserRoot
The cn=NetscapeRoot and cn=UserRoot subtrees contain configuration data for the databases containing the o=NetscapeRoot and o="suffixname" suffixes, respectively. The cn=NetscapeRoot subtree contains the configuration data used by the Sun ONE Administration Server for authentication and all actions that cannot be performed through LDAP (such as start/stop). The cn=UserRoot subtree contains all the configuration data for the user-defined database. The cn=UserRoot subtree is called UserRoot by default. However, this is not hard-coded, and, given the fact that there will be multiple database instances, this name will be changed and defined by the user when new databases are added.
The following attributes are common to both the cn=NetscapeRoot,cn=ldbm database,cn=plugins,cn=config and cn=UserRoot,cn=ldbm database,cn=plugins,cn=config subtrees.
nsslapd-cachesize
This performance tuning related attribute specifies the cache size in terms of the entries it can hold. However, it is worth noting that it is simpler to limit by memory size only (see nsslapd-cachememsize attribute). If you attempt to set a value that is not a number or is too big for a 32-bit signed integer, you will receive an LDAP_UNWILLING_TO_PERFORM error message with additional error information explaining the problem.
nsslapd-cachememsize
This performance tuning related attribute specifies the cache size in terms of available memory space. Limiting cachesize in terms of memory occupied is the simplest method. By activating automatic cache resizing, you override this attribute, replacing these values with its own guessed values at a later stage of the server startup. If you attempt to set a value that is not a number or is too big for a 32-bit signed integer, you will receive an LDAP_UNWILLING_TO_PERFORM error message with additional error information explaining the problem.
Property
Value
Entry DN
cn=suffixName,cn=ldbm database,cn=plugins,cn=config
Valid Range
200KB to 4GB
Default Value
10 485 760 (10Mb)
Syntax
Integer
Example
nsslapd-cachememsize:10
nsslapd-directory
Specifies the absolute path to the database instance. If the database instance is created manually, this attribute must be included. It is set by default in the Sun ONE Server Console and can be modified. Once the database instance has been created, do not modify this path as any changes risk preventing the server from accessing data.
nsslapd-readonly
Specifies read only permission. When this attribute is set to on, directory entries can be viewed but cannot be modified. This is useful, for example, when you are performing a backup of the directory.
Property
Value
Entry DN
cn=suffixName,cn=ldbm database,cn=plugins,cn=config
Valid Range
on | off
Default Value
off
Syntax
DirectoryString
Example
nsslapd-readonly: off
nsslapd-require-index
When switched to on, this attribute allows you to refuse non-indexed or allids searches. This performance related attribute avoids saturating the server with erroneous searches.
Property
Value
Entry DN
cn=suffixName,cn=ldbm database,cn=plugins,cn=config
Valid Range
on | off
Default Value
off
Syntax
DirectoryString
Example
nsslapd-require-index: off
nsslapd-suffix
Specifies the chained suffix. This is a single-valued attribute as each database instance can have only one suffix. Previously, it was possible to have more than one suffix on a single database instance but this is no longer the case. Any changes made to this attribute after the entry has been created take effect only after you restart the server containing the chained suffix.
Property
Value
Entry DN
cn=suffixName,cn=ldbm database,cn=plugins,cn=config
Valid Range
Any valid DN
Default Value
N/A
Syntax
DirectoryString
Example
nsslapd-suffix: o=Netscaperoot
Database Performance Attributes
Table 5-2 lists the read-only database performance attributes. These attributes are stored under cn=database,cn=monitor,cn=ldbm database, cn=plugins,cn=config. All of the values for these attributes are 32-bit integers.
Default Index Attributes
The set of default indexes is stored under cn=default indexes,cn=config, cn=ldbm database,cn=plugins,cn=config. Default indexes are configured per backend in order to optimize Directory Server functionality for the majority of deployments.
All indexes, except system-essential ones, can be removed, but care should be taken not to cause unnecessary disruptions. This section presents four required indexing attributes and one optional indexing attribute. For further information on indexes see Chapter 10, "Managing Indexes" in the Sun ONE Directory Server Administration Guide.
nsSystemIndex
This mandatory attribute specifies whether the index is a system index, that is, an index that is vital for Directory Server operations. If this attribute has a value of true, it is system essential. System indexes must not be removed as this will seriously disrupt server functionality.
Property
Value
Entry DN
cn=default indexes,cn=config,cn=ldbm database,cn=plugins,cn=config
Valid Range
true | false
Default Value
N/A
Syntax
DirectoryString
Example
nssystemindex: true
nsIndexType
This optional, multi-valued attribute specifies the types of index used in Directory Server operations and the values of the attributes to be indexed. Each index type must be entered on a separate line.
nsMatchingRule
This optional, multi-valued attribute specifies the collation order object identifier (OID) required for the Directory Server to operate international indexing.
cn
Provides the name of the attribute to be indexed.
Property
Value
Entry DN
cn=default indexes,cn=monitor,cn=ldbm database,cn=plugins,cn=config
Valid Range
Any valid index cn.
Default Value
None
Syntax
DirectoryString
Example
cn: aci
description
This optional attribute provides a free-hand text description of what the index actually performs.
Property
Value
Entry DN
cn=default indexes,cn=monitor,cn=ldbm database,cn=plugins,cn=config
Valid Range
N/A
Default Value
None
Syntax
DirectoryString
Example
description: substring index
Database Monitoring Attributes Under cn=NetscapeRoot
Table lists the global, read-only entries for monitoring activity on the NetscapeRoot database, stored under cn=monitor,cn=Netscaperoot,cn=ldbm database, cn=plugins,cn=config. These attributes contain database statistics and are provided for each file that makes up your database. For further information see Chapter 12, "Managing Log Files" in the Sun ONE Directory Server Administration Guide.
Database Index Attributes Under cn=NetscapeRoot and cn=UserRoot
In addition to the set of default indexes that are stored under cn=default indexes,cn=config,cn=ldbm database,cn=plugins,cn=config, custom indexes can be created for o=Netscaperoot, o=UserRoot, and manually created databases. These custom indexes are stored under the cn=index,cn=NetscapeRoot,cn=ldbm database,cn=plugins,cn=config and cn=index,cn=UserRoot,cn=ldbm database,cn=plugins,cn=config entries, respectively. Each indexed attribute represents a subentry under the above cn=config information tree nodes, as shown in the following figure:
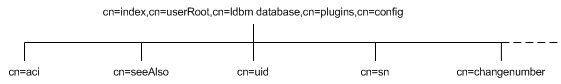
For example, the index file for the aci attribute under o=UserRoot will appear in the Directory Server as follows:
dn:cn=aci,cn=index,cn=UserRoot,cn=ldbm database,cn=plugins,cn=confi
objectclass:top
objectclass:nsIndex
cn=aci
nssystemindex:true
nsindextype:pres
Note that the aci attribute is an operational attribute and is not returned in a search unless you explicitly request it.
For details on the five possible indexing attributes, see the section "Default Index Attributes". For further information about indexes see Chapter 10, "Managing Indexes" in the Sun ONE Directory Server Administration Guide.
VLV Index Object Classes
A VLV (virtual list view) index, also known as a browsing index, provides fast searches and server-side sorting of a known result set. To do this, the object class vlvSearch is needed to define the base, scope, and filter of a search, and the object class vlvIndex is needed to define the ordering of results. VLV index entries are stored in cn=databaseName,cn=ldbm database,cn=plugins,cn=config. Browsing indexes created for and by Directory Server Console are named cn=MCCtargetDN,cn=databaseName,cn=ldbm database,cn=plugins,cn=config.
vlvSearch
Used to define a VLV search. Specifies the entry result set to be VLV indexed.
vlvIndex
Used to define the sort criteria of a Virtual List View index. Each VLV index specification defines the sort order to be imposed on the result set defined in the VLV search entry. A set of VLV index entries may appear below the VLV search entry. The cn (commonName) attribute is used as the naming component for the entry.
VLV Index Attributes
VLV Index Attributes are stored in the two object classes described in the previous section.
vlvBase
Defines the base DN of a VLV search.
Property
Value
Entry DN
cn=MCCtargetDN,cn=databaseName,cn=ldbm database,cn=plugins,cn=config
Valid Range
N/A
Default Value
N/A
Syntax
DN
Example
vlvBase: o=example.com
vlvEnabled
Used by the server to signal whether the index is available or unavailable. When VLV indexes are created offline, new vlvSearch entries are enabled when the indexes are rebuilt. VLV indexes can also be created while the server is running in read-only mode. This attribute is read-only and single-valued.
Property
Value
Entry DN
cn=by MCCtargetDN,cn=MCCtargetDN,cn=databaseName,cn=ldbm database,cn=plugins,cn=config
Valid Range
0
Default Value
N/A
Syntax
Integer
Example
vlvEnabled: 0
vlvFilter
Defines the filter for a VLV search.
Property
Value
Entry DN
cn=MCCtargetDN,cn=databaseName,cn=ldbm database,cn=plugins,cn=config
Valid Range
Default Value
N/A
Syntax
IA5String
Example
vlvFilter: (uid>=r)
vlvScope
Defines the scope of a VLV search.
vlvSort
Defines the sort specification for a VLV search, and contains a space-separated list of attribute names. A minus sign is used to denote a reverse sort. The example below will result in a sort by uid, then by reverse common name.
Property
Value
Entry DN
cn=by MCCtargetDN,cn=MCCtargetDN,cn=databaseName,cn=ldbm database,cn=plugins,cn=config
Valid Range
N/A
Default Value
N/A
Syntax
DirectoryString
Example
vlvSort: uid -cn
vlvUses
This read-only attribute displays the number of times the VLV index was used. This number resets after a restart of the server.
Property
Value
Entry DN
cn=by MCCtargetDN,cn=MCCtargetDN,cn=databaseName,cn=ldbm database,cn=plugins,cn=config
Valid Range
1-x
Default Value
N/A
Syntax
Integer
Example
vlvUses: 7
Chained Suffix Plug-In Attributes
The chained suffix plug-in is organized in an information tree as shown below:
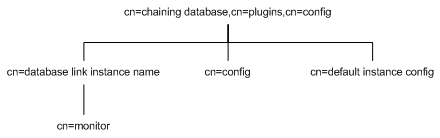
All plug-in technology used by the chained suffix instances is stored in the cn=chaining database plug-in node. This section presents the additional attribute information for the three nodes marked in bold in the cn=chaining database,cn=plugins,cn=config information tree. For more information on the chaining backend, refer to "Creating Chained Suffixes" in Chapter 3 of the Sun ONE Directory Server Administration Guide.
Chained Suffix Attributes
Global chained suffix configuration attributes common to all instances are stored under cn=config,cn=chaining database,cn=plugins,cn=config.
nsActiveChainingComponents
Lists the components using chaining. A component is any functional unit in the server. The value of this attribute overrides the value in the global configuration attribute. To disable chaining on a particular database instance, use the value None.
This attribute also allows you to alter the components used to chain. By default, no components are allowed to chain. For this reason, this attribute does not appear in a list of cn=config,cn=chaining database,cn=config attributes, as LDAP considers empty attributes to be non-existent.
nsMaxResponseDelay
This error detection, performance related attribute specifies the maximum period of time it can take a remote server to respond to an LDAP operation request made by a chained suffix before an error is suspected. Once this delay period has been met, the chained suffix tests the connection with the remote server.
Property
Value
Entry DN
cn=config,cn=chaining database,cn=plugins,cn=config
Valid Range
Any valid delay period in seconds.
Default Value
60 seconds
Syntax
Integer
Example
nsMaxResponseDelay: 60
nsMaxTestResponseDelay
This error detection, performance related attribute specifies the duration of the test issued by the chained suffix to check whether the remote server is responding. If a response from the remote server is not returned within this period, the chained suffix assumes the remote server is down and the connection is not used for subsequent operations.
Property
Value
Entry DN
cn=config,cn=chaining database,cn=plugins,cn=config
Valid Range
Any valid delay period in seconds.
Default Value
15 seconds
Syntax
Integer
Example
nsMaxTestResponseDelay: 15
nsTransmittedControls
This attribute, which can be both a global (and thus dynamic) configuration or an instance (cn=chained suffix instance,cn=chaining database, cn=plugins,cn=config) configuration attribute, allows you to alter the controls that the chained suffix forwards. The following controls are forwarded by default:
- Managed DSA, object identifier: 2.16.840.1.113730.3.4.2.
- Virtual list view (VLV), object identifier: 2.16.840.1.113730.3.4.9
- Server side sorting, object identifier: 1.2.840.113556.1.4.473
Default Instance Chained Suffix Attributes
Default instance chained suffix attributes are stored under cn=default instance config,cn=chaining database,cn=plugins,cn=config.
nsAbandonedSearchCheckInterval
The number of seconds that pass before the server checks for abandoned operations.
nsBindConnectionsLimit
Maximum number of TCP connections the chained suffix establishes with the remote server.
Property
Value
Entry DN
cn=default instance config,cn=chaining database, cn=plugins,cn=config
Valid Range
1 to 50 connections
Default Value
3
Syntax
Integer
Example
nsbindconnectionslimit: 3
nsBindRetryLimit
Number of times a chained suffix attempts to bind with the remote server if the initial bind attempt is unsuccessful. A value of 0 here indicates that the chained suffix will only attempt to bind once only.
Property
Value
Entry DN
cn=default instance config,cn=chaining database, cn=plugins,cn=config
Valid Range
0 to 5
Default Value
3
Syntax
Integer
Example
nsbindretrylimit: 3
nsBindTimeout
Period of time before the bind attempt times out. There is no real Valid Range for this attribute, except reasonable patience limits.
Property
Value
Entry DN
cn=default instance config,cn=chaining database, cn=plugins,cn=config
Valid Range
0 to 60 seconds
Default Value
15
Syntax
Integer
Example
nsbindtimeout:15
nsCheckLocalACI
Reserved for advanced use only. Controls whether ACIs are evaluated on the chained suffix as well as the remote data server. Changes to this attribute only take effect once the server has been restarted.
Property
Value
Entry DN
cn=default instance config,cn=chaining database, cn=plugins,cn=config
Valid Range
on | off
Default Value
off
Syntax
DirectoryString
Example
nschecklocalaci: on
nsConcurrentBindLimit
The maximum number of concurrent bind operations per TCP connection.
Property
Value
Entry DN
cn=default instance config,cn=chaining database, cn=plugins,cn=config
Valid Range
1 to 25 binds
Default Value
10
Syntax
Integer
Example
nsconcurrentbindlimit:10
nsConcurrentOperationsLimit
The maximum number of concurrent operations allowed.
Property
Value
Entry DN
cn=default instance config,cn=chaining database, cn=plugins,cn=config
Valid Range
1 to 50 operations
Default Value
50
Syntax
Integer
Example
nsconcurrentoperationslimit: 50
nsConnectionLife
Specifies the connection lifetime. You can keep connections between the chained suffix and the remote server open for an unspecified time, or you can close them after a specific period of time. Keeping the connections open is faster, but uses more resources. When the value is 0 and a list of failover servers is provided in the nsFarmServerURL attribute, the "main" server is never contacted after failover to the alternate server.
nsOperationConnectionsLimit
Maximum number of LDAP connections the chained suffix establishes with the remote server.
Property
Value
Entry DN
cn=default instance config,cn=chaining database, cn=plugins,cn=config
Valid Range
1 to 20 connections
Default Value
10
Syntax
Integer
Example
nsoperationconnectionslimit:10
nsProxiedAuthorization
Reserved for advanced use only, this attribute permits you to disable proxied authorization. A value of off means that proxied authorization is disabled.
Property
Value
Entry DN
cn=default instance config,cn=chaining database, cn=plugins,cn=config
Valid Range
on | off
Default Value
on
Syntax
DirectoryString
Example
nsproxiedauthorization: on
nsReferralOnScopedSearch
Controls whether or not referrals are returned by scoped searches. This attribute allows you to optimize your directory, because returning referrals in response to scoped searches is more efficient.
Property
Value
Entry DN
cn=default instance config,cn=chaining database, cn=plugins,cn=config
Valid Range
on | off
Default Value
off
Syntax
DirectoryString
Example
nsreferralonscopedsearch: off
nsslapd-sizelimit
Specifies the size limit of an entry for the chained suffix, in bytes.
nsslapd-timelimit
Specifies the default search time limit for the chained suffix.
Property
Value
Entry DN
cn=default instance config,cn=chaining database, cn=plugins,cn=config
Valid Range
-1 to 2147483647 seconds
Default Value
3600
Syntax
Integer
Example
nsslpad-timelimit: 3600
Instance-Specific Chained Suffix Attributes
Instance-specific chained suffix attributes are stored under cn=chained suffix instance name,cn=chaining database,cn=plugins,cn=config.
nsFarmServerURL
The LDAP URL of the remote server. A farm server is contains data in one or more databases. This attribute can contain optional servers for failover, separated by spaces. For cascading chaining, this URL can point to another chained suffix.
nsMultiplexorBindDN
DN of the administrative entry used to communicate with the remote server. The multiplexor is the server that contains the chained suffix and communicates with the farm server. This bind DN cannot be the Directory Manager. If this attribute is not specified, the chained suffix binds as anonymous.
nsMultiplexorCredentials
Password for the administrative user, in plain text. If no password is provided, users can bind as anonymous. The password is encrypted in the configuration file. Please note that the example below is what you view, not what you type.
nshoplimit
Specifies the maximum number of times a suffix is allowed to chain, that is, the number of times a request can be forwarded from one chained suffix to another.
Chained Suffix Monitoring Attributes
Table 5-4 lists the chained suffix attributes used for monitoring activity on instances. These attributes are stored under cn=monitor,cn=database instance name,cn=chaining database,cn=plugins,cn=config.
Frontend Plug-In Attributes
The frontend plug-in enables you to access directory data by methods other than LDAP. Sun ONE Directory Server 5.2 provides a DSML frontend plug-in that enables access using DSMLv2 over HTTP/SOAP. Attributes for the DSML frontend plug-in are stored under cn=DSMLv2-SOAP-HTTP,cn=frontends,cn=plugins,cn=config.
ds-hdsml-clientauthmethod
Defines how the server will identify a client on a secure (SSL) connection.
ds-hdsml-dsmlschemalocation
The path to the DSMLv2 schema. This is generated automatically and should not be changed.
ds-hdsml-iobuffersize
The size of the buffer in which the DSML request is stored.
ds-hdsml-poolmaxsize
The maximum size of the pool of parsers.
ds-hdsml-poolsize
The minimum (and default) size of the pool of parsers
ds-hdsml-port
The HTTP port used for DSML communications. The selected port must be unique on the host system; make sure no other application is attempting to use the same port number. On UNIX systems, specifying a port number of less than 1024 requires the Directory Server to run as root.
Note that you must restart the server for a port number change to be taken into account.
Property
Value
Entry DN
cn=DSMLv2-SOAP-HTTP,cn=frontends,cn=plugins,cn=config
Valid Range
1-65535
Default Value
80
Syntax
Integer
Example
ds-hdsml-port: 8080
ds-hdsml-requestmaxsize
The maximum size of a DSML request. If the request is larger than this value, the server responds with the error message REQUEST_ENTITY_TOO_LARGE and closes the connection to prevent the client from continuing the request.
Property
Value
Entry DN
cn=DSMLv2-SOAP-HTTP,cn=frontends,cn=plugins,cn=config
Valid Range
1-2147483647 (231-1)
Default Value
32768
Syntax
Integer
Example
ds-hdsml-requestmaxsize: 32768
ds-hdsml-responsemsgsize
The maximum size of a server response to a DSML request (or a fraction of the maximum response size in the case of intermediate search responses).
Property
Value
Entry DN
cn=DSMLv2-SOAP-HTTP,cn=frontends,cn=plugins,cn=config
Valid Range
1-2147483647 (231-1)
Default Value
65536
Syntax
Integer
Example
ds-hdsml-responsemsgsize: 65536
ds-hdsml-rooturl
The root URL that will be used in a DSML request.
Property
Value
Entry DN
cn=DSMLv2-SOAP-HTTP,cn=frontends,cn=plugins,cn=config
Valid Range
Any valid URL.
Default Value
/dsml
Syntax
DirectoryString
Example
ds-hdsml-rooturl: /dsml
ds-hdsml-secureport
The port number used for secure DSML communications (over SSL). The selected port must be unique on the host system; make sure no other application is attempting to use the same port number. On UNIX systems, specifying a port number of less than 1024 requires the Directory Server to run as root. Note that you must restart the server for a port number change to be taken into account.
Property
Value
Entry DN
cn=DSMLv2-SOAP-HTTP,cn=frontends,cn=plugins,cn=config
Valid Range
1-65535
Default Value
None
Syntax
Integer
Example
ds-hdsml-secureport: 1443
ds-hdsml-soapschemalocation
The path to the SOAP schema. This is generated automatically and should not be changed.
Implementation of the DSMLv2 Standard
The complete DSMLv2 specification and supporting documentation can be found at:
http://www.oasis-open.org/committees/dsml/docs/DSMLv2.xsd and
http://www.oasis-open.org/committees/dsml/docs/DSMLv2.doc
The Sun ONE Directory Server implementation of this specification is complete, with the following restrictions:
- Bindings
DSMLv2 defines two normative bindings: a SOAP request/response binding and a file binding that serves as the DSMLv2 analog of LDIF. Sun ONE Directory Server supports the SOAP request/response binding.
- Modify DN
Sun ONE Directory Server supports the DSML modDNRequest and modDNResponse operations. Changing of a DN is supported; however, moving an entry to a different part of the directory tree is not supported.
- Abandon Request
Sun ONE Directory Server does not support the abandonRequest operation, since this operation is of no use over HTTP.
- Search Operations
Some DSML clients incorrectly send an equality match with value "*" when a presence match is intended. The directory server will return zero results from these misformatted queries. You can detect these incorrect clients by searching for the characters =\2a in the access log.
Content of the HTTP Header
Sun ONE Directory Server supports only the HTTP POST operation. The following example shows the minimum fields required to send a DSML request to the server over HTTP:
POST /dsml HTTP/1.1
content-length: 450
HOST: hostMachine
SOAPAction: ""
Content-Type: text/xml
Connection: closeThe Connection field is optional. In HTTP 1.0, the default value of this field is close. In HTTP 1.1, however, the default value is keep-alive. It is therefore recommended that you include this field with a value of close in your last request if you are using HTTP 1.1, to accelerate the dialog.
Additional fields may be included in the HTTP header. If they are supported by Directory Server, their values will override the defaults. If the fields are not supported, the request will not be rejected by the server but the fields will be ignored.
Retro Changelog Plug-In Attributes
Two different types of changelogs are maintained by Sun ONE Directory Server 5.2. The first type, referred to as changelog, is used by multi-master replication and the second changelog, which is in fact a plug-in referred to as retro changelog, is intended for use by LDAP clients for maintaining application compatibility with Directory Server 4.x versions.
This Retro Changelog plug-in is used to record modifications made to a supplier server. When the supplier server's directory is modified, an entry is written to the Retro Changelog that contains:
- A number that uniquely identifies the modification. This number is sequential with respect to other entries in the change log.
- The modification action; that is, exactly how the directory was modified.
It is through the Retro Changelog plug-in that you access the changes performed to the Directory Server using searches to "cn=changelog,cn=config" file.
nsslapd-changelogdir
This attribute specifies the name of the directory in which the changelog database is created the first time the plug-in is run. By default the database is stored with all the other databases under:
ServerRoot/slapd-serverID/db/changelog
Note For performance reasons you will probably want to store this database on a different physical disk.
nsslapd-changelogmaxage (Max Changelog Age)
Specifies the maximum age of any entry in the change log. The change log contains a record for each directory modification and is used when synchronizing consumer servers. Each record contains a timestamp. Any record with a timestamp that is older than the value specified in this attribute will be removed. If this attribute is absent, there is no age limit on change log records, which is the default behavior as this attribute is not present by default.
nsslapd-changelogmaxentries (Max Changelog Entries)
Specifies the maximum number of entries in the change log. The change log contains a record for each directory modification and is used when synchronizing consumer servers.
Subtree Entry Counter Plug-In Attributes
The subtree entry counter plug-ins maintain a count of entries with a particular object class. The counter attributes are listed in Table 5-5.