Single Sign-On Integration
Overview of Single Sign-On Integration
This chapter is intended to provide guidance for those planning to deploy or integrate Oracle E-Business Suite Release 12.2 in an enterprise single sign-on environment. Aimed primarily at project managers, DBAs, and system administrators, it describes how to integrate Oracle E-Business Suite Release 12.2 with the appropriate supporting products to provide an enterprise-wide single sign-on solution.
Important: Integration is a complex subject, with different components and sequences of steps being needed to accommodate different requirements. The integration options described require an understanding of the relevant products and deployment options.
In the context of this chapter, the term integration is used to refer to two closely related (but distinct) aspects of optionally deploying Oracle E-Business Suite in an enterprise-level single sign-on environment.
-
Integration with a single sign-on product such as Oracle Access Manager (OAM)
-
Integration with Oracle Directory Services (a Lightweight Directory Access Protocol, or LDAP, directory)
Note: All occurrences of the acronym "OAM" in this chapter are references to the Oracle Access Manager product, and not to the completely unrelated Oracle Applications Manager product. All occurrences of the acronym "LDAP" in this chapter are references to the support LDAP directories. Currently, this is Oracle Directory Services (Oracle Internet Directory and Oracle Unified Directory). Any items that are specific to a directory type will reference the directory itself.
There is a mutual dependency: authenticating against LDAP requires use of a single sign-on product (OAM), and deploying OAM requires the user population to be synchronized with Oracle Directory Services.
Oracle Access Manager
Oracle Access Manager 11g is the preferred Oracle single sign-on product for use with Oracle E-Business Suite Release 12.2. OAM also requires the use of Oracle E-Business Suite AccessGate, a Java Enterprise Edition application that maps a single sign-on user to an Oracle E-Business Suite user, and creates the Oracle E-Business Suite session for that user.
As the single sign-solution for Oracle Fusion Middleware, Oracle Access Manager deals with user authentication (validating the user's identity). In contrast, user authorization (controlling what the user can access) is handled by Oracle E-Business Suite itself.
Oracle Directory Services
Oracle Directory Services refers to both Oracle Internet Directory (OID) and Oracle Unified Directory. Procedures documented for implementing Oracle Directory Services apply to both these directories.
Oracle Directory Services are needed to link the namespaces (user information repositories) employed by Oracle Access Manager and Oracle E-Business Suite respectively. Linking the namespaces ensures that a particular user logging in via Oracle Access Manager is the same user that is represented within Oracle E-Business Suite's own FND_USER repository. The linking is done by associating externally-managed Oracle Access Manager users with internally-managed Oracle E-Business Suite users via Global Unique Identifiers (GUIDs). These GUIDs are generated by Oracle Directory Services, and the associated mapping functions are specific to it.
Oracle Directory Services are also required for another reason. While most usage of Oracle E-Business Suite is within an organization (such as a manufacturing company), certain application modules such as iRecruitment need to be available to outside users without accounts having to be created manually and responsibilities assigned. This means application modules that support self-registration must create user accounts synchronously (in Oracle E-Business Suite and the external directory at the same time) and on demand. Oracle E-Business Suite uses specific Oracle Directory Services function calls to handle these synchronous account creation tasks.
Combining Oracle Access Manager and Oracle Directory Services
Together, OAM and Oracle Directory Services enable an Oracle E-Business Suite Release 12.2 environment to provide the following enterprise single sign-on (SSO) features:
-
Users can access multiple Oracle E-Business Suite Release 12.2 instances (or a mixture of Oracle E-Business Suite Release 12.2 and other single sign-on enabled applications) by logging in only once (single sign-on).
-
A user who logs out of one SSO-enabled application is logged out of all others as well. This is sometimes called single sign-out, and improves security.
-
Administrators and users can perform user management activities, such as account creation, deletion, at enterprise level.
Oracle Identity Manager
A further optional integration option is provided by Oracle Identity Manager (OIM), which provisions users from a central repository to other repositories such as Oracle Directory Services, third-party LDAPs such as Microsoft Active Directory, or non-LDAP repositories such as Oracle E-Business Suite's FND_USER. OIM can be used independently of OAM and Oracle Directory Services, or in conjunction with both.
Oracle Identity Manager includes Connectors for numerous target systems (IT resources) in an organization. For example, OIM provides Connectors for Oracle E-Business Suite that enable provisioning of users to the FND_USER table and the HRMS tables used by Trading Communities Architecture (TCA).
Introduction to Enterprise User Management
In large organizations, users often have a large number of userids for a variety of network-based resources such as corporate web sites and custom applications. As the number of available resources grow, users and security administrators are faced with the increasingly difficult challenge of managing a proliferation of userids and passwords across different systems.
Enterprise identity management solutions allow security administrators to define a user in a single location such as an LDAP (Lightweight Directory Access Protocol) directory and share that common user definition throughout multiple parts of their enterprise.
Oracle Identity Management may be integrated with Oracle E-Business Suite to support centralized user management through Oracle Directory Services, and to support single sign-on functionality by using Oracle Access Manager.
In its default configuration, Oracle E-Business Suite Release 12.2 allows registered users to log in using credentials stored directly in Oracle E-Business Suite. In this default configuration, Oracle E-Business Suite system administrators are responsible for maintaining the local repository of registered Oracle E-Business Suite users.
When optionally integrated with the Oracle Identity Management Suite (which includes OAM and Oracle Directory Services), Oracle E-Business Suite system administrators can reconfigure their environments to delegate both user administration and user authentication to Oracle Access Manager. This integration requires significant changes to how Oracle E-Business Suite Release 12.2 handles authentication. Instead of performing authentication natively, through the local Oracle E-Business Suite FND_USER table, Oracle E-Business Suite Release 12.2 now delegates this functionality to Oracle Access Manager, by using Oracle E-Business Suite AccessGate. In this configuration, Oracle E-Business Suite Release 12.2 can direct unauthenticated users to Oracle Access Manager for identity verification and securely accept identities vouched for by the single sign-on mechanism.
Oracle Access Manager may, in turn, be integrated with existing third-party authentication systems such as Microsoft Windows (Kerberos), and Oracle Directory Services may be integrated with existing third-party LDAP directories such as Microsoft Active Directory.
Note: Oracle Access Manager always performs authentication against information stored in Oracle Directory Services, even if a third-party authentication mechanism is in use.
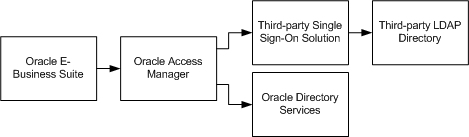
The following diagram illustrates the high-level structure of a typical integration.
High-Level Diagram of Typical Integration
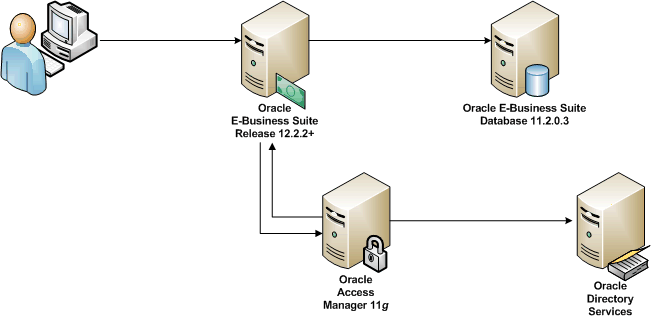
Note: Where a third-party authentication mechanism is in use, Oracle Access Manager and Oracle Directory Services are still required: they provide bridge functionality between Oracle E-Business Suite and the third-party single sign-on solution.
Integration Actions and Options
Integration of Oracle E-Business Suite with Oracle Access Manager is achieved by using the OAM WebGate agent, which is used in conjunction with Oracle E-Business Suite AccessGate.
Note: Each Oracle E-Business Suite instance requires its own deployment of the Oracle E-Business Suite AccessGate application.
Note: For a detailed description of the role of agents in Oracle Access Manager, refer to the Oracle Fusion Middleware Administrator's Guide for Oracle Access Management.
This section focuses on the details of integration using WebGate and Oracle E-Business Suite AccessGate.
When an unauthenticated user attempts to access a protected Oracle E-Business Suite resource, the user is directed to the Oracle E-Business Suite AccessGate application. This application is protected by the Oracle Access Manager server, so the authentication request is rerouted to a separate HTTP Server on which Oracle Access Manager WebGate is installed. This is a component of Oracle Access Manager that intercepts HTTP requests and redirects them to the Oracle Access Manager server to determine if and how the resources are allowed to be accessed, and to authenticate the current user if authentication is required. If Oracle Access Manager is already deployed in the environment, an existing WebGate can be configured for this purpose.
After a user is initially authenticated by Oracle Access Manager, the request for a resource and credentials returned by Oracle Access Manager server are picked up by Oracle E-Business Suite AccessGate. If the credentials are valid, Oracle Access Manager connects to the Oracle E-Business Suite database to link the Oracle Directory Services user to an Oracle E-Business Suite user. If Oracle E-Business Suite fails to identify a linked user for the Oracle Directory Services user, the user is redirected to the linking page so that he can map his unlinked Oracle Directory Services user account to his Oracle E-Business Suite user name. After this mapping is done, the originally requested resource is returned with a valid authenticated Oracle E-Business Suite user session. All subsequent requests for Oracle E-Business Suite resources are then returned directly to the user, for as long as the user session remains valid.
The sequence of actions is illustrated in the following diagram.
Integration Sequence Diagram
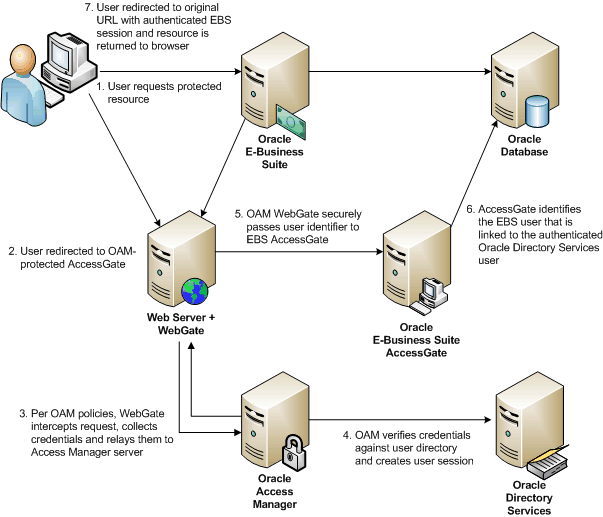
Oracle E-Business Suite AccessGate must be installed in the same internet domain (for example, example.com) as the Oracle E-Business Suite application tier servers. This is because several Oracle E-Business Suite domain cookies are shared between the application tier servers and the Oracle E-Business Suite AccessGate server.
Oracle E-Business Suite AccessGate Features
Forced Authentication
Similar to the session timeout behaviors, the Forced Authentication feature forces users to reauthenticate with Oracle Access Manager when ICX Session Timeout is reached. This happens regardless of whether OAM timeout has been reached.
The following are prerequisites for the Forced Authentication feature with Oracle E-Business Suite:
-
Oracle E-Business Suite Release 12.2.3 through Release 12.2.11 with Patch 32651269.
-
Integration with Oracle Access Manager 12c. For more information, refer to My Oracle Support Knowledge Document 2339348.1, Integrating Oracle E-Business Suite Release 12.2 with Oracle Access Manager 12c using Oracle E-Business Suite Access Gate.
-
Deployment of Oracle E-Business Suite AccessGate 1.4 or later. For more information, refer to My Oracle Support Knowledge Document 2202932.1, Using the Latest Oracle E-Business Suite AccessGate for Single Sign-On Integration with Oracle Access Manager.
Forced Authentication is disabled by default (or "turned off"). It is controlled by profile option Applications SSO Force Authentication.
| Profile Option Name | Code (Internal Name) |
|---|---|
| Applications SSO Force Authentication | APPS_SSO_FORCE_AUTH |
Applications SSO Force Authentication can be set to either one of the following values:
-
Enabled: The Forced Authentication feature is turned on when the profile APPS_SSO_FORCE_AUTH is set to Enabled. Enabled means on ICX session timeout, the user will be required to enter their user credentials, similar to Local login.
-
Disabled: The Forced Authentication feature is turned off when the profile APPS_SSO_FORCE_AUTH is set to Disabled. Disabled means the user session will automatically be revalidated as long as the OAM session is not timed out or invalidated.
This profile option can be set at either site or user level.
Note that this feature requires /oamreauthenticate to be configured as a protected resource in OAM. Without configuring /oamreauthenticate as a protected resource, with APPS_SSO_FORCE_AUTH enabled on ICX Session Timeout when attempting to redirect to OAM login, the user will receive the following error: "The requested URL /oamreauthenticate was not found." See the Oracle Access Manager documentation for configuration details.
Limit SSO Sessions
Limit SSO Sessions is an Oracle E-Business Suite AccessGate feature available for Oracle E-Business Suite Release 12.2 which limits the user to only one active ICX session.
For example, if a user logs in from one browser or PC and then logs into another, since users are limited to only one active session all other sessions for that user will be timed out. If the user reauthenticates a session that was previously timed out, the newly reauthenticated session now becomes the single active session and all other sessions for that user will be timed out.
Limiting SSO Sessions requires the Forced Authentication feature (APPS_SSO_FORCE_AUTH) to be enabled.
| Profile Option Name | Code (Internal Name) |
|---|---|
| Applications SSO Limit ICX Sessions | APPS_SSO_LIMIT_SESSIONS |
If the user accesses a function and is redirected to the OAM Login page, they are able to reauthenticate and continue the session at which time any active ICX sessions will again be timed out.
Advanced Options and Configurations
Various options exist for extending the basic integration of Oracle E-Business Suite with Oracle Access Manager. These include using multiple WebGates for load balancing, enabling SSL communication between the nodes, and configuring one or more nodes in a DMZ or with a reverse proxy. This subsection will briefly mention any special Oracle E-Business Suite integration steps that may need to be taken for different Oracle Access Manager configurations.
Deploying Oracle E-Business Suite AccessGate in a TLS-Enabled Environment
In production environments, it is advisable to use TLS on both the Oracle E-Business Suite application tier and on the WebLogic Server instance where the Oracle E-Business Suite AccessGate is deployed. Also, the WebGate plug-in should be deployed on an HTTP server that is secured using TLS.
An important related point is that Oracle E-Business Suite application tiers and WebLogic Server instances must all be configured to use the same protocol (either HTTP or HTTPS). If the relevant nodes are configured to use TLS (HTTPS), the HTTP server on which WebGate is installed must also be configured to use TLS. If, however, the HTTP server running WebGate is configured to use TLS, it is not necessary to configure TLS on the Oracle E-Business Suite application tiers or WebLogic Server instances.
There are other considerations that apply to SSL environments. For further information, refer to the following resources:
-
Steps to enable TLS communication for the Oracle Access Manager components: Oracle Fusion Middleware Administrator's Guide for Oracle Access Management
-
Oracle WebLogic Server configuration steps: Oracle Fusion Middleware Securing Oracle WebLogic Web Services for Oracle WebLogic Server
-
Oracle HTTP Server: Oracle Fusion Middleware Administrator's Guide
Deploying Oracle E-Business Suite AccessGate with an Oracle RAC Database
A database instance configured to use Oracle RAC load balancing requires creation of either a JDBC multidata source or Active GridLink for Oracle RAC. This can be done using the Oracle WebLogic Server Administration Console.
Once the multidata source has been created, an automated deployment script (txkEBSAuth.xml) can be run with the appropriate options.
This script performs two major functions, which can either be performed independently or together in a single execution. These functions are:
-
Create a connection pool and data source for Oracle E-Business Suite AccessGate
-
Deploy the Oracle E-Business Suite AccessGate war file with a customized application deployment plan
For more information, refer to Oracle Fusion Middleware Administering JDBC Data Sources for Oracle WebLogic Server.
Deploying Oracle E-Business Suite with Single Sign-On Integration in a DMZ
When configuring single sign-on using Oracle Access Manager and Oracle E-Business Suite AccessGate in a DMZ, specific firewall ports must be opened to allow additional connections from the end user to Oracle E-Business Suite AccessGate, and to allow communication between WebGate (located in the DMZ) and Oracle Access Server (located on the internal network). In addition, some of the values needed to configure Oracle E-Business Suite AccessGate will need to be modified to point back to a reverse proxy. There is no need to open the ports for LDAP or LDAPS connections from the DMZ to the internal network.
For more information, refer to My Oracle Support Knowledge Document 1375670.1, Oracle E-Business Suite Release 12.2 Configuration in a DMZ.
If you are using Oracle E-Business Suite Release 12.2.6 or later, you can choose to configure single sign-on and local authentication at site and at server level. For example, you may choose to register your Oracle E-Business Suite Release 12.2.6 or later instance with Oracle Access Manager for single sign-on at site level as the default for all internal users. For external users, you may not wish to register external entry points for single sign-on, but use local user authentication.
For more information, refer to My Oracle Support Knowledge Document 1576425.1, Integrating Oracle E-Business Suite Release 12.2 with Oracle Access Manager 11gR2 (11.1.2) using Oracle E-Business Suite AccessGate.
Centralized Logout
When logging out of an application protected by Oracle Access Manager, the host and domain cookies created by Oracle Access Manager are removed, which forces a user to re-authenticate the next time he accesses a protected resource. However, this process does not clean up sessions, or remove cookies specific to partner applications such as Oracle E-Business Suite.
The process of logging out must invalidate all sessions for Oracle Access Manager, WebGate, and Oracle E-Business Suite. To ensure that these cookies are cleared when a single sign-on session is terminated, Oracle Access Manager and Oracle E-Business Suite AccessGate must be configured to initiate a "callback" to a script that will clean up these sessions. Without this, a user who terminates his single sign-on session may still be able to access Oracle E-Business Suite, or even create a new Oracle E-Business Suite session.
To help implement this functionality, a sample script called samplecleanup.html is provided. Using this script requires making some site-specific customizations to it, then configuring Oracle E-Business Suite AccessGate to load it. This file will subsequently be invoked whenever a user logs out of SSO, terminating any current sessions the user has for Oracle E-Business Suite instances protected by that WebGate.
The script works with Oracle E-Business Suite AccessGate to perform several actions:
-
Registers logout callbacks for the current Oracle E-Business Suite environment, and any others that are protected by this WebGate, which must be provided. This logout callback is a servlet within Oracle E-Business Suite AccessGate, which:
-
Destroys the Oracle E-Business Suite session for the instance it is protecting
-
Removes the ICX cookie
-
Frees allocated E-Business resources
-
Returns an image indicating success or failure
-
-
Processes the logout callbacks one by one, indicating success or failure.
-
Removes any cookies that are listed, such as WebGate 10g cookies, or session-related cookies for any custom applications that are deployed.
-
Redirects the user to a target URL (if one is provided) to control where a user is sent after the logout completes. The value of the target URL which will depend on where the user initiated the logout.
The samplecleanup.html script can be used regardless of where a user initiates the logout request. When logging out of Oracle E-Business Suite, Oracle E-Business Suite AccessGate will handle the logout process for the current instance, and then load this cleanup script on other WebGates (as configured in the script). As the scripts are loaded in parallel, the script also invokes a logout on the Oracle Access Manager server, which expires the Oracle Access Manager session and associated cookies. For external partner applications such as Oracle WebCenter, the logout link must be modified to invoke the cleanup script, which will redirect to the original logout URL or landing page upon completion.
The samplecleanup.html script has to be customized on a site-specific basis, as it must explicitly list the locations of every deployed Oracle E-Business Suite AccessGate application that is protected by the WebGate in question. The customized script must then be deployed to the server where WebGate is installed, so the Oracle Access Manager Server can load it.
Enterprise User Management
Oracle Directory Services is the integration point that allows Oracle E-Business Suite to participate in enterprise-level user management. Each Oracle E-Business Suite instance must still maintain a record of registered users, in the form of the traditional application accounts. However, the level of abstraction needed for an enterprise level user requires a mechanism that can uniquely identify a user across the enterprise. This is accomplished through a globally unique identifier (GUID). Oracle Directory Services and Oracle E-Business Suite store GUID information for each enterprise level user; the GUID can be considered as an identity badge that is recognized by both Oracle Directory Services and Oracle E-Business Suite.
Another requirement in such an environment is for user enrollment to be done only once, at well-defined places, with the user subsequently being known to the rest of the enterprise. Two additional features enable support for automatic propagation of user information across an enterprise:
-
A synchronization process between Oracle Directory Services and a third-party LDAP server
-
A provisioning process between Oracle Directory Services and Oracle E-Business Suite
Much of the complexity involved with integrating Oracle E-Business Suite into a single sign-on environment arises because of the need to consolidate fragmented or duplicated user data in the single sign-on environment, as a legacy of integrating previously isolated systems. The solution described in this document provides mechanisms to link the existing data together using the GUID. In addition, bulk migration tools are provided to move a large number of users between Oracle Directory Services and Oracle E-Business Suite during the transition to a single sign-on environment.
Additional Single Sign-On Features, Limitations, and Known Issues
Advanced features include automatically keeping a set of user profile information synchronized across an enterprise for an entity, and the ability to link an account in Oracle Directory Services to multiple application accounts in Oracle E-Business Suite.
In this release, provisioning from Oracle E-Business Suite to Oracle Directory Services is synchronous: that is, all user management operations carried out in Oracle E-Business Suite are also carried out in Oracle Directory Services. However, provisioning from Oracle Directory Services to Oracle E-Business Suite is done asynchronously.
The solution described here does not address the issue of authorization. After a user has been authenticated, Oracle E-Business Suite retrieves from the relevant FND tables the authorization information associated with the application account the user is logged into. Authorization information for application accounts is managed through application responsibilities. Oracle E-Business Suite applies authorization checks as and when required during the user's session.
| Configuration Option | Possible Settings | Configured Using |
|---|---|---|
| Initial Source of User Information |
|
Execution of manual initial provisioning steps (described later). |
| Source of Truth for Updates to User Information |
|
Provisioning profile selected for Oracle Directory Integration Platform (described later). |
| New Userids Created in Oracle Directory Services |
|
Related Oracle E-Business Suite Profile Options:
|
| New Userids Created in Oracle E-Business Suite |
|
Related Oracle E-Business Suite Profile Options:
|
| Specific Oracle E-Business Suite Userids |
|
APPS_SSO_LOCAL_LOGIN profile option |
| All Oracle Directory Services Userids |
|
APPS_SSO_ALLOW_MULTIPLE_ ACCOUNTS profile option |
The above list of identity management configuration options is not exhaustive.
Deployment Scenario 0: E-Business Suite + SSO and Oracle Directory Services
This section explains the technical details and deployment steps using a simplified deployment scenario, where an existing Oracle E-Business Suite instance is integrated with a fresh Oracle Access Manager/Oracle Directory Services infrastructure. Although many real world deployments are likely to be more complex, this scenario serves to illustrate the core concepts and procedures of the integration effort. In later sections, we build on this basic scenario to describe more sophisticated situations such as the existence of a third-party single sign-on solution, or the presence of multiple user repositories. The goal is not to describe every conceivable deployment variation, but rather to provide a number of representative cases from which implementers can intelligently derive the exact steps needed for their particular requirements.
Starting Point
This scenario presumes that:
-
Oracle E-Business Suite Release 12.2 has been installed and has an existing user population.
-
Oracle Access Manager, Oracle E-Business Suite AccessGate, and Oracle Directory Services have all been installed (on a separate machine) in accordance with the appropriate instructions.
-
Oracle Directory Services has no currently existing users, apart from pre-seeded users.
The requirement is to integrate Oracle E-Business Suite Release 12.2 with Oracle Access Manager, Oracle E-Business Suite AccessGate, and Oracle Directory Services.
Solution Outline
The results of implementing this solution will be that:
-
Oracle E-Business Suite will delegate user sign-on and authentication to Oracle Access Manager.
-
Oracle Access Manager will authenticate user credentials against user entries in Oracle Directory Services.
-
Oracle Directory Services will contain the account ID and password for every user that is configured for single sign-on.
Warning: For security reasons, local users and standard administrative accounts such as SYSADMIN should never be configured for single sign-on.
Deployment Scenario Flow
User Management Options
Oracle E-Business Suite Release 12.2 maintains a local cache of user information in its existing user directory (FND_USER). The Oracle E-Business Suite User Bulk Migration Tool can be used to migrate existing Oracle E-Business Suite application accounts to single sign-on accounts in Oracle Directory Services. After the migration, a system administrator has a number of user management options about the locations where the user information is created, and where it is provisioned (sent).
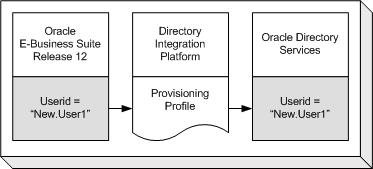
Option 1: Provision Oracle E-Business Suite Users to Oracle Directory Services
All user information is created in Oracle E-Business Suite, then provisioned into Oracle Directory Services: Oracle E-Business Suite is configured as a provisioning integrated application with Oracle Directory Services. System administrators configure the provisioning integration by using Directory Integration Platform (DIP) provisioning profiles. A DIP server synchronizes policy changes in the directory with connected databases, using a separate DIP provisioning profile for each database.
The creation of a new application account in Oracle E-Business Suite will automatically trigger the creation of a new single sign-on account in Oracle Directory Services. Some of the user attributes from the application account may be provisioned in the single sign-on account in Oracle Directory Services during account creation.
Option 1 Flow
Option 2: Provision Oracle Directory Services Users to Oracle E-Business Suite
All user information is created in Oracle Directory Services, then provisioned into Oracle E-Business Suite. Oracle E-Business Suite is configured as a provisioning integrated application with Oracle Directory Services.
System administrators configure the provisioning integration using provisioning profiles: the creation of a new single sign-on account in Oracle Directory Services will automatically trigger the creation of a new application account in Oracle E-Business Suite. Some of the user attributes from the single sign-on account may be provisioned in the application account in Oracle Directory Services during account creation.
With provisiontype=3 (OID to App), the OID Enterprise Manager console shows both 'Applications to OID' and 'OID to Applications' enabled. This is expected due to the need to make use of the SUBSCRIPTION_ADD event for the 'Applications to OID' provisioning profile. The user is added to the subscription list once the user is successfully created on the Applications side.
Option 2 Flow
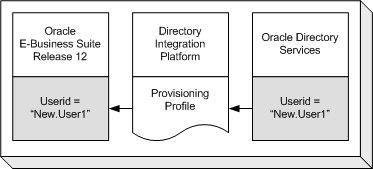
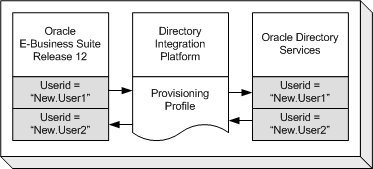
Option 3: Bidirectional Provisioning Between E-Business Suite and Oracle Directory Services
All user information is created in either Oracle Directory Services or Oracle E-Business Suite, then provisioned into the other system. Oracle E-Business Suite is configured as a provisioning integrated application with Oracle Directory Services. System administrators configure the provisioning integration using provisioning profiles.
The creation of a new application account in Oracle E-Business Suite will automatically trigger the creation of a new single sign-on account in Oracle Directory Services. The creation of a new single sign-on account in Oracle Directory Services will automatically trigger the creation of a new application account in Oracle E-Business Suite.
During account creation, some of the user attributes from the application account may be provisioned in the single sign-on account in Oracle Directory Services, and some of the user attributes from the single sign-on account may be provisioned in the application account in Oracle Directory Services.
Option 3 Flow
Synchronizing User Attributes
For all three options above, a predefined set of user attributes is synchronized between Oracle E-Business Suite and Oracle Directory Services. Currently-supported attributes are listed later in the Supported Attributes section.
End-User Experience
This section describes the user's perception of the single sign-on environment.
Single Sign-On User Experience
On attempting to access an Oracle E-Business Suite environment, a user who has not yet been authenticated with Oracle Access Manager is directed to a single sign-on login page:
Oracle Access Manager Single Sign-On Login Page
After authentication using Oracle Access Manager (or if authentication has previously been carried out), the user is redirected to the requested page or the user's home page in Oracle E-Business Suite Release 12.2.
Sign-Out User Experience
When a user logs out of an Oracle E-Business Suite instance, he is also logged out of Oracle Access Manager, as well as any other applications (partner applications) that have been integrated with Oracle Access Manager and have been accessed through Oracle Access Manager.
Single Sign-On Authentication Flow
The user attempts to access the Oracle E-Business Suite Release 12.2 instance, and Oracle E-Business Suite looks for a session cookie. If the cookie is found and validated, the user is directed to the requested application page, and the rest of the steps shown here are skipped.
If the session cookie is not found, Oracle E-Business Suite redirects the user to an Oracle E-Business Suite AccessGate URL in Oracle Access Manager. This URL is intercepted by OAM WebGate, which obtains policy information from OAM and then checks for a valid OAM session cookie in the user's browser. If one does not exist, it redirects the user to the credential collection page, which is an unprotected page in AccessGate. The credentials are submitted to OAM, which looks for an Oracle Single Sign-On security cookie in the user's browser. If the Oracle Single Sign-On security cookie is not found, the user must log into a valid account by using Oracle Access Manager before authentication can proceed further.
Next, Oracle Access Manager contacts Oracle Directory Services and authenticates the user's credentials against the list of registered users in Oracle Directory Services. After successful authentication, Oracle Access Manager sets an OAM session cookie in the user's browser, and retrieves user attributes for the single sign-on account from Oracle Directory Services.
Once the credentials are verified, OAM returns the user to the URL in Oracle E-Business Suite AccessGate. It passes a request that includes HTTP response headers containing a user identifier and the GUID. Oracle E-Business Suite verifies the URL token, locates the application user and creates an application session and corresponding cookie, based upon the user's assigned application responsibilities and roles. This process entrusts the process of user authentication to Oracle Access Manager, and user authorization to Oracle E-Business Suite. Oracle E-Business Suite then redirects the user to the requested application page, or the user's home page.
Session Timeout Behavior
When both the application session and the single sign-on session timeout, the user will be directed to the single sign-on login page to re-authenticate. After a successful re-authentication, the user will be redirected back to Oracle E-Business Suite. The application page the user sees depends on the application technology stack in use; see table below.
Currently, when the application session has expired, but not the single sign-on session, the user will be directed to Oracle E-Business Suite AccessGate, and then back to Oracle E-Business Suite Release 12.2, without being prompted to re-authenticate. Depending on the technology stack in use at the time when the session timeout occurred, the user will then see one of the following pages listed in the table below.
| Technology Stack | Session Timeout Behavior |
|---|---|
| Oracle Application Framework | Application home page |
| CRM | If the current request on detection of application session expiration was a 'GET', the user sees the requested page. If the current request was a 'POST', the user sees the posting page without the post having been performed. |
| Forms | A series of pop-up windows will appear, leading the user to the Oracle Access Manager login page for re-authentication. |
When an application session is terminated because the maximum valid period has been reached, or because of a period of user inactivity, Oracle E-Business Suite redirects the user to Oracle Access Manager for re-authentication. Oracle Access Manager checks the single sign-on cookie; if it is still valid, the user is redirected back to Oracle E-Business Suite Release 12.2. If the single sign-on cookie has expired as well, Oracle Access Manager requires the user to authenticate again before redirecting him back to Oracle E-Business Suite Release 12.2.
The application session timeout value takes precedence over the Oracle Access Manager timeout settings. For example, until an application session times out (or the user explicitly logs out), a user may continue to access the partner application even if his Oracle Access Manager security cookie has expired. We therefore recommend setting Oracle E-Business Suite's application session timeout value to be equal to, or less than, that of the Oracle Access Manager server.
User Management Options
This section describes the various options for management of users in a single sign-on environment.
Local Access to Oracle E-Business Suite
Selected users can be permitted to log in to the application directly, that is, without going through the single sign-on process. This allows users such as the system administrator to troubleshoot a configuration when Oracle Access Manager is not functioning correctly, or is unavailable. Such local users can now log into the application directly by using the applications login page, AppsLocalLogin.jsp. The supplied SYSADMIN account is configured to have local access. In addition, the SYSADMIN account can control which additional users (if any) are permitted to have local access to the Oracle E-Business Suite; this is accomplished through the Applications SSO Login Types (APPS_SSO_LOCAL_LOGIN) profile option.
Important: Generic accounts, especially those with administrative rights (such as SYSADMIN), should always be local only.
Identifying a User Across the Enterprise
After Oracle Access Manager integration is complete, user information exists in two places: Oracle Directory Services and Oracle E-Business Suite Release 12.2.
This shared information has the following characteristics:
-
A GUID uniquely identifies a user across multiple systems.
-
Both Oracle Directory Services and Oracle E-Business Suite store GUID information for each single sign-on user.
-
During the authentication handshake between Oracle Directory Services and Oracle E-Business Suite, Oracle Access Manager passes the authenticated user information in the form of GUID to Oracle E-Business Suite AccessGate, which then uses the GUID to locate the corresponding application account.
-
Once a GUID is generated and stored in both a single sign-on account in Oracle Directory Services and an application account in Oracle E-Business Suite, the two accounts are said to be linked.
-
A number of processes are used to establish this link. The most commonly used ones are explained below, and the rest in the more advanced deployment scenarios later in this section.
Bulk Migration of Users
Tools are provided to migrate existing users in bulk between Oracle Directory Services and Oracle E-Business Suite. Both Oracle Directory Services and Oracle E-Business Suite provide command-line utilities to export and import users using flat text files in LDIF format.
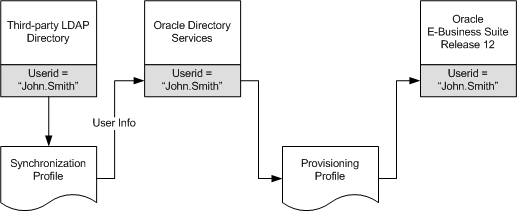
User Provisioning Between Oracle E-Business Suite and Oracle Directory Services
New users created on either system can be provisioned into the other through the provisioning process. The provisioning system consists of components of both Oracle Directory Services and Oracle E-Business Suite that queue user events on each system, plus an Oracle Directory Services process that periodically pushes or pulls these events to or from Oracle E-Business Suite. The provisioning process establishes the GUID link for provisioned accounts. During this process, single sign-on accounts are automatically linked to Oracle E-Business Suite application accounts.
Diagram of User Provisioning Between Oracle E-Business Suite and Oracle Directory Services
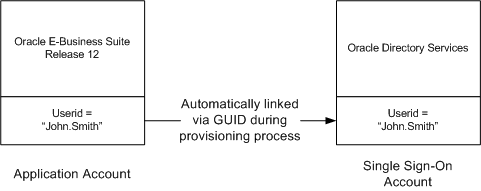
Provisioning has the following characteristics:
-
Once linked, user changes from either system can be provisioned into the other.
-
The provisioning process between Oracle Directory Services and each Oracle E-Business Suite instance is determined by a provisioning profile.
-
The provisioning profile controls which user events are provisioned, the direction of provisioning, and the user attributes included in each event.
-
Oracle E-Business Suite is said to be a provisioning integrated application with Oracle Directory Services when a provisioning profile is created for it.
Refer to the Supported Attributes section for information on which attributes can be provisioned between the systems, and Configuring Directory Integration Platform Provisioning Templates for more details on the provisioning process.
Strategies for User Management
At the start of the deployment, Oracle E-Business Suite Release 12 is the sole repository of user information. Users who will need to access Oracle E-Business Suite using Oracle Access Manager must already exist or be created in Oracle Directory Services.
For pending users that are enabled in Oracle E-Business Suite after user creation, the IDENTITY_MODIFY event from Oracle E-Business Suite to Oracle Directory Services must be enabled.
Note: Refer to Configuring Directory Integration Platform Provisioning Templates for more details.
Populating Oracle Directory Services with Existing Oracle E-Business Suite Users
Existing Oracle E-Business Suite users can be migrated into Oracle Directory Services by means of the bulk migration tool (see Migrating Data Between Oracle E-Business Suite and Oracle Directory Services for details).
Creating New Users
After the initial migration, you may choose to allow new users to be created either from Oracle Directory Services or from Oracle E-Business Suite, and then provision them into the other system. This is achieved by enabling either the SUBSCRIPTION_ADD event from Oracle Directory Services to Oracle E-Business Suite, or the IDENTITY_ADD event from Oracle E-Business Suite to Oracle Directory Services. Refer to Configuring Directory Integration Platform Provisioning Templates for more details.
Bidirectional Provisioning
Alternatively, you may choose to create new users from either Oracle Directory Services or Oracle E-Business Suite, and then provision them into the other system. This is achieved by enabling both the SUBSCRIPTION_ADD event from Oracle Directory Services to Oracle E-Business Suite, and the IDENTITY_ADD event from Oracle E-Business Suite to Oracle Directory Services. Refer to Configuring Directory Integration Platform Provisioning Templates for more details.
Bidirectional provisioning requires careful planning, and the following restrictions must be considered:
-
The provisioning process from Oracle Directory Services to Oracle E-Business Suite is asynchronous. In contrast, the provisioning process from Oracle E-Business Suite to Oracle Directory Services is synchronous.
-
Whether new users are created in either Oracle Directory Services or Oracle E-Business Suite, they must be granted the appropriate roles or responsibilities using Oracle E-Business Suite User Management in order to access application functionality.
-
The provisioning events will fail if, for example, a user with the same user name has been created concurrently on the other system, or some aspect of the user's profile does not meet the policy set on the other system. As there is no mechanism to roll back the original change on the system that triggered the event, the failure can put the entire system into an unstable state. It is therefore essential to coordinate the account policy on all the systems involved, and place appropriate safeguards on the user creation process. For example, user names created directly on one system need to be chosen in the context of names used across the single sign-on environment.
Updating User Information
User information stored in Oracle Directory Services single sign-on accounts is generally managed independently of user information stored in Oracle E-Business Suite Release 12.2 application accounts.
System administrators must decide:
-
Which user attributes are to be provisioned between an Oracle E-Business Suite Release 12.2 instance and Oracle Directory Services.
-
Which system is to be the primary "source of truth" for a given attribute. This determines the provisioning direction for that attribute.
System administrators then enable the IDENTITY_MODIFY events in the appropriate direction with the appropriate attribute list. Refer to Configuring Directory Integration Platform Provisioning Templates for more details.
Note the following current restrictions:
-
Updates to email ID in Oracle Directory Services are not correctly reflected in Oracle E-Business Suite (HZ_CONTACT_POINTS in TCA) unless the PERSON_PARTY_ID foreign key in the FND_USER table has been defined. Furthermore, if PERSON_PARTY_ID is changed, because a user is linked to another person in TCA, information stored in Oracle Directory Services can overwrite this other person's information during provisioning.
-
Provisioning from Trading Community Architecture (TCA) to Oracle Directory Services is not supported.
-
Provisioning of data from Oracle Human Resources to Oracle Directory Services is supported through the Oracle Human Resources Agent, which is released as part of the Oracle Directory Services suite of utilities. Note that the Oracle Human Resources Agent supplied with Oracle Directory Services is unidirectional. That is, it ensures that Oracle Directory Services is synchronized with HR, so that changes to user data in HR cause the corresponding data to be updated in Oracle Directory Services. However, if changes are made to user data in Oracle Directory Services, the HR connector does not synchronize these changes back to HR. A bidirectional connector is planned for a future build.
Terminating and End-Dating Users
Dates are not synchronized between Oracle Directory Services and Oracle E-Business Suite. However, the provisioning process may be set up so that when a single sign-on account in Oracle Directory Services is deleted, the associated Oracle E-Business Suite application accounts is end-dated. This is accomplished in the provisioning profile, by enabling the IDENTITY_DELETE event from Oracle Directory Services to Oracle E-Business Suite.
Note: Refer to Configuring Directory Integration Platform Provisioning Templates for details.
Subject to organizational security and audit policies, it may be preferable to disable single sign-on accounts in Oracle Directory Services rather than delete them, since this allows an applications account to be re-enabled at a later date as required. This can be particularly useful in the case of contractors who may leave and rejoin.
Additional Information: See Enabling and Disabling Users for more information on enabling/disabling users.
Password Management
One of the major objectives of single sign-on integration is centralized user password management using Oracle Directory Services, which provides the following features:
-
Accessing Oracle E-Business Suite using Oracle Access Manager does not require passwords in the Oracle E-Business Suite; the password stored in Oracle Directory Services is sufficient for authentication.
-
The password for an application account in Oracle E-Business Suite Release 12.2 is replaced with the reserved keyword 'EXTERNAL', if (as will usually be the case) the only permitted method to access that application account is through Oracle Access Manager
-
Password management for such users is carried out entirely in Oracle Directory Services.
End-User Password Changes
The majority of end users will be able to change their single sign-on passwords using the standard methods provided by Oracle Directory Services. For example, users may employ Oracle Identity Manager.
System Administrator Password Changes and Resets
To reset single sign-on passwords, an administrator using Oracle Directory Services should follow the methods detailed in the "Managing Accounts and Passwords" chapter of the Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory and "Managing User Accounts" section of Oracle Fusion Middleware Administering Oracle Unified Directory.
Password Policies
Oracle Directory Services is designated as the primary user directory for passwords. The user's password creation, modification and Oracle Access Manager login activities are subject to the Oracle Directory Services rules that govern how passwords are created and used. For example, Oracle Directory Services system administrators may establish policies for password expiration, minimum length, and alphanumeric mixes. Refer to either the Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory or Oracle Fusion Middleware Administering Oracle Unified Directory, depending which is used, for an explanation of supported password policies.
If the provisioning profile specifies that passwords in application accounts are to be provisioned from Oracle E-Business Suite Release 12.2 to Oracle Directory Services, Oracle E-Business Suite Release 12.2 password policies must be at least as restrictive as the ones in Oracle Directory Services. This ensures that passwords can be successfully propagated from Oracle E-Business Suite Release 12.2 to the single sign-on accounts in Oracle Directory Services.
Note: Passwords stored in Oracle Directory Services are case sensitive. Mixed case passwords in Oracle E-Business Suite are migrated with the case preserved.
Password Management and Applications SSO Login Types
For users who have been granted local access to Oracle E-Business Suite by using the Applications SSO Login Types (APPS_SSO_LOCAL_LOGIN) profile, Oracle E-Business Suite retains the relevant applications account password. This is true even if Oracle Directory Services or the third-party LDAP directory has been designated as the primary user directory for passwords. All existing password-related features in the Oracle E-Business Suite remain the same for local accounts. For example, the user must use the Self-Service change password screen (Preferences page) to maintain passwords.
For users who have both single sign-on and local access to Oracle E-Business Suite, local password change in Oracle E-Business Suite can be synchronized to Oracle Directory Services, if the provisioning profiles are set up accordingly. The reverse direction is not possible, because Oracle Directory Services only stores the hash of the passwords, not encrypted passwords as Oracle E-Business Suite does.
Because of the potential difficulty of educating users about the special password management considerations that apply to application accounts configured with the Applications SSO Login Types (APPS_SSO_LOCAL_LOGIN) profile, this profile option should, as noted earlier, only be employed for a limited number of system administration or other advanced accounts. The system administrator is required to set the local password using the AFPASSWD utility or FNDCPASS utility, in case user passwords stored only in LDAP (APPS password is set to EXTERNAL) also need to be stored locally in Oracle E-Business Suite.
For more information about the AFPASSWD and FNDCPASS utilities, refer to the Oracle E-Business Suite Maintenance Guide.
Critical Implementation Decisions
-
Oracle Directory Services has a powerful and flexible set of configuration options. Most Oracle E-Business Suite system and security administrators will be able to use the default Oracle Directory Services configuration. Security administrators with advanced security requirements may choose to use alternative Oracle Directory Services configurations.
Items of particular importance to Oracle E-Business Suite integration include:
-
Identity management realm
-
DIT structure
-
What attribute is chosen as the nickname attribute
-
Whether new users are to be created:
-
Only from Oracle Directory Services
-
Only from Oracle E-Business Suite Release 12.2
-
From both Oracle E-Business Suite and Oracle Directory Services
-
-
-
Whether updates to user information are to be provisioned. If so, what user attributes are to be provisioned, and the direction of provisioning.
-
Which users should only use local access to Oracle E-Business Suite Release 12.2, which users only need access through Oracle Access Manager, and which users need both types of access.
-
Oracle Access Manager settings:
-
Session timeout values for both Oracle E-Business Suite and Oracle Access Manager.
-
Password policy for both Oracle E-Business Suite and Oracle Identity Management.
-
Implementation Instructions
-
Identify the user population that only need local login access to Oracle E-Business Suite, and set the Applications SSO Login Types (APPS_SSO_LOCAL_LOGIN) profile accordingly for those users (see: Single Sign-On Profile Options).
-
Configure session time out values in both Oracle E-Business Suite Release 12.2 and Oracle Single Sign-On.
-
Configure password policies, as appropriate, in Oracle Directory Services and Oracle E-Business Suite.
-
Migrate existing Oracle E-Business Suite accounts to Oracle Directory Services using the Oracle E-Business Suite User Bulk Migration Tool (see: Migrating Data Between Oracle E-Business Suite and Oracle Directory Services).
-
Set Oracle E-Business Suite profile options (see: Single Sign-On Profile Options).
| Profile Option Name (Internal Name) | Recommended Value |
|---|---|
| Applications Authentication Agent (APPS_AUTH_AGENT) | Set to the location of the Oracle E-Business Suite AccessGate login page. |
| Applications SSO Type (APPS_SSO) | Set to 'SSWA w/SSO' to switch to Single Sign-On mode. |
| Self-Service Personal Home Page mode (APPLICATIONS_HOME_PAGE) | Set to the desired choice of home page. |
| Applications SSO Login Types (APPS_SSO_LOCAL_LOGIN) | At the site level, set the value to be the usage mode the majority of users will be in. Override at the user level for users who have special needs. |
| Applications Local Login URL (APPS_LOCAL_LOGIN_URL) | If using a customized local login page, set the value to be the name of the page, otherwise leave unchanged. |
| Applications SSO Auto Link User (APPS_SSO_AUTO_LINK_USER) | Set as needed. See: Single Sign-On Profile Options. |
| Applications SSO Allow Multiple Accounts (APPS_SSO_ALLOW_MULTIPLE_ACCOUNTS) | Leave unchanged. |
| Applications SSO LDAP Synchronization (APPS_SSO_LDAP_SYNC) | Leave unchanged at the site level, override at user level for users with special needs. |
| Applications Local Change Password URL (APPS_LOCAL_CHANGE_PWD_URL) | Leave unchanged unless using a customized self-service change password page to change passwords in Oracle E-Business Suite Release 12. |
| Applications SSO Change Password URL (APPS_SSO_CHANGE_PWD_URL) | Set to the absolute URL for self-service password change page in Oracle Directory Services. |
| Applications SSO Enable OID Identity Add Event (APPS_SSO_OID_IDENTITY) | Set as needed. See: Single Sign-On Profile Options. |
| Applications SSO Link Same Names (APPS_SSO_LINK_SAME_NAMES) | Indicates whether the Oracle E-Business Suite Release 12.2 instance should link a newly-created Oracle E-Business Suite user to an existing Oracle Directory Services account with the same name. |
Deployment Scenario 1: Multiple Oracle E-Business Suite Instances + Central SSO and Oracle Directory Services Instance
This section and the following three present more sophisticated deployment scenarios. The solutions given should be interpreted as guidelines or building blocks rather than definitive instructions, as all real world deployments will be unique. In the cases presented, the solutions are built upon the basic scenario discussed above, and only highlight those actions that are different from or additional to, the basic one.
Starting Point
-
Multiple new Oracle E-Business Suite environments (Release 12.0.0 and later) have been installed using Rapid Install. Other than the default seeded administrative accounts, no user accounts have been registered yet.
-
No single sign-on infrastructure in place.
Architectural Requirements
This scenario applies when a customer wants to integrate multiple new Oracle E-Business Suite Release 12.2 environments with a single Oracle Access Manager instance.
Solution Outline
-
Oracle Access Manager, Oracle E-Business Suite AccessGate, and Oracle Directory Services are needed for the integration required. All the installations of Oracle E-Business Suite Release 12.2 delegate user sign-on and authentication to Oracle Access Manager.
-
Oracle Access Manager authenticates user credentials against user entries in Oracle Directory Services. Oracle Directory Services contains every user's single sign-on account id and password (except those such as
SYSADMINthat are configured for local access only). -
Either Oracle Directory Services or one Oracle E-Business Suite Release 12.2 instance can be designated as the source of user enrollment. If Oracle Directory Services is the source, details of user accounts can be propagated to each Oracle E-Business Suite instance by using the provisioning process. If an Oracle E-Business Suite instance is the source, the provisioning process will propagate user accounts from that instance to Oracle Directory Services, and then to the other Oracle E-Business Suite instances.
-
Optional: User profile information in an Oracle E-Business Suite Release 12.2 instance can be kept synchronized with the information in Oracle Directory Services.
Solution Details
User Management Options
In this solution, the system administrator must decide which component will be the point of user enrollment and the source of truth for user information. Either Oracle Directory Services or an Oracle E-Business Suite instance can be chosen for this role.
-
Oracle Directory Services is the point of user enrollment and source of truth.
-
After a user is created in Oracle Directory Services, the user identity can be propagated to each Oracle E-Business Suite instance using the provisioning process. To accomplish this, the provisioning profile for each Oracle E-Business Suite Release 12.2 instance needs to enable the SUBSCRIPTION_ADD event from Oracle Directory Services to Oracle E-Business Suite Release 12.2.
-
Optional: The provisioning profile can also be configured such that user profile information change in Oracle Directory Services can be propagated to each Oracle E-Business Suite Release 12.2 instance. To accomplish this, the provisioning profile for each Oracle E-Business Suite Release 12.2 instance needs to enable the IDENTITY_MODIFY event from Oracle Directory Services to Oracle E-Business Suite Release 12.2.
-
-
An Oracle E-Business Suite Release 12.2 instance is designated as the point of user enrollment and source of truth (the primary instance).
-
After a user is created from the primary Oracle E-Business Suite Release 12.2 instance, the provisioning process can be used to propagate the user identity first to Oracle Directory Services, then to other Oracle E-Business Suite Release 12 instances. To accomplish this, the provisioning profile for the primary Oracle E-Business Suite Release 12.2 instance needs to enable the IDENTITY_ADD event from Oracle E-Business Suite Release 12.2 to Oracle Directory Services. The provisioning profile for the rest of the Oracle E-Business Suite Release 12.2 instances needs to enable the SUBSCRIPTION_ADD event from Oracle Directory Services to Oracle E-Business Suite Release 12.2.
-
Deployment Scenario 2: New Oracle E-Business Suite Installation + Existing Third-Party Identity Management Solution
This section presents a slightly more sophisticated deployment scenario.
Starting Point
-
Oracle E-Business Suite Release 12.2 has been newly installed using Rapid Install. Other than the default seeded Release 12.2 administrative accounts, no user accounts have been registered yet.
-
A third-party authentication mechanism is in use as a corporate single sign-on solution.
-
A third-party LDAP directory is in use as a corporate user directory.
Architectural Requirements
Need to integrate new installation of Oracle E-Business Suite Release 12.2 with existing third-party single authentication mechanisms and third-party LDAP directory infrastructure.
Solution Outline
-
Oracle Access Manager, Oracle E-Business Suite AccessGate, and Oracle Directory Services are used for integration with third-party authentication mechanisms or third-party LDAP directories.
Note: Integrating Oracle E-Business Suite directly with third-party authentication mechanisms or third-party LDAP directories is not supported.
-
Oracle E-Business Suite and Oracle Access Manager need to be set up to enable Oracle E-Business Suite delegation of authentication to Oracle Access Manager, which in turn delegates the functionality to the third-party single sign-on authentication mechanism.
The following is the Single Sign-On Chain of Trust with Third-Party Single Sign-On Solution:
Single Sign-On Chain of Trust with Third-Party Single Sign-On Solution
-
Oracle Directory Services needs to be set up to synchronize a minimal set of user attributes when integrating with a third-party LDAP directory. Refer to the Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory or Oracle Fusion Middleware Administering Oracle Unified Directory for more information about performing this integration.
-
User information from the third-party LDAP directory for all users who will access Oracle E-Business Suite using single sign-on. Oracle Directory Services also needs to be set up to provision users in Oracle Directory Services to Oracle E-Business Suite.
-
Existing users in the third-party LDAP can be bulk migrated into Oracle Directory Services, and then bulk migrated into Oracle E-Business Suite.
-
Optional: A set of user profile information in Oracle E-Business Suite can be kept synchronized with the information in the third-party LDAP directory.
End-User Experience
Single Sign-On User Experience
-
Sign on process: the sign on user experience is the same as that in the base scenario, except that the login page is served by the third-party authentication mechanism.
-
Sign out process: when a user logs out from Oracle E-Business Suite Release 12.2, Oracle Access Manager logs the user out of all registered Oracle partner applications. The user is also logged out of the third-party single sign-on solution, if the administrator has set this up in the
samplecleanupscript. -
Session timeout: the session timeout user experience is the same as that in the base scenario, except that the user will be asked to re-authenticate only when the application session, the Oracle single sign-on session and the third-party session have all become invalid.
Single Sign-On Technical Architecture
When an unauthenticated user attempts to access Oracle E-Business Suite Release 12.2, Oracle E-Business Suite Release 12.2 delegates user authentication to Oracle Access Manager, which in turn delegates to the third-party authentication mechanisms.
User Management
Oracle Directory Services and Third-Party LDAP Directories
-
Oracle Directory Services can synchronize user information with a third-party LDAP server using the synchronization process.
-
Oracle Directory Services includes tools to bulk migrate user between Oracle Directory Services and third-party LDAP server.
Additional Information: Refer to Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory or Oracle Fusion Middleware Administering Oracle Unified Directory for more information.
Strategies for User Management
At the starting point of the deployment, the third-party LDAP server is the sole user repository. For users registered there who will need to access Oracle E-Business Suite, the single sign-on solution requires them to exist in Oracle Directory Services as well as in Oracle E-Business Suite Release 12.2.
Oracle recommends retaining the third-party LDAP directory as the primary source of truth for user information. Use the Oracle Directory Services synchronization solution to migrate users from the third-party LDAP directory into Oracle Directory Services, and then use the Oracle Directory Services provisioning solution to move users into Oracle E-Business Suite.
Important: For pending users that are enabled in Oracle E-Business Suite after user creation, the IDENTITY_MODIFY event from E-Business Suite to Oracle Directory Services must be enabled.
Populating E-Business Suite with Third-Party LDAP Users
Existing users can be migrated from the third-party LDAP directory into Oracle Directory Services, and then into Oracle E-Business Suite using the bulk migration tool.
Creating New Users
System administrators can create synchronization profiles to integrate Oracle Directory Services with the third-party LDAP directory, which results in:
-
Creation of a new single sign-on account in the third-party LDAP directory automatically triggering the creation of a new single sign-on account in Oracle Directory Services.
-
Ability to specify users to be synchronized, and which attributes of the users are to be created in Oracle Directory Services.
-
Creation of a GUID attribute for each user created in Oracle Directory Services.
System administrators also create provisioning profiles to integrate Oracle E-Business Suite Release 12 with Oracle Directory Services, which results in:
-
Creation of a new account in Oracle Directory Services automatically triggering the creation of a new application account in Oracle E-Business Suite Release 12.
-
Ability to specify user attributes created in Oracle E-Business Suite.
Diagram of Using Synchronization Profiles to Integrate Oracle Directory Services with a Third-Party LDAP
Updating User Information (optional)
System administrators can configure synchronization profiles to synchronize some or all of the user attributes from the single sign-on account in the third-party LDAP directory into the single sign-on account in Oracle Directory Services when those attributes are modified.
System administrators can configure provisioning profiles to provision some or all of the user attributes from Oracle Directory Services into Oracle E-Business Suite when those attributes are modified.
Terminating and End-Dating Users
Synchronization and provisioning profiles can also be used to configure the system such that terminating a user in the third-party LDAP directory also end-dates the user in Oracle E-Business Suite.
Password Management
Password management can, if desired, remain as it was before the integration. That is, user passwords can remain in the third-party LDAP; it is not necessary to duplicate them in Oracle Directory Services. Note that Oracle E-Business Suite will not store passwords for users provisioned from Oracle Directory Services.
-
End user tasks: Most end users should use the methods provided by the third-party LDAP directory for password maintenance functions.
-
System administrator tasks: To reset single sign-on passwords, an administrator should follow the methods provided by the third-party LDAP directory.
-
Password management policies: User's password creation, modification and single sign-on login activities are subject to the third-party LDAP rules that govern how passwords are created and used.
Critical Implementation Decisions
Oracle Directory Services has a powerful and flexible set of configuration options. Most Oracle E-Business Suite system and security administrators will be able to use the default Oracle Directory Services configuration. Security administrators with advanced security requirements may choose to use alternate Oracle Directory Services configurations. For more information, refer to Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory or Oracle Fusion Middleware Administering Oracle Unified Directory.
-
Oracle E-Business Suite integration:
-
Identity management realm
-
DIT structure
-
The attribute chosen as the nickname attribute
-
-
Synchronization between Oracle Directory Services and third-party LDAP directory:
-
Identifying users who need to access Oracle E-Business Suite Release 12.2, and must therefore be synchronized from the third-party LDAP directory to Oracle Directory Services.
-
Which user attributes to synchronize from the third-party LDAP directory to Oracle Directory Services.
-
-
Provisioning between Oracle Directory Services and Oracle E-Business Suite:
-
Which attributes to provision during account creation.
-
Whether to provision user changes from Oracle Directory Services to Oracle E-Business Suite Release 12.2. If yes, which attributes to provision.
-
-
Single sign-on settings
-
Session timeouts for Oracle Access Manager, third-party single sign-on, and Oracle E-Business Suite Release 12.
-
Current third-party LDAP/single sign-on deployment information, including host, port, and administration account information.
-
Documentation from Oracle and third-party LDAP and single sign-on product vendors describing integration with Oracle Application Server 10g.
Implementation Instructions
-
Configure Oracle Access Manager to work with third-party authentication mechanism.
-
Replicate existing accounts that need to access Oracle E-Business Suite from third-party LDAP into Oracle Directory Services. Configure Oracle Directory Services and third-party LDAP synchronization process.
-
Migrate existing Oracle Directory Services users into Oracle E-Business Suite.
-
Set Oracle E-Business Suite profile options. The profile settings should be similar to that of the base scenario. Refer to Single Sign-On Profile Options for details of all relevant profile options.
Variations On This Scenario
Variation of this scenario may have some of the following characteristics:
-
Oracle E-Business Suite fresh install.
-
Existing Oracle Access Manager and Oracle Directory Services infrastructure.
-
No third-party authentication mechanism or third-party LDAP directory involved.
The major difference here is that the steps relating to third-party (non-Oracle) software can be ignored.
Deployment Scenario 3: Existing Oracle E-Business Suite Instance + Existing Third-Party Identity Management Solutions
This scenario describes a more complex deployment possibility, which may be required in some larger organizations.
Starting Point
-
Oracle E-Business Suite Release 12.2 is in use, and has existing users populated in an up-to-date FND_USER repository.
-
A third-party authentication mechanism is in use as a corporate single sign-on solution.
-
A third-party LDAP directory in use as a corporate user directory.
-
At the start of the implementation, a user may exist in both Oracle E-Business Suite Release 12.2 and the third-party LDAP directory, with either the same user name in both, or a different user name in each.
Architectural Requirements
Need to integrate existing Oracle E-Business Suite Release 12.2 with existing third-party single sign-on and user directory infrastructure.
Solution Outline
-
Oracle Access Manager, Oracle E-Business Suite AccessGate, and Oracle Directory Services are used for the integration. Oracle E-Business Suite and Oracle Access Manager need to be set up so that Oracle E-Business Suite delegates authentication to Oracle Access Manager, which in turn delegates the functionality to the third-party authentication mechanism in use.
-
Oracle Directory Services must be configured to synchronize a minimal set of information from the third-party LDAP directory for users who will access Oracle E-Business suite by using single sign-on.
-
Existing users in the third-party LDAP directory can be bulk migrated into Oracle Directory Services.
-
Existing accounts in both Oracle E-Business Suite and third-party LDAP can be linked. With proper planning, new users can be synchronized from the third-party LDAP directory into Oracle Directory Services, and then into Oracle E-Business Suite.
-
Optional: User profile information in Oracle E-Business Suite can be kept synchronized with the information in the third-party LDAP directory.
Solution Details
The single sign-on, sign-off and session timeout processes in this deployment scenario are similar to that in Scenario 2, with one significant difference during sign-on. In the case where a user already has an account in the third-party LDAP directory and an account in Oracle E-Business Suite (with the same account name or a different account name), Oracle recommends the following approach:
-
Migrate the third-party LDAP account into Oracle Directory Services through either the bulk migration tool (for existing accounts) or the synchronization process (for new accounts).
-
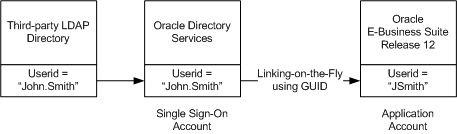
Use the Link-on-the-Fly feature to link the single sign-on account in Oracle Directory Services with the applications account in Oracle E-Business Suite Release 12.2, by proceeding as follows:
-
In the single sign-on handshake (described in the base scenario), Oracle Access Manager returns the GUID of the authenticated user to Oracle E-Business Suite.
-
Oracle E-Business Suite then uses the GUID to try to locate the user's Oracle E-Business Suite application account.
-
If it is the first time the user is accessing an Oracle E-Business Suite instance, no associated application account will be found, since the user's Oracle E-Business Suite account did not have the GUID information before the Oracle Access Manager integration took place.
-
The user is directed to a Link Account screen for entry of the Oracle E-Business Suite user name and password.
-
-
Once the application account information has been successfully verified, the user is redirected to the requested Oracle E-Business Suite page or the user's home page, as applicable. Additional logic is as follows:
-
The association between the single sign-on account and the application account (represented by the GUID) is retained.
-
Oracle E-Business Suite will not redirect the user to the Link Account page on subsequent accesses.
-
If the application account information is not verified, the user is directed back to the Link Account page.
-
-
This overall process is illustrated by the following diagram:
Deployment Scenario Flow
Advanced Option: In cases where users have accounts in both a third-party LDAP directory and Oracle E-Business Suite, it may sometimes be the case that all the LDAP account names are known to be identical to the Oracle E-Business Suite account names. In such cases, the value of the profile Applications SSO Auto Link User can be set to 'Y'. Subsequently, when Oracle E-Business Suite fails to locate an application account by GUID, it will try to locate one by the account name, and if successful it will then link the two accounts by GUID. The linking operation will be performed behind the scenes, and the user will not see the Link Account page. See Single Sign-On Profile Options for more details.
User Management Options
The complexity of user management in this scenario lies mostly in the process of reconciling existing user data in the third-party LDAP and Oracle E-Business Suite. It is always necessary to synchronize the third-party LDAP data into Oracle Directory Services for any users who need to access Oracle E-Business Suite using single sign-on. The single sign-on accounts in Oracle Directory Services should be identical to the accounts in the third-party LDAP directory. No action is required for users whose details reside in the third-party LDAP and who do not need to access Oracle E-Business Suite.
For the rest of this discussion, it is assumed that all existing third-party LDAP users will need to access Oracle E-Business Suite, and that such users will therefore need to exist in Oracle Directory Services. Depending on the characteristics of the existing data and desired functionality, there are various possibilities.
Option 1: Require users always to have created an account in the third-party LDAP directory and an account in the Oracle E-Business Suite, using the user enrollment method provided by each system.
In this case, the LDAP accounts are migrated into Oracle Directory Services. The Oracle Directory Services accounts and the Oracle E-Business Suite accounts are linked through the Link-on-the-Fly process described above (neither SUBSCRIPTION_ADD nor IDENTITY_ADD event are enabled in any provisioning profiles used).
Optionally, administrators can configure the synchronization and provisioning process so that changes in user attributes can be propagated:
-
From the third-party LDAP directory into Oracle E-Business Suite using Oracle Directory Services
-
From Oracle E-Business Suite into the third-party LDAP directory using Oracle Directory Services
-
In both directions
The list of user attributes supported is currently limited, and listed later in Supported Attributes.
Option 2: Propagate new accounts from the third-party LDAP directory to Oracle E-Business Suite by using Oracle Directory Services (as described in Scenario 2).
Existing accounts in LDAP and/or Oracle E-Business Suite will need to be reconciled. If a user has an existing account in the LDAP directory, and an existing account in Oracle E-Business Suite, the Link-on-the-Fly feature can be used to link the two accounts; no other action is required If a user has an existing account in Oracle E-Business Suite, but not in the third-party LDAP directory, an account must be created in the LDAP directory, and Link-on-the-Fly used to link the two accounts (this step needs to be performed before provisioning is configured).
If a user has an existing account in the third-party LDAP directory, but not in the Oracle E-Business Suite, an account must be created in Oracle E-Business Suite, and Link-on-the-Fly used to link the two accounts.
To eliminate the need to use the "Link Account" functionality for new users, new accounts can be propagated from the third-party LDAP directory to Oracle E-Business Suite through the Oracle Directory Services synchronization and provisioning process. This strategy also eliminates the need for new users to enroll multiple times. However, before enabling this process, system administrators must set up procedures to ensure that new account names created in the third-party LDAP directory will not conflict with any existing account names in Oracle E-Business Suite.
Optionally, administrators can configure the synchronization and provisioning process so that changes in user attributes can be propagated from the third-party LDAP directory into Oracle E-Business Suite using Oracle Directory Services.
User Management Options
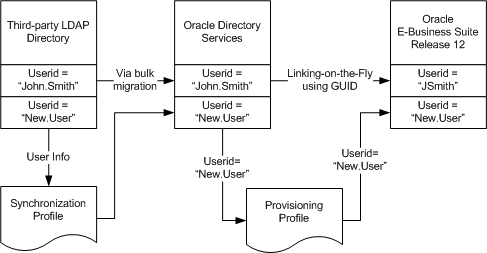
Password Management
Once a single sign-on account in Oracle Directory Services is linked to an application account in Oracle E-Business Suite, the password for the application account in Oracle E-Business Suite is, as mentioned earlier, replaced with the reserved keyword "EXTERNAL." The password stored in the primary user directory for passwords is sufficient for authentication purposes.
Note that Oracle Access Manager delegates user authentication to the third-party single sign-on solution, which in turn authenticates users against the third-party LDAP directory. Users cannot gain access to Oracle E-Business Suite through AppsLocalLogin.jsp. As Oracle Directory Services passwords will be ignored, it is not advisable to retain any passwords in Oracle Directory Services.
Note: If an SSO user's setting of APPS_SSO_LOCAL_LOGIN is changed to Local or Both (for local access), the user's password will need to be changed by an administrator.
The primary role of the third-party LDAP directory here can be represented as shown in the following diagram:
Diagram of the Role of the Third-Party LDAP Directory
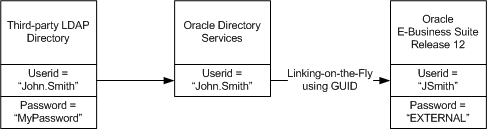
Critical Implementation Decisions
-
Oracle Directory Services has a powerful and flexible set of configuration options. Most E-Business Suite system and security administrators will be able to use the default Oracle Directory Services configuration. Security administrators with advanced security requirements may choose to use alternate Oracle Directory Services configurations. Refer to the Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory or Oracle Fusion Middleware Administering Oracle Unified Directory.
Items of particular importance to Oracle E-Business Suite integration are:
-
Identity management realm
-
DIT structure
-
The attribute chosen as the nickname attribute
-
-
Synchronization between Oracle Directory Services and third-party LDAP directory.
Items of particular importance are:
-
Identifying users who need to access Oracle E-Business Suite Release 12.2 and who therefore need to be synchronized between the third-party LDAP directory and Oracle Directory Services
-
Which attributes to use to synchronize between Oracle Directory Services and the third-party LDAP directory
-
-
Which user management option described above to use.
-
Decisions related to single sign-on settings, especially session timeouts for:
-
Oracle Access Manager
-
Third-party single sign-on components
-
Oracle E-Business Suite Release 12.2
-
-
Current third-party LDAP and single sign-on deployment information, including host, port, and administration account information. For this, you may need to refer to documentation from Oracle and third-party LDAP and single sign-on product vendors describing integration with Oracle Access Manager.
Implementation Instructions
-
Depending on the user management options, develop a strategy to reconcile existing accounts in Oracle E-Business Suite Release 12.2 and the third-party LDAP directory.
-
Configure Oracle Access Manager to work with the third-party authentication mechanism.
-
Migrate existing third-party LDAP accounts to Oracle Directory Services, and configure synchronization between third-party LDAP and Oracle Directory Services.
-
Configure session timeout setting.
-
Set Oracle E-Business Suite profile options. Refer to Single Sign-On Profile Options for further details of relevant profile options.
Variations On This Scenario
A variation of this scenario may have the following characteristics:
-
Existing Oracle E-Business Suite Release 12.2 Installation
-
Existing Oracle Access Manager and Oracle Directory Services infrastructure
-
No third-party single authentication mechanism or third-party LDAP directory involved
The major difference here is that all steps relating to third-party (non-Oracle) software can be ignored.
Deployment Scenario 4: Multiple Oracle E-Business Suite Instances with Unique User Populations
Starting Point
-
Multiple Oracle E-Business Suite Release 12.2 instances are implemented and each has an existing user population.
-
No existing Oracle Access Manager infrastructure is in place.
Architectural Requirements
This scenario applies to sites that have more than one Oracle E-Business Suite Release 12.2 instance in use, but no Oracle Access Manager infrastructure in place. The requirement is to enable Oracle Access Manager for the multiple Oracle E-Business Suite instances.
Solution Outline
-
Oracle Access Manager, Oracle E-Business Suite AccessGate, and Oracle Directory Services are used for the integration. Each Oracle E-Business Suite instance delegates user sign-on and authentication to Oracle Access Manager.
-
Oracle Access Manager authenticates user credentials against user entries in Oracle Directory Services, which contains every user's single sign-on account ID and password.
-
A single sign-on account needs to be created for every user in Oracle Directory Services. Existing applications accounts in Oracle E-Business Suite instances need to be linked to the single sign-on account.
-
Optional: User profile information in Oracle E-Business Suite can be kept synchronized with the information in Oracle Directory Services.
Solution Details
The single sign-on architecture is the same as that described in the base scenario. In addition, the Link-on-the-Fly feature described in Scenario 3 may be used.
User Management Options
The options for user management in this scenario depend on the characteristics of existing user data in the multiple Oracle E-Business Suite instances.
Option 1: If one of the Oracle E-Business Suite instances is currently serving as the source of truth for user information for all Oracle E-Business suite instances, it is possible to change this in a two-stage process. First, migrate the existing users from that Oracle E-Business Suite instance into Oracle Directory Services using the bulk migration tool, and then configure the provisioning process such that any further new users created in that Oracle E-Business Suite instance are automatically provisioned into Oracle Directory Services.
-
Users who already have accounts on the other Oracle E-Business Suite instances will use the Link-on-the-Fly mechanism to link their single sign-on accounts to their application accounts on those instances.
-
New users provisioned into Oracle Directory Services can be selectively provisioned into the other Oracle E-Business Suite instances.
Option 2: If none of the existing Oracle E-Business Suite instances is the primary source of truth for user information, it is possible to migrate the existing accounts in all Oracle E-Business Suite instances into Oracle Directory Services with the following restrictions on the existing data:
-
No two users have the same account names across all Oracle E-Business Suite instances.
-
If a user has accounts in multiple Oracle E-Business Suite instances, those accounts must be of the same account name.
After the migration, new users can be created from Oracle Directory Services, and then selectively provisioned into an Oracle E-Business suite instance.
Option 3: If the above options are not feasible, a deployment may choose not to rely on the provisioning process for creating accounts (no SUBSCRIPTION_ADD nor IDENTITY_ADD event enabled in provisioning profile). Every user who needs single sign-on access to an Oracle E-Business Suite is required to have created a single sign-on account in Oracle Directory Services, and an application account in that Oracle E-Business Suite Release 12.2 instance, by using the user enrollment method provided by each system. The Oracle Directory Services account and Oracle E-Business Suite account are linked through the Link-on-the-Fly process when the user accesses an Oracle E-Business instance for the first time.
Advanced Features
Linking Multiple Application Accounts to One Oracle Single Sign-On Account
In most cases, a user's single sign-on account in Oracle Directory Services will correspond to a single application account in Oracle E-Business Suite Release 12.2. However, there may be special cases where a user has a single sign-on account in Oracle Directory Services and multiple application accounts in Oracle E-Business Suite Release 12.2. In such a case, it is possible to associate a single sign-on account in Oracle Directory Services with multiple application accounts in Oracle E-Business Suite Release 12.2:
Diagram of an Oracle Directory Services Single Sign-On Account Associated with Multiple Application Accounts
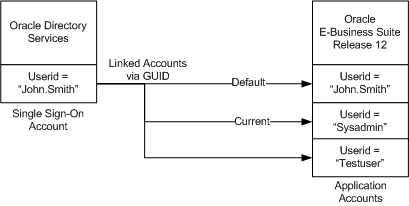
This feature can be enabled by system administrators by using a profile option (Applications SSO Allow Multiple Accounts). To utilize this feature, proceeds as follows:
-
Log in to Oracle E-Business Suite using a valid single sign-on account in Oracle Directory Services.
-
Once logged in, access the Single Sign-On Account Settings page by clicking Account Settings from the Preferences page.
-
To associate additional application accounts with an existing single sign-on account, choose Add Account and enter the new application account user name and password when prompted.
-
Verification of the new application account information will result in redirection back to the Single Sign-On Account Settings page, showing the newly linked account.
-
Failure to verify the new account information will result in redirection back to the Add Account page.
The first linked application account is marked as the default application account for the single sign-on account, and is the account the user will be logged into after Oracle single sign-on authentication. If required, the default account can be changed by making the appropriate selection on the Single Sign-On Account Settings page.
After logging into Oracle E-Business Suite using Oracle single sign-on, a user can view all currently linked application accounts using the Single Sign-On Account Settings page, and can, if desired, switch to another linked application account by selecting that account and clicking on Make Current Account. If this feature is disabled by the system administrator, the Add Account button will not appear on the Single Sign-On Account Settings page and users will not be permitted to link multiple application accounts to their single sign-on account.
Only one single sign-on account in Oracle Directory Services may be linked to a given application account in Oracle E-Business Suite Release 12.2 at a time; simultaneous linking of multiple single sign-on accounts to a single application account is not supported.
The FND_SSO_UTIL package contains procedures for linking and unlinking users. For more information, see: FND_SSO_UTIL Procedures.
Time Zone Support
Oracle Access Manager and the Oracle E-Business Suite database machine system clocks should be accurate, and kept synchronized. If the clocks are inaccurate or out-of-sync, user provisioning flows may be affected.
Be aware of the following points:
-
Oracle Access Manager converts all times to GMT. If the orclStartDate attribute is defaulted, it will pick the system date and convert it to GMT.
-
The Oracle E-Business Suite database machine runs in the local time zone, so dates are also in the local time zone.
-
When a user is provisioned from Oracle Directory Services, the dates are converted to the local time zone.
Switching User Back to Local Authentication
It may be necessary to switch the user management source of truth from Oracle Directory Services back to Oracle E-Business Suite for specific users. Credentials for these users will need to be switched back to being authenticated by FND_USER for local authentication. Special procedures to do this are necessary, because the FND User form as well as the User Preferences screen will not allow you to change the password once it has been set to "EXTERNAL."
To preserve the password and allow users to locally log in to Oracle E-Business Suite, follow these steps:
-
Ensure that the profile option Applications SSO Login Types (APPS_SSO_LOCAL_LOGIN) is set to either "LOCAL" or "BOTH" for users to whom you want to keep the local access.
-
Use the AFPASSWD utility or FNDCPASS utility to reset the user's password. The new password then needs to be emailed to the user.
For more information about the AFPASSWD and FNDCPASS utilities, refer to Basic DBA Tasks in Oracle E-Business Suite Maintenance Guide.
Recommended Nickname (Login Attribute) Setting
The default nickname used for login is "uid", which can be verified in the Oracle Directory Services Delegated Administration Service Configuration screen, Attribute for Login Name field. "uid" corresponds to User Name in the Oracle Directory Services Manager UI.
Changing the nickname attribute is generally not recommended, but other unique attributes such as email address can be used in special circumstances. Oracle E-Business Suite currently supports setting of the nickname (login attribute) to either uid or mail.
The attribute set as the nickname in Oracle Directory Services is mapped to the FND_USER.USER_NAME column in the Oracle E-Business Suite database. If the nickname is changed in Oracle Directory Services, the Oracle E-Business Suite database must be restarted to force a refresh of the cached value.
Customizing Directory Information Tree (DIT) and Relative Distinguished Name (RDN)
Customizable Directory Information Trees (DIT) and Relative Distinguished Names (RDN) are supported for use with Oracle E-Business Suite single sign-on environments. Described further in Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory and Oracle Fusion Middleware Administering Oracle Unified Directory, the following parameters can be defined at realm level:
-
Name Attribute (NickNameAttribute)
-
UserCreateBase: one or more DN where the user entries are located
-
Attribute for RDN
-
UserSearchBase: in the hierarchical path for all defined UserCreateBases, this is the location to start searching for users of a given user name
Caution: Implementing the Custom DIT feature in an existing infrastructure is not recommended, as it may result in data corruption. If there is such a need, contact Oracle Support for details of how to migrate existing data safely.
The Custom DIT feature should not be confused with Multiple Realm support.
Custom DIT Configuration Steps
The Custom DIT feature requires the following configuration steps within Oracle Directory Services, Oracle Access Manager, and Oracle E-Business Suite.
See the Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory or Oracle Fusion Middleware Administering Oracle Unified Directory for more details.
In Oracle Directory Services
-
Create the new DIT structure.
-
Optionally, configure the CommonNameAttribute to be used for the RDN (the default is cn).
-
Specify a single UserSearchBase where all UserCreateBases can be located. This can be updated using one of the following methods:
-
Using the ODSM user interface.
For example:
cn=Common,cn=Products,cn=OracleContext,dc=example,dc=comIn the "Optional Attributes" section, locate the
orclCommonUserSearchBaseattribute and add the new search base.For example:
cn=new_repository,dc=example,dc=com -
Using the
ldapmodifycommand.For example:
ldapmodify -h <host> -p <port> > -D "cn=orcladmin" -w <password> -f <full file path to ldif file>A sample ldif file is as follows:
dn:cn=Common,cn=Products,cn=OracleContext,dc=example,dc=com changetype: modify add: orclCommonUserSearchBase orclCommonUserSearchBase:cn=new_repository,dc=example,dc=com
Caution: The current implementation supports only one UserSearchBase. Using more than one may result in incorrect operation.
-
-
Add access control for the new container. For details, see My Oracle Support Knowledge Document 1311294.1, ORA-20001 and ORA-31202 When Creating a User in EBS With Custom DIT.
In Oracle Access Manager
-
Log in to the Oracle Access Manager (OAM) console.
-
Navigate to Configuration > User Identity Store > OID Identity Store (or OUD Identity Store).
-
Update the user search base with the new DIT.
In Oracle E-Business Suite
-
Register the Oracle E-Business instance with the desired deployment template. Note that this feature is only relevant for the deployments provisioning users from Oracle E-Business Suite to Oracle Directory Services.
-
From the APPS account, run the API
fnd_oid_plug.setpluginfrom SQL*Plus to configure Oracle E-Business Suite for use with the new user repository.For example:
sql> fnd_oid_plug.setPlugin(default_user_repository=>'cn=new_repository,dc=example,dc=com');
The Oracle Directory Services configuration attributes are now stored in Oracle E-Business Suite preferences.
Note: Any configuration changes in OID will require this API to be re-run so that the new values are picked up by Oracle E-Business Suite.
The preference storing the create base can be confirmed using the following query from the Oracle E-Business Suite instance:
select fnd_preference.get('#INTERNAL','OID_CONF','CREATE_BASE') from dual; -
Stop and restart the application tier processes.
-
Verify that the new users are successfully created and modified from Oracle E-Business Suite to Oracle Internet Directory or Oracle Unified Directory.
Now, when new users are created in Oracle E-Business Suite, they will also be created in the User Repository. This will have no impact to the propagation of users from Oracle Directory Services to Oracle E-Business Suite. Note, however, that the same "user" cannot be created in multiple user repositories.
If an error occurs, enable FND Logging and review the log output to get the error details. For example:
ERROR ----------------------- Unable to call fnd_ldap_wrapper.create_user due to the following reason: ORA-20001: Unabled to call fnd_ldap_wrapper.create_user due to the following reason: An unexpected error occurred. Please contact your system administrator
In FND_LOG_MESSAGES, the following error is seen:
fnd.plsql.oid.fnd_ldap_user.create_user: 4 ORA-31202: DBMS_LDAP: LDAP client/server error: Insufficient access
This error indicates that the access control was not added for this DIT.
Single Sign-On Profile Options
The logon process by which users are authorized to access Oracle E-Business Suite is significantly modified in an environment where Oracle Access Manager (and the associated Oracle E-Business Suite AccessGate) have been integrated. This section discusses the key changes, in particular the use of profile options.
Overview of Login Pages
In a standalone Oracle E-Business Suite environment, all users and system administrators connect by using Oracle E-Business Suite's AppsLogin page. This page redirects users to an Oracle E-Business Suite login page that authenticates their userid and password against the FND_USER table. Oracle E-Business Suite then determines the user's authorization by looking up the application responsibilities against entries in the FND_USER table.
In an environment where Oracle E-Business Suite has been integrated with Oracle Access Manager and Oracle Directory Services, the following points apply:
-
End users connect to Oracle E-Business Suite using the AppsLogin page, which redirects them to the Oracle Access Manager login page. Oracle Access Manager authenticates the Oracle E-Business Suite user's userid and password against Oracle Directory Services, and redirects the user back to Oracle E-Business Suite, which then determines the user's authorizations by looking up application responsibilities against entries in the Oracle E-Business Suite FND_USER table.
-
System administrators and other selected users connect to Oracle E-Business Suite using Oracle E-Business Suite's AppsLocalLogin page, which authenticates their userid and password against the FND_USER table. Oracle E-Business Suite then determines the user's authorizations by looking up application responsibilities against entries in the FND_USER table. Users in this special user population have their credentials authenticated locally in Oracle E-Business Suite instead of externally in Oracle Access Manager and Oracle Directory Services.
The login process is controlled by a group of Oracle E-Business Suite profile options, which are described in more detail below.
The key components involved in the login process are as follows.
AppsLogin
<http://[host]:[port]/OA_HTML/AppsLogin>
The login route is determined by the profile option "Applications SSO Type" (APPS_SSO). If the Oracle E-Business Suite instance is integrated with Oracle Access Manager, this should be set to "SSWA w/SSO." The user is redirected to the Oracle E-Business Suite AccessGate login page, and after entering his credentials (user name and password), he is authenticated against the LDAP server.
AppsLocalLogin
<http://[host]:[port]/OA_HTML/AppsLocalLogin.jsp>
The login route is determined by the profile option "Applications SSO Type" (APPS_SSO). If this site level profile is set to "SSWA", the user will be shown the local login page, and after entering his credentials (user name and password), he is authenticated against the Oracle E-Business Suite instance.
Note: If APPS_SSO is set to SSWA, the user will be redirected to AppsLocalLogin.jsp regardless of whether or not OAM integration is in effect. When accessing AppsLocalLogin.jsp, the APPS_SSO profile is not used to determine the page to redirect to.
About the Lightweight Login Page
Starting with Oracle E-Business Suite Release 12.2.5, a lightweight login page is provided.
The lightweight login page consists of 4 components:
-
HTML (
AppsLocalLogin.jsp): includes the CSS and Javascript elements -
login.css: formats the HTML page -
login.js: Javascript to handle the page and the credentials posting -
LoginService: to attend REST service calls related to the login page
To customize the login page style, create a file called "custom-login.css" in the same directory as the login.css file with the same owner and protection. The custom-login.css file will automatically be appended to login.css when the login page is displayed.
Note: Do not modify the AppsLocalLogin.jsp, login.css, or login.js files.
Login Page Display
The following items may be personalized. By default, all the items on the login page are displayed.
-
User Name
-
Password
-
Login button
-
Cancel button
-
Login Assistance Link
-
Register Here Link
-
Accessibility
-
Language Options
Customizing the Login Page
Oracle E-Business Suite Release 12.2.5 and Later
Suppress or Hide Elements on the Login Page
Use the profile FND_LOGIN_HIDE to enter a comma-separated list of elements to suppress or hide from the login page. Elements can be named by their DOM object ID or by the message the element displays. The ID must be preceded by the '#' or number sign.
For example, the following suppresses the display of the "Login Assistance" link and the copyright text at the bottom of the page:
FND_LOGIN_HIDE=#ForgotPasswordURL,FND_COPYRIGHT
Changing Colors and Backgrounds
Create a custom-login.css file to override attributes defined in the login.css file. Do not change the login.css or login.js files since they may be rewritten in the next patch.
For example, if you want to add an image to the disclaimer, add similar content to the custom-login.css file:
div[id="CopyrightBox"]::after { display: block; content: url('http://www.example.com/images/disclaimer.png'); }
Add/Override JavaScript
Create the file custom-login.js. This javascript file will be run when the page loads. Note that pages load asynchronously. Do not expect all HTML elements to be display at the same time.
Add/Remove/Modify HTML Elements Using JavaScript
Inside a custom-login.js file, create the function document.afterLoad=function().
For example, if you want to add a custom disclaimer message at the bottom the login page for 12.2.5, you would add the following custom-login.js:
document.afterLoad=function()
{
var e = document.getElementById(C'opyrightBox');
e.innerHTML="<p> <em style='font-size: 1.5em' >JavaScript custom Disclaimer</em> [custom-login.js]</p> ";
}
Note that this can be done only after the page load is completed.
Retain the Old Login Page from Oracle E-Business Suite Release 12.2.4
If you would like to retain the old login page from Oracle E-Business Suite Release 12.2.4 and earlier, create a copy of the old AppsLocalLogin.jps to OldAppsLogin.jsp, for example, and compile it. Then, set the profile value of APPS_LOCAL_LOGIN_URL to 'http://server:por/OA_HTML/OldAppsLogin.jsp'.
Oracle E-Business Suite Release 12.2.4 and Earlier
The login page for Oracle E-Business Suite Releases 12.2.4 and earlier is an Oracle Application Framework-based page. Administrators can personalize the page by performing the following the steps:
-
Set the profile FND_PERSONALIZATION_REGION_LINK_ENABLED to Yes.
-
Select the Functional Administrator responsibility.
-
Select the Personalization tab.
-
Enter the document path for the Local Login page definition.
-
Select a Region to customize.
-
This takes you to the Choose Personalization Context page: select Apply.
-
The personalization structure is displayed where an item can be selected and its properties changed.
Custom Login Pages
System Administrators can create custom login pages. The custom page will need to post to the servlet AuthenticateUser, which requires two attributes: user name and password. Once the user is successfully authenticated, the servlet will redirect the user to a destination defined in requestUrl or the default APPSHOMEPAGE. If the authentication fails, the servlet will redirect the user to the login page with the error message in the parameter errCode.
To deploy a custom login page:
-
Place the new servlet in the OA_HTML directory.
-
Create a new function (FND_FORM_FUNCTION) - the web_html value of this function should be populated with file name of your new login page. The function code should begin with 'APPS_LOGIN'.
-
Assign this function to the APPS_LOGIN_DEFAULT menu. As this menu is already granted to all users (including guest), the grant flag is not needed.
-
Update the profile option APPS_LOGIN_FUNCTION with new function name. The drop-down for this profile will query only function codes starting with APPS_LOGIN.
-
Set the profile APPS_LOCAL_LOGIN_URL to point to the custom login page. Ensure that the page includes:
-
The javascript file "login.js"
-
A form containing id=login with inputs for
usernameFieldandpasswordField -
A button with "onclick=submitCredentials()"
Note: Custom login pages do not necessarily have all of the same functions as the default login page (e.g., change language, translated error message display).
-
CRMLogin Servlet and jtflogin.jsp
<http://[host]:[port]/oa_servlets/CRMLogin.jsp> http://[host]:[port]/OA_HTML/jtflogin.jsp
There is a new recommended login flow for the CRM System Administrator Console. You can use the servlet CRMLogin to log in. The servlet checks whether your system is SSO-enabled, and directs you to the appropriate login page. The old login page, jtflogin.jsp, is still supported, but is only recommended in cases where jtflogin.jsp has been customized.
Oracle Applications Manager Login
http://[host]:[port]/servlets/weboam/oam/oamLogin
Important: Here, "oam" refers to Oracle Applications Manager, not Oracle Access Manager.
You will be prompted for the Oracle E-Business Suite user account and password. Log in to an account that has System Administrator and Self-Service System Administrator responsibilities. Upon successful login, the Oracle Applications Manager Console will show the Oracle E-Business Suite system to which you have connected.
Profiles and Profile Categories
The login process is determined by a group of Oracle E-Business Suite profile options, which are divided into several categories and described below. The major components involved in the logon process are as follows.
Profiles for Login and Logout
The profiles described in this category are all related to the login and logout process.
Applications SSO Type (APPS_SSO)
Features of this profile:
-
Available at site level (cannot be set for individual servers or users). As of Release 12.2.6, this may also be set at the server level.
-
Updatable only by system administrators
-
Defined by the lookup type 'APPS_SSO_TYPE'
-
Has a default value of 'SSWA'
This profile determines the overall user login and authentication experience, as follows:
| Profile Value | Login Using | Authentication | User Directory | Integration Model | Requires | Home Page |
|---|---|---|---|---|---|---|
| SSWA w/SSO | OAM login page | Oracle Access Manager | Oracle Directory Services | Oracle E-Business Suite is partner application to Oracle SSO | Oracle E-Business Suite AccessGate installed into Oracle E-Business Suite instance | Set by APPLICATIONS_HOME_PAGE profile |
| Portal w/SSO | OAM login page | Oracle Access Manager | Oracle Directory Services | Oracle E-Business Suite is a partner application to SSO | Oracle E-Business Suite AccessGate installed into Oracle E-Business Suite instance | Portal home page |
| SSWA | Oracle E-Business Suite login page | Oracle E-Business Suite | FND_USER | N/A | N/A | Set by APPLICATIONS_HOME_PAGE profile |
Additional Information: In the above table, Oracle Directory Services = the LDAP directory with which Oracle E-Business Suite is integrated; OAM = Oracle Access Manager; SSWA = Self-Service Web Applications.
Self-Service Personal Home Page Mode (APPLICATIONS_HOME_PAGE)
This profile determines the default home page for the application, which is the first page a user sees after logging into Oracle E-Business Suite.
Note: Prior to Release 12.2.9, the profile option APPLICATIONS_HOME_PAGE determines the look-and-feel of the Oracle Self-Service Applications Personal Home Page. With the change to use Masonry, the user preference set in the Settings > Preferences page takes precedence over the profile option value. The values set in this page for both home page and icon style are stored in the FND_USER_PREFERENCES table. If no value is set here, the value from the APPLICATIONS_HOME_PAGE profile option is used.
Features of this profile:
-
Available at site and user level (can be set for individual users)
-
System administrators can change setting at both Site and user levels
-
End users can change this from user level profiles
-
Default value is 'Framework only'
Note: If an end user changes the value for this profile option, that value overrides administrative-level personalization for the home page. In this case, those administrative-level personalizations will not be displayed for that user.
Features of this profile:
| Profile Value | Description |
|---|---|
| Framework Only | Displays the Home page from Release 12.2.3 and earlier, based on the value of profile option FND: Disable Configurable Home Page. |
| Framework Tree | Displays the Home page from Release 12.2.3 and earlier, based on the value of profile option FND: Disable Configurable Home Page. |
| Framework Simplified | Displays the Simple Home page from Release 12.2.4 and later. |
| None | Do not use a personal home page. |
FND: Disable Configurable Home Page
This profile accepts a value of False or True to determine whether to display the Configurable Home page with the Tree-based Navigator or Home page with the flat list Navigator, respectively, when the Self Service Personal Home Page Mode profile is set to Framework Only or Framework Tree.
Note: The combination of values set for the Self-Service Personal Home Page Mode and FND: Disable Configurable Home Page profile options affect the appearance of the home page. For details on the behavior that result from the various profile option combinations, see the "Home Page Profile Options" section of the Oracle Application Framework Developer's Guide, available from My Oracle Support Knowledge Document 1315485.1.
Applications Local Login URL (APPS_LOCAL_LOGIN_URL)
This profile specifies which login page is used to perform local access to Oracle E-Business Suite. When the 'Applications SSO type' profile is set to 'SSWA', the application login servlet (AppsLogin) will redirect a user to the login page specified by this profile.
Features of this profile:
-
Available at site level only (cannot be set for individual users)
-
Updatable only by system administrators
-
Default value is 'AppsLocalLogin.jsp'
Applications Portal (APPS_PORTAL)
This profile is used to specify Oracle Portal-related settings.
Features of this profile:
-
Available at site level only (cannot be set for individual users)
-
Updatable only by system administrators
-
Defines the portal entry page
Applications Post-Logout URL (APPS_SSO_POSTLOGOUT_HOME_URL)
This profile can be used to specify where the user should be redirected after logging out of the Oracle E-Business Suite instance. Profile changes take effect for newly created sessions only.
Features of this profile:
-
Available at site and user level
-
Default value is NULL
-
May be any valid URL
Note: Product groups may programmatically set the post-logout URL, overriding any site or user level profile settings.
Profiles for Linking Accounts
The profile options described in this category control how Oracle E-Business Suite user accounts are linked to single sign-on accounts.
Applications SSO Auto Link User (APPS_SSO_AUTO_LINK_USER)
This profile determines whether Oracle E-Business Suite Release 12.2 will automatically link an authenticated single sign-on account to an application account of the same account name, without prompting the user for authentication information for the application account during login.
Features of this profile:
-
Available at site level only (cannot be set for individual users)
-
Updatable only by system administrators
-
Has possible values of:
-
Enabled - Allow auto link
-
Disabled - Do not allow auto link (the default)
-
Create User and Link - To create and link user on-demand
-
When automatic linking is enabled for users, they must meet two criteria: have the same name as the SSO user, and a USER_GUID of null or 1. FND Users with a different name, or with a USER_GUID that is not null and not 1, cannot be linked in this way.
Note: As the user with GUID=1 cannot be linked on the fly, the only way to link this user is with APPS_SSO_AUTO_LINK_USER.
Applications SSO Link Same Names (APPS_SSO_LINK_SAME_NAMES)
This profile indicates whether the Oracle E-Business Suite Release 12.2 instance should link a newly-created Oracle E-Business Suite user to an existing Oracle Directory Services account with the same name.
-
Available at site level only (cannot be set for individual users)
-
Updatable only by system administrators
-
Has possible values of:
-
Enabled - Link users with the same user name
-
Disabled - Do not link users with the same user name
-
Applications SSO Allow Multiple Accounts (APPS_SSO_ALLOW_MULTIPLE_ACCOUNTS)
This profile indicates whether the Oracle E-Business Suite Release 12.2 instance allows linking of one Oracle Directory Services user to multiple Oracle E-Business Suite user accounts.
Features of this profile:
-
Available at site level only (cannot be set for individual users)
-
Updatable only by system administrators
-
Has possible values of:
-
'Y' - Allow multiple accounts to be linked
-
'N' - Do not allow multiple accounts to be linked (the default)
-
The Link additional account operation uses this profile, which has the following implications:
-
If the APPS_SSO_ALLOW_MULTIPLE_ACCOUNTS profile is set to 'Y' in the Single Sign-On Account Settings page (accessible from the User Preferences page), the Add Account button will be shown.
-
If the profile is set to the default value of 'N', the Add Account button will not be shown, and the Link account page will therefore not permit linking of multiple accounts.
Profiles for Password Settings
The profile options in this category specify how passwords are managed in a single sign-on Oracle E-Business Suite environment.
Applications SSO Login Types (APPS_SSO_LOCAL_LOGIN)
Features of this profile:
-
Available at both site and user level (can be set for individual users)
-
Updatable only by system administrators
-
Determines whether a user's password is managed:
-
Externally in Oracle Directory Services
-
Locally in Oracle E-Business Suite
-
In both Oracle Directory Services and Oracle E-Business Suite
-
Valid values are defined in the Lookup Type, FND_SSO_LOCAL_LOGIN:
-
SSO - Login is only allowed through single sign-on. The password is set to 'EXTERNAL' after a single sign-on account and an application account are linked.
-
LOCAL - Login is only allowed through Oracle E-Business Suite local login. Passwords must be retained in the Oracle E-Business Suite and the account cannot be linked to any Oracle Directory Services user.
-
BOTH - Login can be through both single sign-on and Oracle E-Business Suite. Since changes to the Oracle E-Business Suite password can be synchronized to Oracle Directory Services, but not vice versa, a user's single sign-on password will not necessarily be synchronized with his Oracle E-Business Suite password.
The default site level value is "BOTH". The user level value, applicable for example to the SYSADMIN and GUEST accounts, is set to "LOCAL".
The SYSADMIN and GUEST user profile options should not be changed. The SYSADMIN user is a standard account that can only be used for local login, and cannot be used to log in using single sign-on. Once a password is set to "EXTERNAL" Oracle E-Business Suite, it is no longer possible to use the original password to log in locally. For the password to be changed if the profile is updated to allow LOCAL access, the AFPASSWD utility or FNDCPASS utility will need to be run by a system administrator.
Important: Regardless of whether the user credentials are correct, a LOCAL user cannot be linked on the fly, and the linking page will display the error: FND-9921: Unable to link account. This E-Business Suite user account is marked as a local account. The user can then choose to enter a different (non-local) account to link to.
For information on using the FND_SSO_UTIL procedure to set this profile, see: FND_SSO_UTIL Procedures.
For more information about the AFPASSWD and FNDCPASS utilities, refer to the "Basic DBA Tasks" chapter of the Oracle E-Business Suite Maintenance Guide.
Applications Local Change Password URL (APPS_LOCAL_CHANGE_PWD_URL)
This profile stores the location of the page where Self-Service users can change their Oracle E-Business Suite password. The page specified should only allow the password to be changed by a user whose APPS_SSO_LOCAL_LOGIN profile has the value of either "BOTH" or "LOCAL" (that is, not "SSO").
Note: For 'SSO' and 'Both' users an API is used to determine whether the password can be changed locally, or if the APPS_SSO_CHANGE_PWD URL should be used. The criteria are whether the password can be synchronized to OID.
Features of this profile:
-
Available at site level only (cannot be set for individual users)
-
Updatable only by system administrators
-
Default value is 'AppsChangePassword.jsp'
Applications SSO Change Password URL (APPS_SSO_CHANGE_PWD_URL)
This profile points to the LDAP self-service user interface for password changes. When an Oracle E-Business Suite Self-Service change password page determines that a user's password in stored in LDAP, it can redirect the user to the location stored in this profile. For example, the password may be stored in Oracle Identity Management.
Features of this profile:
-
Available at site level only (cannot be set for individual users)
-
Updatable only by system administrators
Profiles for Provisioning Settings
The profile options in this category determine how provisioning (automatic updating of user accounts) is carried out in a single sign-on Oracle E-Business Suite environment.
Applications SSO LDAP Synchronization (APPS_SSO_LDAP_SYNC)
This profile determines whether provisioning is enabled for a particular FND_USER account. User information associated with an FND_USER account will be provisioned with Oracle Directory Services only if the APPS_SSO_LDAP_SYNC profile of the user is set to 'Y'.
Features of this profile:
-
Available at site and user level (can be set for individual users)
-
System administrators can change setting at both site and user levels
-
End users can change this from user level profiles.
-
Default site level value is 'Y'
-
User level values for
SYSADMINandGUESTaccounts are set to 'N'
The site level value is provided to obviate the need for every user to define a user level value, and has the following important characteristics:
-
Setting the site level value (to 'Y' or 'N') does not globally enable (or disable) provisioning.
-
Since provisioning with Oracle Directory Services is the most common deployment scenario, this profile is shipped with a default site level value of 'Y'.
-
For any user accounts that are not to be provisioned, this profile should be overridden with a user level value of 'N'.
-
To provision users from FND to Oracle Directory Services, APPS_SSO_LDAP_SYNC needs to be enabled and the Oracle Directory Services provisioning profile set.
-
If an existing user's APPS_SSO_LOCAL_LOGIN profile has "LOCAL" as the value, the user modifications are not provisioned, regardless of this profile value. Profile APPS_SSO_LOCAL_LOGIN has higher precedence than APPS_SSO_LDAP_SYNC at user level.
Important: Linking a single enterprise user account to multiple Oracle E-Business Suite (FND_USER) user accounts can have undesirable consequences, such as data from one application overwriting data from another. Therefore, after the first FND_USER account is linked, all accounts subsequently linked to the same enterprise account will have the APPS_SSO_LDAP_SYNC user level profile value set to 'N'. Users who still wish to change the user level value of this profile can do so by using the Single Sign-On Account Settings page.
For information on using the FND_SSO_UTIL procedure to set this profile, see: FND_SSO_UTIL Procedures.
Applications SSO Enable OID Identity Add Event (APPS_SSO_OID_IDENTITY)
This profile determines whether users created in Oracle Directory Services are automatically created in Oracle E-Business Suite and subscribed to the given Oracle E-Business Suite instance. You can enable this profile to allow the automatic subscriptions for users created in Oracle Directory Services.
Features of this profile:
-
Available at site level only (avoids the need for every user to define a user level value)
-
System administrators can change setting at site level
-
Default site level value is 'Disabled'
The default site level value of 'Disabled' means that users created in Oracle Directory Services will not be automatically created in Oracle E-Business Suite. The reason for this is that significant numbers of users from different sources may be created in Oracle Directory Services quite rapidly, and typically not all will also need to be created in Oracle E-Business Suite.
When the profile 'Applications SSO Enable OID Identity Add Event' value is set to 'Enabled', users created in Oracle Directory Services are automatically both created in Oracle E-Business Suite and subscribed to the Oracle E-Business Suite instance.
Applications SSO User Creation And Updating Allowed (APPS_SSO_USER_CREATE_UPDATE)
This profile is for Oracle internal use only.
Configuring Directory Integration Platform Provisioning Templates
This section describes how to configure an Oracle E-Business Suite Release 12.2 instance as a provisioning integrated application with Oracle Access Manager. The goal is to keep user information synchronized between Oracle Directory Services and Oracle E-Business Suite Release 12.
Configure and Create a Provisioning Profile
Bidirectional provisioning between Oracle E-Business Suite and Oracle Directory Services is built around the Oracle Directory Integration Platform, as described further in the Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory or Oracle Fusion Middleware Administering Oracle Unified Directory.
A key feature of this solution is the provisioning integration service, which enables automatic provisioning (updating between the systems) of account creation or changes of user attributes. The provisioning process between each Oracle E-Business Suite instance and Oracle Directory Services is controlled by a provisioning profile.
When changes are made in Oracle Directory Services that match an application's provisioning profile event subscription criteria, the Provisioning Integration Service is the agent that sends the relevant new data to that application. Going in the other direction, the Provisioning Integration Service filters changes coming from an application (according to the application's provisioning profile's permitted events criteria), and transmits applicable ones to Oracle Directory Services.
One of the advantages of this solution is a high level of flexibility at deployment time, i.e. the provisioning profile is highly customizable. Configuration of the profile is carried out by either using the oidprovtool, or by instantiating an LDIF template file that contains the requisite values for the particular deployment.
Profile Creation Prerequisites
Before a profile can be created, the relevant Oracle E-Business Suite instance must be registered with Oracle Directory Services. This involves creating a unique application identity for the instance in Oracle Directory Services.
Oracle E-Business Suite instances are created at the following location in the directory information tree (DIT): "cn=E-Business,cn=Products,cn=OracleContext, <Identity Management Realm>"
The created application identity (combination of dn and password) also needs to be stored in Oracle E-Business Suite. Note that the registered application identity and password can be used by the application administrator to connect to Oracle Directory Services for certain tasks, such as querying the provisioned profile details between this application instance and Oracle Directory Services.
Provisioning Profiles - Configuring Provisioning Events
CREATION, MODIFICATION, and DELETION events can be enabled or disabled individually. Four event types are currently used:
-
SUBSCRIPTION_ADD
-
IDENTITY_ADD
-
IDENTITY_MODIFY
-
IDENTITY_DELETE
Each of these is described below:
SUBSCRIPTION_ADD
This event is generated by either Oracle Directory Services or Oracle E-Business Suite Release 12.
Oracle Directory Services maintains a subscription list for each Oracle E-Business instance that has registered with Oracle Directory Services. The subscription list maintains a list of all single sign-on user accounts that need to access the associated Oracle E-Business Suite instance.
-
Oracle Directory Services and the associated Oracle E-Business Suite instance jointly maintain the accuracy of the subscription list.
-
When a single sign-on account is created in Oracle Directory Services, and subsequently added to the subscription list of an Oracle E-Business Suite instance (see Manual Subscription Management With Provsubtool for how this is done), a SUBSCRIPTION_ADD event is generated in Oracle Directory Services. If this event is enabled in the Oracle Directory Services to Oracle E-Business Suite direction, a new application account will be created and linked to the single sign-on account.
-
When Oracle Directory Services receives an IDENTITY_ADD event (see below) from an Oracle E-Business Suite instance, it adds the user to the subscription list of that Oracle E-Business Suite instance.
-
When Link-on-the-Fly is performed on an Oracle E-Business Suite Release 12 instance, the Oracle E-Business Suite instance will send a SUBSCRIPTION_ADD event to Oracle Directory Services.
-
When an IDENTITY_MODIFY (see below) event is generated in Oracle Directory Services, Oracle Directory Services will check the subscription lists of all registered Oracle E-Business Suite Release 12 instances, and only send the event to an Oracle E-Business Release 12 instance if the modified user appears on its subscription list.
IDENTITY_ADD
This event is generated by either Oracle E-Business Suite or Oracle Directory Services when a new user is created. If this event is enabled from Oracle E-Business Suite to Oracle Directory Services direction, after Oracle Directory Services receives this event, it will create an Oracle single sign-on account in Oracle Directory Services and add the account to the subscription list of that Oracle E-Business Suite Release 12 instance. The other way, if this event is enabled from Oracle Directory Services to E-Business Suite and profile Applications SSO Enable OID Identity Add Event is 'Enabled', it has the same affect as SUBSCRIPTION_ADD event generated by Oracle Directory Services.
IDENTITY_MODIFY
This event is generated by either Oracle Directory Services or Oracle E-Business Suite when a user account is modified. If this event is enabled in either direction, the receiving system will apply the modification to the account on that system.
IDENTITY_DELETE
This event is generated by Oracle Directory Services when an Oracle single sign-on account is deleted. If this event is enabled from the Oracle Directory Services to Oracle E-Business Suite direction, after an Oracle E-Business Suite Release 12 instance receives this event, it will end-date the application account linked to the Oracle single sign-on account.
Provisioning Direction
Each event can be enabled in:
-
One direction:
-
From Oracle Directory Services to Oracle E-Business Suite only
-
From Oracle E-Business Suite to Oracle Directory Services only
-
-
Both directions:
-
From Oracle Directory Services to Oracle E-Business Suite
-
From Oracle E-Business Suite to Oracle Directory Services
-
Attribute List
For each direction, and each type of event, the list of provisioned attributes can be customized as required (removing an attribute from the attribute list would disable sending that attribute). The Supported Attributes section lists the attributes that are currently supported for each direction, and also as the mapping between Oracle Directory Services attributes and application table and column names.
Polling Interval
By default, Oracle Directory Services sends out provisioning events every 60 seconds; this value can be increased or decreased by using oidprovtool, or by editing the orclodipprofileschedule attribute value in the provisioning template (see below). The polling interval should be set with caution; provisioning that is not frequent enough for site activity may have an impact on operations, while provisioning that is more frequent than necessary will result in needless network traffic.
Creating a Profile
Once the values of the configurable variables for a profile have been decided, there are two methods available to create the profile in Oracle Directory Services. The first is oidProvTool (see the Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory or Oracle Fusion Middleware Administering Oracle Unified Directory for more information). The second option is to instantiate an LDIF template, which captures the configuration choices. The instantiated templates can then be loaded into Oracle Directory Services using the ldapmodify command. The template method is described in detail below.
Creating a Profile From a Provisioning Template
Creating the provisioning profile consists of the following steps:
-
Create a suitable template based on deployment choices. The sample templates shipped can be used as examples and starting points.
-
Instantiate the template with deployment specific values, to generate an LDIF file.
-
Load the LDIF file into Oracle Directory Services.
Once the LDIF file is loaded, Oracle Directory Services will start sending and polling provisioning events to and from the Oracle E-Business Suite instance for which the profile was created. It takes the provisioning service approximately two minutes to detect that a new profile has been added or an existing one has changed. The new or updated profile is then read by the service.
Four types of provisioning are provided by the registration utility:
-
BiDirectional Provisioning: Set by specifying "-provisiontype=1" as a command line argument during Oracle Directory Services registration. This is the default provisioning type set by the registration utility.
-
InBound Provisioning: Set by specifying "-provisiontype=2" as a command line argument during Oracle Directory Services registration
-
OutBound Provisioning: Set by specifying "-provisiontype=3" as a command line argument during Oracle Directory Services registration.
-
BiDiNoCreation Provisioning: Set by specifying "-provisiontype=4" as a command line argument during Oracle Directory Services registration.
To decide on the right template to use, an Oracle E-Business Suite administrator needs to determine the direction or directions of provisioning, and which provisioning events need to be enabled in each direction. The deployment scenarios discussed in this section may be used as a reference.
For example, if the Oracle E-Business Suite instance only needs to send events to Oracle Directory Services, then an INBOUND provisioning profile should be created. If the Oracle E-Business Suite instance only needs to receive provisioning events from Oracle Directory Services, then an OUTBOUND profile should be created.
If provisioning events may need to be sent in both directions, a bidirectional profile (BOTH) should be created.
Note: Oracle recommends using the base provisioning profile templates provided with Oracle E-Business Suite. Best-efforts support will be provided for customizations to the standard provisioning profile templates. Customers may wish to engage Oracle Consulting for assistance with specific customization requirements and issues.
Administering the Provisioning Process
The monitoring and other administration tasks for the provisioning process are normally performed by Oracle Directory Services system administrators. Refer to the Oracle Internet Directory Release Administrator's Guide for more details.
Each of the following sections cover topics related to Oracle Directory Services and Oracle E-Business Suite.
Maintaining DIP Server Log Files (Oracle Directory Services)
The main DIP log file is located in the $ORACLE_HOME/ldap/log/odisrv<instance number>.log directory. The <instance number> is a unique integer id, e.g. 1, assigned by a system administrator when specifying the instance parameter as part of the oidctl command line used to start the DIP server.
The provisioning profile logs are located in the $ORACLE_HOME/ldap/odi/log directory. Each log file name is of the form: <ApplicationName>_<RealmName>_[I/E].[trc/aud].
Where:
-
I = INBOUND provisioning event (from Oracle E-Business Suite to Oracle Directory Services)
-
E = OUTBOUND provisioning event (from Oracle Directory Services to Oracle E-Business Suite)
-
.trc = Trace file, which grows until the file size is approximately 10MB. When the maximum file size is reached, the current trace file is backed up (and a timestamp appended) and a new trace file started. All old trace files are kept in the same directory.
-
.aud = Audit file, which records all the events from the time the profile was created and therefore grows continually. This file consequently needs to be archived periodically. The system administrator needs institute a policy to back up and archive audit files. This will involve temporarily disabling the profile, archiving the audit file, then re-enabling the profile. If archiving is not required, the old audit file can simply be deleted.
Additional Information: For more information, refer to the Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory or Oracle Fusion Middleware Administering Oracle Unified Directory for more details.
Enabling or Disabling a Profile (Oracle Directory Services)
To enable or disable a profile, use manageProvProfiles if the 11.1.1.9.0 stack is installed. The oidProvTool utility is to be used on previous release versions, prior to 11.1.1.9.0, although the utility is still delivered in 11.1.1.9.0 for backwards compatibility.
Refer to the Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory or Oracle Fusion Middleware Administering Oracle Unified Directory for usage of this tool.
Changing Profile Characteristics in an Existing Deployment (Oracle Directory Services)
If any properties of the provisioning profile are to be changed, the following steps must be performed.
For Oracle Internet Directory 11.1.1.9 (and Later) or Oracle Unified Directory:
-
Delete the existing profile using
manageProvProfiles. -
Use
manageProvProfilesto create a new profile that suites the current requirements.
For Oracle Internet Directory Prior to 11.1.1.9:
-
Delete the existing profile, using
oidProvTool. -
Use
oidProvToolto create a new profile that suits the current requirements.
The DIP server may take approximately two minutes to detect changes to the provisioning profile entries, that is, read the new profile configuration entry and then begin processing events based on the new configuration.
Creating Custom Workflow Subscriptions (Oracle E-Business Suite)
Customization of data synchronized between Oracle Directory Services and the Oracle E-Business Suite can be achieved by creating custom Workflow Business Event Subscriptions.
The required steps are:
-
Create the procedure that creates or updates the desired attributes. See example code below.
-
Create a new subscription for the relevant Workflow Business Event. Listed below are the Business Events provided, and how they are used:
-
oracle.apps.global.user.change - this event is raised whenever a FND_USER is updated by any source.
-
oracle.apps.fnd.identity.add - this event is raised whenever the Oracle E-Business Suite instance receives an IDENTITY_ADD event from Oracle Directory Services, such as when a new user is created in Oracle Directory Services.
-
oracle.apps.fnd.identity.modify - this event is raised whenever the Oracle E-Business Suite instance receives an IDENTITY_MODIFY event from Oracle Directory Services, such as when a user is updated in Oracle Directory Services.
-
oracle.apps.fnd.identity.delete - this event is raised whenever the Oracle E-Business Suite instance receives an IDENTITY_DELETE event from Oracle Directory Services, such as when a user is deleted from Oracle Directory Services.
-
oracle.apps.fnd.subscription.add - this event is raised whenever the Oracle E-Business Suite instance receives a SUBSCRIPTION_ADD event from Oracle Directory Services, such as when a user added to the subscription list in Oracle Directory Services.
-
oracle.apps.fnd.subscription.delete - this event is raised whenever the Oracle E-Business Suite instance receives a SUBSCRIPTION_DELETE event from Oracle Directory Services, such as when a user is deleted from the subscription list in Oracle Directory Services. Currently, this subscription does nothing in Oracle E-Business Suite. Administrators may customize this behavior by adding their own subscriptions.
-
oracle.apps.fnd.ondemand.create - this event is raised when a user is created on demand from SSO.
-
Example code for a custom Workflow subscription rule function
create or replace package custom_update_user AS
function disable_fnd_user (p_subscription_guid in raw,
p_event in out nocopy wf_event_t)
return varchar2;
end custom_update_user;
create or replace package body custom_update_user as
function disable_fnd_user (p_subscription_guid in raw,
p_event in out nocopy wf_event_t)
return varchar2 is
l_event_name varchar2(256);
l_event_key varchar2(256);
l_change_source varchar2(256);
l_change_source varchar2(256);
l_orcl_guid fnd_user.user_guid%type;
l_ent_type varchar2(256);
l_oid_user_enabled boolean;
l_end_date date;
if (p_event.GetValueForParameter('CHANGE_SOURCE') = 'OID') then
l_event_key := p_event.GetEventKey();
l_ent_type := wf_entity_mgr.get_entity_type(p_event.GetEventName());
l_orcl_guid := wf_entity_mgr.get_attribute_value(l_ent_type, l_event_key, 'ORCLGUID');
l_end_date := wf_entity_mgr.get_attribute_value(l_ent_type, l_event_key, 'ORCLACTIVEENDDATE');
if (l_end_date <= sysdate) then
fnd_user_pkg.DisableUser(username => l_event_key);
end if;
end if;
return(wf_rule.default_rule(p_subscription_guid, p_event));
exception when others
then
return(wf_rule.error_rule(p_subscription_guid, p_event));
end disable_fnd_user;
end custom_update_user;
Customizing SSO Workflow Business Events (Oracle E-Business Suite)
Oracle Directory Services provisioning events are processed in Oracle E-Business Suite using Workflow Business Events. The Workflow Business Events have subscriptions that are enabled by default and if disabled will change the default behavior. The event subscriptions that an administrator may want to disable are:
-
Event: oracle.apps.fnd.identity.add Subscription: assign_def_resp
This event subscription will add the default responsibility "Preferences" when provisioning a new user from Oracle Directory Services to Oracle E-Business Suite.
-
Event: oracle.apps.fnd.identity.add Subscription: hz_identity_add
This event subscription will create TCA records when provisioning a new user from Oracle Directory Services to Oracle E-Business Suite.
-
Event: oracle.apps.fnd.identity.modify Subscription: hz_identity_modify
This event subscription will modify TCA records when updates are made to a user in Oracle Directory Services.
Maintaining the Workflow Attribute Cache (Oracle E-Business Suite)
Data is synchronized between Oracle Directory Services and Oracle E-Business Suite using a Workflow attribute cache. The data resides in this table until manually removed by the system administrator. It is recommended that periodically the API WF_ENTITY_MGR.FLUSH_CACHE should be run to remove obsolete data. This API deletes cached records that match the specified entity information provided. When passing a specific entity_type (for example, 'USER'), the specific entity_key_value should also be passed. The special entity_type "*ALL*" will truncate the entire table.
| Name | Type | Direction | Default | Description |
|---|---|---|---|---|
| p_entity_type | varchar2 | In | Null | Entity type to be deleted, for example 'USER' |
| p_entity_key_value | varchar2 | In | Null | Entity value to be deleted, for example 'SCOTT' |
Changing E-Business Suite Database Account Password
The APPS database account password is used to register a provisioning profile in Oracle Directory Services for a specific Oracle E-Business Suite instance. If the APPS database account password for that instance is changed using the AFPASSWD utility or FNDCPASS utility, the Oracle Directory Services provisioning profile must to be updated with the new information. This can be done by running the manageProvProfiles or oidprovtool command-line utility.
For more information about the AFPASSWD and FNDCPASS utilities, refer to the Oracle E-Business Suite Maintenance Guide.
manageProvProfiles Usage
The command syntax for this tool is:
manageProvProfiles operation=modify \ ldap_host=<LDAP_HOST> \ ldap_port=<LDAP_PORT> \ ldap_user_dn=<bindDN> \ application_dn="<LDAP distinguished name of application>" \ interface_connect_info=<Oracle E-Business Suite connect info of the format, host:port:Sid:username:password>
Note: For Oracle Internet Directory, <bindDN> is cn=orcladmin. For Oracle Unified Directory, <bindDN> is cn=Directory Manager.
For example:
manageProvProfiles operation=modify \ ldap_host=infra30qa ldap_port=3060 \ ldap_user_dn="cn=orcladmin" \ application_dn="orclApplicationCommonName=ebizqa,cn=EBusiness,cn=Products,cn=OracleContext,dc=com" \ interface_connect_info=ebiz30qa:1521:ebizqa:apps:password
Example output:
orclODIPProfileName=EA3EFF8640819A51F0301990304E5D0B_EA960F743D5D7552F0301990304E34B3, cn=Provisioning Profiles, cn=Changelog Subscriber,cn=Oracle Internet Directory The Provisioning Profile for the Application has been modified.
For further details about the manageProvProfiles utility, see Oracle Fusion Middleware Administering Oracle Unified Directory or Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory.
oidprovtool Usage
Used for Oracle Internet Directory prior to 11.1.1.9, the command syntax for this tool is:
oidprovtool operation=modify \ ldap_host=<OID Server hostname> \ ldap_port=<OID Server Port> \ ldap_user_dn="cn=orcladmin" \ application_dn="<LDAP distinguished name of application>" \ interface_connect_info=<Oracle E-Business Suite connect info of the format, host:port:Sid:username:password>
For example:
oidprovtool operation=modify \ ldap_host=infra30qa ldap_port=3060 \ ldap_user_dn=cn="orcladmin" \ application_dn="orclApplicationCommonName=ebizqa,cn=EBusiness,cn=Products,cn=OracleContext,dc=com" \ interface_connect_info=ebiz30qa:1521:ebizqa:apps:password
Example output:
orclODIPProfileName=EA3EFF8640819A51F0301990304E5D0B_EA960F743D5D7552F0301990304E34B3, cn=Provisioning Profiles, cn=Changelog Subscriber,cn=Oracle Internet Directory The Provisioning Profile for the Application has been modified.
For further details about the oidprovtool utility, see the Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory.
Manual Subscription Management With Provsubtool
Provsubtool Subscription Management Tool
Depending on how your Oracle E-Business Suite Single Sign-On profile options have been configured, it may be necessary to manage subscriptions for some of your users manually.
The Oracle Directory Services provsubtool command-line utility is used to manage application-specific subscription lists in Oracle Directory Services. The tool can be used by the application administrator or the Identity Management Realm administrator (such as orcladmin).
Use the provsubtool shipped under <DIP Oracle Home>/bin on the DIP side. Ensure that ORACLE_HOME is set to the DIP home and ORACLE_HOME/bin is in the PATH before running the command.
Specific uses of this tool are to:
-
Add or remove users from application-specific subscription lists in bulk mode or batch mode.
-
Add users to the application-specific subscription lists when Applications SSO Enable OID Identity Add Event profile value is 'Disabled'. This profile controls the automatic subscription for users created in Oracle Directory Services.
-
List the memberships of a particular subscription list for an application.
-
Read from a file of a list of simple user login names (nickname attribute values) or user DNs and add or remove them from the appropriate subscription list as specified.
Command Line Parameters
| Parameter Name | Required or Optional | Default Value | Parameter Description |
|---|---|---|---|
| LDAP_HOST | Optional | Local host | LDAP server host |
| LDAP_PORT | Optional | 389 | LDAP Server port |
| APP_DN | Required | None | Application Identity DN, for example: orclapplicationcommonname=Financials,cn=EBusiness,cn=Products,cn=OracleContext,<Identity Realm> |
| APP_PWD | Required | None | Application DN password |
| REALM_DN | Required | None | DN of the identity Management Realm, for example: dc=ganseycorp,dc=com |
| LIST_NAME | Optional | ACCOUNTS | The Subscription List Name. By default, ACCOUNTS is created for Oracle E-Business Suite instances. |
| OPERATION | Required | None | ADD, REMOVE, LIST. The LIST option will list all the current members of the subscription list. |
| FILE_NAME | Optional | members.lst | File containing the user list either as simple names or DNs |
| FILE_TYPE | Optional | 0 | 0 = Simple Names 1 = DNs |
| LOG_FILE | Optional | report.log | Output log file. The output from the command is written to a file specified by the parameter "LOG_FILE." If no filename is specified, the default of report.log is used. |
| DEBUG | Optional | 0 | Debugging On/Off ( 0 or 1) |
| MAX_ERRORS | Optional | 1000 | Abort operation after this number of errors have occurred. If the numbers of errors exceed the value specified by the "MAX_ERRORS" parameter (during a bulk operation when trying to add many users together in a batch), the command will fail. |
Manually Adding and Removing Users
For an Oracle Financials E-Business Suite instance registered in Oracle Directory Services as: orclapplicationcommonname=Financials,cn=EBusiness,cn=Products,cn=OracleContext,<Identity Realm> for the ID realm: dc=ganseycorp,dc=com
To add a user whose nickname is "john.smith" to the default subscription list "ACCOUNTS," you would add the line "john.smith" (without the quotes) to an input file, in this case with the default name of members.lst, and then run the command:
provsubtool ldap_host=LDAP_HOST ldap_port=LDAP_PORT \ app_dn="orclapplicationcommonname=Financials,cn=EBusiness,\ cn=Products,cn=OracleContext,dc=ganseycorp,dc=com" \ realm_dn="dc=ganseycorp,dc=com" list_name=ACCOUNTS \ operation=ADD \ file_name=members.lst file_type=0 \ app_pwd=tea4two
To remove a user, you would follow the same procedure, simply substituting the operation REMOVE for the operation ADD:
provsubtool ldap_host=LDAP_HOST ldap_port=LDAP_PORT \ app_dn="orclapplicationcommonname=Financials,cn=EBusiness,cn=Products,cn=OracleContext,dc=ganseycorp,dc=com" \ realm_dn="dc=ganseycorp,dc=com" list_name=ACCOUNTS \ operation=REMOVE \ file_name=members.lst file_type=0 \ app_pwd=tea4two
Migrating Data Between Oracle E-Business Suite and Oracle Directory Services
The Oracle E-Business Suite Release 12.2 user migration utilities include:
-
The AppsUserExport utility, which exports existing application accounts from Oracle E-Business Suite Release 12.2 into an intermediate LDIF file. This tool is a Java program that is invoked from the command line on an Oracle E-Business Suite application tier machine.
-
The LDAPUserImport utility, which reads an LDIF file, creates new Oracle E-Business Suite application accounts as needed, and imports the data. This tool is invoked from the command line.
LDAPUserImportis provided for bulk migration of existing Oracle Directory Services accounts into Oracle E-Business Suite Release 12.2.
The following provides details of the migration process between Oracle E-Business Suite Release 12.2 and Oracle Directory Services, and the usage of these utilities.
Migrating Existing Application Accounts in Oracle E-Business Suite Release 12.2 to Oracle Directory Services
An Oracle E-Business Suite administrator can use the AppsUserExport utility to export a selected set of application accounts from the Oracle E-Business Suite native user directory (FND_USER) into an intermediate LDIF file. An Oracle Directory Services administrator then uses the Oracle Directory Services ldifmigrator tool to convert this intermediate LDIF file into a final LDIF file, based on Oracle Directory Services deployment choices. The Oracle Directory Services administrator then loads the final LDIF file into Oracle Directory Services using either the bulkload or import-ldif utility. This process is depicted in the following diagram.
Process of Migrating Existing Application Accounts in Oracle E-Business Suite Release 12.2 to Oracle Directory Services
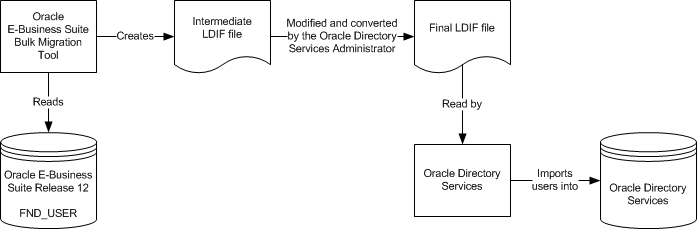
The migration process and intermediate LDIF format are explained further in Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory and Oracle Fusion Middleware Administering Oracle Unified Directory. In addition, usage of the Oracle Internet Directory Data Migration Tool (ldifmigrator) is described in Oracle Fusion Middleware Reference for Oracle Identity Management.
Note: Oracle E-Business Suite user passwords are stored as a non-reversable hash and cannot be recovered for export to Oracle Directory Services. After you implement password hashing, the AppsUserExport utility can no longer include the passwords when exporting Oracle E-Business Suite user information. For more information, see: "Using ADPASSWD to Migrate to a Password Hashing Scheme" in the Oracle E-Business Suite Maintenance Guide.
If you have an Identity Management solution configured for user password management, follow Option 1; otherwise, follow Option 2.
Option 1: Follow the instructions in this section if you use an Identity Management solution for your user password management (such as Oracle Identity Manager, Oracle Access Manager Password Management, Microsoft Active Directory, or another 3rd party LDAP for example).
-
Run the
AppsUserExportutility without the-goption. -
Follow the process to load the LDIF into Oracle Directory Services.
-
The Identity Management administrator should determine the best approach for their configuration to set the initial password of each user and communicate this to the users. This will be performed using the Identity Management solution used by your organization, which may be Oracle Identity Manager, Oracle Access Manager Password Management, Microsoft Active Directory, or another third party LDAP.
Option 2: Follow the instructions in this section if you provision users between Oracle E-Business Suite and Oracle Directory Services and do not have an Identity Management solution configured for your user password management.
Before using this option, ensure that users will be synchronized from Oracle E-Business Suite to Oracle Directory Services by setting the Oracle Directory Services provisioning profile for deployment (provisioning type 1, 2, or 4) from Oracle E-Business Suite to Oracle Directory Services and enabling the Applications SSO LDAP Synchronization (APPS_SSO_LDAP_SYNC) profile option.
-
Run the
AppsUserExportutility with the-goption. -
Follow the process to create and load the LDIF into Oracle Directory Services. When loading the LDIF file, use the
bulkloadutility. -
Expire these users' passwords using the
AFCPEXPIRE.sqlscript. -
Direct users to log in to Oracle E-Business Suite using the local login and change their passwords. Once a user's password is reset, the user should be able to log in using single sign-on.
The following focuses on application-specific tasks.
Task 1: Export Application Accounts into an Intermediate LDIF File
-
Determine which accounts to migrate
Having determined which accounts to export, the application administrator can then specify whether an account is migrated by utilizing the following profiles:
-
Applications SSO Login Types (APPS_SSO_LOCAL_LOGIN) - An account will not be migrated if the user level profile value of the account is "LOCAL", that is, the account is a local account.
-
Applications SSO LDAP Synchronization (APPS_SSO_LDAP_SYNC) - An account will not be migrated if the user level profile value of the account is "N", that is, the account is marked to not synchronize with Oracle Directory Services.
Oracle E-Business Suite ships a number of standard accounts, such as SYSADMIN and GUEST. These accounts should not be migrated. To enforce this, the
SYSADMINandGUESTaccounts are pre-seeded with Applications SSO Login Types (APPS_SSO_LOCAL_LOGIN) set to "LOCAL" and Applications SSO LDAP Synchronization (APPS_SSO_LDAP_SYNC) set to "N".Important: Accounts with user_id less than 10 can only be logged into locally, and not through single sign-on (you can check for these with the query
select user_name from FND_USER where user_id < 10). -
-
Use the AppsUserExport utility to extract user information
Use the
AppsUserExportutility to extract application user information into an intermediate LDIF file. This utility is invoked from the command line.Note: The list of attributes migrated to Oracle Directory Services from Oracle E-Business Suite is currently limited to those listed in Supported Attributes.
To invoke the
AppsUserExportutility, ensure your environment is set up correctly, and use the following syntax. Note that all parameters can if desired be entered on the same command line; they are shown here on different lines (using the UNIX '\' continuation character) for clarity.java oracle.apps.fnd.oid.AppsUserExport \ [-v] \ [-oud] \ -dbc <dbcfile> \ -o <outputfile> \ -pwd <apps schema pwd> \ -g [-l <logfile>]
where:
[-v]- Run in verbose mode[-oud]- Only required when directory server is Oracle Unified Directory<dbcfile>- Full path to the dbcfile<outputfile>- Intermediate LDIF file<apps schema pwd>- Apps schema password-g- Create and copy orclGuid users to Oracle Internet Directory, or entryUUID users to Oracle Unified Directory<logfile>- Log file (default is<outputfile>.log)Examples
For Oracle Internet Directory:
java oracle.apps.fnd.oid.AppsUserExport -v -dbc \ $FND_SECURE/myebiz.dbc -o users.txt -pwd password -g -l users.log
For Oracle Unified Directory (add option
-oudon the command line):java oracle.apps.fnd.oid.AppsUserExport -v -oud -dbc \ $FND_SECURE/myebiz.dbc -o users.txt -pwd password -g -l users.log
Warning: The resulting data file and log file may contain confidential information, such as the start and end dates for a user's account, and should therefore be secured appropriately.
Task 2: Convert the Intermediate LDIF File into a Final LDIF File
Before loading data into Oracle Directory Services by converting the intermediate LDIF file into the final LDIF file, the Oracle Directory Services administrator must ensure that:
-
The extracted data file is copied from the Oracle E-Business Suite instance to Oracle Directory Services.
-
If the provisioning profile has been set up for the Oracle E-Business Suite instance and the profile mode is either OUTBOUND or BOTH (i.e. you have enabled any provisioning events from Oracle Directory Services to Oracle E-Business Suite), the profile will need to be temporarily disabled during the migration process.
-
The LDIF file contains the appropriate orclguid and entryUUID entry. For OID, the LDIF file must contain an orclguid entry and for OUD it must contain an entryUUID entry. If a mismatch is found, revisit the previous task (Task 1: Export Application Accounts into an Intermediate LDIF File) and ensure the correct option is specified when exporting user data using the
AppsUserExportutility.
To convert the intermediate LDIF file to the final LDIF file format, an Oracle Directory Services administrator must instantiate certain variables in the intermediate LDIF file created by the AppsUserExport utility using the ldifmigrator tool. These variables are as follows:
-
s_UserContainerDN - DN of the entry under which all users are added, for example
cn=users,dc=us,dc=oracle,dc=com. -
s_UserNicknameAttribute - The nickname attribute used for user entries in the subscriber, such as uid.
-
s_UserNamingAttribute - The RDN attribute used for user entries, by default:
cnfor Oracle Internet Directory oruidfor Oracle Unified Directory
Examples
For Oracle Internet Directory
ldifmigrator "input_file=data.txt" \ "output_file=data.ldif" \ "s_UserContainerDN=cn=users,dc=us,dc=oracle,dc=com" \ "s_UserNicknameAttribute=uid" \ "s_UserNamingAttribute=cn"
For Oracle Unified Directory
ldifmigrator "input_file=data.txt" \ "output_file=data.ldif" \ "s_UserContainerDN=ou=people,dc=us,dc=oracle,dc=com" \ "s_UserNicknameAttribute=uid" \ "s_UserNamingAttribute=uid"
Important: Note that the variable names above are case sensitive.
If you encounter problems running any of the Oracle Directory Services command-line tools such as oidprovtool or ldapsearch, refer to the Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory or Oracle Fusion Middleware Administering Oracle Unified Directory for more information.
Task 3: Load the Final LDIF file into Oracle Directory Services
Once the final LDIF file has been generated, the user data is ready to be uploaded into Oracle Directory Services. Import can be done in either online or offline mode. This section describes the basic commands required in offline mode.
Additional Information: For further details, see Oracle Fusion Middleware Administering Oracle Unified Directory or Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory.
Before performing a bulk load, use the manageProvProfiles tool with operation=DISABLE to disable the profile before the migration is started (the oidProvTool tool CLI is still supported for backwards compatibility).
For example:
manageProvProfiles operation=disable \ ldap_host=testsys1.example.com \ ldap_port=3060 \ ldap_user_dn=cn=orcladmin \ application_dn="orclApplicationCommonName=beta,cn=EBusiness,cn=Products,cn=OracleContext,dc=example,dc=com" \ profile_mode=BOTH
Important: Do not add spaces after any of the commas in the application_dn parameter.
Loading the LDIF File into Oracle Internet Directory
-
Before using the
bulkloadutility to load the LDIF file, stop all Oracle Internet Directory processes running out of the Oracle Internet Directory Oracle home. -
Load the LDIF file into Oracle Internet Directory, using the steps described in the following section, Preventing Collisions in Oracle Internet Directory.
Preventing Collisions in Oracle Internet Directory
The user namespaces contained in an LDIF file that is to be bulk loaded must be unique and non-overlapping. When bulk loading users into Oracle Directory Services, the potential for collisions (duplicate users) exists. Collisions can result when integrating multiple sources into a single Oracle Directory Services instance or by performing an import more than once for the same LDIF file. As collisions can lead to numerous problems, you should follow the steps below to ensure that they do not occur:
-
Run the
bulkloadutility with thecheckandgenerateoptions to verify that there are no duplicate users. For example:bulkload connect=<connect string> check=true generate=true file=<full path to LDIF file> -
Check the log file for duplicate users.
-
If the log file indicates duplicate users, manually remove these users from the LDIF file.
-
Rerun Step 1 to verify all duplicates have been successfully removed.
-
Once all duplicates are removed, run the
bulkloadutility with the-loadoption to load the users. For example:bulkload connect=<connect string> load=true file=<full path to LDIF file>
Additional Information: For further details of the bulkload utility, see the Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory.
Instead of the bulkload utility, the ldapadd command can also be used for Oracle Internet Directory:
ldapadd -h <host> -p <port> -D "cn=orcladmin" -w <password> -f <full path to ldif file>
Note that the ldapadd command cannot be used when the LDIF file contains users with no value for the userPassword attribute.
Warning: As some operating systems also include an ldapadd executable (which will not work with Oracle Directory Services), it is advisable to specify the full path of $ORACLE_HOME/bin/ldapadd to ensure the correct one is used.
Loading the LDIF File into Oracle Unified Directory
-
In offline mode, stop the directory server:
$ORACLE_INSTANCE/OUD/bin/stop-ds
-
Using the
import-ldifutility, import the LDIF file into Oracle Unified Directory.import-ldif -b ou=people,dc=example,dc=com -l <full path to LDIF file> -n userRoot --append -R <path to rejected entries log file>
Caution: The --append or -a option must be specified in order to append the entries, otherwise all existing entries in the backend directory server will be replaced.
For further details on the import-ldif utility, see Appendix A of Oracle Fusion Middleware Administering Oracle Unified Directory.
Preventing Collisions in Oracle Unified Directory
The user namespaces contained in an LDIF file that is to be bulk loaded must be unique and non-overlapping. When bulk loading users into Oracle Directory Services, the potential for collisions (duplicate users) exists. Collisions can result when integrating multiple sources into a single Oracle Directory Service instance or by performing an import more than once for the same LDIF file. As collisions can lead to numerous problems, you should follow the steps below to ensure that they do not occur.
For Oracle Unified Directory, import-ldif can be used to avoid duplicate users. For example:
import-ldif -h localhost -port 4444 -D "cn=Directory Manager" -w password -X -l /ldif-files/example.ldif --rejectFile rejected.ldif --skipFile skipped.ldif
You can also use the ldapmodify command instead of import-ldif to avoid duplicate users:
ldapmodify -h <host> -p <port> -D "cn=Directory Manager" -w password -a -f <full path to ldif file>
For further details on the import-ldif and ldapmodify utilities, see Appendix A of Oracle Fusion Middleware Administering Oracle Unified Directory.
Importing Multiple LDIF Files
It is possible to bulk load to import multiple LDIF files. The most common scenario is one in which multiple LDIF files are generated from different Oracle E-Business Suite instances. Consolidating user information from each Oracle E-Business Suite instance into a single Oracle Directory Services can reduce the administrative overhead of managing multiple user repositories.
The user namespaces from each Oracle E-Business Suite instance's LDIF file must be unique and non-overlapping. For example, if user name "John.Brown" exists in the LDIF file to be imported from Oracle E-Business Suite instance A, it must not exist in the LDIF file to be imported from Oracle E-Business Suite instance B. If these user names do not correspond to the same user, then the user name should be updated in Oracle E-Business Suite instance B. This will both distinguish between the two users and eliminate the duplication. Otherwise, the user name must be removed from the LDIF file from instance B.
Once the LDIF file for Oracle E-Business Suite instance A has been bulk loaded into Oracle Directory Services, then the procedure should be done for the LDIF file for Oracle E-Business Suite instance B. By removing the duplicate users from the LDIF file, only the unique users from Oracle E-Business Suite instance B should bulk loaded into Oracle Directory Services. If a third Oracle E-Business Suite instance is to be bulk loaded, the same procedure should be carried out: after removing the duplicate users from the LDIF file, only the users unique to Oracle E-Business Suite instance C will be bulk loaded into Oracle Directory Services.
Final LDIF File Excerpts
The following sample is an excerpt from a final LDIF file for Oracle Internet Directory:
dn: cn=001, cn=Users,dc=example,dc=com
sn: 001
uid: 001
description: Testing OID sync
mail: 001@example.com
facsimileTelephoneNumber: 650-555-1111
orclActiveStartDate: 20181012000000z
orclIsEnabled: ENABLED
userPassword: {MD5}xxxxxxxxxxxxxxxxxxxxxx==
orclGuid: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
cn: 001
objectClass: inetOrgPerson
objectClass: orclUserV2
The following sample is an excerpt from a final LDIF file for Oracle Unified Directory:
dn: uid=001, ou=people,dc=example,dc=com
sn: 001
uid: 001
description: Testing OUD sync
mail: 001@example.com
facsimileTelephoneNumber: 650-555-1111
orclActiveStartDate: 20181012000000z
orclIsEnabled: ENABLED
userPassword: {MD5}xxxxxxxxxxxxxxxxxxxxxx==
entryUUID: xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx
cn: 001
objectClass: inetOrgPerson
objectClass: orclUserV2
Password Restrictions and Bulk Loading
-
Passwords stored in Oracle Directory Services are case-sensitive. Mixed-case passwords in Oracle E-Business Suite are migrated with the case preserved.
-
The passwords in the LDIF file are encrypted using the MD5 hashing method. If errors occur while importing the LDIF file into Oracle Directory Services, check the hashing method used by Oracle Directory Services. If is not MD5, use ODM to reset the import hashing method to MD5 and try importing the LDIF file.
-
When you export users from Oracle E-Business Suite and create an LDIF file, the passwords are encrypted and so the bulk loader cannot verify if they follow Oracle Directory Services password policy. Therefore, the password policy cannot be enforced when such users are bulk-loaded into Oracle Directory Services.
Task 4: Update lastchangenumber and Restart the Oracle Directory Services Processes
-
Start all Oracle Directory Services processes.
-
Shutdown the Oracle Directory Integration Platform (DIP) by opening the Oracle Enterprise Manager Console for the DIP domain (
http://<AdminServerhost.domain>:<AdminServer_Port>/em). In the navigation panel on the left, navigate to Identity and Access > DIP(<version>) > DIP Server > Control > Shut Down. -
Update the
lastchangenumberattribute of the profile. To do so, find the current last change number in Oracle Directory Services with theldapsearchcommand:$ORACLE_HOME/bin/ldapsearch -h <host> -p <port> -D <bindDN> \ -w <bindDN pwd> -s base -b "" "objectclass=*" \ lastchangenumber
Next, the
oidprovtoolcommand may be used to update thelastchangenumberattribute to the numbernthat was discovered in the last step. Theoidprovtoolcommand can be used with either Oracle Internet Directory or Oracle Unified Directory with the following syntax.oidprovtool operation=MODIFY \ ldap_host=<ldap_host> \ ldap_port=<ldap_port> \ ldap_user_dn=<user to connect to LDAP> \ ldap_user_password=<user password> \ application_dn=<dn of the registered app for which the profile is modified> \ orclLastAppliedChangeNumber=<n>
For example:
oidprovtool operation=MODIFY \ ldap_host=testsys1.example.com \ ldap_port=3060 \ ldap_user_dn=cn=orcladmin \ application_dn="orclApplicationCommonName=testsys1,cn=EBusiness,cn=Products,cn=OracleContext,dc=example,dc=com" \ orclLastAppliedChangeNumber=100
You can also use the
manageProvProfilescommand with the following syntax.Note: For Oracle Internet Directory and Oracle Unified Directory 12c,
oidprovtoolis no longer used and therefore themanageProvProfilescommand must be used instead.manageProvProfiles operation=MODIFY \ ldap_host=<ldap_host> \ ldap_port=<ldap_port> \ ldap_user_dn=<bindDN> \ application_dn=<dn of the registered app for which the profile is modified> \ lastchangenumber=<number>
For example:
manageProvProfiles operation=MODIFY \ ldap_host=testsys1.example.com \ ldap_port=3060 \ ldap_user_dn=cn=orcladmin \ application_dn="orclApplicationCommonName=testsys1,cn=EBusiness,cn=Products,cn=OracleContext,dc=example,dc=com" \ lastchangenumber=100
Additional Information: Reference the Oracle Fusion Middleware Administrator's Guide for Oracle Directory Integration Platform for more information.
-
Use the
manageProvProfilestool with operation=ENABLE to enable the profile.For example:
manageProvProfiles operation=enable \ ldap_host=testsys1.example.com \ ldap_port=3060 \ ldap_user_dn=cn=orcladmin \ application_dn="orclApplicationCommonName=beta,cn=EBusiness,cn=Products,cn=OracleContext,dc=example,dc=com" \ profile_mode=BOTH
-
Start up the DIP by opening the Oracle Enterprise Manager Console for the DIP domain (
http://<AdminServerhost.domain>:<AdminServer_Port>/em). In the navigation panel on the left, navigate to Identity and Access > DIP(<version>) > DIP Server > Control > Start Up.
Task 5: Create Subscriptions for Bulk Loaded Users
The bulkload utility does not automatically subscribe users to the parent Oracle E-Business Suite instance. To create the subscriptions for your bulk loaded users, run the following SQL statement on your Oracle E-Business Suite database:
select user_name from FND_USER where
FND_profile.VALUE_SPECIFIC('APPS_SSO_LOCAL_LOGIN', user_id)<>'LOCAL' and
FND_profile.VALUE_SPECIFIC('APPS_SSO_LDAP_SYNC', user_id)='Y'
You can save the results of this query in a text file using your SQL client's capabilities. See Manual Subscription Management With Provsubtool for details on how to run provsubtool to add these users to the subscription list.
Migrating Existing Accounts from Oracle Directory Services to Oracle E-Business Suite Release 12
The LDAPUserImport command-line utility takes an LDIF file generated from Oracle Directory Services, and inserts appropriate data into the Oracle E-Business Suite schema. It can be used for bulk migration of existing accounts from Oracle Directory Services to Oracle E-Business Suite. LDAPUserImport updates both FND and TCA schema.
Warning: Importing user accounts and related information into Oracle E-Business Suite is a resource-intensive operation that may take a significant amount of time, as large amounts of business events and DML statements are issued in the process.
Task 1: Export Oracle Directory Services Users into the LDIF File
For Oracle Internet Directory
The Oracle Internet Directory ldifwrite command-line utility is used to create an LDIF file that can be loaded into the Oracle E-Business Suite schema by using the LDAPUserImport command-line utility.
Syntax and usage details for ldifwrite are described in the Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory.
General syntax of the command is as follows:
ldifwrite -c <db connect string> -b <base dn> -f <LDIF file>
For example:
ldifwrite -c asdb -b "cn=Users,dc=us,dc=example,dc=com" -f output.ldif
Note: Do not modify the output file output.ldif in any way before proceeding with Task 2 below.
For Oracle Unified Directory
Oracle Unified Directory utilizes ldapsearch command-line utility to export users data. General syntax of the command is as follows:
$ORACLE_INSTANCE/OUD/bin/ldapsearch -h <host> -p <port> -D <bindDN> \ -w <bindDN pwd> -b "ou=people,dc=example,dc=com" -s sub "(objectclass=orclUserV2)" \ dn orclguid cn sn mail userpassword description facsimiletelephonenumber orclactivestartdate \ orclactiveenddate orclisenabled telephonenumber street postalcode physicaldeliveryofficename \ ou st l displayname employeenumber employeetype givenname homephone manager o uid c \ postaladdress title > export.ldif
For more information, see: Oracle Fusion Middleware Administering Oracle Unified Directory.
Task 2: Import LDAP Users into Oracle E-Business Suite Using the LDAPUserImport Utility
The LDAPUserImport utility is run from the command line using the following steps:
Note: The list of attributes migrated to the Oracle E-Business Suite from Oracle Directory Services is limited to those described later in Supported Attributes.
-
Ensure the environment is set up properly.
-
Invoke the
LDAPUserImportutility with the following syntax: Note that all parameters can be entered on the same command line; for clarity, they are shown on different lines here (using the UNIX '\' continuation character).
java oracle.apps.fnd.oid.LDAPUserImport \ [-v] \ -dbc <dbcfile> \ -f <ldiffile> \ -n <nicknameattribute> \ -b <size in integer> \ -d \ [-l <logfile>] \ [-tcaRecord <N or Y>] \ [-defresp <N or Y>]
where:
[-v] - Run in verbose mode.
<dbcfile> - Full path to the dbc file.
<ldiffile> - LDIF file.
<nicknameattribute> - Name of the attribute used as the nicknameattribute in OID.
<logfile> - Log file name. If not specified, the default is LDAPUserImport.log.
-defresp - Indicates whether to assign the default responsibility 'Preferences SSWA' to the uploaded users or not. Default is 'Y' (assign the responsibility).
For example:
java oracle.apps.fnd.oid.LDAPUserImport \ -v \ -dbc $FND_SECURE/myebiz.dbc \ -f users.ldif \ -n uid \ -l users.log
If the LDAP record already exists in the Oracle E-Business Suite instance, the following actions are taken:
-
The duplicate record is ignored.
-
The log file is updated with a reference to the duplicate record.
-
Processing continues to the next LDAP record.
Task 3: Create Subscriptions for Bulk Loaded Users
Refer to Manual Subscription Management With Provsubtool for details on how to run the provsubtool utility in order to add the bulk loaded users to the subscription list.
Enabling and Disabling Users
Enabling and disabling events for users are raised and consumed differently in Oracle Directory Services and E-Business Suite.
Oracle E-Business Suite to Oracle Directory Services
New user accounts whose start date are in the future or end date in the past are currently not provisioned from Oracle E-Business Suite to Oracle Directory Services. Such pending user accounts have a corresponding place holder record created in the Oracle Directory Services: this record is either deleted or activated once the account request has been processed.
Important: The IDENTITY_MODIFY event must be enabled in Oracle Directory Services to allow users to be enabled at the time of approval.
If an existing Oracle E-Business Suite user account is end-dated, the corresponding Oracle Directory Services account is not affected. This is because the Oracle Directory Services user may still require access to other partner applications. If no such access is needed, the relevant account will need to be disabled within Oracle Directory Services.
Oracle Directory Services to Oracle E-Business Suite
The status of an account in Oracle Directory Services is propagated to Oracle E-Business Suite as being either enabled or disabled. The application account start and end date are not updated, and users with local access to the applications should not be affected.
The default functionality can be customized by creating a Workflow subscription for the event oracle.apps.fnd.identity.modify. See Creating Custom Workflow Subscriptions for details.
User accounts deleted from the Oracle Directory Services are end-dated in Oracle E-Business Suite, in order to maintain an audit trail.
Synchronizing Oracle HRMS with Oracle Directory Services
The Oracle HR Agent can be utilized to manage Oracle Human Resources employees in Oracle Directory Services, or to create E-Business Suite accounts automatically for new employees.
Definitions and Distinctions
An Oracle E-Business Suite user is someone who needs to be able to log into Oracle E-Business Suite. That user might need to file expense reports, view payslips, or file purchase requisitions. All Oracle E-Business Suite users have userids and records in the FND_USER repository, and have associated responsibilities that govern the functions and data that they can access.
An employee is someone whose information is managed by the Human Resources module in Oracle E-Business Suite. Oracle Human Resources tracks information such as employee numbers, manager hierarchies, and other personally identifiable information like birth dates.
Not all employees are users and vice versa. For example, a retailer might use Oracle E-Business Suite's Human Resources modules to manage employee information for their cashiers, but those cashiers may not be authorized to log into Oracle E-Business Suite at all.
From an organizational standpoint, this distinction enables the HR department to manage employees and the IT department to manage Oracle E-Business Suite accounts. Following on from the example above, consider a scenario where the cashiers are permitted to view their payslips by using the Self-Service Human Resources module. In such a case, the same person would be represented both in the Human Resources module and in the FND_USER repository. For Oracle E-Business Suite environments that are not integrated with Oracle Directory Services, user records need to be individually maintained in each location.
Creating Employee Entries in Oracle Directory Services
It is possible to use the Oracle Directory Services Human Resources connector to push employee information from Oracle HR to Oracle Directory Services:
Diagram of Flow Using Oracle Directory Services Human Resources to Push Employee Information

Note: Refer to the Oracle Fusion Middleware Administrator's Guide for Oracle Directory Integration Platform for more information.
A subset of employee data can be exported from Oracle Human Resources into Oracle Directory Services. The connector includes both a prepackaged integration profile, and an Oracle Human Resources agent that handles communication with Oracle Directory Services.
The Oracle Human Resources connector can be scheduled to run at any time, configuring it to extract incremental changes from the Oracle Human Resources system.
Administrators can set and modify mapping between column names in Oracle Human Resources and attributes in Oracle Directory Services. Since it is possible to provision users from Oracle Directory Services to Oracle E-Business Suite, the following flow can be configured:
Configuration Diagram to Provision Users from Oracle Directory Services to Oracle E-Business Suite
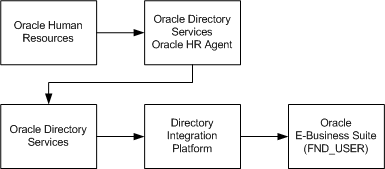
This architecture would support a business flow where a new employee is registered in E-Business Suite Human Resources by the HR department. That employee's information is then propagated using Oracle Directory Services to FND_USER, where an IT administrator grants the appropriate Oracle E-Business Suite responsibilities to the user account.
Important: The opposite direction is not supported. It is not possible to have an employee created in Oracle HR based upon a new user entry in Oracle Directory Services.
Supported Attributes
The following two tables list, respectively, the attributes that may be provisioned from Oracle Directory Services to Oracle E-Business Suite, and from Oracle E-Business Suite to Oracle Directory Services.
Note: This is a subset of the attributes listed in the provisioning templates.
| Oracle Directory Services Attribute Name | FND_USER Column Name | TCA Table and Column Names |
|---|---|---|
| UID and [nickname]* | USER_NAME | |
| DESCRIPTION | DESCRIPTION | |
| FACSIMILETELEPHONENUMBER | FAX | |
| EMAIL_ADDRESS | HZ_CONTACT_POINTS.EMAIL_ADDRESS (CONTACT_POINT_TYPE is 'EMAIL') | |
| SN | HZ_PARTIES.PERSON_LAST_NAME | |
| TELEPHONENUMBER | HZ_CONTACT_POINTS.RAW_PHONE_NUMBER (CONTACT_POINT_TYPE is 'PHONE' and CONTACT_POINT_PURPOSE is 'BUSINESS' | |
| STREET | HZ_LOCATIONS. ADDRESS1 | |
| POSTALCODE | HZ_LOCATIONS.POSTAL_CODE | |
| PHYSICALDELIVERYOFFICENAME | HZ_PARTY_SITES.MAILSTOP | |
| ST | HZ_LOCATIONS.STATE | |
| L | HZ_LOCATIONS.CITY | |
| GIVENNAME | HZ_PARTIES.PERSON_FIRST_NAME | |
| HOMEPHONE | HZ_CONTACT_POINTS.PHONE_NUMBER (CONTACT_POINT_TYPE is 'PHONE' and CONTACT_POINT_PURPOSE is 'PERSONAL') | |
| C | HZ_LOCATIONS.COUNTRY |
* Refer to Recommended Nickname (Login Attribute) Setting for more information.
| FND_USER | Oracle Directory Services |
|---|---|
| USER_NAME | UID and [nickname]* |
| DESCRIPTION | DESCRIPTION |
| EMAIL_ADDRESS | |
| FAX | FACSIMILETELEPHONENUMBER |
| END_DATE | ORCLACTIVEENDDATE |
| START_DATE | ORCLACTIVESTARTDATE |
| START_DATE/END_DATE | ORCLISENABLED |
| ENCRYPTED_USER_PASSWORD | USERPASSWORD |
* Refer to Recommended Nickname (Login Attribute) Setting for more information. Also refer to Configuring Directory Integration Platform Provisioning Templates for details of the provisioning process.
FND_SSO_UTIL Procedures
The FND_SSO_UTIL package contains procedures that provide capabilities to manage an SSO configuration.
enableLDAPIntegration
procedure enableLDAPIntegration
Used with the support of External/Internal Authentication first delivered in Release 12.2.6. This will set the preference indicating that the LDAP integration is enabled; and if the LDAP configuration is correct and complete, then provisioning will be enabled from Oracle E-Business Suite to LDAP.
disableLDAPIntegration
procedure disableLDAPIntegration
Used with the support of External/Internal Authentication delivered originally in Release 12.2.6. This will set the preference indicating that the LDAP integration is disabled and no provisioning will occur from Oracle E-Business Suite to LDAP.
deleteLDAPIntegration
procedure deleteLDAPIntegration
This API removes the value for checking if LDAP integration is enabled. Note that the LDAP registration itself is not affected.
setPasswordExternal
procedure setPasswordExternal(p_user_name_patt in varchar2, p_upd_local_user in varchar2 default 'N')
This API will make the user's password externally managed. This API should be carefully used as the user's LDAP password must be accessible in OID/OUD.
To run this procedure for a user that is defined as a local user and is linked, set p_upd_local_user to 'Y'.
setUserLocalLoginProfile
procedure setUserLocalLoginProfile(p_user_name_patt in varchar2, p_profile_value in varchar2)
This API will set the value of the profile APPS_SSO_LOCAL_LOGIN at the User level for the user or group of users to the value specified.
setUserLDAPSyncProfile
procedure setUserLDAPSyncProfile(p_user_name_patt in varchar2, p_profile_value in varchar2)
This API will set the value of the profile APPS_SSO_LDAP_SYNC at the User level for the user or group of users to the value specified: 'Y', 'N', or null (the higher level will be used).
unlink_user
procedure unlink_user(p_user_name_patt in varchar2)
This API unlinks the FND user from the LDAP user.
link_batch
procedure link_batch(cuser in userCursor)
This API links the FND user or group of users with the LDAP user if the user is not currently linked.
References and Resources for Single Sign-On
This section lists some important resources for additional information that will be needed when planning and undertaking integration of Oracle E-Business Suite into a single sign-on environment. These should be used in conjunction with the references given in the chapter.
References
See the Oracle Fusion Middleware Documentation Library for a description of:
-
Oracle Access Manager architecture and configuration
-
Oracle WebLogic Server architecture and configuration
-
The various single sign-on choices available for use with Oracle Fusion Middleware
Also see My Oracle Support Knowledge Document 1388152.1, Overview of Single Sign-On Integration Options for Oracle E-Business Suite, to find the recommended integration for your version of Oracle E-Business Suite and a reference to the detailed setup instructions and steps needed to perform this integration.
Glossary of Terms
Common Name. May include a user name.
DN
Distinguished Name The DN uniquely identifies a user in the directory. It comprises all of the individual names of the parent entries, back to the root.
DIP
Directory Integration Platform, the infrastructure that keeps user information bidirectional synchronized between Oracle Directory Services, Oracle E-Business Suite Release 12, and third-party LDAP servers.
DIT
Directory information tree. A hierarchical tree-like structure consisting of the DNs of the entries.
GUID
Global Unique Identifier, a token used to identify a user's accounts in multiple systems during the single sign-on and enterprise level user management processes.
Identity Management Realm
A collection of identities, all of which are governed by the same administrative policies. In an enterprise, all employees having access to the intranet may belong to one realm, while all external users who access the public applications of the enterprise may belong to another realm. An identity management realm is represented in the directory by a specific entry with a special object class associated with it.
LDAP
The Lightweight Directory Access Protocol is a Internet-standard protocol and schema for user directories, and has gained widespread acceptance. LDAP was conceived as a standard, extensible directory access protocol for communication between suitably configured clients and servers. As a lightweight implementation of the International Standardization Organization (ISO) X.500 standard for directory services, LDAP requires a minimal amount of networking software on the client side, which makes it particularly attractive for Internet-based, thin client applications. Currently Oracle E-Business Suite Release 12 is certified to synchronize directly with Oracle Directory Services only. However, Oracle Directory Services can itself synchronize with one or more external, third-party user directories.
Oracle Access Manager
An Oracle Fusion Middleware component that can be integrated with Oracle E-Business Suite to provide a single sign-on solution.
Oracle E-Business Suite AccessGate
A Java Enterprise Edition application that can be used as part of a single sign-on solution for Oracle E-Business Suite. AccessGate is responsible for mapping a single sign-on user to an Oracle E-Business Suite user, and creating the Oracle E-Business Suite session for that user.
Oracle Directory Services
Oracle Directory Services refers to both Oracle Internet Directory and Oracle Unified Directory. Procedures documented for implementing Oracle Directory Services apply to both these directories.
Oracle Internet Directory
Oracle Internet Directory is a general-purpose directory service runs as an application on the Oracle database and enables retrieval of information about dispersed users and network resources. It combines LDAP Version 3 with the high performance, scalability, robustness, and availability of the Oracle database. It communicates with the database (which may be on the same or on a different operating system) via Oracle Net, Oracle's operating system-independent database connectivity solution. As noted above, Oracle E-Business Suite is certified to synchronize directly with Oracle Internet Directory only, but Oracle Internet Directory can itself synchronize with one or more external, third-party user directories. For more information, see Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory.
Oracle Unified Directory
Oracle Unified Directory is a comprehensive, next generation directory service that is designed to address large deployments, to provide high performance, to be highly extensive, and to be easy to deploy, manage, and monitor. It includes an LDAP directory server used for storing data, a proxy server where the server acts as an interface between the client and the directory server that contains the data, and a replication gateway between Oracle Unified Directory and Oracle Directory Server Enterprise Edition. For more information, see Oracle Fusion Middleware Administering Oracle Unified Directory.
Nickname Attribute
The attribute used to uniquely identify a user in the entire directory. The default value for this is uid. Oracle E-Business Suite uses this to resolve a simple user name to the complete distinguished name. The user nickname attribute cannot be multi-valued--that is, a given user cannot have multiple nicknames stored under the same attribute name.
Partner Application
An application that works within the Oracle single sign-on framework. It is designed (or has been modified) to delegate responsibility for user authentication to Oracle Access Manager. Oracle E-Business Suite Release 12.2 can be deployed as a partner application.
Provisioning
Refers to the process by which user information is synchronized between Oracle Directory Services and Oracle E-Business Suite. How provisioning is set up depends both on site requirements and the configuration in use.
Provisioning Profile
Metadata that controls details of the provisioning process between Oracle Directory Services and an Oracle E-Business Suite instance. A provisioning profile is required for each application that sends or receives provisioning events to or from Oracle Directory Services.
Single Sign-On
Technology that allows a user to sign on once and gain access to multiple applications, instead of having to sign on to each application separately. In the context of Oracle E-Business Suite Release 12.2, refers to use of Oracle Access Manager to perform authentication, rather than the native FND_USER table.
Users
Individuals who have access to one or more software applications at a particular enterprise. Users are "global" entities, i.e. their existence and attributes exist outside the context of any particular software application.
User Directory
Software services that store the list of users and their attributes. Oracle E-Business Suite currently has its own proprietary user directory (the FND_USER table). There are also general purpose user directories that manage user information and expose it to integrated applications through a standard interface.
The Lightweight Directory Access Protocol (LDAP, see above for definition) is an example of a user directory.