Using Tunnel Addresses
Figure 5-5 depicts the configuration in which a host is communicating with a hidden system through a tunnel address to an encrypting gateway. The hidden system also uses a tunnel address from the encrypting gateway to the host.
Figure 5-5 Using Tunnel Addresses
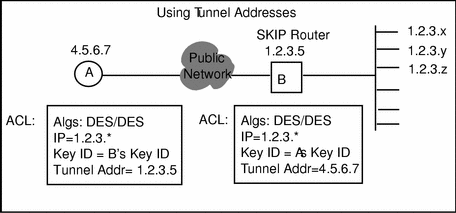
In tunneling, the packets are sent from the host to the gateway. The packets are encrypted such that the gateway decrypts them and sends them to their final destination in the clear.
When setting up tunneling, the user must add the address for the gateway into the host's ACL because there is no way that the host can discover the gateway's certificate.
- © 2010, Oracle Corporation and/or its affiliates
