1 About the Fusion Apps Connector
The Fusion Apps connector integrates Oracle Identity Manager (OIM) with the Fusion Apps target system.
The following topics provide a high-level overview of the Fusion Apps connector:
1.1 Introduction to the Fusion Apps Connector
The Fusion Apps connector enables you to use Fusion Apps as a managed (target) source of identity data for Oracle Identity Manager.
Note:
At some places in this guide, Fusion Apps has been referred to as the target system.The Fusion Apps Connector aims to allow provisioning and reconciliation operations on the target including trusted and target operations. In the account management (target resource) mode of the connector, information about users created or modified directly on the target system can be reconciled into Oracle Identity Manager.
Note:
The Fusion Apps Connector consists of FA User Request service and FA Identity service for performing various operations. The FA User Request service is used to perform trusted reconciliation operation and is ATOM based. The FA Identity service is used to perform provisioning and target reconciliation operations and is System for Cross-domain Identity Management (SCIM) based.FA Identity REST service is used to perform provisioning and reconciliation operations for users present on the target system. Reconciliation operation is performed only for those users who have an externalID, which indicates that the users are managed by Oracle Identity Manager. To perform a trusted reconciliation operation, the connector uses the FA User Request service. The Fusion Apps Connector aims to allow provisioning and reconciliation operations on the target including trusted and target operations. To perform a trusted reconciliation operation, the Fusion Apps Connector uses the FA User Request service. To perform a target provisioning and reconciliation operation, the connector uses the FA Identity service.
During a provisioning operation, Single Sign-On (SSO) accounts are first created for all the users and the respective SSO mail IDs are updated back in the target system. If the SSO email is updated later through Oracle Identity Manager, then the updated email is also propagated to the target system.
In the identity reconciliation (trusted source) configuration of the connector, users are created or modified only on the target system and information about these users is reconciled into Oracle Identity Manager. However, to perform target based provisioning or reconciliation, the connector uses the FA Identity service.
This connector is an integration between Oracle Identity Manager and Fusion Apps and makes use of the ATOM pub and SCIM RESTful services for managing users and entitlements in the target from Oracle Identity Manager.
1.2 Certified Components for the Fusion Apps Connector
These are the software components and their versions required for installing and using the Fusion Apps connector.
Table 1-1 lists the deployment requirements for the connector.
Table 1-1 Certified Components
| Component | Requirement |
|---|---|
|
Oracle Identity Governance or Oracle Identity Manager |
You can use one of the following releases of Oracle Identity Governance or Oracle Identity Manager:
|
|
Target System |
Fusion Apps Release 12, Release 13 |
|
Connector Server |
11.1.1.5.0 |
|
Connector Server JDK |
JDK 1.6 or later |
1.3 Certified Languages for the Fusion Apps Connector
These are the languages that the connector supports.
-
Arabic
-
Chinese (Simplified)
-
Chinese (Traditional)
-
Czech
-
Danish
-
Dutch
-
English (US)
-
Finnish
-
French
-
French (Canadian)
-
German
-
Greek
-
Hebrew
-
Hungarian
-
Italian
-
Japanese
-
Korean
-
Norwegian
-
Polish
-
Portuguese
-
Portuguese (Brazilian)
-
Romanian
-
Russian
-
Slovak
-
Spanish
-
Swedish
-
Thai
-
Turkish
1.4 Connector Architecture of the Fusion Apps Connector
The Fusion Apps connector is implemented by using the Identity Connector Framework (ICF).
The ICF is a component that provides basic reconciliation and provisioning operations that are common to all Oracle Identity Manager connectors. In addition, ICF provides common features that developers would otherwise need to implement on their own, such as connection pooling, buffering, time outs, and filtering. The ICF is shipped along with Oracle Identity Manager. Therefore, you need not configure or modify the ICF.
Following are the various topologies supported by the connector:
-
External HRMS or IDM Source of Truth – FA on Cloud or On-Premise Use Case
-
FA and External HRMS Source of Truth – FA on Cloud or On-Premise Use Case
-
FA Source of Truth With LDAPSync – FA on Cloud or On-Premise Use Case
-
External HRMS Source of Truth With LDAPSync – FA on Cloud or On-Premise Use Case
-
FA and External HRMS Source of Truth With LDAPSync – FA on Cloud or On-Premise Use Case
1.4.1 FA Source of Truth – Cloud or On-Premise Use Case
Topology 1: FA Source of Truth – Cloud or On-Premise Use Case
Figure 1-1 Connector Architecture: Topology 1
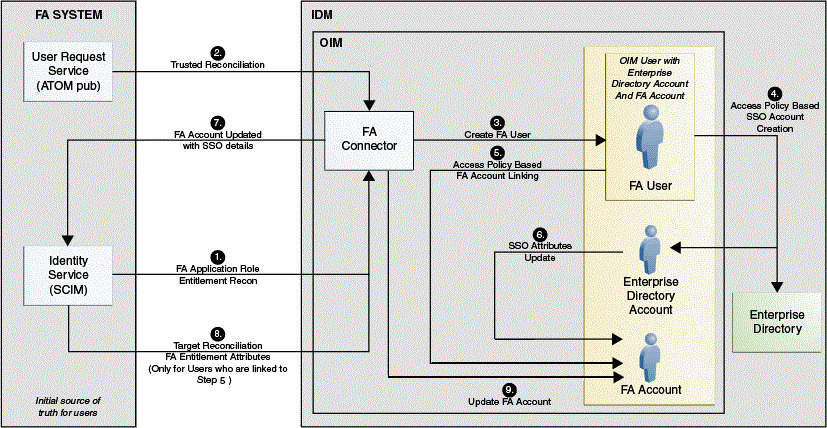
Description of "Figure 1-1 Connector Architecture: Topology 1"
In this use case, the FA user trusted reconciliation scheduled task will be using the FA User Request service REST API which is responsible for fetching all the users for the first time and later incrementally from the ATOM feed and create them in the Oracle Identity Manager repository. Once the users are successfully created, the FA Role for FA User will be defined in Oracle Identity Manager, which helps define a user membership rule based on the user profile attribute of the FA user created earlier. Once this role is defined, the FA access policy for FA user will be based on the role created earlier. This will be responsible for provisioning an enterprise directory account and also link an FA account for the user created earlier. This process of linking is performed in Oracle Identity Manager in order to ensure that the same can be used to update the SSO attributes back to the target system at a later stage. Additionally, in this use case, a FA Enterprise Directory Resource dependency also exists. To update the SSO, the Fusion Apps connector will ship an adapter which is responsible for copying all the SSO account details like email and username from the enterprise directory process form to the FA process form. Now, the Fusion Apps connector will update the FA account with SSO details using the Identity Service REST API. At this point, the user should be able to login to the target using the SSO details. Finally, the FA User Target Reconciliation scheduled task will use the Identity Service REST API to query all users for the first time and later incrementally followed by updating the FA user accounts in the Oracle Identity Manager. Once the manage FA user account is linked in an earlier stage, roles are listed in the Oracle Identity Manager catalog after which more entitlements can be requested for this Fusion Apps account. To request entitlements, in Step 1 of Figure 1-1 , you must run the FA Identity Service Application Roles Lookup Reconciliation schedule job to reconcile the FA Roles into Oracle Identity Manager and those roles will then list as entitlements. Through this, users can request these entitlement for the FA Account in Oracle Identity Manager itself.
1.4.2 External HRMS or IDM Source of Truth – FA on Cloud or On-Premise Use Case
Topology 2: External HRMS or IDM Source of Truth – FA on Cloud or On-Premise Use Case
Figure 1-2 Connector Architecture: Topology 2
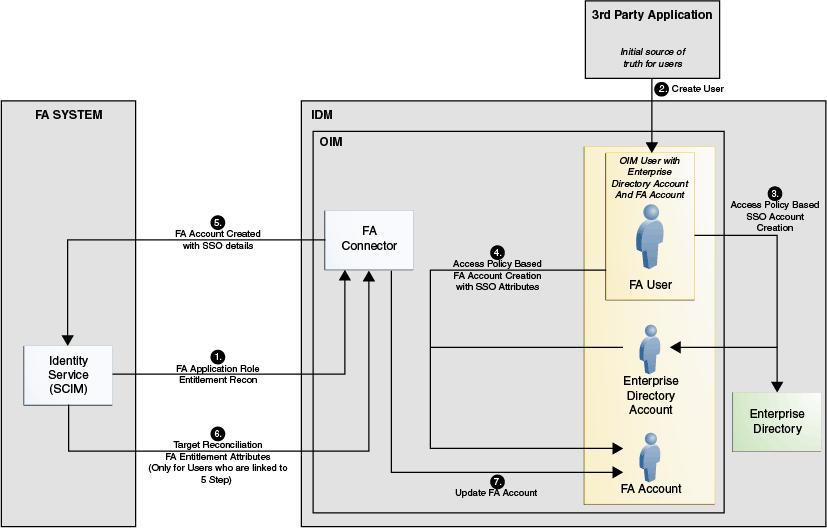
Description of "Figure 1-2 Connector Architecture: Topology 2"
In this use case, users are created in the Oracle Identity Manager repository by running the external HRMS user trusted reconciliation or through other means. After users are successfully created, the FA Role for External User role will be defined in Oracle Identity Manager which helps define a user membership rule based on an attribute of the Oracle Identity Manager user created earlier. Once this role is defined, the FA access policy for an external user will be based on the role created earlier. This policy will be responsible to provision an Enterprise Directory Account and an FA account for the user created earlier. The FA account will create an account in the FA target system as this account is not present in the FA target earlier. This creation will include the creation of SSO attributes and an externalID. The value for externalID will be provided when an Oracle Identity Manager user was created at an earlier instance. Additionally, in this use case, a FA OID resource dependency also exists. This dependency will ensure that an OID account will be provisioned followed by the provisioning of an FA account for users created earlier. Finally, the FA user target reconciliation scheduled task uses the Identity Service REST API to query all users for the first time and later incrementally followed by updating the FA user accounts in the Oracle Identity Manager. This task will get all the attributes of the Fusion Apps account including any entitlements assigned. However, this task will not get any SSO attributes and will also ensure that it will only get users who have their externalID values set.
1.4.3 FA and External HRMS Source of Truth – FA on Cloud or On-Premise Use Case
Topology 3: FA and External HRMS Source of Truth – FA on Cloud or On-Premise Use Case
Figure 1-3 Connector Architecture: Topology 3
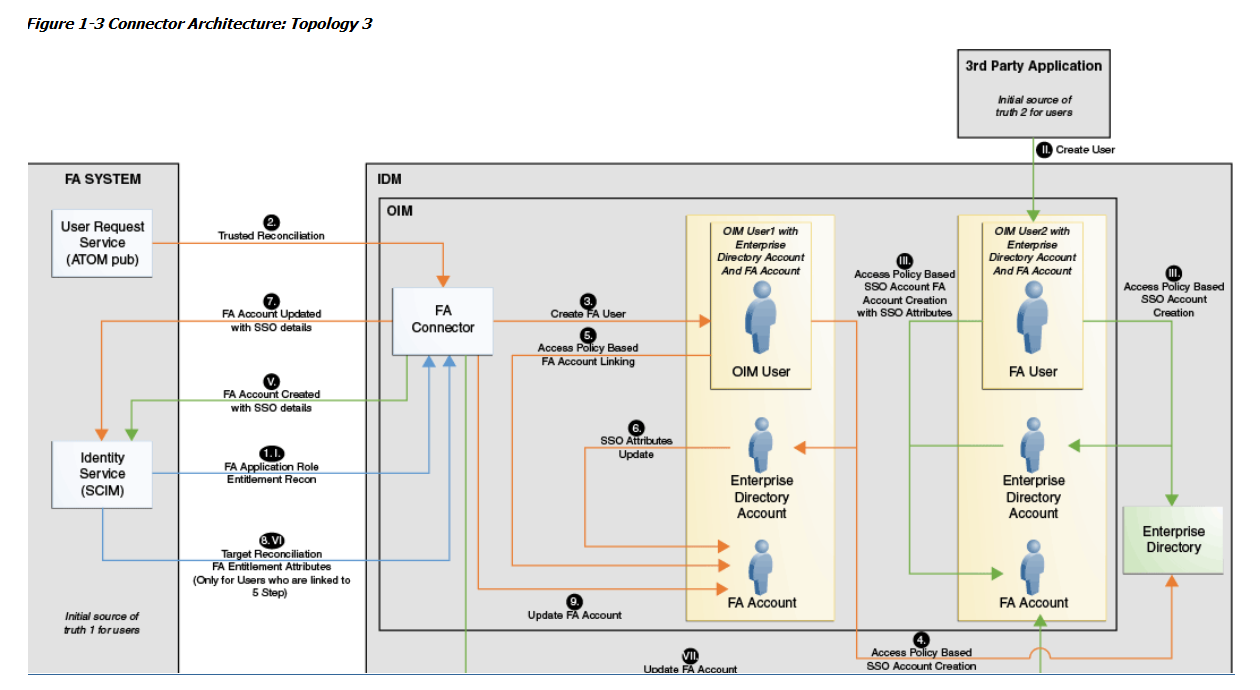
Description of "Figure 1-3 Connector Architecture: Topology 3"
This use case is a combination of the above two use cases where the source of truth are both FA target system and External HRMS. In this case, depending on the source, the role FA Role for FA User or FA Role for External User are associated to the user and their corresponding access policies. Additionally, based on the source, the FA User Accounts are either linked or created
1.4.4 FA Source of Truth With LDAPSync – FA on Cloud or On-Premise Use Case
Topology 4: FA Source of Truth With LDAPSync – FA on Cloud or On-Premise Use Case
Note:
This topology is not supported for Oracle Identity Governance 12c (12.2.1.3.0, 12.2.1.4.0). In the case that you upgrade to OIG 12c please refer to Integrating Oracle Identity Governance and Oracle Access Manager Using LDAP Connectors for LDAPSync.Figure 1-4 Connector Architecture: Topology 4
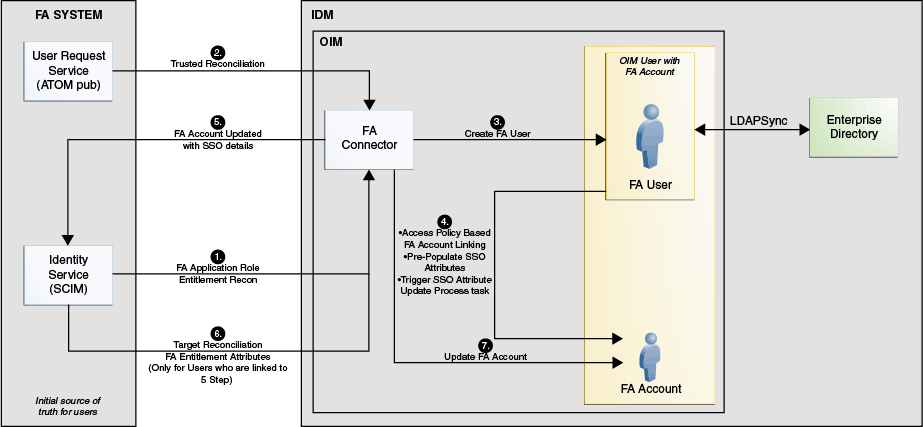
Description of "Figure 1-4 Connector Architecture: Topology 4"
This use case is similar to the use case discussed in FA Source of Truth – Cloud or On-Premise Use Case. In this use case, the LDAP Sync mode is responsible to manage users within LDAP. Here, Oracle Identity Manager with Oracle Internet Directory (OID) or iplanet (ODSEE) or Active Directory (AD) or Oracle Unified Directory (OUD) is selected during installation. It is not required to install any directory connector separately and the dependency of LDAP resource is managed internally in this use case.
1.4.5 External HRMS Source of Truth With LDAPSync – FA on Cloud or On-Premise Use Case
Topology 5: External HRMS Source of Truth With LDAPSync – FA on Cloud or On-Premise Use Case
Note:
This topology is not supported for Oracle Identity Governance 12c (12.2.1.3.0, 12.2.1.4.0). In the case that you upgrade to OIG 12c please refer to Integrating Oracle Identity Governance and Oracle Access Manager Using LDAP Connectors for LDAPSync.Figure 1-5 Connector Architecture: Topology 5
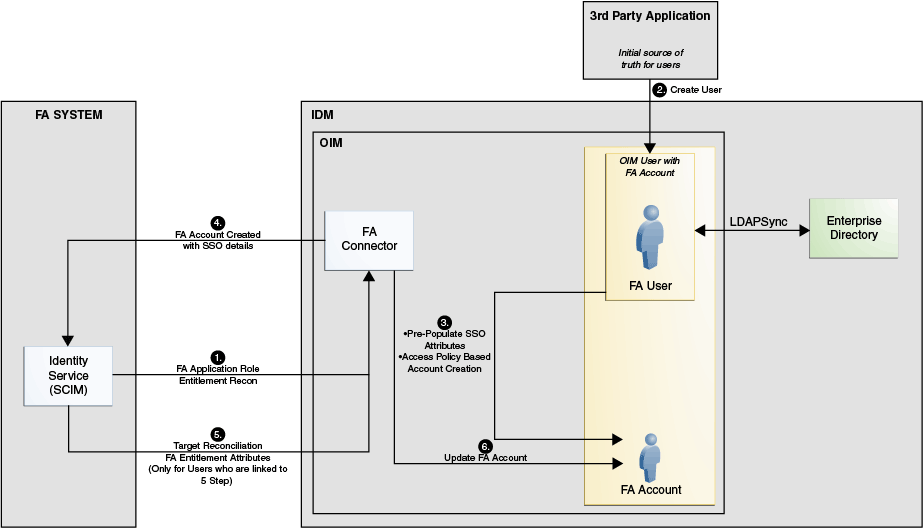
Description of "Figure 1-5 Connector Architecture: Topology 5"
This use case is similar to the use case discussed in External HRMS or IDM Source of Truth – FA on Cloud or On-Premise Use Case. In this use case, the LDAP Sync mode is responsible to manage users within LDAP. Here, Oracle Identity Manager with Oracle Internet Directory (OID) or iplanet (ODSEE) or Active Directory (AD) or Oracle Unified Directory (OUD) is selected during installation. It is not required to install any directory connector separately and the dependency of LDAP resource is managed internally in this use case.
1.4.6 FA and External HRMS Source of Truth With LDAPSync – FA on Cloud or On-Premise Use Case
Topology 6: FA and External HRMS Source of Truth With LDAPSync – FA on Cloud or On-Premise Use Case
Note:
This topology is not supported for Oracle Identity Governance 12c (12.2.1.3.0, 12.2.1.4.0). In the case that you upgrade to OIG 12c please refer to Integrating Oracle Identity Governance and Oracle Access Manager Using LDAP Connectors for LDAPSync.Figure 1-6 Connector Architecture: Topology 6
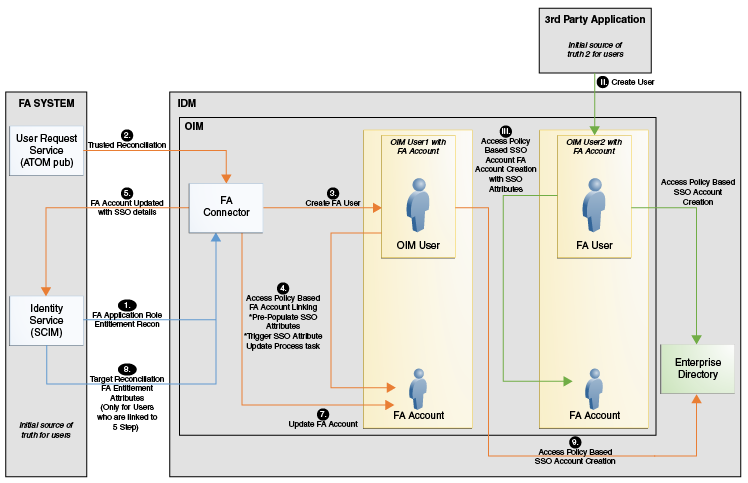
Description of "Figure 1-6 Connector Architecture: Topology 6"
This use case is similar to the use case discussed in FA and External HRMS Source of Truth – FA on Cloud or On-Premise Use Case. In this use case, the LDAP Sync mode is responsible to manage users within LDAP. Here, Oracle Identity Manager with Oracle Internet Directory (OID) or iplanet (ODSEE) or Active Directory (AD) or Oracle Unified Directory (OUD) is selected during installation. It is not required to install any directory connector separately as the dependency of the LDAP resource is managed internally in this use case.
1.5 Features of the Fusion Apps Connector
The features of the connector include support for connector server, full reconciliation, and limited reconciliation.
1.5.1 Full and Incremental Reconciliation
In full reconciliation, all records are fetched from the target system to Oracle Identity Manager.
After you deploy the connector, you can perform full reconciliation to bring all existing user data from the target system to Oracle Identity Manager. After the first full reconciliation run, incremental reconciliation is automatically enabled. In incremental reconciliation, user accounts that have been added or modified since the last reconciliation run are fetched into Oracle Identity Manager. You can perform a full reconciliation run at any time.
1.5.2 Limited Reconciliation
You can reconcile records from the target system based on a specified filter criterion.
To limit or filter the records that are fetched into Oracle Identity Manager during a reconciliation run, you can specify the subset of added or modified target system records that must be reconciled. See Limited Reconciliation for Fusion Apps Connector.
1.5.3 Batched Reconciliation
You can break down a reconciliation run into batches by specifying the number of records that must be included in each batch.
1.5.4 Reconciliation of Deleted User Records
You can configure the connector for reconciliation of deleted user records.
In the target resource mode (FA Non-authoritative) , if a user record is deleted on the target system, then the corresponding FA user resource is revoked from the OIM User. In trusted source mode (FA Authoritative mode), if a user record is deleted on the target system, then the corresponding OIM User is deleted. To perform FA Identity Service user delete reconciliation, you must specify values for Fusion Apps User Delete Reconciliation scheduled job. This scheduled job is used to reconcile data about deleted users in the target source (identity management) mode of the connector.
See Scheduled Job for Reconciliation of Deleted Users Records.
1.5.5 Transformation and Validation of Account Data
You can configure validation of account data that is brought into or sent from Oracle Identity Manager during reconciliation and provisioning.
In addition, you can configure transformation of account data that is brought into Oracle Identity Manager during reconciliation. The following sections provide more information:
1.5.6 Support for the Connector Server
Connector Server is one of the features provided by ICF. By using one or more connector servers, the connector architecture permits your application to communicate with externally deployed bundles.
A Java connector server is useful when you do not want to execute a Java connector bundle in the same VM as your application. It can be beneficial to run a Java connector on a different host for performance improvements if the bundle works faster when deployed on the same host as the native managed resource.
See Also:
Using an Identity Connector Server in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager for information about installing and configuring connector server and running the connector server
1.6 Lookup Definitions Used During Connector Operations
Lookup definitions used during reconciliation and provisioning are either preconfigured or can be synchronized with the target system.
Lookup definitions used during connector operations can be categorized as follows:
1.6.1 Lookup Definition Synchronized with the Target System
Lookup field synchronization involves copying additions or changes made to specific fields in the target system to lookup definitions in Oracle Identity Manager.
During a provisioning operation, you use a lookup field on the process form to specify a single value from a set of values. For example, you use the Identity Source lookup field to select an identity source during a provisioning operation performed through the Administrative and User Console. When you deploy the connector, lookup definitions corresponding to the lookup fields on the target system are automatically created in Oracle Identity Manager.
The Lookup.FAIdentityService.ApplicationRoles lookup definition is populated with values fetched from the target system by the scheduled jobs for lookup field synchronization.
During a provisioning operation, you use the Application Role Name lookup field on the process form to specify a role for the user for whom the provisioning operation is being performed. The Application Role Name lookup field is populated with values from the Lookup.FAIdentityService.ApplicationRoles lookup definition, which is automatically created on Oracle Identity Manager when you deploy the connector.
The Code Key and Decode columns contain values of the __UID__ and __NAME__ of the ApplicationRole object class.
Data in each of the lookup definitions for lookup field synchronization is stored in the following format:
<IT_RESOURCE_KEY>~<LOOKUP_FIELD_VALUE>
In this format:
-
IT_RESOURCE_KEY is the numeric code assigned to each IT resource in Oracle Identity Manager.
-
LOOKUP_FIELD_VALUE is the connector attribute value defined for code.
14~FARole1
<IT_RESOURCE_NAME>~<LOOKUP_FIELD_VALUE>
In this format:
-
IT_RESOURCE_NAME is the name of the IT resource in Oracle Identity Manager.
-
LOOKUP_FIELD_VALUE is the connector attribute value defined for decode.
FA Identity Service~FARole1
1.6.2 Preconfigured Lookup Definitions for the Fusion Apps Connector
Preconfigured lookup definitions are the other lookup definitions that are created in Oracle Identity Manager when you deploy the connector. These lookup definitions are either prepopulated with values or values must be manually entered in them after the connector is deployed.
The other lookup definitions are as follows:
1.6.2.1 Lookup.FAIdentityService.Configuration
The Lookup.FAIdentityService.Configuration lookup definition holds connector configuration entries that are used during target resource reconciliation and provisioning operations.
Note:
The values for these lookup definitions are preconfigured and cannot be modified.Table 1-2 lists the default entries in this lookup definition.
Table 1-2 Entries in the Lookup.FAIdentityService.Configuration Lookup Definition
| Code | Decode | Description |
|---|---|---|
|
Any Incremental Recon Attribute Type |
true |
This entry holds the value which specified that the latest token can be of any type. |
|
Bundle Name |
org.identityconnectors.faidentityservice |
This entry holds the name of the connector bundle package. |
|
Bundle Version |
1.0.1115 |
This entry holds the version of the connector bundle class. |
|
Connector Name |
org.identityconnectors.faidentityservice.FAIdentityServiceConnector |
This entry holds the name of the connector class. |
|
defaultBatchSize |
500 |
This entry holds the number of records that must be included in each batch during batched reconciliation. This entry is used only when the Batch Size attribute of the user reconciliation scheduled jobs is either empty or set to 0. See Batched Reconciliation for Fusion Apps Connector for more information about the Batch Size attribute. |
|
User Configuration Lookup |
Lookup.FAIdentityService.UM.Configuration |
This entry holds the name of the lookup definition that contains user-specific configuration properties. |
1.6.2.2 Lookup.FAIdentityService.UM.Configuration
The Lookup.FAIdentityService.UM.Configuration lookup definition holds configuration entries that are specific to the user object type. This lookup definition is used during user management operations when your target system is configured as a target resource.
Table 1-3 lists the default entries in this lookup definition.
Table 1-3 Entries in the Lookup.FAIdentityService.UM.Configuration Lookup Definition
| Code | Decode | Description |
|---|---|---|
|
Provisioning Attribute Map |
Lookup.FAIdentityService.UM.ProvAttrMap |
This entry holds the name of the lookup definition that maps process form fields and target system attributes. See Lookup.FAIdentityService.UM.ReconAttrMap for more information about this lookup definition. |
|
Recon Attribute Map |
Lookup.FAIdentityService.UM.ReconAttrMap |
This entry holds the name of the lookup definition that maps resource object fields and target system attributes. See Lookup.FAIdentityService.UM.ReconAttrMap for more information about this lookup definition. |
1.6.2.3 Lookup.FAIdentityService.UM.ProvAttrMap
The Lookup.FAIdentityService.UM.ProvAttrMap lookup definition holds mappings between process form fields and target system attributes. This lookup definition is preconfigured and used during provisioning. Table 1-10 lists the default entries.
You can add entries in this lookup definition if you want to map new target system attributes for provisioning. See Adding New User Attributes for Provisioning.
1.6.2.4 Lookup.FAIdentityService.UM.ReconAttrMap
The Lookup.FAIdentityService.UM.ReconAttrMap lookup definition holds mappings between resource object fields and target system attributes. This lookup definition is preconfigured and used during reconciliation. Table 1-7 lists the default entries.
You can add entries in this lookup definition if you want to map new target system attributes for reconciliation. See Adding New User Attributes for Reconciliation.
1.6.2.5 Lookup.FAUserRequestService.Configuration.Trusted
The Lookup.FAUserRequestService.Configuration.Trusted lookup definition holds connector configuration entries that are used during trusted source reconciliation.
Note:
The values for these lookup definitions are preconfigured and cannot be modified.Table 1-4 lists the default entries in this lookup definition.
Table 1-4 Entries in the Lookup.FAUserRequestService.Configuration.Trusted Lookup Definition
| Code | Decode | Description |
|---|---|---|
|
Bundle Name |
org.identityconnectors.fauserrequestservice |
This entry holds the name of the connector bundle package. |
|
Bundle Version |
1.0.1115 |
This entry holds the version of the connector bundle class. |
|
Connector Name |
org.identityconnectors.fauserrequestservice.FAUserRequestServiceConnector |
This entry holds the name of the connector class. |
|
User Configuration Lookup |
Lookup.FAUserRequestService.UM.Configuration.Trusted |
This entry holds the name of the lookup definition that contains user-specific configuration properties. |
|
defaultBatchSize |
500 |
This entry holds the number of records that must be included in each batch during batched reconciliation. This entry is used only when the Batch Size attribute of the user reconciliation scheduled jobs is either empty or set to 0. See Batched Reconciliation for Fusion Apps Connector for more information about the Batch Size attribute. |
1.6.2.6 Lookup.FAUserRequestService.UM.Configuration.Trusted
The Lookup.FAUserRequestService.Configuration.Trusted lookup definition holds connector configuration entries that are used during trusted source reconciliation.
Table 1-5 lists the default entries in this lookup definition.
Table 1-5 Entries in the Lookup.FAUserRequestService.Configuration.Trusted Lookup Definition
| Code | Decode | Description |
|---|---|---|
|
Recon Attribute Defaults |
Lookup.FAUserRequestService.UM.ReconAttrMap.TrustedDefaults |
This entry holds the name of the lookup definition that holds default values of the resource object fields and target system attributes. See Lookup.FAUserRequestService.UM.ReconAttrMap.TrustedDefaults. |
|
Recon Attribute Map |
Lookup.FAUserRequestService.UM.ReconAttrMap.Trusted |
This entry holds the name of the lookup definition that maps resource object fields and target system attributes. See Lookup.FAUserRequestService.UM.ReconAttrMap.Trusted. |
1.6.2.7 Lookup.FAUserRequestService.UM.ReconAttrMap.Trusted
The Lookup.FAUserRequestService.UM.ReconAttrMap.Trusted lookup definition holds the name of the lookup definition that maps resource object fields and target system attributes. This lookup definition is preconfigured. Table 1-8 lists the default entries.
1.6.2.8 Lookup.FAUserRequestService.UM.ReconAttrMap.TrustedDefaults
The Lookup.FAUserRequestService.UM.ReconAttrMap.TrustedDefaults lookup definition holds default values of the resource object fields and target system attributes. This lookup definition is preconfigured.
Table 1-6 lists the default entries in this lookup definition.
Table 1-6 Entries in the Lookup.FAUserRequestService.UM.ReconAttrMap.TrustedDefaults Lookup Definition
| Code | Decode |
|---|---|
|
Employee Type |
Full-Time |
|
Organization |
Xellerate Users |
|
User Type |
Xellerate Users |
1.7 Connector Objects Used During Target Resource Reconciliation
Target resource reconciliation involves fetching data about newly created or modified accounts on the target system and using this data to add or modify resources assigned to OIM Users.
The Lookup.FAIdentityService.UM.ReconAttrMap lookup definition maps user resource object fields and target system attributes. This lookup definition is used for performing target resource user reconciliation runs.
In this lookup definition, entries are in the following format:
-
Code Key: Reconciliation field of the resource object
-
Decode: Name of the target system attribute
Table 1-7 lists the entries in this lookup definition.
Table 1-7 Entries in the Lookup.FAIdentityService.UM.ReconAttrMap lookup definition
| Resource Object Field | Target System Field |
|---|---|
|
Display Name |
|
|
|
|
|
External ID |
externalId |
|
Family Name |
name.familyName |
|
Given Name |
name.givenName |
|
Id |
_UID_ |
|
Preferred Language |
preferredLanguage |
|
Roles~Role Name[LOOKUP] |
roles.id |
|
Status |
_ENABLE_ |
|
User Name |
_NAME_ |
1.8 Connector Objects Used During Trusted Source Reconciliation
Trusted source reconciliation involves fetching data about newly created or modified accounts on the target system and using that data to create or update OIM Users.
The Lookup.FAUserRequestService.UM.ReconAttrMap.Trusted lookup definition maps user fields of the OIM User form with corresponding field names in the target system. This lookup definition is used for performing trusted source reconciliation runs.
In this lookup definition, entries are in the following format:
-
Code Key: OIM User Form Field
-
Decode: Target System Field
Table 1-8 lists the user identity fields whose values are fetched from the target system during a trusted source reconciliation run.
Table 1-8 Entries in the Lookup.FAUserRequestService.UM.ReconAttrMap.Trusted lookup definition
| OIM User Form Field | Target System Field |
|---|---|
|
Country Name |
addresses.country |
|
Display Name |
user.displayName |
|
|
user.emails.value |
|
Employee Number |
employeeNumber |
|
Employee Type |
userType |
|
FA Account Id |
_UID_ |
|
FA Account Status[TRUSTED] |
_ENABLE_ |
|
Generation Qualifier |
user.name.honorificSuffix |
|
Given Name |
user.name.givenName |
|
Initials |
user.name.initials |
|
Locality Name |
addresses.locality |
|
Manager |
manager.displayName |
|
Middle Name |
user.name.middleName |
|
Postal Address |
addresses.formatted |
|
Postal Code |
addresses.postalCode |
|
Preferred Language |
user.preferredLanguage |
|
State |
addresses.region |
|
Street |
addresses.streetAddress |
|
Surname |
user.name.familyName |
|
Telephone Number |
phoneNumbers.value |
|
User Login |
_NAME_ |
1.9 Connector Objects Used During Provisioning
Provisioning involves creating or modifying user data on the target system through Oracle Identity Manager.
This section contains the following topics:
1.9.1 Provisioning Functions
These are the supported provisioning functions and the adapters that perform these functions for the connector.
The Adapter column in Table 1-9 gives the name of the adapter that is used when the function is performed.
Table 1-9 Provisioning Functions
| Function | Adapter |
|---|---|
|
Add a role |
adpFAIDENTITYSERVICEADDROLE |
|
Create a user |
adpFAIDENTITYSERVICECREATEUSER |
|
Delete a user |
adpFAIDENTITYSERVICEDELETEUSER |
|
Disable a user |
adpFAIDENTITYSERVICEDISABLEUSER |
|
Enable a user |
adpFAIDENTITYSERVICEENABLEUSER |
|
External Id for a source |
adpFAIDENTITYSERVICEEXTERNALIDFORFASOURCE |
|
Multi update |
adpFAIDENTITYSERVICEMULTIUPDATE |
|
Prepopulate an adapter |
adpFAIDENTITYSERVICEPREPOPULATEADAPTER |
|
Prepopulate external Id for an adapter |
adpFAIDENTITYSERVICEPREPOPULATEEXTERNALIDADAPTER |
|
Remove a role |
adpFAIDENTITYSERVICEREMOVEROLE |
|
Update a role |
adpFAIDENTITYSERVICEUPDATEROLE |
|
Update a user |
adpFAIDENTITYSERVICEUPDATEUSER |
|
Complete a task |
adpFATCCOMPLETETASK |
|
Trigger, create, or link an account |
adpTRIGGERCREATEORLINKFAACCOUNT |
1.9.2 User Fields for Provisioning
The Lookup.FAIdentityService.UM.ProvAttrMap lookup definition maps process form fields with target system attributes. This lookup definition is used for performing user provisioning operations.
Table 1-10 lists the user identity fields of the target system for which you can specify or modify values during provisioning operations.
Table 1-10 Entries in the Lookup.FAIdentityService.UM.ProvAttrMap lookup definition
| Code | Decode |
|---|---|
|
Display Name |
displayName |
|
|
emails.value |
|
External Id |
externalId |
|
Family Name |
name.familyName |
|
Given Name |
name.givenName |
|
Id |
_UID_ |
|
Preferred Language |
preferredLanguage |
|
User Name |
_NAME_ |
1.10 Roadmap for Deploying and Using the Connector
The following is the organization of information in the rest of this guide:
-
Deploying the Fusion Apps Connector describes procedures that you must perform on Oracle Identity Manager and the target system during each stage of connector deployment.
-
Using the Fusion Apps Connector describes guidelines on using the connector and the procedure to configure reconciliation runs and perform provisioning operations.
-
Extending the Functionality of the Fusion Apps Connector describes procedures that you can perform if you want to extend the functionality of the connector.
-
Files and Directories on the Fusion Apps Connector Installation Media lists the files and directories that comprise the connector installation media.