| Skip Navigation Links | |
| Exit Print View | |
|
Oracle Identity Synchronization for Windows 6.0 Installation and Configuration Guide |
| Skip Navigation Links | |
| Exit Print View | |
|
Oracle Identity Synchronization for Windows 6.0 Installation and Configuration Guide |
Part I Installing Identity Synchronization for Windows
Windows NT Connector Subcomponents
System Components Distribution
Directory Server Connector and Plug-in
Windows NT Connector and Subcomponents
How Identity Synchronization for Windows Detects Changes in Directory Sources
How Directory Server Connectors Detect Changes
How Active Directory Connectors Detect Changes
How Windows NT Connectors Detect Changes
Using the Password Filter DLL to Obtain Clear-Text Passwords
Using On-Demand Password Synchronization to Obtain Clear-Text Passwords
6. Synchronizing Existing Users and User Groups
9. Understanding Audit and Error Files
Part II Identity Synchronization for Windows Appendixes
A. Using the Identity Synchronization for Windows Command Line Utilities
B. Identity Synchronization for Windows LinkUsers XML Document Sample
C. Running Identity Synchronization for Windows Services as Non-Root on Solaris
D. Defining and Configuring Synchronization User Lists for Identity Synchronization for Windows
E. Identity Synchronization for Windows Installation Notes for Replicated Environments
This section describes a deployment scenario in which Identity Synchronization for Windows is used to synchronize user object creation and bidirectional password modification operations between Directory Server and Active Directory sources.
The deployment scenario consists of two machines:
A machine running a Sun Java System Directory Server (host name: corp.example.com)
A machine running Active Directory on a Windows 2000 Server (host name: sales.example.com)
Note - Even though Windows NT is not used in this scenario, Identity Synchronization for Windows also supports synchronization with NT domains.
The following figure illustrates the synchronization requirements (node structures with associated attribute values) used for this deployment scenario.
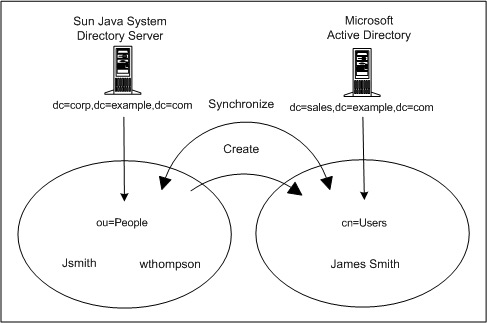
The two goals for this scenario are as follows:
To synchronize user passwords bidirectionally between the user subtrees (ou=people in Directory Server and cn=users in Active Directory), which means that whenever a user password changes in either directory, the password change is synchronized to the associated user in the other directory.
For example, if you change the password for uid=Jsmith in the ou=people container in the Directory Server, the new password should automatically be synchronized to cn=James Smith in the cn=users container in Active Directory.
To synchronize user object creation operations from the Directory Server people subtree to the Active Directory user subtree only.
For example, if you create a new user uid=WThompson in the ou=People container with a specified set of attributes, Identity Synchronization for Windows will create a new account cn=William Thompson in the cn=Users container with the same set of attributes in Active Directory.
Note - Identity Synchronization for Windows supports multiple synchronization sources of the same type. For example, you can have more than one Directory Server in a deployment or multiple Active Directory domains.
Creation, modification, and deletion synchronization settings are global for the entire set of directories, and cannot be specified for individual directory sources. If you synchronize user object creations from Directory Server to Active Directory, user object creations will propagate from all Directory Servers to all Active Directory domains and Windows NT domains configured in the installation.
The following figure illustrates how all the product’s components are physically deployed on a single Solaris system, while the Active Directory domain resides in a separate Active Directory domain controller where no components have been installed.
Figure 1-7 Directory Server and Active Directory Scenario
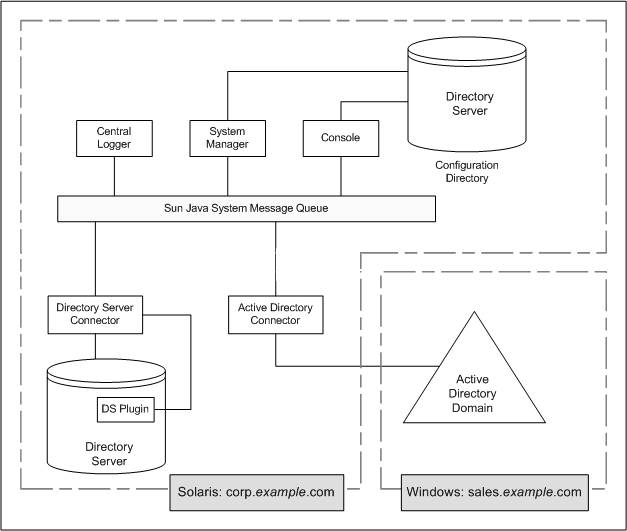
corp.example.com is a machine where Directory Server is installed on a Solaris operating system. The root suffix for the Directory Server instance being synchronized is dc=corp,dc=example,dc=com.
This topology contains the following:
Identity Synchronization for Windows Core components
Identity Synchronization for Windows Directory Server Connector
Identity Synchronization for Windows Directory Server Plug-in
Identity Synchronization for Windows configuration directory (located in a different Directory Server instance than the one being synchronized)
sales.example.com is the Active Directory domain being synchronized.