Setting Up an Encrypted Connection Between Two or More Hosts
Figure 5-1 depicts the configuration in which a host has an encrypted connection to another host. This is the simplest case.
Figure 5-1 Communicating with a Host
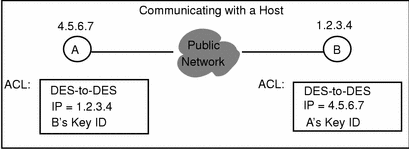
Figure 5-1 is an example of host-to-host communication using UDH keys and SKIP.
All the hosts must:
-
Share the same key types, such as UDH, SunCA X.509, or the like, and of the same encryption strength. If X.509 certificates and keys are used, the certificates and keys for both hosts must be from the same vendor.
-
Exchange certificates.
-
Have the same algorithm to use that includes authentication, key encryption, and traffic encryption.
-
Enable SKIP.
A machine must also have a local identity. Hosts can have many identities, but the user must choose one with which to communicate to the other host. This local identity consists of the local key type (NSID) and the local key name.
The hosts must exchange key IDs. The safest method of exchanging UDH key IDs is to have each user run skiptool, then call each other on the telephone and type the other's UDH key ID in the Remote Key ID field in the Add window.
UDH key IDs can be exchanged and added to the ACL of each using the skiplocal export command. In this case, both system administrators should telephone one another and confirm the key ID.
The address of each host with which a host wants to communicate must be in its ACL.
- © 2010, Oracle Corporation and/or its affiliates
