74 WEM Framework: Single Sign-On for Production Sites
Our SSO sample application is driven by a delivery use case. Given that ready-to-use CAS cannot be used to secure applications on production sites, we provide a simple example of how to enable single sign-on and sign-out for applications on live sites.
This chapter contains the following sections:
74.1 Deploying the SSO Sample Application
-
Unpack the
wem-sso-api-cas-sample.warfile (to the/sso-samplefolder, for example). The application is located in the WebCenter SitesMisc/Samples/WEM Samples/ WEM Sample applications/directory. -
Modify the
applicationContext.xmlfile in theWEB-INFfolder by setting the following properties:-
casUrl: Point to the CAS server base path:http://localhost:8080/cas
-
casLoginPath: Include the login form template hosted by the SSO sample application:/login?wemLoginTemplate=http%3A%2F%2Flocalhost%3A9080%2Fsso-cas-sample%2Ftemplate.html
-
-
Deploy the modified SSO sample application to your application server.
-
Access the application.
The SSO sample application consists of the following pages:
-
Protected area: a page that is protected by the WEM SSO filter. This page contains two single sign-out links (Figure 74-1).
Figure 74-1 Protected page with single sign-out links
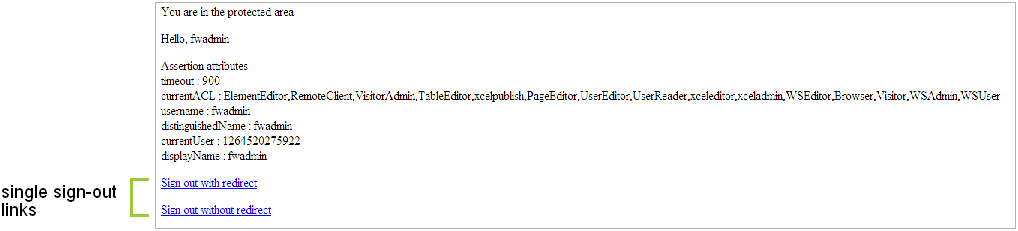
Description of "Figure 74-1 Protected page with single sign-out links"
The first link (single sign-out with redirect) is an HTML link that performs single sign-out on the CAS side and redirects the user back to the home page. The second link (single sign-out without redirect) is also an HTML link that performs single sign-out on the CAS side, but without leaving or reloading the current page.
-
Public area: a page that is excluded from the protection filter.
-
Public area with login form: this page is excluded from the protection filter, but has a login form, which allows performing a sign-in operation without leaving or reloading the current page.
Figure 74-2 Public area with "Sign in" link

Description of "Figure 74-2 Public area with "Sign in" link"
74.2 Application Structure
The SSO sample application provides you with the basic code for utilizing single sign-on and sign-out functionality to protect applications on production sites. The following components provide access to the SSO sample application:
-
index.jsp: Starting page. This page contains links to the pages described as Protected area, Public area, and Public area with login form pages (see Section 74.1, "Deploying the SSO Sample Application"). -
template.html: Used to provide a custom sign-in form for CAS. Its path is referenced in thewemLoginTemplateparameter incasLoginPathin theapplicationContext.xmlfile.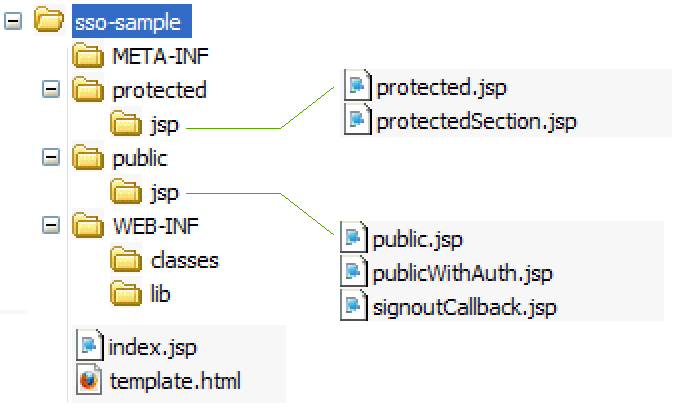
Description of the illustration samplessoapp.gif
Configuration Files: /sso-sample/WEB-INF
WEB-INF contains the following configuration files:
-
applicationContext.xml: Spring web application configuration file, which configures the SSO subsystem. -
web.xml: Web application deployment descriptor.
Protected Files: /sso-sample/protected/jsp
Files in this area are protected by the SSO filter. By default, the following files are included in this folder:
-
protected.jsp: A page protected by the SSO filter. This page hosts two links for performing single sign-out. The first link leads to the CAS sign-out page with a redirect to the application's home page when sign-out is complete. The second link embeds an iframe into this page, which calls the CAS sign-out page with a redirect to thesignoutCallback.jsppage. Theprotected.jsppage also prints out all attributes from theAssertionobject, which describes the current logged in user. -
protected/jsp/protectedSection.jsp: Page that is referenced from thepublic.jsppage, when the Sign in link is clicked in an embedded iframe. As this page is protected, a login screen is presented in the embedded iframe.
Public Files: /sso-sample/public/jsp
Files in this area are not protected by the SSO filter. By default, the following sample files are included in the /public/jsp/ folder:
-
public.jsp: This page not protected by the CAS filter -
publicWithAuth.jsp: This page displays the Sign in link. Clicking the link embeds an iframe into thepublicWithAuth.jspwith the iframe pointing to theprotectedSection.jsppage. As the page is protected, a login screen is presented in the embedded iframe. -
signoutCallback.jsp: This page is called from theprotected.jsppage upon sign-out completion when using iframe.
74.3 Implementing Single Sign-On
Implementing single sign-on for a website amounts to implementing a sign-in form. The sign-in form can be presented to site visitors in one of two ways:
-
The sign-in form is presented when the visitor tries to access a protected page. This is the default sign-in implementation. This sign in form could be either a default sign-in form shipped with CAS or a custom form provided by an application.
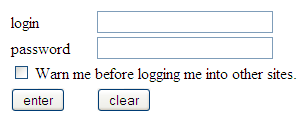
Description of the illustration sso_protectedpage.png
-
The sign-in form is embedded into a public page, and the sign-in function is performed without the user leaving the current page. This behavior can be implemented by embedding the iframe that points to a protected page. As the page is being protected, the sign-in form is presented to the visitor.

Description of the illustration m_areassigninform.png
74.4 Implementing Single Sign-Out
When implementing single sign-out on a web page, you can do one of the following:
-
Retrieve the "single sign-out" URL by invoking the following method:
getSignoutUrl() or getSignoutUrl(String callbackUrl) method of com.fatwire.wem.sso.SSO.getSSOSession() object.
After performing single sign-out, CAS can optionally redirect to the visitor-supplied URL, which is set in the callbackUrl parameter.
-
Use an iframe-embedding technique if the sign-out is to be performed without leaving the current page. This technique involves embedding an iframe with the single sign-out URL as source. When the iframe is loaded, the sign-out URL is called (this is done primarily to avoid cross-domain restrictions in browsers).