| Skip Navigation Links | |
| Exit Print View | |

|
Oracle Fusion Middleware Administration Guide for Oracle Unified Directory 11g Release 1 (11.1.1) |
| Skip Navigation Links | |
| Exit Print View | |

|
Oracle Fusion Middleware Administration Guide for Oracle Unified Directory 11g Release 1 (11.1.1) |
1. Starting and Stopping the Server
2. Configuring the Server Instance
3. Configuring the Proxy Components
4. Configuring Security Between Clients and Servers
5. Configuring Security Between the Proxy and the Data Source
How the Proxy Manages Secure Connections
Configuring Security Between the Proxy and Data Source Using dsconfig
To Configure Security Between the Proxy and Directory Servers Using dsconfig
Configurable LDAP Extension Properties Relevant to Security
Setting Access Control Using Network Group Criteria
6. Managing Oracle Unified Directory With Oracle Directory Services Manager
10. Managing Users and Groups With dsconfig
11. Managing Password Policies
The Oracle Unified Directory proxy handles connections to the remote LDAP servers in three SSL security modes:
always
never
user
You can view or edit these settings using the dsconfig --advanced command. Choose Extension from the main menu.
The remote-ldap-server-ssl-policy property manages the three SSL security modes.
When the remote-ldap-server-ssl-policy property is set to always or user, the Oracle Unified Directory proxy needs to trust the remote LDAP servers. To achieve this, you need to manually import the certificates of each remote LDAP server into the proxy's truststore.
With the remote-ldap-server-ssl-policy property set to always, all connections made from the proxy to the remote LDAP servers are fully secure SSL connections, regardless how the client connects to the proxy.
In this mode, the pool size refers to one type of connection pool: secure LDAPS connections.
In the always secure mode, the certificate of each remote LDAP server must be imported into the truststore of the Oracle Unified Directory proxy. If there is a large number of back-end LDAP servers that are not Oracle Unified Directory servers, and if certificates were not managed during installation, importing certificates into the truststore of the Oracle Unified Directory proxy can be a constraint. For test environment purposes, you can speed up this process by using the ssl-trust-all parameter. This parameter requests the proxy to trust all remote LDAP servers.
With the remote-ldap-server-ssl-policy property set to never, none of the connections from the Oracle Unified Directory proxy to the remote LDAP servers are secure SSL connections.
In this mode, the monitoring connection by Oracle Unified Directory proxy of the remote LDAP servers is never secure.
In this mode, the pool size refers to one type of connection pool: unsecure LDAP connections.
With the remote-ldap-server-ssl-policy property set to user, incoming requests from clients to the proxy dictate whether the connection between the Oracle Unified Directory proxy and remote LDAP servers should be secure, regardless how the client connects to the Oracle Unified Directory proxy.
If the incoming client request is secure, whether SSL or StartTLS, the connection from the Oracle Unified Directory proxy to the remote LDAP servers is a secure SSL connection.
If the incoming client request is not secure, the connection from the Oracle Unified Directory proxy to the remote LDAP servers is not a secure SSL connection.
In this mode, the monitoring connection by Oracle Unified Directory proxy of the remote LDAP servers is never secure.
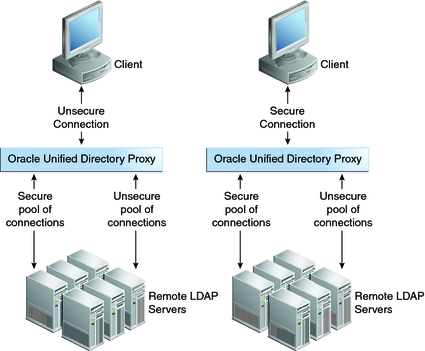
Two pools of connections are created, one secure and one unsecure. This is shown in Figure 5-1. In the scenario on the left, the client connects to Oracle Unified Directory proxy using an unsecure connection, and the unsecure pool of connections from the proxy to the remote LDAP servers is used. In the scenario on the right, the client connects to proxy using a secure connection, whether SSL or StartTLS, and the secure SSL pool of connections from Oracle Unified Directory proxy to the remote LDAP servers is used.
Figure 5-1 Connections in the user Secure Mode
In the user mode, the certificate of each remote LDAP server must be imported into the truststore of the Oracle Unified Directory proxy. If there is a large number of remote LDAP servers that are not Oracle Unified Directory servers, and if certificates were not managed during installation, importing certificates into the truststore of the Oracle Unified Directory proxy can be a constraint. For test environment purposes, you can speed up this process by using the ssl-trust-all parameter. This parameter requests the Oracle Unified Directory proxy to trust all remote LDAP servers.
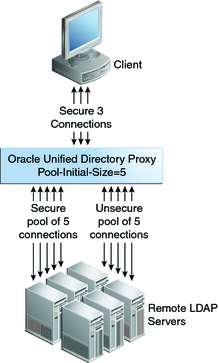
When the remote-ldap-server-ssl-policy property is set to user, the pool size refers to two types of connection pools: unsecure LDAP connections and secure LDAPS connections. If for example the pool-initial-size is set to 5 connections, as shown in Figure 5-2, then when the LDAP Extension is initialized, there will be one pool of 5 LDAP connections and one pool of 5 LDAPS connections, or a total of 10 connections. Each pool evolves separately after this initialization, based on parameters set for that pool.
Note - By default, pool-initial-size is set to 10 connections.
Figure 5-2 Multiple Pools of Connections