Chapter 2 Installing Keys and Certificates
It you have installed SunScreen SKIP on your machine, you must set it up so that it can talk to other systems. This chapter tells you how to install keys and certificates on your system.
Note -
If you installed an UDH certificate during installation, the information in this chapter will not apply to you unless you also plan to install SunCA keys and certificates.
There are two kinds of certificates that you can use with SunScreen SKIP:
-
UDH
-
SunCA
Which certificates you choose to use is determined by the security policy of your company.
At the end of the installation process in Chapter 1 ("Installation Procedure"), you created a SKIP UDH certificate using the skiplocal command.
Note -
You must be root to use the command-line commands.
You may use the install_skip_keys command to install SunCA keys and certificates on SunScreen SKIP at the same time. This section shows how to install certificates signed by the SunCA.
Keys and Certificates
Keys
Traditional cryptography relies on the sender and receiver of a message knowing and using the same secret key. When both sender and receiver use the same secret key, the system is referred to as a symmetric or single-key crypto system. The problems with using the same secret key are: how is one selected, how do the parties inform each other of the secret key if they are not physically in the same location, how do they change keys from time to time, and how is the secret key kept secure.
Public-key cryptography was proposed as a solution to the problems found in traditional, symmetric key cryptography. In public-key cryptography, each person, host, or network participating in a coded exchange, receives a pair of keys: one public and one private. The private key is kept a secret and the public key is published so that anyone who wishes to communicate confidentially with a person or an entity can do so by encoding their message using the public key. The confidential message can then only be decoded by the private key, which is kept in the sole possession of the intended recipient.
SKIP is a public-key, certificate-based, key-management scheme. It uses certified Diffie-Hellman public values to eliminate the need for prior communications between two entities wishing to exchange encrypted data.
There are times when it is useful to allow a system to have more than one pair of public-private keys. For example, different key sizes may be required when communicating with subsidiaries in other countries because of U.S. or local regulations. To meet these user requirements, SunScreen SKIP's implementation permits a system to possess as many local keys as required. Public-private key pairs like UDH keys can be used for authentication.
Certificates
To ensure that a public key is authentic (that is, it has not been tampered with by an unauthorized user and does indeed belong to the claimant), the public key is normally signed by a Certification Authority (CA). The result, a digital document called a certificate, can be freely passed around the network. Its authenticity can be verified by anyone holding the CA's signature information; that is, the CA's public key.
Before any form of encrypted communication can begin, the parties involved in the transaction must exchange certificates. This is a manual procedure in that the certificate and possibly the key are provided by the certifying agency on physical media: tape, diskette, or CD-ROM. The user must load them into the system through a command-line interface.
Key and Certificate Management
Secure key management is a necessary requirement for any cryptographic product. Users must be able to obtain keys as required for their security needs, have a method of looking up other's public keys, publicize their own keys, and determine that a key is valid. Certificates are used for this purpose.
Certificates must be unforgettable, obtainable in a secure manner, and processed in such a way that an unauthorized user cannot misuse them. This means that the network manager must handle the following issues:
-
Loss or compromise of a private key
-
Verifiable signature after key expiration
-
Expiration dates
-
Secure storage of private keys
Adding Certificates or Local Identities with install_skip_keys
The install_skip_keys command is used to install key packages that have been received from a key server or from one of the SunCAs. If used with-icg, it means that the SunCA or the SunCAglobal CA certified the keys. The SunCA certifies 1024-bit and 2048-bit modulus certificates, and the SunCAglobal certifies 512-bit certificates.
To communicate with a SunScreen SPF-100 or SunScreen SPF-100 G, you need to use SunCA or SunCAglobal certificates.
Note -
The install_skip_keys command is not used to add someone else's certificate. It is only used to install local identities for CA key packages.
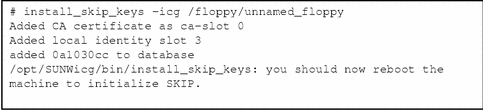
The Figure 2-1 shows installing a SunCAglobal key and certificate from diskettes. After installing the key and certificate, because you have added a new local identity, you must either run the skipd_restart command or reboot your system to initialize the key manager.
Figure 2-1 Installing a SunCA Global Key and Certificate from Diskette
For more information on install_skip_keys, see the man pages.
- © 2010, Oracle Corporation and/or its affiliates
