6 Security
This chapter contains the following topics:
6.1 Security Server
This section discusses these topics:
-
Overview of Security Server
-
Security Server Architecture
-
Security Server Certified Platforms
-
Additional References
6.1.1 Overview of Security Server
JD Edwards EnterpriseOne security runs on an enterprise server in a dedicated internal process. You create a security table on the database server that stores information, such as:
| Value | Description |
|---|---|
| EnterpriseOne User | The user ID used to sign in to JD Edwards EnterpriseOne. |
| EnterpriseOne Password | The user's password, which the software validates when the user signs in to JD Edwards EnterpriseOne. |
| System User and System Password | The actual user and password used to connect to all database management systems (DBMS). If the JD Edwards EnterpriseOne environment includes more than one DBMS, you can create different system users and passwords for each data source. |
| Change Frequency | The frequency of password changes required by the software. |
| Last Change | The date that the password was last changed. |
You must define a security record for each user either by group or by individual. It is recommended that you map multiple users to the same system user. For example, each user can use the same system user that the software uses to connect the database management systems. By setting up the security in this manner, you can simplify database administration of users and passwords.
You can also set up unified logon with JD Edwards EnterpriseOne to simplify sign-in security. When you set up unified logon, JD Edwards EnterpriseOne uses Windows Authentication to verify security. This verification enables sign-in security to use the network logon information that a user supplies when logging on to Windows; JD Edwards EnterpriseOne does not require the user to enter another user ID and password when signing in.
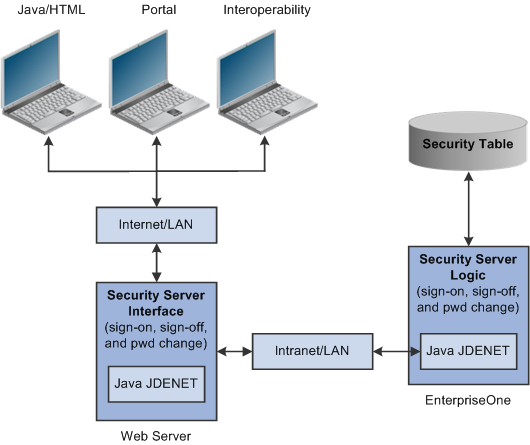
6.1.2 Security Server Architecture
As the security intermediary, the HTML Server security server handles these tasks:
-
Connecting to the JD Edwards EnterpriseOne Security Server for user security authentication and password when a web user signs in.
-
Switching to a secondary JD Edwards EnterpriseOne Security Server when the primary server is down, provided the correct HTML Server.ini settings are defined.
-
Notifying Java/HTML, Portal, and Interoperability client workstations when a user password has expired.
-
If an Interoperability user's password has expired, sign-in fails without notification of the cause.
-
Sending error message to user log after the web user has attempted unsuccessfully to sign in x number of times to JD Edwards EnterpriseOne, where x is the number of sign-in attempts defined in the F98OWSEC table.
-
Allowing Java/HTML and Portal users to change name and password.
-
Encrypting JDENET messages sent between the HTML server security Server and the JD Edwards EnterpriseOne security server.
-
Keeping a valid user session open until the user signs off or the session expires.
-
To the web user, sign-in and sign-out function the same as they do to a user on Windows, UNIX, or IBM i platforms.
6.1.3 Security Server Certified Platform
The Security Server is certified to run on the following platforms:
-
Linux / x86-64
-
Oracle Solaris / SPARC
-
Microsoft Windows /x86-64
-
HP-UX / Itanium
-
IBM AIX /Power
-
IBM i/Power
6.1.4 Additional References
-
Oracle Certification:
https://support.oracle.com, Certifications tab
Product = JD Edwards EnterpriseOne Enterprise Server
6.2 LDAP
This section discusses these topics:
-
Overview of LDAP
-
LDAP Architecture
-
LDAP Certified Platforms
-
Additional References
6.2.1 Overview of LDAP
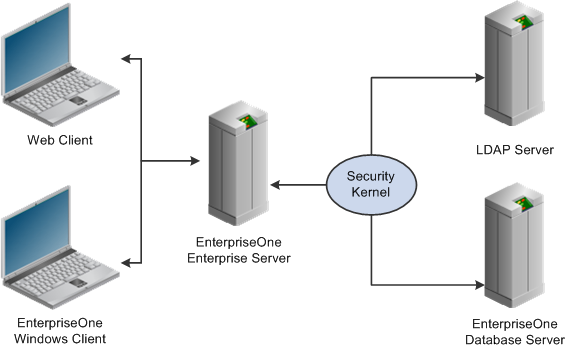
LDAP is an open industry standard protocol that directory services use to manage user profiles, such as user IDs and passwords, across multiple application systems. You can enable EnterpriseOne to use an LDAP-compliant directory service to manage EnterpriseOne user profiles and user-role relationships. After enabling EnterpriseOne for LDAP, user profiles can be administered through an LDAP version 3 compliant directory server, otherwise referred to as the LDAP server. System administrators use a third-party LDAP-enabled application to access the LDAP server.
LDAP provides these benefits:
-
Central administration and repository for user profiles.
-
You can easily maintain user profiles in a single location that serves multiple end user applications, including EnterpriseOne applications.
-
Reduced complexity.
You are not required to use several applications to maintain user profiles. In addition, users are not required to maintain multiple passwords across multiple systems.
LDAP support does not address single sign-on functionality that might exist through other EnterpriseOne functionality.
LDAP does not support certain user profile information. Such information remains in the domain of the EnterpriseOne server and must be maintained by the EnterpriseOne system administrator. Therefore, two distinct and separate user profiles may exist:
6.2.2 LDAP Architecture
The security kernel in the Enterprise Server performs authentication against the LDAP server when LDAP is enabled in the [SECURITY] section of the jde.ini file of the Enterprise Server. Otherwise, when LDAP is disabled, the security kernel authenticates the user against the Enterprise Server database.
6.2.3 LDAP Certified Platform
LDAP is certified to run on the following platforms:
-
Linux / x86-64
-
Oracle Solaris / SPARC
-
Microsoft Windows /x86-64
-
HP-UX / Itanium
-
IBM AIX /Power
-
IBM i/Power
6.2.4 Additional References
-
Oracle Certification:
https://support.oracle.com, Certifications tab
Product = JD Edwards EnterpriseOne LDAP
6.3 Single Sign-on
This section discusses these topics:
-
Overview of Single Sign-on
-
Single Sign-on Architecture
-
Single Sign-on Certified Platforms
-
Additional References
6.3.1 Overview of Single Sign-on
JD Edwards EnterpriseOne single sign-on enables users to access JD Edwards EnterpriseOne applications without re-entering a user ID and password. Single sign-on increases the security for the JD Edwards EnterpriseOne system since passwords are no longer passing between different sub-systems in JD Edwards EnterpriseOne.
Integration with Oracle Access Manager provides an alternative to the native sign-on security with JD Edwards EnterpriseOne. Using Oracle Access Manager as the sign-on mechanism to JD Edwards EnterpriseOne provides several benefits including:
-
Use of long user ids and passwords
-
Windows Native Authentication
-
Single sign-on with other Oracle and third-party applications
6.3.2 Single Sign-on Architecture
Single sign-on with Oracle Access Manager integrates with the JD Edwards EnterpriseOne HTML Server to provide an alternative to the native JD Edwards EnterpriseOne sign-on screen. An Oracle Access Manager Web Gate is installed on an Oracle HTTP Server, and it must be configured to protect the JD Edwards EnterpriseOne URLs that are used to access the HTML Server.
The following illustration shows the integration environment and process flow:
Figure 6-3 JD Edwards EnterpriseOne Single Sign-on through Oracle Access Manager
Description of "Figure 6-3 JD Edwards EnterpriseOne Single Sign-on through Oracle Access Manager"
6.3.3 Single Sign-on Certified Platform
Single Sign-on with Oracle Access Manager integrates with the JD Edwards EnterpriseOne HTML Server running on Oracle WebLogic Server. Refer to the HTML Server section for Certified Platforms.
6.3.4 Additional References
-
Oracle Certification:
https://support.oracle.com, Certifications tab
Product = JD Edwards EnterpriseOne HTML Server
Product = Oracle Access Manager