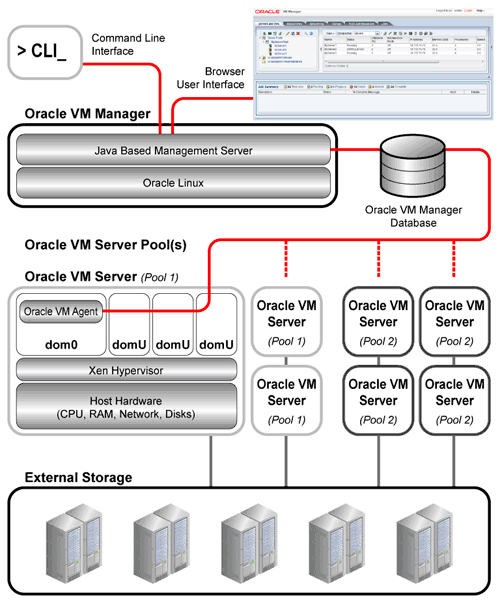
Oracle VM is a platform that provides a fully equipped environment with all the latest benefits of virtualization technology. Oracle VM enables you to deploy operating systems and application software within a supported virtualization environment.
The components of Oracle VM are shown in Figure 1.1, “Oracle VM Architecture”.
The entire configuration of your Oracle VM environment, both physical and virtual, is maintained in the Oracle VM Manager database. As of Oracle VM Release 3.2, the underlying database for demo and testing environments is a MySQL database, whereas prior releases use an Oracle XE database. Both configurations are covered in this Oracle VM Security Guide.
Oracle VM Manager: Provides the command line interface (CLI), as well as the graphical user interface (GUI). The Oracle VM CLI allows you to perform nearly the same management actions as the UI from an SSH connection. The GUI is an Application Development Framework (ADF) web application you use simply through your browser to manage Oracle VM Servers, virtual machines, and resources. Use Oracle VM Manager to:
Configure and manage Oracle VM Servers
Configure and manage networks
Configure and manage storage
Configure and manage resources such as virtual machine images, virtual machine templates, assemblies, and installation media
Create virtual machines from installation media, a virtual machine template, an assembly, or a virtual machine image
Manage virtual machines, including powering on and off, deleting, and live migrating
Import virtual machines created with Oracle VM or another solution for server virtualization
The Oracle VM Manager GUI is an Oracle WebLogic Server application running on Oracle Linux. This can be a standalone computer, or part of a virtual machine running on an instance of Oracle VM Server. However, it is recommended that Oracle VM Manager be run on a standalone computer. This guarantees dedicated resources to Oracle VM Manager, and offers the flexibility to isolate its network traffic from the true guest virtual machine networks, to prevent snooping of any unencrypted contents or denial of service.
Oracle VM Server: A managed virtualization environment providing a lightweight, secure server platform which runs virtual machines. At least one Oracle VM Server is required, but several are needed to take advantage of clustering. Oracle VM Server is based upon an updated version of the underlying Xen hypervisor technology, and includes Oracle VM Agent. It also includes a Linux kernel with support for a broad array of devices, file systems, and software RAID volume management. The Linux kernel is run as dom0 to manage one or more domU virtual machines, each of which could be Linux, Oracle Solaris, or Microsoft Windows.
External Storage: Oracle Storage Connect plugins provide access to storage. The plugins are distributed as RPM packages and deployed on the Oracle VM Servers. They are divided in two major categories: storage array plugins for any block based storage, and file system plugins for any network file system based storage. For both categories, generic plugins are included. They offer standard functionality to discover, register and use NFS storage, iSCSI or Fibre Channel SANs, and local storage. Interactive management operations, such as creating and modifying LUNs or configuring access groups on the storage hardware, are only offered by vendor-specific plugins.
For more background information about virtualization technology at Oracle, refer to Introduction to Virtualization in the Oracle VM User's Guide. For more detailed information about the architecture, concepts and deployment of Oracle VM, refer to Introduction to Oracle VM in the Oracle VM User's Guide.
The Oracle VM security architecture, by design, eliminates many security threats. The guidelines for secure deployment of virtualized solutions based on Oracle VM are largely based on network security. As these guidelines are generally applicable, they should always be reviewed for applicability in the context of each implementation and the security requirements and policies of the broader environment in which Oracle VM is deployed.
The following list describes the main aspects of the Oracle VM security architecture:
Both Oracle VM Server and Oracle VM Manager provide an Oracle Linux environment that includes an iptables firewall with a default ruleset and policies.
Oracle VM Server is a minimalist OS implementation derived from Oracle Linux and uses the Unbreakable Enterprise Kernel (UEK) Release 2 for enhanced performance and scale. By design, it has few moving parts and a minimum of network exposed services to reduce administrative effort, overhead, and attack surface.
The Oracle VM Manager XE or MySQL database is restricted to localhost connections and is not remotely accessible via port 1521. The XE or MySQL database is intended for test and development environments. Production Oracle VM environments must use Oracle Database - Standard (SE) or Enterprise (EE) Edition.
Default installations of Oracle VM Server or Oracle VM Manager do not provide physical security. They can be booted (using runlevel 1 or a rescue cd) and compromised by anyone with access to the physical console. Suitable physical security should be provided to prevent this type of exposure.
SSL is used for the network component of a VM migration.
The Oracle VM Servers' administrative connection to Oracle VM Manager uses HTTPS by default as of Oracle VM version 3.1.1 errata 1.
Openssh along with public/private key authentication are fully supported on Oracle VM Server.
802.1q VLANS are fully supported for segregating VM and dom0 network traffic.
All components of the Oracle VM installation communicate with each other in a secure way. The following table shows in detail how each individual line of communication is set up securely:
|
Communication |
Description |
|---|---|
|
Browser to Oracle VM Manager GUI |
When you log on to Oracle VM Manager, we strongly recommend that you use HTTPS and connect to TCP port 7002. SSL encrypted communication is available as of version 3.1.1, and regular HTTP connectivity at TCP/7001 is disabled by default. However, it may be enabled via Oracle WebLogic Server for testing and demo purposes. By default, two-way SSL encryption is enabled via the built-in
|
|
Oracle VM Manager GUI to Oracle VM Core |
Only local communication, meaning communication between an Oracle VM Manager GUI and Oracle VM Core running on the same server, is allowed over TCP/54321 without SSL encryption. In all other situations SSL encryption is enabled and port 54322 (TCPS) is used instead. |
|
Web Services to Oracle VM Core |
As of version 3.2.1, Oracle VM offers a web services API (WSAPI) exposed over both SOAP and REST. Local communication with Oracle VM Core occurs through TCP/54321; all non-local communication must be SSL-encrypted and uses TCPS/54322. |
|
Client to CLI |
The Oracle VM Command Line Interface (CLI) is officially supported as of version 3.2.1. The client connects to the CLI, which runs on the Oracle VM Manager host, using SSH over port TCP/10000. A public key can be set up in the SSH server in order to allow CLI users to log on automatically without having to enter credentials each time. |
|
CLI to Oracle VM Core |
The Oracle VM Command Line Interface (CLI), when running on the same host, communicates locally with Oracle VM Core through TCP/54321; all non-local communication must be SSL-encrypted and uses TCPS/54322. Note that the direct connection between CLI and Oracle VM Core will be phased out of the product. At that point, the CLI will connect to the Oracle VM Web Services API, as described below. |
|
CLI to web services |
Direct connection between CLI and Oracle VM Core will be phased out of the product. At that point, the CLI will connect to the Oracle VM Web Services API. For that communication, it is recommended that HTTPS be used over TCP/7002. Regular HTTP is possible via TCP/7001 but should be avoided for purposes other than demonstration and testing. |
|
Oracle VM Agent to Oracle VM Core |
The Oracle VM Agents running on the Oracle VM Servers use SSL encryption. They communicate with Oracle VM Core via TCP/7002 (HTTPS). |
|
Oracle VM Core to Oracle VM Agent |
Oracle VM Core, in turn, uses TCP/8899 to communicate with the Oracle VM Agents in the environment. The protocol is also HTTPS. |
|
Oracle VM Agent to Oracle VM Agent |
Communication between Oracle VM Agents is SSL-encrypted (HTTPS) and uses TCP/8899. |
|
VNC proxy |
The VNC proxy on the Oracle VM Manager host, used for connections to virtual machine consoles, listens on TCP/15901. Traffic is SSL-encrypted (TCPS). |
|
VNC Server |
The VNC server opens 1 tunnel for each remote virtual machine connection on the Oracle VM Servers. For SSL-encrypted connections, TCP ports 6900 and up (TCPS) are used. TCP ports 5900 and up can be used for unencrypted local connections. |
|
Live Migration |
Traffic related to live migration of virtual machines uses separate ports: TCP/8002 for non-encrypted and TCP/8003 for SSL-encrypted (TCPS) live migration. Secure live migration is a setting the user needs to switch on in the server pool properties as required. Based on this setting, Oracle VM Manager initiates SSL or non-SSL migration of the running virtual machine. For optimized security and performance, consider further network segregation by creating a separate network for live migration. |
|
Oracle VM Agent Certificate |
At installation, the Oracle VM Agent generates the SSL key and matching certificate. The properties are:
By default, VNC traffic, virtual machine migration traffic and Oracle VM Agent
communications are all secured using the same SSL key and certificate. The
administrator can regenerate the key/certificate combination via the Oracle VM Server
command line by means of this command: |
|
Other traffic | In an Oracle VM environment, the Oracle VM Manager host is used as the
reference for time synchronization. Consequently, UDP port 123 is used for NTP
traffic. Oracle VM Servers in a clustered server pool use an OCFS2 pool file system and require a heartbeat network function to determine the status of each cluster member. The port used for this specific type of traffic is TCP/7777. |