16 Creating a Split Domain Topology
This chapter describe additional procedures and modifications to procedures that are necessary to deploy a split domain topology.
This chapter contains the following topics:
-
Section 16.3, "Additional Requirements for Preparing the File System"
-
Section 16.4, "Additional Requirement for Preparing the Servers"
-
Section 16.5, "Requirements for Creating the Additional Domain"
-
Section 16.8, "Additional Oracle Identity Manager Requirements"
16.1 Introduction to Split Domain Topology
As described in Section 2.2.2.3, "Architecture Notes," in a split domain configuration, Oracle Identity Manager is installed into a separate domain from other components. The decision to use the split domain topology requires several modifications and additions to the procedures in this Guide. This chapter describes these changes and additions.
16.2 Additional Network Requirements
In addition to preparing the network as described in Chapter 3, perform the following additional preparations for split domain implementations.
This section contains the following topics:
16.2.1 Virtual Server Names
In addition to the virtual server names listed in Section 3.3, "About Virtual Server Names Used by the Topologies," you need the following additional virtual server for the split domain topology:
-
This virtual server is only required when a split domain topology is being used.
-
This virtual server is enabled on LBR1. It acts as the access point for all internal HTTP traffic that gets directed to the administration services in the OIM Domain. The incoming traffic from clients is non-SSL enabled. Thus, the clients access this service using the address
OIMADMIN.mycompany.com:80(HTTP_PORT) and in turn forward these to ports 7777 (OHS_PORT) on WEBHOST1 and WEBHOST2. The services accessed on this virtual host include the WebLogic Administration Server Console, and Oracle Enterprise Manager Fusion Middleware Control. -
Create rules in the firewall to block outside traffic from accessing the
/consoleand/emURLs using this virtual host. Only traffic inside the DMZ should be able to access these URLs on theOIMADMIN.mycompany.comvirtual host.
16.2.2 Load Balancer Configuration
In Section 3.4.3, "Load Balancer Configuration," Table 3-1 describes the configuration of your load balancer. For a split domain topology, configure the following additional virtual host:
16.2.3 Virtual IP Addresses
Section 3.5, "About IP Addresses and Virtual IP Addresses," lists Virtual IP addresses required by Oracle Identity Management. The following additional Virtual IP address is required for a split domain topology:
OIMADMINVHN.mycompany.com
You need this virtual IP address when you are using a split domain topology. It serves a similar function to ADMINVHN.mycompany.com. This virtual IP address fails over along with the Administration Server from IDMHOST1 to IDMHOST2, or vice versa.
16.2.4 Configuring Servers to Listen on Virtual and Physical IP Addresses
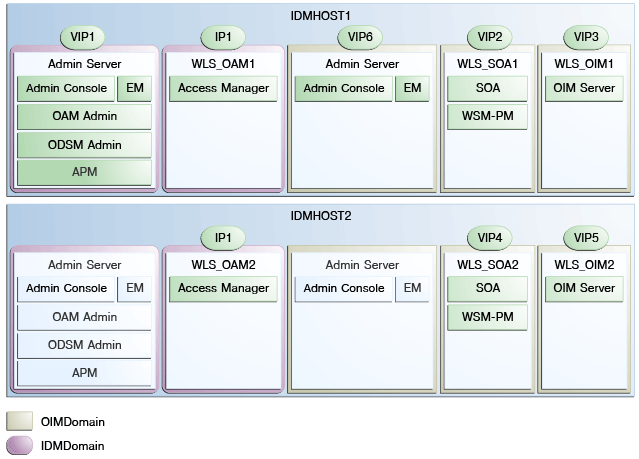
Section 3.5, "About IP Addresses and Virtual IP Addresses," also describes how to configure the administration server and the managed servers to listen on different virtual IPs and physical IPs. This illustrated in Figure 3-1. The following figure is a modified version of Figure 3-1, listing all the IP addresses and VIP Addresses, including those for OIMDomain.
Table 3-2 provides a mapping of VIP addresses to Virtual hosts. All of the VIP addresses in that table are required. For a split domain topology, the VIP address VIP6, which maps to OIMADMINVHN, must be enabled as shown:
Table 16-2 VIP Addresses and Virtual Hosts
| Virtual IP | VIP Maps to... | Description |
|---|---|---|
|
VIP6 |
OIMADMINVHN |
OIMADMINVHN is the virtual host name that is the listen address for the Oracle Identity Manager Administration Server. It fails over with manual failover of the Administration Server. It is enabled on the node where the Oracle Identity Manager Administration Server process is running (IDMHOST1 by default). |
16.2.5 Firewalls and Ports
Section 3.6, "About Firewalls and Ports," lists the firewall ports used by the topology in Table 3-3. The following additional port is required for Oracle WebLogic Administration Server access from the Web Tier.
Table 16-3 Ports Used in the Oracle Identity Management Enterprise Deployment topologies
| Type | Firewall | Port and Port Range | Protocol / Application | Inbound / Outbound | Timeout |
|---|---|---|---|---|---|
|
Oracle WebLogic Administration Server access from web tier |
FW1 |
|
HTTP / Oracle HTTP Server and Administration Server |
Inbound |
N/A |
16.3 Additional Requirements for Preparing the File System
Section 4.4, "About Recommended Locations for the Different Directories" describes directory usage. Among other things, it recommends that you have more than one Middleware home (MW_HOME).
When you are implementing a split domain topology, you need yet another Middleware home, a separate MW_HOME for the second domain. This facilitates independent patching.
The details for shared and local storage must be modified as follows.
-
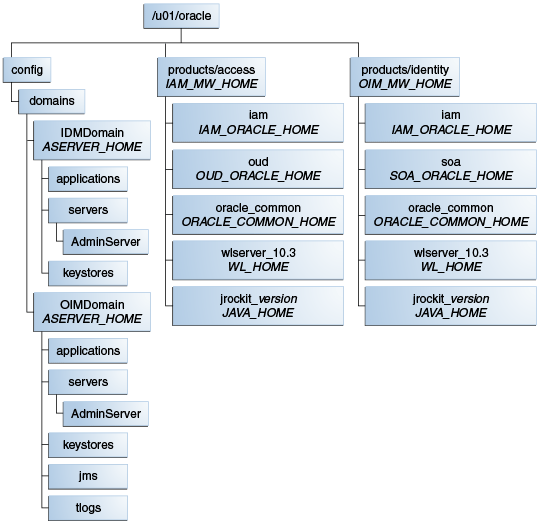
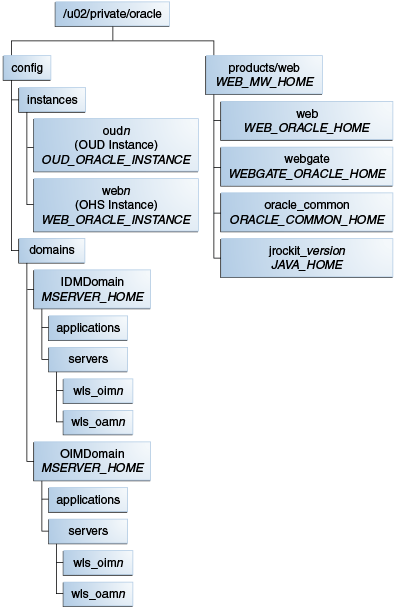
Section 4.4.4.1, "Shared Storage" discusses the volumes that should be kept on shared storage. When you are using a split domain topology, there are additional volumes to be kept on shared storage. The recommended layout is described in Table 16-4 and shown in Figure 16-2.
-
Section 4.4.4.2, "Local Storage" lists the directories to be created on local storage.
The recommended layout for local storage is described in Table 4-1. The split domain differs in that it includes an additional MSERVER_HOME in OIMDomain, as shown in Figure 16-3.
16.4 Additional Requirement for Preparing the Servers
Table 5-2 in Chapter 5, "Preparing the Servers for an Enterprise Deployment," lists additional virtual hosts that you must enable. For a split domain topology, you must also enable virtual host OIMADMINVHN.mycompany.com as shown:
16.5 Requirements for Creating the Additional Domain
In a split domain topology, you must create two domains, one for Access Manager and the other for Oracle Identity Manager.
Note:
There is no need to create a separate node manager for this domain. Only one Node Manager is deployed per host, and that is used to manage WebLogic components in both domains.
Perform the instructions in Section 8.4, "Running the Configuration Wizard to Create a Domain" to create a domain for Access Manager called IDMDomain. Then repeat the instructions with the following modifications to create a second domain called OIMDomain to host the Oracle Identity Manager components.
-
In Step 5, on the Select Domain Source screen, select only the following products:
-
Oracle Enterprise Manager [oracle_common]
-
Oracle Platform Security Service [iam]
-
Oracle JRF [oracle_common]
-
-
In Step 14, on the Configure the Administration Server screen, enter the following values for Listen Address and Listen Port:
-
Listen Address:
OIMADMINVHN.mycompany.com -
Listen Port:
7101(SPLIT_WLS_ADMIN_PORT) -
SSL Listen Port:
7102(SPLIT_WLS_ADMIN_SSL_PORT) -
SSL Enabled: Selected
-
-
In Step 17, on the Configure Machines screen, specify the Name value
OIMADMINVHNinsteadADMINVHN.
As described in Section 8.5.1, "Copying OIM Adapter Template," you must perform the following steps if you are using Oracle Unified Directory in active-active mode:
-
After installing Oracle Identity and Access Management, apply Patch 16943171 .
-
Manually copy the file
adapter_template_oim.xmlfromORACLE_COMMON_HOME/modules/oracle.ovd_11.1.1/templates/to IAM_ORACLE_HOME/libovd/. For example:cp ORACLE_COMMON_HOME/modules/oracle.ovd_11.1.1/templates/adapter_template_oim.xml IAM_ORACLE_HOME/libovd/
In Section 8.5.3, "Reassociate the Domain with the Existing OPSS Policy Store," you associate the first domain with the OPSS policy store. For a split domain topology, you must also associate the additional domain with the existing policy store. To do that, you must first export the encryption key from the policy store and then join the new domain to the policy store using the generated encryption key.
To generate the OIMDomain with the existing OPSS data store, proceed as follows:
-
Start
wlstusing the command:ORACLE_COMMON_HOME/common/bin/wlst.shThen execute this command to generate the encryption key:
exportEncryptionKey (jpsConfigFile="wls-domain-path/config/fmwconfig/jps-config.xml",keyFilePath="opss-keyfile-path",keyFilePassword="opss-keyfile-password" )
For Example:
exportEncryptionKey(jpsConfigFile="ASERVER_HOME/config/fmwconfig/jps-config.xml",keyFilePath="/u01/oracle/opss_keystore", keyFilePassword="password" )
where
ASERVER_HOMEis theASERVER_HOMEof IDMDomain. This creates a file calledewallet.p12in the location specified inopss-keyfile-path.Note:
Before you run the command, the directory specified in the
opss-keyfile-pathmust exist. -
Associate OIMDomain with the policy store by running the following command:
ORACLE_COMMON_HOME/common/bin/wlst.sh IAM_ORACLE_HOME/common/tools/configureSecurityStore.py -d ASERVER_HOME -c IAM -m join -p opss_schema_password -k opss-keyfile-path -w opss-keyfile-password
where
ASERVER_HOMEis theASERVER_HOMEof OIMDomain,opss_schema_passwordis the password of the schema EDG_OPSS andopss-keyfile-pathandopss-keyfile-passwordare the values you supplied to the export command. For example:ORACLE_COMMON_HOME/common/bin/wlst.sh IAM_ORACLE_HOME/common/tools/configureSecurityStore.py -d ASERVER_HOME -c IAM -m join -p opss_schema_password -k /u01/oracle/opss_keystore -w password
To associate subsequent domains with the existing policy store, you must first export the encryption key from the policy store and then join the new domain to the policy store using the generated encryption key.
When performing a backup after creating domains, back up the OIMDomain as well as the IDMDomain. See Section 17.6.3, "Performing Backups During Installation and Configuration."
16.6 Additional Web Tier Requirements
Section 10.5, "Setting the Front End URL for the Administration Console" describes how to change the Administration Server's front end URL so that the user's browser is redirected to the appropriate load balancer address. When you have a split domain topology, in Step 8, set the Front End Host and Front End HTTP PORT fields to the OIMADMIN load balancer address, as follows.
-
Front End Host:
OIMADMIN.mycompany.com -
Front End HTTP PORT: 80 (HTTP_PORT)
Section 10.3.3.2, "Create Virtual Host Definitions" describes the files to create on each web host in WEB_ORACLE_INSTANCE/config/OHS/component_name/moduleconf. When you are using a split domain, you must make the following changes:
-
Create Virtual Host for ADMIN.mycompany.com–The file
admin_vh.confmust not contain the Oracle Identity Manager configuration. The file should contain only the following lines:<VirtualHost *:7777> ServerName ADMIN.mycompany.com:80 RewriteEngine On RewriteOptions inherit ServerAdmin you@your.address ################################### ## General Domain Configuration ################################### # Admin Server and EM <Location /console> SetHandler weblogic-handler WebLogicHost ADMINVHN.mycompany.com WebLogicPort 7001 </Location> <Location /consolehelp> SetHandler weblogic-handler WebLogicHost ADMINVHN.mycompany.com WebLogicPort 7001 </Location> <Location /em> SetHandler weblogic-handler WebLogicHost ADMINVHN.mycompany.com WebLogicPort 7001 </Location> ################################################### ## Entries Required by Oracle Entitlements Server ################################################### # APM <Location /apm> SetHandler weblogic-handler WebLogicHost ADMINVHN.mycompany.com WebLogicPort 7001 </Location> ################################################## ## Entries Required by Oracle Unified Directory ################################################## # OUD ODSM <Location /odsm> SetHandler weblogic-handler WebLogicHost ADMINVHN.mycompany.com WebLogicPort 7001 </Location> ############################################## ## Entries Required by Oracle Access Manager ############################################## # OAM Console <Location /oamconsole> SetHandler weblogic-handler WebLogicHost ADMINVHN WebLogicPort 7001 </Location> </VirtualHost> -
Create Virtual Host for OIMADMIN.mycompany.com–For split domain only, create a file called
oimadmin_vh.conf. This will contain a list of locations which are supported by clients accessing the domain usingOIMADMIN.mycompany.com. These entries are used by clients accessing the administration components in the OIMDomain.<VirtualHost *:7777> ServerName http://OIMADMIN.mycompany.com:80 RewriteEngine On RewriteOptions inherit ServerAdmin you@your.address ########################### ## Generic Entries ########################### # Admin Server and EM <Location /console> SetHandler weblogic-handler WebLogicHost OIMADMINVHN.mycompany.com WebLogicPort 7101 </Location> <Location /consolehelp> SetHandler weblogic-handler WebLogicHost OIMADMINVHN.mycompany.com WebLogicPort 7101 </Location> <Location /em> SetHandler weblogic-handler WebLogicHost OIMADMINVHN.mycompany.com WebLogicPort 7101 </Location> ################################################# ## Entries required by Oracle Identity Manager ################################################# # OIM self and advanced admin webapp consoles(canonic webapp) <Location /oim> SetHandler weblogic-handler WLProxySSL ON WLProxySSLPassThrough ON WLCookieName oimjsessionid WebLogicCluster OIMHOST1VHN:14000,OIMHOST2VHN:14000 WLLogFile "${ORACLE_INSTANCE}/diagnostics/logs/OHS/oim_component.log" </Location> # OIM, xlWebApp - Legacy 9.x webapp (struts based) <Location /xlWebApp> SetHandler weblogic-handler WLProxySSL ON WLProxySSLPassThrough ON WLCookieName oimjsessionid WebLogicCluster OIMHOST1VHN:14000,OIMHOST2VHN:14000 WLLogFile "${ORACLE_INSTANCE}/diagnostics/logs/OHS/oim_component.log" </Location> # OIM self service console <Location /identity> SetHandler weblogic-handler WLProxySSL ON WLProxySSLPassThrough ON WLCookieName oimjsessionid WebLogicCluster OIMHOST1VHN:14000,OIMHOST2VHN:14000 WLLogFile "${ORACLE_INSTANCE}/diagnostics/logs/OHS/oim_component.log" </Location> # OIM Nexaweb WebApp - used for workflow designer and DM <Location /Nexaweb> SetHandler weblogic-handler WLProxySSL ON WLProxySSLPassThrough ON WLCookieName oimjsessionid WebLogicCluster OIMHOST1VHN:14000,OIMHOST2VHN:14000 WLLogFile "${ORACLE_INSTANCE}/diagnostics/logs/OHS/oim_component.log" </Location> # OIM System Admin Console <Location /sysadmin> SetHandler weblogic-handler WLCookieName oimjsessionid WebLogicCluster OIMHOST1VHN:14000,OIMHOST2VHN:14000 WLLogFile "${ORACLE_INSTANCE}/diagnostics/logs/OHS/oim_component.log" </Location> </VirtualHost>
16.7 Additional Access Manager Requirements
When updating the OAM agent, as described in Section 11.6.5, "Updating Newly-Created Agent," enter the following values for Host Name and Port in addition to the values listed in Step 16:
-
Host Name:
OIMADMIN.mycompany.com -
Port:
80(HTTP_PORT)
16.8 Additional Oracle Identity Manager Requirements
Chapter 12, "Extending the Domain to Include Oracle Identity Manager," describes how to install and configure Oracle Identity Manager for the single domain topology. In general, when you are building a split domain topology, the procedures are similar, but you specify the OIMDomain instead of IDMDomain and the virtual host OIMADMINVHN instead of ADMINVHN. The specific changes are described in the following sections.
This section contains the following topics:
-
Section 16.8.2, "Provisioning the Login Modules and Creating the wlfullclient.jar "
-
Section 16.8.3, "Extending the Domain to Configure Oracle Identity Manager and Oracle SOA Suite"
-
Section 16.8.5, "Deploying Oracle Identity Manager and Oracle SOA"
-
Section 16.8.6, "Enabling Oracle Identity Manager to Connect to SOA"
-
Section 16.8.7, "Configuring Access Manager for Oracle Identity Manager Integration"
16.8.1 Domain URLs
In Section 12.2, "About Domain URLs," Table 12-1 list the URLs for Oracle Identity Manager that become available after the installation and configuration are complete. When you are configuring a split domain topology, the Oracle Identity Manager URL will be as follows, rather than the one listed in Table 12-1:
16.8.2 Provisioning the Login Modules and Creating the wlfullclient.jar
In a split doamin topology, perform the steps in Section 12.4, "Provisioning the OIM Login Modules Under the WebLogic Server Library Directory," but in OIM_MW_HOME rather than IAM_MW_HOME.
As described in Section 12.5, "Creating the wlfullclient.jar File," you must create the wlfullclient.jar library this library under the IAM_MW_HOME/wlserver_10.3/server/lib directory on all the machines hosting Oracle Identity Manager in the application tier of your environment. In a split domain topology, create the library in OIM_MW_HOME rather than IAM_MW_HOME. Specifically, in Step 1, you must navigate to the OIM_MW_HOME/wlserver_10.3/server/lib directory.
16.8.3 Extending the Domain to Configure Oracle Identity Manager and Oracle SOA Suite
You must extend the domain with Oracle Identity Manager components as described in Section 12.7, "Extending the Domain to Configure Oracle Identity Manager and Oracle SOA Suite." When you are creating a split domain topology, you extend the OIMDomain rather than the IDMDomain.
In Step 2, on the Select WebLogic Domain Directory screen, select the location of the domain directory for the OIMDomain, ASERVER_HOME, for example: /u01/oracle/config/domains/domain_name
16.8.4 Configuring Oracle Identity Manager
When configuring Oracle Identity Manager, as described in Section 12.10, "Configuring Oracle Identity Manager," on the WebLogic Administration Server screen in Step 4, specify the following URL to connect to the WebLogic Administration Server:
t3://OIMADMINVHN.mycompany.com:7101
where 7101 is WLS_ADMIN_PORT in Section B.3.
16.8.5 Deploying Oracle Identity Manager and Oracle SOA
As described in Section 12.8, "Deploying Oracle Identity Manager and Oracle SOA to Managed Server Domain Directory on IDMHOST1 and IDMHOST2," once the configuration is complete, you must propagate the Oracle Identity Manager configuration to the managed server directory on IDMHOST1 and IDMHOST2. Instead of packing the domain IDMDomain, do this on OIMDomain.
16.8.6 Enabling Oracle Identity Manager to Connect to SOA
In Section 12.20, "Enabling Oracle Identity Manager to Connect to SOA Using the Administrative Users Provisioned in LDAP," you perform post installation steps to enable Oracle Identity Manager to work with the Oracle WebLogic Server administrator user provisioned in the central LDAP store. Be sure to specify the correct domain in the following steps:
-
Step 2: For a split domain topology, select Farm_OIMDomain –> Identity and Access –> OIM –> oim(11.1.2.0.0).
-
Step 7: For a split domain topology, select Weblogic Domain –> OIMDomain from the Navigator.
-
Step 14a: Log in to the OIM Administration Console at the URL
http://OIMADMIN.mycompany.com/sysadmin, rather thanhttp://ADMIN.mycompany.com/sysadmin, as the userxelsysadm.
16.8.7 Configuring Access Manager for Oracle Identity Manager Integration
In Section 12.23.4, "Integrating Oracle Identity Manager with Oracle Access Manager Using the idmConfigTool," your configuration must reflect the fact that your Oracle Identity Manager components are in are in a different domain from your Access Manager components. The following changes are required:
-
When you create the properties file
oimitg.propsin Step 2, use the following contents instead of the contents shown in Section 12.23.4:LOGINURI: /${app.context}/adfAuthentication LOGOUTURI: /oamsso/logout.html AUTOLOGINURI: None ACCESS_SERVER_HOST: IDMHOST1.mycompany.com ACCESS_SERVER_PORT: 5575 ACCESS_GATE_ID: Webgate_IDM COOKIE_DOMAIN: .mycompany.com COOKIE_EXPIRY_INTERVAL: 120 OAM_TRANSFER_MODE: simple WEBGATE_TYPE: ohsWebgate11g SSO_ENABLED_FLAG: true IDSTORE_PORT: 389 IDSTORE_HOST: IDSTORE.mycompany.com IDSTORE_DIRECTORYTYPE: OUD, OID or OVD IDSTORE_ADMIN_USER: cn=oamLDAP,cn=Users,dc=mycompany,dc=com IDSTORE_USERSEARCHBASE: cn=Users,dc=mycompany,dc=com IDSTORE_GROUPSEARCHBASE: cn=Groups,dc=mycompany,dc=com IDSTORE_LOGINATTRIBUTE: uid MDS_DB_URL: jdbc:oracle:thin:@(DESCRIPTION=(LOAD_BALANCE=on)(FAILOVER=on)(ADDRESS_LIST=(ADDRESS=(protocol=tcp)(host=OIDDBHOST1-VIP.mycompany.com)(port=1521))(ADDRESS=(protocol=tcp)(host=OIDDBHOST2-VIP.mycompany.com)(port=1521)))(CONNECT_DATA=(SERVER=DEDICATED)(SERVICE_NAME=OIDEDG.mycompany.com))) MDS_DB_SCHEMA_USERNAME: edg_mds OIM_MANAGED_SERVER_NAME: WLS_OIM1 WLSADMIN: weblogic WLSPORT: 7101 WLSHOST: OIMADMINVHN.mycompany.com OAM11G_WLS_ADMIN_HOST: ADMINVHN.mycompany.com OAM11G_WLS_ADMIN_PORT: 7001 OAM11G_WLS_ADMIN_USER: weblogic DOMAIN_NAME: OIMDomain DOMAIN_LOCATION: ASERVER_HOMEAdditional and changed values, relative to those in Step 2 of Section 12.23.4, are shown in bold. The property definitions are the same, with one addition:
OAM11G_WLS_ADMIN_HOST,OAM11G_WLS_ADMIN_PORTandOAM11G_WLS_ADMIN_USERspecify the details of the OAM Domain if your Oracle Identity Manager components are in a separate domain from your Access Manager components. -
When the script runs, you are prompted for information, as described in Step 3. When Access Manager and Oracle Identity Manager are in separate domains, you are also prompted for:
Access Manager domain user password
-
At the end of the procedure in Section 12.23.4, restart the WebLogic Administration Servers on both of the domains.
16.8.8 Backing Up Oracle Identity Manager
When performing a backup after configuring Oracle Identity Manager, back up the OIMDomain as well as the IDMDomain. See Section 17.6.3, "Performing Backups During Installation and Configuration."
16.9 Additional Single Sign-On Requirements
When performing a backup after configuring Single Sign-On, back up the OIMDomain as well as the IDMDomain. See Section 17.6.3, "Performing Backups During Installation and Configuration."
16.10 Additional Node Manager Requirements
In Section 13.3.1, "Generating Self-Signed Certificates Using the utils.CertGen Utility," Step 4, when you run the utils.CertGen tool, create an additional certificate on OIMADMINVHN.mycompany.com. For example
java utils.CertGen Key_Passphrase OIMADMINVHN.mycompany.com_cert OIMADMVHN.mycompany.com_key domestic OIMADMINVHN.mycompany.com
Also perform the steps in Section 13.3.2, "Creating an Identity Keystore Using the utils.ImportPrivateKey Utility," for OIMADMINVHN.mycompany.com.
16.11 Additional Management Requirements
Perform the following additional management tasks when you are using a split domain topology.
This section contains the following topics:
16.11.1 Applying Patches
Section 17.7.2, "Patching Identity and Access Management," describes how to patch Identity and Access management in a single domain topology.
In a split domain topology, where Oracle Identity Manager is located in a domain separate from other components, apply patches as follows:
-
Common patches
-
Oracle Access Manager Patches
-
IDM Tool Patches
-
Common patches
-
Oracle Identity Manager Patches
-
IDM Tool Patches
-
Common patches
-
Oracle Internet Directory Patches
-
Oracle Virtual Directory Patches
It is not necessary to stop processes in the IDMDomain while applying patches to the OIMDomain. Similarly, it is not necessary to stop processes in the OIMDomain while applying patches to the IDMDomain.
16.11.2 Performing Backups
When performing a backup after creating a domain, configuring Oracle Identity Manager, and configuring Single Sign-On, back up the OIMDomain as well as the directories in the IDMDomain. See Section 17.6.3, "Performing Backups During Installation and Configuration."