14 Managing Instant Messaging and Presence
This chapter describes how to configure and manage instant messaging and presence (IMP) for WebCenter Portal and Portal Framework applications.
Always use Fusion Middleware Control or WLST command-line tool to review and configure back-end tools and services for WebCenter Portal and Portal Framework applications. Any changes that you make to these applications, postdeployment, are stored in MDS metatdata store as customizations. See Section 1.3.5, "Oracle WebCenter Portal Configuration Considerations."
Note:
Configuration changes for instant messaging and presence, through Fusion Middleware Control or using WLST, are not dynamic, so you must restart the managed server on which WebCenter Portal or your Portal Framework application is deployed for changes to take effect. See Section 7.2, "Starting and Stopping Managed Servers for WebCenter Portal Application Deployments."
This chapter includes the following topics:
-
Section 14.1, "About Instant Messaging and Presence Connections"
-
Section 14.2, "Instant Messaging and Presence Server Prerequisites"
-
Section 14.3, "Registering Instant Messaging and Presence Servers"
-
Section 14.4, "Choosing the Active Connection for Instant Messaging and Presence"
-
Section 14.5, "Modifying Instant Messaging and Presence Connection Details"
-
Section 14.6, "Deleting Instant Messaging and Presence Connections"
-
Section 14.7, "Setting Up Instant Messaging and Presence Defaults"
-
Section 14.8, "Testing Instant Messaging and Presence Connections"
Permissions:
To perform the tasks in this chapter, you must be granted the WebLogic Server Admin role through the Oracle WebLogic Server Administration Console and the Administrator role in the deployed application:
-
WebCenter Portal:
Administratorrole granted through Portal Builder Administration. -
Portal Framework application:
Administratorrole granted through the Administration Console.
For more information about roles and permissions, see Section 1.8, "Understanding Administrative Operations, Roles, and Tools."
14.1 About Instant Messaging and Presence Connections
Instant Messaging and Presence (IMP) lets you see the presence status of other authenticated application users (online, offline, busy, or away), and it provides quick access to interaction options, such as instant messages (IM) and mail.
A single connection to a back-end presence server is required. WebCenter Portal is certified with Microsoft Office Live Communications Server (LCS) 2005, Microsoft Office Communications Server (OCS) 2007, and Microsoft Lync 2010.
Notes:
Oracle Beehive Server connections are not supported in this release.
You can register the presence server connection for your application through the Fusion Middleware Control Console or using WLST. You must mark a connection as active for IMP to work. You can register additional presence server connections, but only one connection is active at a time.
14.2 Instant Messaging and Presence Server Prerequisites
This section includes the following subsections:
-
Section 14.2.1, "Microsoft Live Communications Server (LCS) Prerequisites"
-
Section 14.2.2, "Microsoft Office Communications Server (OCS) Prerequisites"
14.2.1 Microsoft Live Communications Server (LCS) Prerequisites
This section describes the Microsoft Live Communications Server 2005 (LCS) prerequisites as the presence server for instant messaging and presence.
This section includes the following subsections:
14.2.1.1 Microsoft LCS - Installation
Refer to the Microsoft Live Communications Server 2005 documentation for installation information.
14.2.1.2 Microsoft LCS - Configuration
To use Microsoft Live Communications Server 2005 as the presence server for instant messaging and presence, you must install and configure the Microsoft RTC API v1.3, and you must install the Oracle RTC Web service for Microsoft LCS 2005.
-
To install the Microsoft RTC API v1.3, download the RTC SDK from Microsoft RTC Client API SDK 1.3, and run the installer. The installer provides the necessary installation components. If you choose the default options, the following two installers are available at
C:\Program Files\RTC Client API v1.3 SDK\INSTALLATION:-
RtcApiSetup.msi -
RtcSxSPolicies.msi
Run the
RtcApiSetup.msiinstaller first, then the side-by-side policy switcher installer (RtcSxSPolicies.msi), and restart the system. -
-
To install the Oracle RTC Web service for Microsoft Live Communications Server 2005, extract the
owc_lcs.zipfile from the Oracle Fusion Middleware companion CD. It is located in the directory/Disk1/WebCenter/services/imp/NT. The zip file contains the following:/Bin/imagesApplicationConfigurationService.asmxBlafPlus.cssExtAppLogin.aspxExtAppLogin.aspx.csGlobal.asaxLog4Net.configRTCService.asmxWeb.ConfigWebcenterTemplate.master -
Open the Internet Information Services (IIS) Manager.
-
Expand the server node and then Web Sites in the IIS Manager window.
-
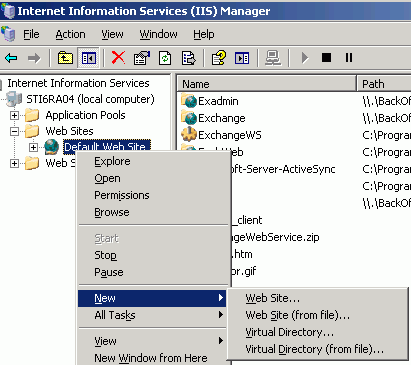
Right-click Default Web Site, select New, and then select Virtual Directory to create a site for the Oracle RTC Web service, as shown in Figure 14-1.
The Virtual Directory Creation Wizard displays.
-
Click Next.
-
Enter an alias for the virtual directory in the Alias field, for example RTC.
-
Enter the path to the directory where you extracted the
owc_lcs.zipfile. Alternatively, use the Browse button to navigate to that directory. -
Click Next.
-
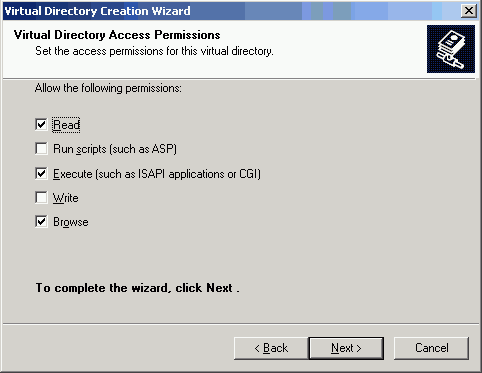
Ensure that the virtual directory has the Read, Execute, and Browse privileges. (Figure 14-2)
-
Click Next.
-
Click Finish.
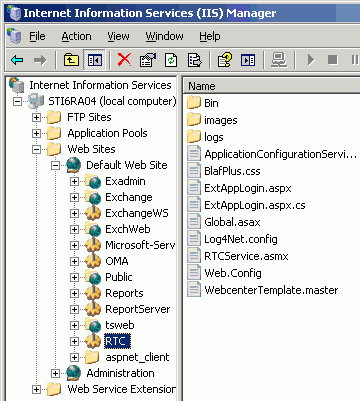
The newly created virtual directory appears under Default Web Site in the Internet Information Services (IIS) Manager window (Figure 14-3).
-
Right-click the newly created virtual directory for the Oracle RTC Web service, and then select Properties to open the Properties dialog.
-
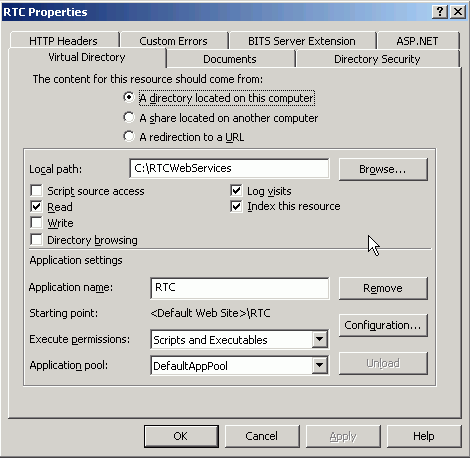
In the Virtual Directory tab, under Application settings, click Create.
Notice that the button label changes to Remove, and the name of your newly created virtual directory appears in the Application name field.
-
Select Scripts and Executables from the Execute permissions drop-down list (Figure 14-4).
-
Under the ASP.NET tab, select the ASP.NET version as 2.0 or higher from the ASP.NET version drop-down list.
Configure IIS to consume ASP.NET 2.0 applications.
-
Click OK.
-
Ensure that the LSC pool name in the LCS connection has been set.
-
Test the Web service by accessing the website using the following URL format:
http://localhost/default_website/ApplicationConfigurationService.asmx
Where
default_websiterefers to the virtual directory that you created for the Oracle RTC Web service.For example:
http://localhost/RTC/ApplicationConfigurationService.asmx
14.2.1.3 Microsoft LCS - Security Considerations
You must configure an external application for Microsoft Live Communications Server connections so that users can supply credentials to authenticate themselves on the LCS server.
With a secured application, users get presence status. With LCS, if security is required, then LCS should be on a private trusted network.
LCS provides an option for changing external credentials, which works as an alternative to using an external application. A logged-in user can click any Presence tag and select Change Credentials from the menu.
For more information, see Section 14.3.1, "Registering Instant Messaging and Presence Servers Using Fusion Middleware Control."
14.2.2 Microsoft Office Communications Server (OCS) Prerequisites
This section describes the Microsoft Office Communications Server 2007 (OCS) prerequisites as the presence server for instant messaging and presence.
This section includes the following subsections:
14.2.2.1 Microsoft OCS - Installation
Refer to the Microsoft Office Communications Server 2007 documentation for installation information.
14.2.2.2 Microsoft OCS - Configuration
This section includes the following subsections:
-
Section 14.2.2.2.4, "Provisioning WebCenter Portal's Proxy Application on OCS Server"
-
Section 14.2.2.2.7, "Installing WebCenter Portal's Proxy Application"
To use Microsoft OCS 2007 as the presence server for IMP, you must deploy WebCenter Portal's Proxy application for Microsoft OCS 2007 in one of two topologies:
-
Simple Deployment – All components reside on the same box
-
Remote Deployment – The proxy application and Microsoft OCS reside on separate boxes
14.2.2.2.1 Simple Deployment
In this topology, WebCenter Portal's Proxy application is deployed in the Internet Information Services (IIS) server hosted on the OCS box.
-
Install Microsoft Unified Communications Managed API (UCMA) 2.0 on the OCS box.
For detailed information, see Section 14.2.2.2.6, "Installing UCMA v2.0."
-
Deploy WebCenter Portal's Proxy application on the IIS server.
This proxy application provides web services for interacting with the OCS server, and for sending and receiving information. WebCenter Portal talks to these web services and presents the data.
For detailed information, see Section 14.2.2.2.7, "Installing WebCenter Portal's Proxy Application."
14.2.2.2.2 Remote Deployment
In this topology, WebCenter Portal's Proxy application is deployed on an IIS server remote to the OCS box. That is, the IIS server and the OCS server are hosted on separate machines.
Because this proxy application is hosted on a remote box, you must set up a trust between the application and the OCS server. This is known as provisioning an application. Provisioning is done through the Application Provisioner utility shipped with Microsoft UCMA v2.0. For more details, see http://msdn.microsoft.com/en-us/library/dd253360%28office.13%29.aspx.
Figure 14-5 provides an overview of the steps (including installing UCMA v2.0) to be performed on different deployment entities.
Figure 14-5 Microsoft OCS Configuration - Remote Deployment
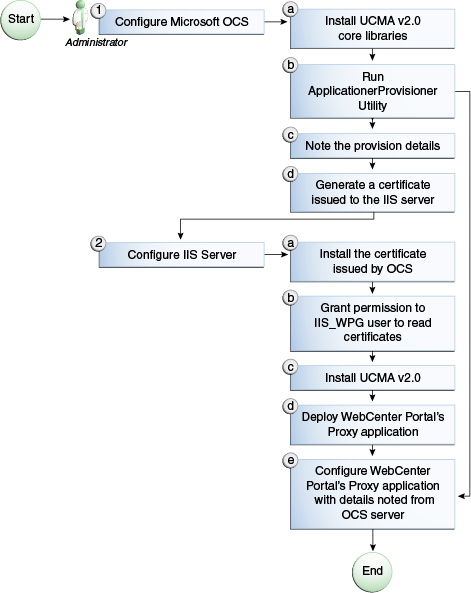
Description of "Figure 14-5 Microsoft OCS Configuration - Remote Deployment"
The details of these steps are described in the following sections.
14.2.2.2.3 Building Application Provisioner
This section lists the steps Microsoft provides for provisioning other IIS servers to access OCS.
-
Install Visual Studio 2008 on any developer box (not necessarily IIS/OCS).
-
Install UCMA version 2.0 on the same box following the steps in Section 14.2.2.2.6, "Installing UCMA v2.0."
The Application Provisioner application comes with the UCMA SDK.
-
Go to the directory
Sample Applications\Collaboration\ApplicationProvisionerunder the location where you installed UCMA Core (for example,C:\Program Files\Microsoft Office Communications Server 2007 R2\UCMA SDK 2.0\UCMACore\Sample Applications\Collaboration\ApplicationProvisioner).The directory contains the Application Provisioner application.
-
Build the application using Visual Studio 2008.
This generates the
ApplicationProvisioner.exefile. -
Copy the executable file to the OCS box.
14.2.2.2.4 Provisioning WebCenter Portal's Proxy Application on OCS Server
-
Install UCMA v2.0 core libraries on the OCS box.
Follow the same steps in Section 14.2.2.2.6, "Installing UCMA v2.0," except that after installing Visual C++ 2008 Redistributable, run
OCSCore.msi.This installs the WMI classes required to provision an application.
-
Run the
ApplicationProvisioner.exefile, generated in the previous section.The Application Provisioner dialog appears.
-
In the Application Provisioner dialog, enter
WebCenterProxyApplicationas the name of your application for the Application name, and then click Find or Create. -
In the Create Application Pool dialog, select the Office Communications Server pool for your application in the OCS Pool Fqdn list.
-
For Listening port, enter the listening port for your application (for example, 6001).
-
For Application server Fqdn, enter the fully qualified domain name (FQDN) of the computer on which the application is deployed. (This is the IIS box.)
-
If the application is deployed on two or more computers, then select the Load balanced application check box, and for Load balancer Fqdn, enter the FQDN of the load balancer.
The application pool now appears in the Application Provisioner dialog.
-
-
Double-click the server entry.
The View Server dialog appears. Note the information shown there; that is, Server FQDN, port, and GRUU.
-
Create a certificate on the OCS server with the subject name as the Server FQDN, noted in the previous step, using the Office Communications Server Certificate Wizard.
This certificate is used to authorize the requests coming from the IIS server.
-
After the certificate is created, view the certificate.
-
On the Details tab click Copy to File.
The Certificate Export Wizard appears.
-
Export the certificate with the private key to a file.
A
.pfx(Personal Information Exchange) file with the certificate name is created.
14.2.2.2.5 IIS Server Configuration
Because the IIS server hosts WebCenter Portal's Proxy application in the remote deployment scenario, use the information from the previous section to make it a trusted authority.
-
Install the certificate issued by the OCS server with the private key: Copy the .pfx file generated in step 7 under section "Provisioning WebCenter Portal's Proxy Application on OCS Server" to the IIS box, and double-click it.
The Certificate Import wizard appears.
-
Import the certificate in Personal Folder under LOCAL_MACHINE.
-
Give permission to IIS_WPG user for reading the certificate.
This is required so that the IIS server has appropriate read access on the certificate. To do this, you can use a utility provided by Microsoft called Windows HTTP Services Certificate Configuration Tool (
http://www.microsoft.com/downloads/details.aspx?familyid=c42e27ac-3409-40e9-8667-c748e422833f&displaylang=en). Download the utility and install it. This creates an executable calledwinhttpcertcfg.exe. Go to the install location and run the following command to grant permission:winhttpcertcfg.exe -g -c LOCAL_MACHINE\MY -s "<certificate-name>" -a "IIS_WPG"
-
Make an entry in
C:/WINDOWS/system32/drivers/etc/hostsfor the pool name of the OCS server as follows:<ip-address-of-ocs-box> <poolname-of-ocs-box>
For example:
10.177.252.146 pool01.example.com
-
Because the IIS server hosts WebCenter Portal's Proxy application, install Microsoft UCMA v2.0 on it.
For detailed information, see Section 14.2.2.2.6, "Installing UCMA v2.0."
-
After UCMA is installed, deploy the proxy application on the IIS server.
WebCenter Portal's Proxy application provides web services for interacting with OCS server, and for sending and receiving information. WebCenter Portal talks to these web services and presents the data.
For detailed information, see Section 14.2.2.2.7, "Installing WebCenter Portal's Proxy Application."
-
Go to the location where WebCenter Portal's Proxy application was extracted, and open
Web.configand edit theappSettingsXML node to add the values noted in Step 7 in previous section.Ensure to set value for
RemoteDeploymentto true.For example, the
appsettingsXML node should look somewhat like this.<appSettings> <add key="ApplicationName" value="WebCenterProxyApplication"/> <add key="RemoteDeployment" value="true"/> <add key="ApplicationFQDN" value="iis.server.com"/> <add key="ApplicationGRUU" value="sip:iis.server.com@EXAMPLE.COM;gruu;opaque=srvr:WebCenterProxyApplication:7mhSo94PlUK-5Q2bKPLyMAAA"/> <add key="ApplicationPort" value="6001"/> </appSettings>
The trust is established, and WebCenter Portal's Proxy application can talk to OCS.
14.2.2.2.6 Installing UCMA v2.0
Microsoft Unified Communications Managed API v2.0 (UCMA) is an endpoint API that allows advanced developers to build server applications that can interact with the OCS environment.
In a simple deployment, the UCMA is installed on the same box as OCS. In a remote deployment, the OCS core libraries are installed on the OCS box, and the UCMA is installed on the IIS (proxy) box.
-
Download UCMA v2.0 from the following location:
-
For OCS2007 R2 installation (64 bit):
http://www.microsoft.com/downloads/details.aspx?FamilyID=b20967b1-6cf5-4a4b-b7ae-622653ac929f&displaylang=enDownload and run the
UcmaSDKWebDownload.msifile. This extracts files to the folderC:\Microsoft Unified Communications Managed API 2.0 SDK Installer package\amd64.
-
-
Go to the directory (where the files from the previous step were extracted) and run
vcredist_x86.exe.This step installs run-time components of Visual C++ Libraries required for UCMA APIs.
-
Go to directory called
Setupand runUcmaRedist.msi.This step installs the UCMA 2.0 assemblies in the GAC.
14.2.2.2.7 Installing WebCenter Portal's Proxy Application
-
Extract
owc_ocs2007.zipfrom the companion CD.A directory named
OCSWebServicesis created. -
Open the Internet Information Services (IIS) Manager.
-
Expand the server node and then Web Sites in the Internet Information Services (IIS) Manager.
-
Right-click Default Web Site, select New, and then select Virtual Directory to create a site for the Oracle RTC Web service.
The Virtual Directory Creation Wizard displays.
-
Click Next.
-
Enter an alias for the virtual directory in the Alias field, for example
RTC. -
Enter the path to the directory extracted from
owc_ocs2007.zipfile.If you had extracted the zip file in C:\, then the path supplied should be C:\OCSWebServices. Alternatively, use the Browse button to navigate to that directory.
-
Click Next.
-
Ensure that the virtual directory has the Read, Execute, and Browse privileges.
-
Click Next.
-
Click Finish.
The newly created virtual directory appears under Default Web Site in the Internet Information Services (IIS) Manager window.
-
Right-click the newly created virtual directory for the Oracle RTC Web service, and then select Properties to open the Properties dialog.
-
In the Virtual Directory tab, under Application settings, click Create.
Notice that the button label changes to Remove, and the name of your newly created virtual directory appears in the Application name field.
-
Select Scripts and Executables from the Execute permissions drop-down list.
-
Under the ASP.NET tab, select the ASP.NET version as 2.0 or higher from the ASP.NET version drop-down list.
IIS should be configured to consume ASP.NET 2.0 applications.
-
Click OK.
-
Test the Web service by accessing the Web site using the following URL format:
http://localhost/default_website/OCSWebService.asmx.where
default_websiteis the virtual directory you created for the Oracle RTC Web serviceFor example:
http://localhost/RTC/OCSWebService.asmx
14.2.2.3 Microsoft OCS - Security Considerations
You must configure an external application for Microsoft Office Communications Server connections so that users can supply credentials to authenticate themselves on the OCS server.
With a secured application, users get presence status. With OCS, if security is required, then OCS should be on a private trusted network.
OCS provides an option for changing external credentials, which works as an alternative to using an external application. A logged-in user can click any Presence tag and select Change Credentials from the menu.
For more information, see Section 14.3.1, "Registering Instant Messaging and Presence Servers Using Fusion Middleware Control."
14.2.3 Microsoft Lync Prerequisites
This section describes the Microsoft Lync 2010 prerequisites as the presence server for instant messaging and presence.
This section includes the following subsections:
14.2.3.1 Microsoft Lync - Installation
Refer to the Microsoft Lync 2010 documentation for installation information.
14.2.3.2 Microsoft Lync - Configuration
This section includes the following subsections:
-
Section 14.2.3.2.4, "Provisioning WebCenter Portal's Proxy Application on Lync Server"
-
Section 14.2.3.2.6, "Migrating Trusted Service Entries Using Topology Builder or PowerShell Cmdlets"
-
Section 14.2.3.2.9, "Installing WebCenter Portal's Proxy Application"
Configuration for Microsoft Lync is similar to configuration for Microsoft OCS.
To use Microsoft Lync 2010 as the presence server for IMP, you must deploy WebCenter Portal's Proxy application for Microsoft Lync 2010 in one of two topologies:
-
Simple Deployment – All components reside on the same box
-
Remote Deployment – The proxy application and Microsoft Lync reside on separate boxes
14.2.3.2.1 Simple Deployment
In this topology, WebCenter Portal's Proxy application is deployed in the Internet Information Services (IIS) server hosted on the Lync box.
-
Install Microsoft Unified Communications Managed API (UCMA) 2.0 on the Lync box.
For detailed information, see Section 14.2.3.2.8, "Installing UCMA v2.0."
-
Deploy WebCenter Portal's Proxy application on the IIS server.
This proxy application provides web services for interacting with the Lync server, and for sending and receiving information. WebCenter Portal talks to these web services and presents the data. For detailed information, see Section 14.2.3.2.9, "Installing WebCenter Portal's Proxy Application."
14.2.3.2.2 Remote Deployment
In this topology, WebCenter Portal's Proxy application is deployed on an IIS server remote to the Lync box. That is, the IIS server and the Lync server are hosted on separate machines.
Because this proxy application is hosted on a remote box, you must set up a trust between the application and the Lync server. This is known as provisioning an application. Provisioning is done through the Application Provisioner utility shipped with Microsoft UCMA v2.0.
Figure 14-6 provides an overview of the steps (including installing UCMA v2.0) to be performed on different deployment entities.
Figure 14-6 Microsoft Lync Configuration - Remote Deployment
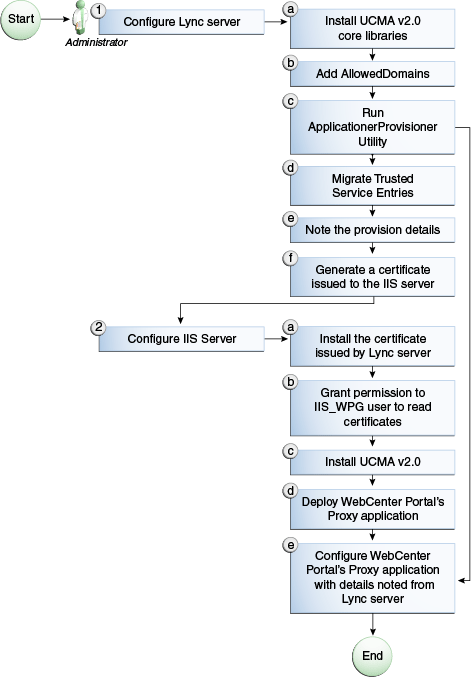
Description of "Figure 14-6 Microsoft Lync Configuration - Remote Deployment"
The details of these steps are described in the following sections.
14.2.3.2.3 Building Application Provisioner
This section lists the steps Microsoft provides for provisioning other IIS servers to access Lync.
-
Install Visual Studio 2008 on any developer box (not necessarily IIS/Lync).
-
Install UCMA version 2.0 on the same box following the steps in Section 14.2.3.2.8, "Installing UCMA v2.0."
The Application Provisioner application comes with the UCMA SDK.
-
Go to the directory
Sample Applications\Collaboration\ApplicationProvisionerunder the location where you installed UCMA Core (for example,C:\Program Files\Microsoft Lync 2010 R2\UCMA SDK 2.0\UCMACore\Sample Applications\Collaboration\ApplicationProvisioner). -
Open the application in Visual Studio 2008 and edit the
Application.csfile as perhttp://msdn.microsoft.com/en-us/library/gg448038.aspx. -
Build the application using Visual Studio 2008.
This generates the
ApplicationProvisioner.exefile. -
Copy the executable file to the Lync box.
14.2.3.2.4 Provisioning WebCenter Portal's Proxy Application on Lync Server
-
Run the
OCSWMIBC.msifile that comes with the Lync setup package.When a UCMA 2.0 application is deployed directly against Lync Server 2010, the SIP domains used in the Lync Server 2010 environment must be added to the Office Communications Server 2007 R2 SIP domain list before you run the
Merge-CsLegacyTopologycmdlet. The application is deployed as if it were being deployed against OCS 2007 R2, then migrated to run against Lync Server 2010. To add the domains, see Section 14.2.3.2.5, "Adding AllowedDomains Using WBemTest." -
Run the
ApplicationProvisioner.exefile, generated in the previous section.The Application Provisioner dialog appears.
-
In the Application Provisioner dialog, enter
WebCenterProxyApplicationas the name of your application for the Application name, and then click Find or Create. -
In the Create Application Pool dialog, select the pool for your application in the Lync Pool Fqdn list.
-
For Listening port, enter the listening port for your application (for example, 6001).
-
For Application server Fqdn, enter the fully qualified domain name (FQDN) of the computer on which the application is deployed. (This is the IIS box.)
-
If the application is deployed on two or more computers, then select the Load balanced application checkbox, and for Load balancer Fqdn, enter the FQDN of the load balancer.
The application pool now appears in the Application Provisioner dialog.
-
-
Double-click the server entry.
The View Server dialog appears. Note the information shown there; that is, Server FQDN, port, and GRUU.
-
Migrate the newly-created trusted entry to Lync Server 2010.
-
Create a certificate on the Lync server with the subject name as the Server FQDN noted in the previous step using the Lync Certificate Wizard.
This certificate is used to authorize the requests coming from the IIS server.
-
After the certificate is created, view the certificate.
-
On the Details tab click Copy to File.
The Certificate Export Wizard appears.
-
Export the certificate with the private key to a file.
A
.pfx(Personal Information Exchange) file with the certificate name is created.
14.2.3.2.5 Adding AllowedDomains Using WBemTest
-
To start
WBemTest.exe, typeWBemTestin a command prompt window and press Enter. -
In the Windows Management Instrumentation Tester dialog, click Connect.
-
In the Connect dialog, click Connect.
-
In the Windows Management Instrumentation Tester dialog, click Enum Classes.
-
In the Superclass Info dialog, click OK.
-
In the Query Result dialog, scroll down to MSFT_SIPDomainData(), and double-click this entry.
-
In the Object editor for MSFT_SIPDomainData dialog, click Instances.
The Query Result dialog appears, displaying the InstanceIDs for any instances of the MSFT_SIPDomainData WMI class. These entries are the AllowedDomain entries.
-
To add AllowedDomain entries, click Add.
-
In the Instance of MSFT_SIPDomainData dialog, in the Properties listbox, double-click Address.
-
In the Property Editor dialog, select the Not NULL radio button.
-
In the Value text input pane, enter the Lync server domain; for example,
contoso.com, and click Save Property. -
In the Instance of MSFT_SIPDomainData dialog, in the Properties listbox, double-click Authoritative, make sure that the Authoritative property is not Null and is set to
False, and then click Save Property. -
In the Instance of MSFT_SIPDomainData dialog, in the Properties listbox, double-click Default Domain, make sure that the Default Domain property is not Null and is set to
True, then click Save Property. -
In the Instance of MSFT_SIPDomainData dialog, click Save Object.
14.2.3.2.6 Migrating Trusted Service Entries Using Topology Builder or PowerShell Cmdlets
To migrate trusted service entries using Microsoft Lync Server 2010 Topology Builder:
-
Launch Microsoft Lync Server 2010, Topology Builder.
-
After the existing topology is loaded, under Action, select Merge 2007 or 2007 R2 Topology.
-
Go through the resulting wizard, keeping the default options.
-
Select Publish Topology and complete the wizard, as in the previous step.
-
After the wizard has finished, check that it completed successfully.
There should be no errors in the user interface.
To migrate trusted service entries using Microsoft Lync Server 2010 PowerShell Cmdlets:
-
From the Start menu, in the Microsoft Lync Server 2010 program group, open Lync Server Management Shell.
-
Run the following PowerShell cmdlet:
Merge-CsLegacyTopology -TopologyXmlFileName D:\output.xml
-
Run the following PowerShell cmdlet:
Publish-CsTopology -FileName D:\output.xml
14.2.3.2.7 IIS Server Configuration
Because the IIS server hosts WebCenter Portal's Proxy application in the remote deployment scenario, use the information from the previous section to make it a trusted authority.
-
Install the certificate issued by the Lync server with the private key: Copy the .pfx file generated in step 7 under section "Provisioning WebCenter Portal's Proxy Application on Lync Server" to the IIS box, and double-click it.
The Certificate Import wizard appears.
-
Import the certificate in Personal Folder under LOCAL_MACHINE
-
Make an entry in
C:/WINDOWS/system32/drivers/etc/hostsfor the pool name of the Lync server as follows:<ip-address-of-lync-box> <poolname-of-lync-box>
For example:
10.177.252.146 pool01.example.com
-
Because the IIS server hosts WebCenter Portal's Proxy application, install Microsoft UCMA v2.0 on it.
For detailed information, see Section 14.2.3.2.8, "Installing UCMA v2.0."
-
After UCMA is installed, deploy this proxy application on the IIS server.
WebCenter Portal's Proxy application provides web services for interacting with Lync, and for sending and receiving information. WebCenter Portal talks to these web services and presents the data. For detailed information, see Section 14.2.3.2.9, "Installing WebCenter Portal's Proxy Application."
-
Go to the location where WebCenter Portal's Proxy application was extracted, and open
Web.configand edit theappSettingsXML node to add the values noted in Step 7 in the previous section (Section 14.2.2.2.5, "IIS Server Configuration").Make sure to set the value for
RemoteDeploymentto true. For example, theappsettingsXML node should look somewhat like this.<appSettings> <add key="ApplicationName" value="WebCenterProxyApplication"/> <add key="RemoteDeployment" value="true"/> <add key="ApplicationFQDN" value="iis.server.com"/> <add key="ApplicationGRUU" value="sip:iis.server.com@EXAMPLE.COM;gruu;opaque=srvr:WebCenterProxyApplication:7mhSo94PlUK-5Q2bKPLyMAAA"/> <add key="ApplicationPort" value="6001"/> </appSettings>
Note:
If you see the following exception in the log file:
ErrorCode = -2146893039
FailureReason = NoAuthenticatingAuthority
e.Message = "Unable to perform authentication of credentials."
base {Microsoft.Rtc.Signaling.FailureResponseException} = {"Unable to perform authentication of credentials."}
InnerException = {"NegotiateSecurityAssociation failed, error: \-2146893039"}
then add the following entry to Web.config:
<identity impersonate="true" userName="Administrator" password="MyPassword*"/>
where username is the administrator's user name, and password is the administrator's password.
The trust is established, and WebCenter Portal's Proxy application can talk to the Lync server.
14.2.3.2.8 Installing UCMA v2.0
Microsoft Unified Communications Managed API v2.0 (UCMA) is an endpoint API that allows advanced developers to build server applications that can interact with the Lync environment.
In a simple deployment, the UCMA is installed on the same box as Lync. In a remote deployment, the Lync core libraries are installed on the Lync box, and the UCMA is installed on the IIS (proxy) box.
-
Download UCMA v2.0 installation from the following location:
http://www.microsoft.com/downloads/details.aspx?FamilyID=b20967b1-6cf5-4a4b-b7ae-622653ac929f&displaylang=en -
Download and run the
UcmaSDKWebDownload.msifile.Setup files are extracted to the folder
C:\Microsoft Unified Communications Managed API 2.0 SDK Installer package\amd64 -
Go to the directory (where the files from the previous step were extracted) and run
vcredist_x86.exe.Run-time components of Visual C++ Libraries, required for UCMA APIs, are installed.
-
Go to the directory called
Setupand runUcmaRedist.msi.UCMA 2.0 assemblies in the GAC are installed.
14.2.3.2.9 Installing WebCenter Portal's Proxy Application
-
Extract
owc_ocs2007.zipfrom the companion CD.A directory named
OCSWebServicesis created. -
Open the Internet Information Services (IIS) Manager.
-
Expand the server node and then Sites in the IIS Manager.
-
Right-click Lync Internal Web Site, and then select Add Application.
-
In the Add Application wizard, enter an alias for the virtual directory in the Alias field, for example
RTC. -
Enter the path to the directory extracted from the
owc_ocs2007.zipfile, and then click OK.For example, if you extracted the zip file in C:\, then enter
C:\OCSWebServices. Alternatively, use the Browse button to navigate to that directory. Click OK. -
Right-click the newly created application and select Edit Permissions to open the Properties dialog.
-
In the Security tab, edit permissions to grant user Everyone read permission.
-
Test the Web service by accessing the website using the following URL format:
http://localhost/lync_internal_web_site/OCSWebService.asmx.where
lync_internal_web_siteis the virtual directory you created for the Oracle RTC Web service.For example:
http://localhost/RTC/OCSWebService.asmx
14.2.3.3 Microsoft Lync - Security Considerations
You must configure an external application for Microsoft Lync connections so that users can supply credentials to authenticate themselves on the Lync server.
With a secured application, users get presence status. With Lync, if security is required, then Lync should be on a private trusted network.
Lync provides an option for changing external credentials, which works as an alternative to using an external application. A logged-in user can click any Presence tag and select Change Credentials from the menu.
For more information, see Section 14.3.1, "Registering Instant Messaging and Presence Servers Using Fusion Middleware Control."
14.3 Registering Instant Messaging and Presence Servers
You can register multiple presence server connections with WebCenter Portal, but only one of them is active at a time.
To start using the new (active) presence server you must restart the managed server on which WebCenter Portal is deployed.
This section includes the following subsections:
-
Section 14.3.1, "Registering Instant Messaging and Presence Servers Using Fusion Middleware Control"
-
Section 14.3.2, "Registering Instant Messaging and Presence Servers Using WLST"
14.3.1 Registering Instant Messaging and Presence Servers Using Fusion Middleware Control
To register a presence server connection:
-
Log in to Fusion Middleware Control and navigate to the home page for WebCenter Portal. For more information, see:
-
Do one of the following:
-
For WebCenter Portal - From the WebCenter Portal menu, select Settings > Service Configuration.
-
For Portal Framework application - From the Application Deployment menu, select WebCenter Portal > Service Configuration.
-
-
On the WebCenter Portal Service Configuration page, select Instant Messaging and Presence.
-
To connect to a new presence server, click Add (Figure 14-7).
Figure 14-7 Configuring Instant Messaging and Presence
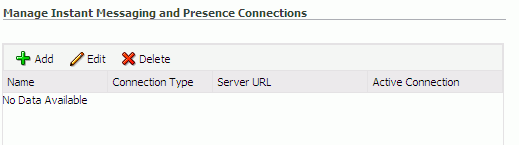
Description of "Figure 14-7 Configuring Instant Messaging and Presence"
-
Enter a unique name for this connection, specify the presence server type, and indicate whether this connection is the active (or default) connection for the application (Table 14-1).
Table 14-1 Instant Messaging and Presence Connection - Name
Field Description Connection Name
Enter a unique name for the connection. The name must be unique (across all connection types) within WebCenter Portal.
Connection Type
Specify the type of presence server:
-
Microsoft Live Communications Server (LCS)
-
Microsoft Office Communications Server 2007 (OCS)
Out-of-the-box, WebCenter Portal supports Microsoft LCS, OCS, and Lync.
Note: Microsoft Lync connections use the Microsoft Office Communications Server 2010 connection type. (Oracle Beehive Server connections are not supported in this release.)
Active Connection
Select to use this connection in WebCenter Portal for instant messaging and presence.
While you can register multiple presence server connections for an application, only one connection is used by IMP—the default (or active) connection.
-
-
Enter connection details for the server hosting instant messaging and presence (Table 14-2).
Table 14-2 Instant Messaging and Presence Connection - Connection Details
Field Description Server URL
Enter the URL of the server hosting instant messaging and presence.
For example:
http://myocshost.com:8888User Domain
(OCS/Lync Only) Enter the name of the Active Directory domain (on the Microsoft Office Communications Server) that is associated with this connection. The user domain is mandatory for OCS/Lync connections.
Refer to Microsoft documentation for details on the user domain.
Pool Name
Enter the name of the pool that is associated with this connection. The pool name is mandatory.
Refer to Microsoft documentation for details on the pool name.
Associated External Application
Associate the instant messaging and presence server with an external application. External application credential information is used to authenticate users against the instant messaging and presence server.
An external application is mandatory.
You can select an existing external application from the list, or click Create New to configure a new external application.
The external application you configure for instant messaging and presence must use the
POSTauthentication method, and specify an additional field namedAccount(Name property) that is configured toDisplay to User(checked). For more information, see Chapter 23, "Managing External Applications." -
Enter a timeout in the Advanced Configuration field (Table 14-4).
Table 14-3 Instant Messaging and Presence Connection - Advanced Configuration
Field Description Connection Timeout (seconds)
Specify a suitable timeout for the connection.
This is the length of time (in seconds) WebCenter Portal waits for a response from the presence server before issuing a connection timeout message.
The default is -1 which means that the default is used. The default is 10 seconds.
-
Sometimes, additional parameters are required to connect to the presence server.
If additional parameters are required to connect to the presence server, expand Additional Properties and enter details as required (Table 14-4).
Table 14-4 Instant Messaging and Presence Connection - Additional Properties
Field Description Add
Click Add to specify an additional connection parameter:
-
Property Name -Enter the name of the connection property.
-
Property Value - Enter the default value for the property.
-
Is Property Secured - Indicate whether encryption is required. When selected, the property value is stored securely using encryption.
For example, select this option to secure the
admin.passwordproperty where the value is the actual password.
Delete
Click Delete to remove a selected property.
Select the correct row before clicking Delete.
Note: Deleted rows appear disabled until you click OK.
-
-
Click OK to save this connection.
-
To start using the new (active) connection you must restart the managed server on which WebCenter Portal or your Portal Framework application is deployed.
For more information, see Section 7.2, "Starting and Stopping Managed Servers for WebCenter Portal Application Deployments."
14.3.2 Registering Instant Messaging and Presence Servers Using WLST
Use the WLST command createIMPConnection to create a presence server connection. For command syntax and examples, see the "createIMPConnection" section in Oracle Fusion Middleware WebLogic Scripting Tool Command Reference.
For information on how to run WLST commands, see Section 1.13.3.1, "Running Oracle WebLogic Scripting Tool (WLST) Commands."
To configure instant messaging and presence to actively use a new IMP connection, set default=true. For more information, see Section 14.4.2, "Choosing the Active Connection for Instant Messaging and Presence Using WLST."
Note:
To start using the new (active) connection you must restart the managed server on which WebCenter Portal or your Portal Framework application is deployed. For more information, see the "Starting and Stopping Managed Servers Using the Command Line" section in Oracle Fusion Middleware Administrator's Guide.
14.4 Choosing the Active Connection for Instant Messaging and Presence
You can register multiple instant messaging and presence server connections with WebCenter Portal, but only one connection is active at a time. The active connection becomes the back-end presence server for WebCenter Portal.
This section includes the following subsections:
14.4.1 Choosing the Active Connection for Instant Messaging and Presence Using Fusion Middleware Control
To change the active connection:
-
Log in to Fusion Middleware Control and navigate to the home page for WebCenter Portal. For more information, see:
-
Do one of the following:
-
For WebCenter Portal - From the WebCenter Portal menu, select Settings > Service Configuration.
-
For Portal Framework applications - From the Application Deployment menu, select WebCenter Portal > Service Configuration.
-
-
On the WebCenter Portal Services Configuration page, select Instant Messaging and Presence.
The Manage Instant Messaging and Presence Connections table indicates the current active connection, if any.
-
Select the connection you want to make the active (or default) connection, and then click Edit.
-
Select the Active Connection check box.
-
Click OK to update the connection.
-
To start using the new (active) connection you must restart the managed server on which WebCenter Portal or your Portal Framework application is deployed.
See Section 7.2, "Starting and Stopping Managed Servers for WebCenter Portal Application Deployments."
14.4.2 Choosing the Active Connection for Instant Messaging and Presence Using WLST
Use the WLST command setIMPConnection with default=true to activate an existing presence server connection. For command syntax and examples, see the "setIMPConnection" section in Oracle Fusion Middleware WebLogic Scripting Tool Command Reference.
To disable a presence server connection, either delete it, make another connection the 'active connection,' or use the removeIMPServiceProperty command:
removeIMPServiceProperty('appName='webcenter', property='selected.connection')
Using this command, connection details are retained but the connection is no longer named as an active connection. For more information, see the "removeIMPServiceProperty" section in Oracle Fusion Middleware WebLogic Scripting Tool Command Reference.
For information on how to run WLST commands, see Section 1.13.3.1, "Running Oracle WebLogic Scripting Tool (WLST) Commands."
Note:
To start using this active connection you must restart the managed server on which WebCenter Portal or your Portal Framework application is deployed. For more information, see the "Starting and Stopping Managed Servers Using the Command Line" section in Oracle Fusion Middleware Administrator's Guide.
14.5 Modifying Instant Messaging and Presence Connection Details
You can modify instant messaging and presence server connection details at any time.
To start using an updated (active) connection you must restart the managed server on which WebCenter Portal is deployed.
This section includes the following subsections:
14.5.1 Modifying Instant Messaging and Presence Connections Details Using Fusion Middleware Control
To update connection details for an instant messaging and presence server:
-
Log in to Fusion Middleware Control and navigate to the home page for WebCenter Portal. For more information, see:
-
Do one of the following:
-
For WebCenter Portal - From the WebCenter Portal menu, select Settings > Service Configuration.
-
For Portal Framework applications - From the Application Deployment menu, select WebCenter Portal > Service Configuration.
-
-
On the WebCenter Portal Service Configuration page, select Instant Messaging and Presence.
-
Select the connection name, and click Edit.
-
Edit connection details, as required.
For detailed parameter information, see Table 14-2, "Instant Messaging and Presence Connection - Connection Details".
-
Click OK to save your changes.
-
To start using the updated (active) connection you must restart the managed server on which WebCenter Portal or your Portal Framework application is deployed.
For more information, see Section 7.2, "Starting and Stopping Managed Servers for WebCenter Portal Application Deployments."
14.5.2 Modifying Instant Messaging and Presence Connections Details Using WLST
Use the WLST command setIMPConnection to edit presence server connection details. For command syntax and examples, see the "setIMPConnection" section in Oracle Fusion Middleware WebLogic Scripting Tool Command Reference.
If additional parameters are required to connect to your presence server, then use the setIMPConnectionProperty command. For more information, see the "setIMPConnectionProperty" section in Oracle Fusion Middleware WebLogic Scripting Tool Command Reference.
For information on how to run WLST commands, see Section 1.13.3.1, "Running Oracle WebLogic Scripting Tool (WLST) Commands."
Note:
To start using the updated (active) connection you must restart the managed server on which WebCenter Portal and your Portal Framework application is deployed. For more information, see the "Starting and Stopping Managed Servers Using the Command Line" section in Oracle Fusion Middleware Administrator's Guide.
14.6 Deleting Instant Messaging and Presence Connections
You can delete instant messaging and presence connections at any time, but use caution when deleting the active connection. When you delete the active connection, user presence options are not available, as these require a back-end instant messaging and presence server.
When you delete a connection, consider deleting the external application associated with instant messaging and presence if the application's sole purpose was to support it. For more information, see Section 23.6, "Deleting External Application Connections."
This section includes the following subsections:
14.6.1 Deleting Instant Messaging and Presence Connections Using Fusion Middleware Control
To delete an instant messaging and presence server connection:
-
Log in to Fusion Middleware Control and navigate to the home page for WebCenter Portal. For more information, see:
-
Do one of the following:
-
For WebCenter Portal - From the WebCenter Portal menu, select Settings > Service Configuration.
-
For Portal Framework applications - From the Application Deployment menu, select WebCenter Portal > Service Configuration.
-
-
On the WebCenter Portal Service Configuration page, select Instant Messaging and Presence.
-
Select the connection name, and click Delete.
-
To make this change you must restart the managed server on which WebCenter Portal or your Portal Framework application is deployed.
For more information, see Section 7.2, "Starting and Stopping Managed Servers for WebCenter Portal Application Deployments."
Note:
Before restarting the managed server, mark another connection as active; otherwise, Instant Messaging and Presence is disabled.
14.6.2 Deleting Instant Messaging and Presence Connections Using WLST
Use the WLST command deleteConnection to remove a presence server connection. For command syntax and examples, see the "deleteConnection" section in Oracle Fusion Middleware WebLogic Scripting Tool Command Reference.
For information on how to run WLST commands, see Section 1.13.3.1, "Running Oracle WebLogic Scripting Tool (WLST) Commands."
14.7 Setting Up Instant Messaging and Presence Defaults
Use the WLST command setIMPServiceProperty to set defaults for IMP:
-
selected.connection: Connection used by instant messaging and presence. -
rtc.cache.time: Cache timeout for instant messaging and presence data. -
resolve.display.name.from.user.profile: Determines what to display if user display names are missing. When set to 0, and display name information is unavailable, only the user name displays in the application. When set to1, and display name information is unavailable, display names are read from user profile data. Setting this option to1impacts performance. The default setting is0.Display names are not mandatory in presence data. If the application does not always provide display names by default and you consider this information important, set
resolve.display.name.from.user.profileto1so that display names always display. -
im.address.resolver.class: Resolver implementation used to map user names to IM addresses and IM addresses to user names. The default setting isoracle.webcenter.collab.rtc.IMPAddressResolverImpl. This implementation looks for IM addresses in the following places and order:-
User Preferences
-
User Credentials
-
User Profiles
-
-
im.address.profile.attribute: User profile attribute used to determine a user's IM address. The default setting isBUSINESS_EMAIL. Users can change this default withim.address.profile.attribute.
For command syntax and detailed examples, see the "setIMPServiceProperty" section in Oracle Fusion Middleware WebLogic Scripting Tool Command Reference.
For information on how to run WLST commands, see Section 1.13.3.1, "Running Oracle WebLogic Scripting Tool (WLST) Commands."
14.8 Testing Instant Messaging and Presence Connections
Oracle RTC web services expose a set of web methods that you can invoke to test validity. To verify a connection, try accessing the web service endpoints. The following examples assume the application context path is /RTC:
-
protocol://host/RTC/ApplicationConfigurationService.asmx -
protocol://host/RTC/RTCService.asmx -
protocol://host/RTC/OCSWebService.asmx