1 About the ServiceNow Connector
The ServiceNow connector integrates Oracle Identity Manager (OIM) with the ServiceNow.
The following topics provide a high-level overview of the ServiceNow connector:
1.1 Introduction to ServiceNow Connector
ServiceNow connector is used to integrate OIM with a ServiceNow instance. ServiceNow connector ensures that all ServiceNow accounts are created, updated, and deactivated on an integrated cycle with the rest of the identity-aware applications in your enterprise. ServiceNow Connector standardizes service processes and implements automation to replace manual tasks.
Note:
At some places in this guide, ServiceNow has been referred to as the target system.
In the account management (target resource) mode of the connector, information about users created or modified directly on the target system can be reconciled into Oracle Identity Manager. This data is used to add or modify resources (that is, accounts) allocated to OIM Users. In addition, you can use Oracle Identity Manager to provision or update ServiceNow resources (accounts) assigned to OIM Users. These provisioning operations performed on Oracle Identity Manager translate into the creation or updates to target system accounts.
1.2 Certified Components for ServiceNow Connector
These are the software components and their versions required for installing and using ServiceNow connector.
Table 1-1 Certified Components
| Item | Requirement |
|---|---|
|
Oracle Identity Governance or Oracle Identity Manager |
You can use one of the following releases of Oracle Identity Governance of Oracle Identity Manager:
|
|
Target System |
ServiceNow release Eureka or later |
|
Connector Server |
11.1.2.1.0 |
|
Connector Server JDK |
JDK 1.6 or later |
1.3 Certified Languages for the ServiceNow Connector
These are the languages that the connector supports.
-
Arabic
-
Chinese (Simplified)
-
Chinese (Traditional)
-
Czech
-
Danish
-
Dutch
-
English (US)
-
Finnish
-
French
-
French (Canadian)
-
German
-
Greek
-
Hebrew
-
Hungarian
-
Italian
-
Japanese
-
Korean
-
Norwegian
-
Polish
-
Portuguese
-
Portuguese (Brazilian)
-
Romanian
-
Russian
-
Slovak
-
Spanish
-
Swedish
-
Thai
-
Turkish
1.4 Architecture of the ServiceNow Connector
The ServiceNow connector is implemented by using the Identity Connector Framework (ICF).
The ICF is a component that is required in order to use Identity Connector. ICF provides basic reconciliation and provisioning operations that are common to all Oracle Identity Manager connectors. In addition, ICF provides common features that developers would otherwise need to implement on their own, such as, buffering, time outs, and filtering. ICF is distributed together with Oracle Identity Manager. Therefore, you do not need to configure or modify ICF.
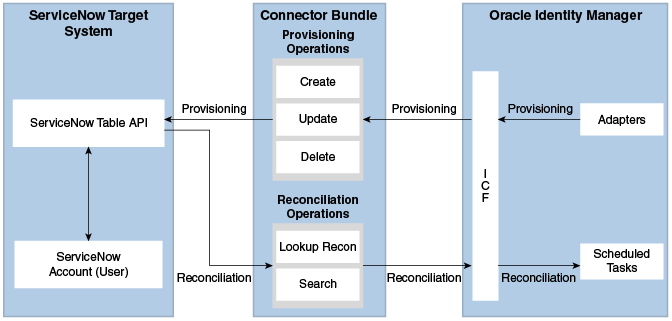
Figure 1-1 shows the architecture of the ServiceNow connector.
- Provisioning
Provisioning involves creating, updating, or deleting users on the target system through Oracle Identity Manager. During provisioning, the Adapters invoke ICF operation, ICF inturn invokes create operation on the ServiceNow Identity Connector Bundle and then the bundle calls the target system API for provisioning operations. The ServiceNow Table API on the target system accepts provisioning data from the bundle, carries out the required operation on the target system, and returns the response from the target system back to the bundle, which passes it to the adapters.
- Target resource reconciliation
During reconciliation, a scheduled task invokes an ICF operation. ICF inturn invokes a search operation on the ServiceNow Identity Connector Bundle and then the bundle calls ServiceNow API for reconciliation operation. The API extracts user records that match the reconciliation criteria and hands them over through the bundle and ICF back to the scheduled task, which brings the records to Oracle Identity Manager.
Each record fetched from the target system is compared with ServiceNow resources that are already provisioned to OIM Users. If a match is found, then the update made to the ServiceNow record from the target system is copied to the ServiceNow resource in Oracle Identity Manager. If no match is found, then the user ID of the record is compared with the user ID of each OIM User. If a match is found, then data in the target system record is used to provision an ServiceNow resource to the OIM User.
The ServiceNow Identity Connector Bundle communicates with the ServiceNow Table API using the HTTPS protocol. The ServiceNow Table API provides programmatic access through REST API endpoints. Apps can use the ServiceNow API to perform create, read, update, and delete (CRUD) operations on directory data and directory objects, such as users.
See Also:
Understanding the Identity Connector Framework in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager for more information about ICF
1.5 Use Cases Supported by the ServiceNow Connector
ServiceNow connector is used to integrate OIM with a ServiceNow instance. ServiceNow connector ensures that all ServiceNow accounts are created, updated, deleted, and deactivated on an integrated cycle with the rest of the identity-aware applications in your enterprise. ServiceNow connector standardizes service processes and implements automation to replace manual tasks. In a typical IT scenario, an organization using OIM wants to manage accounts, user association with a role or with a department across a ServiceNow Cloud instance.
As a business use case, consider a leading logistics company in Australia which was using ServiceNow for the ticketing system solution and OIM for identity management. Before using ServiceNow connector, operations such as create, edit, and delete were performed manually and lacked a centralized streamlining operation. These operations can be easily automated using the ServiceNow REST APIs. By integrating ServiceNow connector with Oracle Identity Manager, the logistics company was able to achieve complete automation.
-
ServiceNow User Management
An organization using ServiceNow wants to integrate with OIM to manage identities. The organization wants to manage its user identities by creating them in the target system using OIM. The organization also wants to synchronize user identity changes performed directly in the target system with OIM. In such a scenario, a quick and an easy way is to install the ServiceNow connector and configure it with your target system by providing connection information in the IT resource.
ServiceNow connector allows new users to self-provision on a ServiceNow Cloud instance. New users can request and provision from a catalog of cloud-based resources.
To create a new user in the target system, fill in and submit the OIM process form to trigger the provisioning operation. The connector executes the create operation against your target system and the user is created on successful execution of the operation. Similarly, operations such as delete and update can be performed.
To search or retrieve the user identities, you must run a scheduled task from OIM. The connector will run the corresponding search operation against the user identities in the target system and fetch all the changes to OIM.
- Entitlement Grant Management
- ServiceNow Groups
In ServiceNow context, a group is a collection of users who share a common purpose. Generally, a group will perform tasks such as approving change requests and resolving incidents.
For example, consider a network outage scenario. A Network group with several team members will receive a group notification about the incident. The outage incident task can be assigned to any Network group member for a resolution. The ServiceNow connector integration with OIM provides a request-based policy option. Before using ServiceNow connector, the approver must be an user from the Network group. With ServiceNow integration, the said outage resolution can be automatically assigned to users or groups based on predefined polices. For administrators and users, the ServiceNow connector provides an option to facilitate a request-based group membership assignment or group membership revocation options.
-
ServiceNow Roles
In ServiceNow context, a role is an administrator who can create groups and provide access-based permissions to various groups.
ServiceNow connector manages role memberships. Role memberships provide selective access to ServiceNow functionalities. A user can be a member of one or more roles. Generally, new users are added to a specific role. Each role determines various tasks such as view, update, and delete operations that a ServiceNow user can perform.
As an example, a user with specific role has the rights to view a change request, however does not have access privileges to approve or reject a change request. A ServiceNow user without a role assignment can perform minimal read and write operations. A ServiceNow user needs to have role access privilege in order to create a group. In large organizations, it may be necessary for an administrator to designate other employees to act as administrators to serve different functions. For example, you can set admin roles for your IT staff that can act as support agents to other employees, partners, customers and vendors. With the ServiceNow connector, you can assign or revoke a ServiceNow admin role to users as an entitlement, thus facilitating you to leverage the delegated administration capability of ServiceNow.
- ServiceNow Groups
1.6 Features of the ServiceNow Connector
The features of the connector include support for connector server, full reconciliation, limited reconciliation, and reconciliation of deleted account data.
1.6.1 Full Reconciliation
In full reconciliation, all records are fetched from the target system to Oracle Identity Manager.
After the first full reconciliation run, you can configure your connector for incremental reconciliation.
The connector is capable of performing incremental reconciliation provided the target system supports it. That is, incremental reconciliation is supported if there is a field in the target system that can hold timestamp values.
You can perform a full reconciliation any time.
See Full Reconciliation for more information about performing full reconciliation.
1.6.2 Support for the Connector Server
Connector Server is one of the features provided by ICF. By using one or more connector servers, the connector architecture permits your application to communicate with externally deployed bundles.
A Java connector server is useful when you do not want to execute a Java connector bundle in the same VM as your application. It can be beneficial to run a Java connector on a different host for performance improvements if the bundle works faster when deployed on the same host as the native managed resource.
See Installation for more information about the installation options for this connector.
See Also:
Using an Identity Connector Server in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager for more information about installing and configuring connector server and running the connector server
1.6.3 Limited (Filtered) Reconciliation
You can reconcile records from the target system based on a specified filter criterion.
You can set a reconciliation filter as the value of the Filter Suffix attribute of the user reconciliation scheduled job. This filter specifies the subset of newly added and modified target system records that must be reconciled. The Filter Suffix attribute helps you to assign filters to the API based on which you will get a filtered response from target.
See Limited (Filtered) Reconciliation for more information about limited reconciliation.
1.6.4 Transformation and Validation of Account Data
You can configure validation of account data that is brought into or sent from Oracle Identity Manager during reconciliation and provisioning.
1.7 Lookup Definitions Used During Connector Operations
Lookup definitions used during reconciliation and provisioning are either preconfigured or can be synchronized with the target system.
Lookup definitions used during connector operations can be categorized as follows:
1.7.1 Lookup Definitions Synchronized with the Target System
During a provisioning operation, you use a lookup field on the process form to select a single value from a set of values. For example, you may want to select a role from the Role Name lookup field to specify the role being assigned to the user. When you deploy the connector, lookup definitions corresponding to the lookup fields on the target system are created in Oracle Identity Manager. Lookup field synchronization involves copying additions or changes made to specific fields in the target system to lookup definitions in Oracle Identity Manager.
After you deploy the connector, the following lookup definitions, which are used as an input source for lookup fields, are automatically created in Oracle Identity Manager:
-
Lookup.ServiceNow.Groups
-
Lookup.ServiceNow.Roles
-
Lookup.ServiceNow.Departments
These lookup definitions are empty by default. They are populated with values fetched from the target system when you run the scheduled jobs for lookup field synchronization. For example, when you run the scheduled job for role lookup field synchronization, all Roles on the target system are fetched to Oracle Identity Manager and populated in the Lookup.ServiceNow.Roles lookup definition.
After lookup field synchronization, data in each of the lookup definitions for lookup field synchronization is stored in the following format:
-
Code Key: <IT_RESOURCE_KEY>~<FIELD_VALUE_ID>
In this format:-
IT_RESOURCE_KEY is the numeric code assigned to an IT resource in Oracle Identity Manager.
-
FIELD_VALUE_ID is the ID of the target system field value.
89~1b5d6697-f4a6-4f03-8df7-4fae1512fd16.In this example,89is the numeric code assigned to the IT resource associated with the target system and1b5d6697-f4a6-4f03-8df7-4fae1512fd16is the ID of the Role in the target system. -
-
Decode: <IT_RESOURCE_NAME>~<LOOKUP_FIELD_NAME>
In this format:-
IT_RESOURCE_NAME is the name assigned to an IT resource in Oracle Identity Manager.
-
FIELD_VALUE is the value of the field in the target system.
ServiceNow~admin.In this example,ServiceNowis the name assigned to the IT resource associated with the target system andadminis the name of the Role in the target system. -
Table 1-2 shows sample entries in the Lookup.ServiceNow.Groups lookup definition.
Table 1-2 Sample Entries in the Lookup.ServiceNow.Groups Lookup Definition
| Code Key | Decode |
|---|---|
|
87~287ebd7da9fe198100f92cc8d1d2154e |
ServiceNow~Network |
|
87~287ee6fea9fe198100ada7950d0b1b73 |
ServiceNow~Database |
|
87~7a0d3844db125200b88df7a0cf96198a |
ServiceNow~OIM |
|
87~97f274a1db129200b88df7a0cf9619e2 |
ServiceNow~OIM Connector |
1.7.2 Predefined Lookup Definitions
Preconfigured lookup definitions are the other lookup definitions that are created in Oracle Identity Manager when you deploy the connector. These lookup definitions are either prepopulated with values or values must be manually entered in them after the connector is deployed.
The Preconfigured lookup definitions are as follows:
1.7.2.1 Lookup.ServiceNow.Configuration
The Lookup.ServiceNow.Configuration lookup definition holds connector configuration entries that are used during target resource reconciliation and provisioning operations.
Table 1-3 lists the default entries in the Lookup.ServiceNow.Configuration values lookup definition.
Note:
Do not modify the entries in this lookup definitionTable 1-3 Entries in the Lookup.ServiceNow.Configuration Definition
| Code Key | Decode | Description |
|---|---|---|
|
Any Incremental Recon Attribute Type |
true |
By default, OIM accepts timestamp information sent from the target system only in Long datatype format. A decode value of True for the Incremental Recon Attribute Type entry indicates that OIM will accept timestamp information in any datatype format. |
|
Bundle Name |
org.identityconnectors.servicenow |
This entry holds the name of the connector bundle. |
|
Bundle Version |
1.0.1115 |
This entry holds the version of the connector bundle. |
|
Connector Name |
org.identityconnectors.genericrest.GenericRESTConnector |
This entry holds the name of the connector class. |
|
customPayload |
"__ACCOUNT__.__GROUP__.UPDATEOP={\"user\": \"$(__UID__)$\",\"group\": \"$(sys_id)$\"}"," __ACCOUNT__.__ROLE__.UPDATEOP={\"user\": \"$(__UID__)$\",\"role\": \"$(sys_id)$\"}"," __ACCOUNT__.__ENABLE__.UPDATEOP={\"active\":\"$(__ENABLE__)$\",\"locked_out\":\"false\"}" |
This entry lists the payloads for all operations that are not in the standard format. |
|
enableEmptyString |
true |
This entry holds the boolean value and indicates that an empty string needs to be sent to the target system. When the ServiceNow Table API receives a null value for any parameter, and if the |
|
httpHeaderAccept |
application/json |
This entry holds the accept type expected from the target system in the header. |
|
httpHeaderContentType |
application/json |
This entry holds the content type expected by the target system in the header. |
|
jsonResourcesTag |
"__ACCOUNT__=result","__GROUP__=result", "__ACCOUNT__.__GROUP__=result", "__ACCOUNT__.__ROLE__=result","__ROLE__=result","Department=result", "__ACCOUNT__.__MEMBERSHIP__.__GROUP__=result", "__ACCOUNT__.__MEMBERSHIP__.__ROLE__=result" |
This entry holds the json tag value that is used during reconciliation for parsing multiple entries in a single payload. |
|
nameAttributes |
"__ACCOUNT__.user_name", "__GROUP__.name", "__ROLE__.name","Department.name" |
This entry holds the name attribute for all the objects that are handled by this connector. For example, for the __ACCOUNT__ object class that it used for User accounts, the name attribute is user_name. |
|
opTypes |
"__ACCOUNT__.__GROUP__.UPDATEOP=POST", "__ACCOUNT__.__ROLE__.UPDATEOP=POST" |
This entry specifies the HTTP operation type for each object class supported by the connector. Values are comma separated and are in the following format: OBJ_CLASS.OP=HTTP_OP In this format, OBJ_CLASS is the connector object class, OP is the connector operation (for example, CreateOp, UpdateOp, SearchOp), and HTTP_OP is the HTTP operation (GET, PUT, or POST). |
|
passwordAttribute |
user_password |
This entry holds the name of the target system attribute that is mapped to the __PASSWORD__ attribute of the connector in OIM. |
|
relURI’s |
"__ACCOUNT__.CREATEOP=/api/now/v1/table/sys_user?sysparm_input_display_value=true", "__ACCOUNT__.SEARCHOP=/api/now/v1/table/sys_user/$(FilterSuffix)$", "__ACCOUNT__=/api/now/v1/table/sys_user/$(__UID__)$?sysparm_input_display_value=true", "__GROUP__.CREATEOP=/api/now/v1/table/sys_user_group", "__GROUP__.SEARCHOP=/api/now/v1/table/sys_user_group/$(FilterSuffix)$", "__GROUP__=/api/now/v1/table/sys_user_group/$(__UID__)$", "__ROLE__.SEARCHOP=/api/now/v1/table/sys_user_role/$(FilterSuffix)$", "__ACCOUNT__.__GROUP__.UPDATEOP=/api/now/table/sys_user_grmember", "__ACCOUNT__.__ROLE__.UPDATEOP=/api/now/table/sys_user_has_role", "__ACCOUNT__.__GROUP__.SEARCHOP=/api/now/v1/table/sys_user_grmember?sysparm_query=user.sys_id=$(__UID__)$", "__ACCOUNT__.__ROLE__.SEARCHOP=/api/now/table/sys_user_has_role?sysparm_query=user.sys_id=$(__UID__)$", "__ACCOUNT__.__GROUP__.DELETEOP=/api/now/table/sys_user_grmember/$(__MEMBERSHIP__.sys_id)$", "__ACCOUNT__.__MEMBERSHIP__.__GROUP__.SEARCHOP =/api/now/v1/table/sys_user_grmember?sysparm_query=user.sys_id=$ (__UID__)$%5E (__UID__)$%5Egroup.sys_id=$(__GROUP__.sys_id) $&sysparm__fields=sys_id", "__ACCOUNT__.__ROLE__.DELETEOP=/api/now/table/sys_user_has_role$(__MEMBERSHIP__.sys_id)$", "__ACCOUNT__.__MEMBERSHIP__.__ROLE__.SEARCHOP=/api/now/v1/table/sys_user_has_role?sysparm_query= user.sys_id=$(__UID__)$%5Erole.sys_id=$(__ROLE__.sys_id) $&sysparm _fields=sys_id", "Department.SEARCHOP =/api/now/v1/table/cmn_department", "__ACCOUNT__.__ENABLE__.UPDATEOP=/api/now/v1/table/sys_user/$(__UID__)$?sysparm__input_display_value=true", "__ACCOUNT__.__ENABLE__.UPDATEOP=/api/now/v1/table/sys_user/$(__UID__)$?sysparm__input_display_value=true" |
This entry holds the relative URL of every object class supported by this connector and the connector operations that can be performed on these object classes. For example, the |
|
specialAttributeHandling |
"__ACCOUNT__.__GROUP__.UPDATEOP=SINGLE", "__ACCOUNT__.__ROLE__.UPDATEOP=SINGLE", "__ACCOUNT__.__ENABLE__.CREATEOP=SINGLE", "__ACCOUNT__.__ENABLE__.UPDATEOP=SINGLE" |
This entry lists the special attributes whose values should be sent to target one by one ("SINGLE"). Values are comma separated and are in the following format: OBJ_CLASS.ATTR_NAME.PROV_OP=SINGLE For example, the |
|
specialAttributeTargetFormat |
"__ACCOUNT__.__GROUP__=group", "__ACCOUNT__.__ROLE__=role" |
This entry lists the format in which an attribute is present in the target system endpoint. Values are comma separated and are presented in the following format: OBJ_CLASS.ATTR_NAME= TARGET_FORMAT |
|
statusAttribute |
"__ACCOUNT__.active" |
This entry lists the name of the target system attribute that holds the status of an account. For example, for the __ACCOUNT__ object class that it used for User accounts, the status attribute is |
|
uidAttributes |
"__ACCOUNT__.sys_id", "__GROUP__.sys_id", "__ROLE__.sys_id", "Department.sys_id" |
This entry holds the uid attribute for all the objects that are handled by this connector. For example, for User accounts, the uid attribute is sys_Id. In other words, the value__ACCOUNT__.sys_id in decode implies that the sys_id attribute (that is, GUID) of the connector for __ACCOUNT__ object class is mapped to sys_id which is the corresponding uid attribute for user accounts in the target system. |
|
User Configuration Lookup |
Lookup.ServiceNow.UM.Configuration |
This entry holds the name of the lookup definition that contains user-specific configuration properties. |
1.7.2.2 Lookup.ServiceNow.UM.Configuration
The Lookup.ServiceNow.UM.Configuration lookup definition contains entries specific to the user object type. This lookup definition is preconfigured and is used during user management operations.
Table 1-4 Entries in the Lookup.ServiceNow.UM.Configuration Lookup Definition
| Code Key | Decode |
|---|---|
|
Provisioning Attribute Map |
Lookup.ServiceNow.UM.ProvAttrMap |
|
Recon Attribute Map |
Lookup.ServiceNow.UM.ReconAttrMap |
1.7.2.3 Lookup.ServiceNow.UM.ProvAttrMap
The Lookup.ServiceNow.UM.ProvAttrMap lookup definition holds mappings between process form fields and target system attribute names.
This lookup definition is preconfigured and used during target resource provisioning. Table 1-12 lists the default entries.
You can add entries in this lookup definitions if you want to map new target system attributes for target resource provisioning. See Adding New User Attributes for Provisioning.
1.7.2.4 Lookup.ServiceNow.UM.ReconAttrMap
This lookup definition is preconfigured and used during target resource reconciliation.
The Lookup.ServiceNow.UM.ReconAttrMap lookup definition holds mappings between resource object fields and target system attributes. Table 1-9 lists the default entries.
You can add entries in this lookup definitions if you want to map new target system attributes for target resource reconciliation. See Adding New User Attributes for Reconciliation.
1.7.2.5 Lookup.ServiceNow.DateFormat
The Lookup.ServiceNow.DateFormat lookup definition maps date format values that are used for some of the fields in the target system with the corresponding date format to be displayed in the fields of the OIM User form.
Table 1-5 Entries in the Lookup.ServiceNow.DateFormat Lookup Definition
| Code Key (Resource Object Field) | Decode (ServiceNow Field) |
|---|---|
|
dd/MM/yyyy |
dd/MM/yyyy |
|
dd.MM.yyyy |
dd.MM.yyyy |
|
dd-MM-yyyy |
dd-MM-yyyy |
|
MM-dd-yyyy |
MM-dd-yyyy |
|
yyyy-MM-dd |
yyyy-MM-dd |
1.7.2.6 Lookup.ServiceNow.Timezone
The Lookup.ServiceNow.Timezone lookup definition maps timezone values that are used for some of the fields in the target system with the corresponding timezone values to be displayed in the fields of the OIM User form.
Table 1-6 Entries in the Lookup.ServiceNow.Timezone Lookup Definition
| Code Key | Decode |
|---|---|
|
GMT |
GMT |
|
US/Arizona |
US/Arizona |
|
US/Central |
US/Central |
|
US/Eastern |
US/Eastern |
If you want to customize the lookup to add other attributes, you can do so by adding them manually.
1.7.2.7 Lookup.ServiceNow.CalendarIntegration
The Lookup.ServiceNow.CalendarIntegration lookup definition holds information about calender integration that you can select for a target system account that you create through Oracle Identity Manager. This is a static lookup definition.
-
Code Key: Serial number for calendar integration
-
Decode Key: Calendar name for integration
Table 1-7 Entries in the Lookup.ServiceNow.CalendarIntegration Lookup Definition
| Code Key (Resource Object Field) | Decode (ServiceNow Field) |
|---|---|
|
1 |
Outlook |
1.7.2.8 Lookup.ServiceNow.BooleanValues
The Lookup.ServiceNow.BooleanValues lookup definition maps boolean values that are used for some of the fields in the target system with the corresponding boolean values to be displayed in the fields of the OIM User form.
Table 1-8 lists the default entries in the Lookup.ServiceNow.BooleanValues lookup definition.
Table 1-8 Entries in the Lookup.ServiceNow.BooleanValues Lookup Definition
| Code Key (Resource Object Field) | Decode (ServiceNow Field) |
|---|---|
|
true |
True |
|
false |
False |
1.8 Connector Objects Used During Target Resource Reconciliation
Connector objects such as reconciliation rules, reconciliation action rules, and scheduled jobs are used for reconciling user records from the target system into Oracle Identity Manager.
See Also:
Managing Reconciliation in Oracle Fusion Middleware Administering Oracle Identity Manager for conceptual information about reconciliationThis section contains the following topics related to connector objects:
1.8.1 User Fields for Target Resource Reconciliation
The Lookup.ServiceNow.UM.ReconAttrMap lookup definition maps resource object fields with target system attributes. This lookup definition is used for performing target resource user reconciliation runs.
In this lookup definition, entries are in the following format:
-
Code Key: Reconciliation field of the resource object
-
Decode: Name of the target system attribute
Table 1-9 lists the entries in this lookup definition.
Table 1-9 Entries in the Lookup.ServiceNow.UM.ReconAttrMap Lookup Definition
| Code Key (Resource Object Field) | Decode (ServiceNow Field) |
|---|---|
|
Calendar Integration |
calendar_integration |
|
Date Format |
date_format |
|
Department[LOOKUP] |
department.value |
|
|
|
|
First Name |
first_name |
|
Groups~Group Name[LOOKUP] |
__GROUP__~__GROUP__~value |
|
Internal Integration User |
internal_integration_user |
|
Last Name |
last_name |
|
Locked |
locked_out |
|
Mobile Phone |
mobile_phone |
|
Password Needs Reset |
password_needs_reset |
|
Phone |
phone |
|
Roles~Role Name[LOOKUP] |
__ROLE__~__ROLE__~value |
|
status |
Status __ENABLE__ |
|
System Id |
__UID__ |
|
Time Zone |
time_zone |
|
Title |
title |
|
User Name |
__NAME__ |
|
Web Service Access Only |
web_service_access_only |
1.8.2 Reconciliation Rule for User Target Resource Reconciliation
Reconciliation rules for user target resource reconciliation are used by the reconciliation engine to determine the identity to which Oracle Identity Manager must assign a newly discovered account on the target system.
1.8.2.1 Target Resource Reconciliation Rule for Users
Reconciliation rules for target resource reconciliation are used by the reconciliation engine to determine the identity to which Oracle Identity Manager must assign a newly discovered account on the target system.
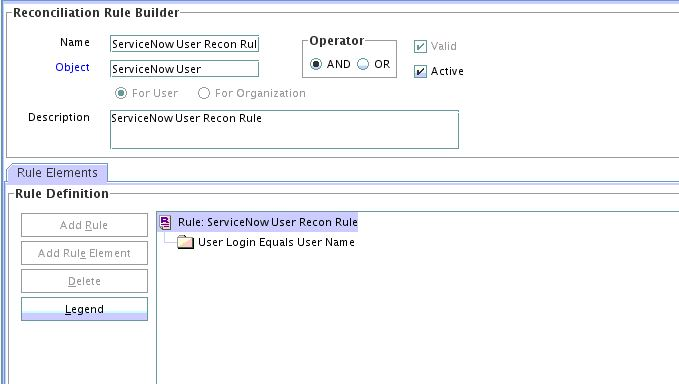
The following is the process-matching rule for users:
Rule name: ServiceNow User Recon Rule
Rule element: User Login Equals User Name
-
User Loginis the User ID field of the OIM User form. -
User Nameis the unique login name for user in target system.
1.8.3 Reconciliation Action Rules for Target Resource Reconciliation
Reconciliation action rules specify actions that must be taken depending on whether or not matching ServiceNow resources or OIM Users are found when the reconciliation rule is applied.
The following sections provide information about the action rules for this connector:
1.8.3.1 Target Resource Reconciliation Action Rules for Users
Reconciliation action rules specify the actions the connector must perform based on the result of the processing of a reconciliation event. The reconciliation action rules for both users and groups are the same.
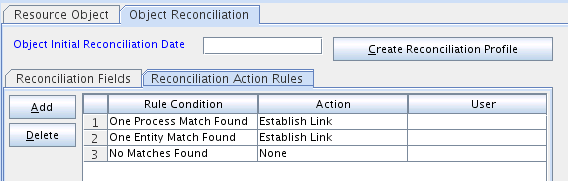
Table 1-10 Action Rules for Target Resource Reconciliation of Users
| Rule Condition | Action |
|---|---|
|
No Matches Found |
None |
|
One Entity Match Found |
Establish Link |
|
One Process Match Found |
Establish Link |
1.9 Connector Objects Used During Provisioning
Connector objects such as adapters are used for performing provisioning operations on the target system. These adapters perform provisioning functions on the fields defined in the lookup definition for provisioning.
See Also:
Managing Provisioning Tasks in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Manager for conceptual information about provisioningThis section contains the following topics:
1.9.1 Provisioning Functions
These are the supported provisioning functions and the adapters that perform these functions for the ServiceNow connector.
The Adapter column in Table 1-11 provides the name of the adapter that is used when the function is performed.
See Also:
Types of Adapters in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager for generic information about process tasks and adaptersTable 1-11 User Provisioning Functions
| Function | Adapter |
|---|---|
|
ServiceNow Add Child Object |
adpSERVICENOWADDCHILDOBJECT |
|
ServiceNow Bulk Adapter |
adpSERVICENOWBULKADAPTER |
|
ServiceNow Create Object |
adpSERVICENOWCREATEOBJECT |
|
ServiceNow Delete Object |
adpSERVICENOWDELETEOBJECT |
|
ServiceNow Disable Object |
adpSERVICENOWDISABLEOBJECT |
|
ServiceNow Enable Object |
adpSERVICENOWENABLEOBJECT |
|
ServiceNow Remove Child Object |
adpSERVICENOWREMOVECHILDOBJECT |
|
ServiceNow Update Child Data |
adpSERVICENOWUPDATECHILDDATA |
|
ServiceNow Update Object |
adpSERVICENOWUPDATEOBJECT |
1.9.2 User Fields for Provisioning
The Lookup.ServiceNow.UM.ProvAttrMap lookup definition maps process form fields with ServiceNow fields. This lookup definition is used for performing user provisioning operations.
In this lookup definition, entries are in the following format:
Code Key: Name of the process form field
Decode: Name of the target system attribute.
Table 1-12 Entries in the Lookup.ServiceNow.UM.ProvAttrMap Lookup Definition
| Code Key | Decode |
|---|---|
|
Calendar Integration |
calendar_integration |
|
Date Format |
date_format |
|
Department[LOOKUP] |
department |
|
|
|
|
First Name |
first_name |
|
Internal Integration User |
internal_integration_user |
|
Last Name |
last_name |
|
Locked |
locked_out |
|
Mobile Phone |
mobile_phone |
|
Password |
__PASSWORD__ |
|
Password Needs Reset |
password_needs_reset |
|
Phone |
phone |
|
System Id |
__UID__ |
|
Time Zone |
time_zone |
|
Title |
title |
|
UD_SN_UGP~Group Name[LOOKUP] |
__GROUP__~__GROUP__~sys_id |
|
UD_SN_URO~Role Name[LOOKUP] |
__ROLE__~__ROLE__~sys_id |
|
User Name |
__NAME__ |
|
Web Service Access Only |
web_service_access_only |
1.10 Roadmap for Deploying and Using the Connector
This is the organization of information available in this guide for deploying and using the connector.
The rest of this guide is divided into the following chapters:
-
Deploying the ServiceNow Connector describes procedures that you must perform on Oracle Identity Manager and the target system during each stage of connector deployment.
-
Using the ServiceNow Connector describes guidelines on using the connector and the procedure to configure reconciliation runs and perform provisioning operations.
-
Extending the Functionality of the ServiceNow Connector describes the procedures to perform if you want to extend the functionality of the connector.
-
Files and Directories of the ServiceNow Connector lists the files and directories that comprise the connector installation media.