6 Migrating Sun Java System Access Manager 7.1 Environments
This chapter describes how to migrate Sun Java System Access Manager 7.1 to Oracle Access Management Access Manager (Access Manager) 11g Release 2 (11.1.2.2.0).
The chapter contains the following sections:
-
Section 6.7, "Installing Oracle Identity and Access Management 11.1.2.2.0"
-
Section 6.13, "Migrating the Artifacts of Sun Java System Access Manager 7.1 to OAM 11.1.2.2.0"
6.1 Migration Overview
This section introduces two tools that are used in the process of migrating Sun Java System Access Manager 7.1 to Access Manager 11.1.2.2.0.
The OpenSSO Agent assessment tool reads the agents and policies from the Sun Java System Access Manager 7.1 server, analyzes the agents and the policy elements which can be migrated to Access Manager 11.1.2.2.0, and generates an assessment report. The generated report provides the information on whether the agents can be migrated or not, and whether the policies can be manually migrated, auto-migrated, or semi-migrated based on the Access Manager 11.1.2.2.0 policy model.
Assessment tool reads and shows information about Sun Java System Access Manager 7.1 agent profile, policies, user stores, and authentication stores. It assesses what data can be migrated to Access Manager 11.1.2.2.0 and what cannot be migrated to Access Manager 11.1.2.2.0 based on the understanding of the supported artifacts in Access Manager 11.1.2.2.0.
You can use the assessment tool to generate assessment report more than once before you can migrate the Sun Java System Access Manager 7.1 environment.
The Migration tool migrates the following artifacts of Sun Java System Access Manager 7.1 to Access Manager 11.1.2.2.0:
-
Agents configuration
-
Policies
-
User store configuration
-
Authentication store configuration
Note:
The migration tool and assessment tool do not support connection with configuration store over SSL port.
For more information about other migration scenarios, see Section 1.2, "Migration and Coexistence Scenarios".
6.2 Modes of Migration
This section describes the three modes of migration that you can perform using the procedure described in this chapter. The following are the two modes of migration:
6.2.1 Complete Migration
Complete migration migrates all compatible agents, policies, user stores, and authentication stores of Sun Java System Access Manager 7.1 to Access Manager 11.1.2.2.0. The migration that you perform for the first time will be a complete migration. After the first migration, each next run will be delta migration. Complete migration can be performed only once, and only for the first time.
The fresh migration sets the migration version in the Access Manager 11.1.2.2.0 configuration store through the migration framework.
To perform a complete migration, follow the procedure described in Migration Roadmap.
Note:
If the complete migration fails, you must manually clean up the partially migrated data, before you start performing the complete migration again.
6.2.2 Incremental Migration
Incremental Migration is referred to as Selective Migration, as you can select the agents and polices of Sun Java System Access Manager 7.1 that you wish to migrate to Access Manager 11.1.2.2.0. You can perform this migration multiple times with different sets of agents and policies, and therefore it is called Incremental Migration. Selecting only the user stores or authentication stores for incremental migration is not supported. When you select the agents and policies for incremental migration, you must also select the respective user stores and authentication stores.
Note:
You can perform Incremental Migration after performing Complete Migration, which will be referred to as Incremental Delta.
You can perform a Complete Migration after multiple Incremental Migration. In this case, the Complete Migration ignores the agents and policies that are already migration as part of the previous Incremental Migrations.
When you perform multiple Incremental Migrations by selecting the artifacts (agents and policies) that are already migrated, those artifacts are ignored, and the Incremental Migration migrates only the non-migrated artifacts.
6.2.3 Delta Migration
Delta migration is a mode of migration where you can migrate the newly added artifacts (agents, policies, user stores, and authentication stores) of Sun Java System Access Manager 7.1 to Access Manager 11.1.2.2.0. Delta migration is supported only for creation operations.
After the first round of migration (that is a complete migration), every migration that you perform is delta migration.
Each time you perform delta migration, information about the migration version set by the complete migration in the Access Manager 11.1.2.2.0 configuration store is retrieved, is incremented by one, and is saved back to Access Manager 11.1.2.2.0 configuration store.
The procedure to perform delta migration is same as that of a complete migration, and is described in Migration Roadmap.
6.3 Migration Summary
This sections summarizes the artifacts of Sun Java System Access Manager 7.1 that are compatible with Access Manager 11.1.2.2.0. This section contains the following topics:
6.3.1 Summary of Migration of Agents
This section summarizes the migration of agents from Sun Java System Access Manager 7.1 to Access Manager 11.1.2.2.0.
-
This migration tool migrates the agent configuration and not the agent itself. The Web Agent 2.2 supported for migration is Sun Java System Web Server 7.0.
-
Local agents are migrated with minimal configuration. Local agents are the agents that work in local configuration mode. These agents honor the local configuration file only for their own configuration. Only the basic configuration properties like agent ID, agent password, agent base URL of the local agents are stored in the Sun Java System Access Manager 7.1 server. After migration, these configuration details are stored in the Access Manager 11.1.2.2.0 Server.
-
Agent migration has the backward compatibility.
-
If two or more agents exist with the same name under different realms, the agents are migrated with the name preceded by the realm name.
For example: If the agent named
j2eeAgentexists in bothTopRealm(/) andSubRealm(/>SubRealm), then these agents are migrated with the nameTopRealm_j2eeAgentandSubRealm_j2eeAgent.
6.3.2 Summary of Migration of Policies
This section summarizes the migration of policies from Sun Java System Access Manager 7.1 to Access Manager 11.1.2.2.0.
Sun Java System Access Manager 7.1 policies consist of the following four artifacts:
-
Rules (resources + actions)
-
Subjects
-
Conditions
-
Response Providers
The policies in the assessment report (PolicyInfo.txt), which is generated when you run the OpenSSO Agent assessment tool, are classified into Auto Policies, Semi Policies, and Manual Policies based on the compatibility of the artifacts in Access Manager 11.1.2.2.0:
-
Auto Policies: A policy is regarded as auto policy if all the artifacts of that policy can be mapped to the policy artifacts in Access Manager 11.1.2.2.0. All the auto policies can be migrated to Access Manager 11.1.2.2.0.
-
Semi Policies: A policy is regarded as semi policy if some of the artifacts of that policy can be mapped to the policy artifacts in Access Manager 11.1.2.2.0. Semi policies are not migrated to Access Manager 11.1.2.2.0.
-
Manual Policies: A policy is regarded as manual policy if none of the artifacts of that policy can be mapped to the policy artifacts of Access Manager 11.1.2.2.0. Manual policies are not migrated to Access Manager 11.1.2.2.0.
Sun Java System Access Manager 7.1 has two types of policies:
-
Referral Policies: These policies do not apply to migration.
-
Non-Referral Policies: These policies are migrated.
-
A Sun Java System Access Manager 7.1 policy without a rule is not supported for migration. Such policy is considered invalid.
-
Rules that have the actions
GETandPOSTare only applicable for migration. These rules have the service type asURL Policy Agent. -
Rules with other service types such as
Discovery Servicethat has the actionsLOOKUPandUPDATE, and service typeLiberty Personal Profile Servicethat has the actionsQUERYandMODIFYare not applicable for migration because these actions (which are known as resource operations in Access Manager 11.1.2.2.0) are not supported in Access Manager 11.1.2.2.0.
Only the subject type AM Identity Subject (user and group) and Authenticated Users are supported for migration. These subjects are migrated as part of Identity Condition in Access Manager 11.1.2.2.0.
-
Active Session Time
-
This condition of Sun Java System Access Manager 7.1 policy is mapped to the attribute
Session Expiry Timeof the AttributeCondition in Access Manager 11.1.2.2.0. -
The attribute
Terminate sessionof this condition is ignored during migration as the appropriate mapping of this attribute does not exist in Access Manager 11.1.2.2.0.
-
-
Authentication by Module Instance
-
This condition of Sun Java System Access Manager 7.1 policy is migrated to Access Manager 11.1.2.2.0 as
AuthNscheme, and not as a condition. -
Table 6-1 lists the authentication modules of Sun Java System Access Manager 7.1 that are migrated and mapped with the
AuthNscheme into Access Manager 11.1.2.2.0.
-
-
Authentication Level (less than or equal to) and Authentication Level (greater than or equal to)
-
Both the conditions of Sun Java System Access Manager 7.1 policy are mapped to the session attributes of the
AttributeConditionwith namespaceSESSIONand attribute nameAuthentication Level. -
Both the conditions are mapped to the AttributeOperator
EQUALS, as Access Manager 11.1.2.2.0 does not have corresponding mapping forgreater then or equal toandless than or equal to. This mapping is done because of theequalsfactor in the policy condition in Sun Java System Access Manager 7.1. Therefore, both the conditionsgreater then or equal toandless than or equal toare similar in Access Manager 11.1.2.2.0.For example, if you migrate a Sun Java System Access Manager 7.1 policy with a condition of authentication level
less than or equal to 5, the migrated policy in Access Manager 11.1.2.2.0 will have the authentication levelequal to 5.
-
-
Current Session Properties
-
This condition is mapped to the session attributes of the AttributeCondition with namespace
SESSIONand attribute nameOther, where the key/value will be added as attributes of this condition. This condition in Sun Java System Access Manager 7.1 is multi-valued. Therefore, this condition in Access Manager 11.1.2.2.0 has multiple attributes with same name but different values.
-
-
Identity Membership
-
This condition in Sun Java System Access Manager 7.1 policy is mapped to
Identity conditionin Access Manager 11.1.2.2.0. -
All the unique users or groups from all the subjects, and all the unique users or groups from all the identity membership conditions in Sun Java System Access Manager 7.1 are created as a set of users or groups in one Identity condition in Access Manager 11.1.2.2.0.
-
During run-time verification, the ORing is performed between this set of users or groups
-
-
IP Address/DNS Name
-
The condition
IP Addressin Sun Java System Access Manager 7.1 policy is mapped toIP conditionin Access Manager 11.1.2.2.0. -
The condition
DNS nameis not supported in Access Manager 11.1.2.2.0.
-
-
LDAP Filter Condition
-
This condition in Sun Java System Access Manager 7.1 policy is mapped to
Identity conditionin Access Manager 11.1.2.2.0. -
All the unique LDAP filters from all the LDAP filter conditions in Sun Java System Access Manager 7.1 are created as a set of LDAP filters in one Identity condition in Access Manager 11.1.2.2.0.
-
-
Time (day, date, time, and time zone)
-
This condition in Sun Java System Access Manager 7.1 policy is mapped to
Time conditionin Access Manager 11.1.2.2.0. -
The
Timecondition in Sun Java System Access Manager 7.1 contains one of the following values: date, time, day, or time zone; whereas theTimecondition in Access Manager 11.1.2.2.0 contains either time or day. Therefore, theTimecondition in Sun Java System Access Manager 7.1 containing only the time (start and end time) and day can be mapped to theTimecondition in Access Manager 11.1.2.2.0. All the other cases are ignored.
-
-
Sun Java System Access Manager 7.1 Server or Policy Server sends Identity or User repository attributes (that is, user attributes from any user store) to the agent as response providers. The OpenSSO agent sends these attributes back to the resource or application via Http header, request attribute, or Http cookie according to the configuration of the agent.
All of the response providers (static as well as dynamic) are migrated from Sun Java System Access Manager 7.1 to Access Manager 11.1.2.2.0 with the type Http header.
6.3.3 Summary of Migration of User Stores
This section summarizes the migration of user stores from Sun Java System Access Manager 7.1 to Access Manager 11.1.2.2.0.
OpenSSO Enterprise has three types of user stores:
-
Active Directory: This user store can be migrated to Access Manager 11.1.2.2.0.
-
Generic LDAPv3: This user store can be migrated to Access Manager 11.1.2.2.0.
-
Sun DS with OpenSSO schema: This user store cannot be migrated to Access Manager 11.1.2.2.0, as no supported data store type is available in 11.1.2.2.0.
6.3.4 Summary of Migration of Authentication Stores
This section summarizes the migration of authentication stores from Sun Java System Access Manager 7.1 to Access Manager 11.1.2.2.0.
The following are the authentication stores in Sun Java System Access Manager 7.1 that can be migrated and mapped to the corresponding authentication modules in Access Manager 11.1.2.2.0:
-
LDAP in Sun Java System Access Manager 7.1 is mapped to OAM LDAP in Access Manager 11.1.2.2.0.
-
Certificate in Sun Java System Access Manager 7.1 is mapped to X509 in Access Manager 11.1.2.2.0.
-
Windows Desktop SSO in Sun Java System Access Manager 7.1 is mapped to Kerberos Access Manager 11.1.2.2.0.
All authentication stores with type LDAP are migrated to Access Manager 11.1.2.2.0 with name AS_RealmName_Modulename. The authentication stores with type other than LDAP are not migrated.
6.4 Topology Comparison
Figure 6-1 compares the topologies of Sun Java System Access Manager 7.1 and Access Manager 11.1.2.2.0.
Figure 6-1 Sun Java System Access Manager 7.1 and Access Manager 11.1.2.2.0 Topologies
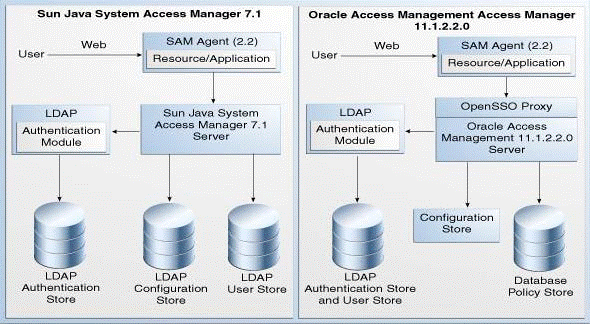
Description of "Figure 6-1 Sun Java System Access Manager 7.1 and Access Manager 11.1.2.2.0 Topologies"
6.5 Migration Roadmap
Table 6-2 lists the steps to migrate Sun Java System Access Manager 7.1 to Access Manager 11.1.2.2.0.
| Task No | Task | For More Information |
|---|---|---|
|
1 |
Complete the prerequisites. |
|
|
2 |
Install Oracle Identity and Access Management 11.1.2.2.0. |
See, Installing Oracle Identity and Access Management 11.1.2.2.0 |
|
3 |
Configure Oracle Access Management Access Manager 11.1.2.2.0. |
|
|
4 |
Generate the assessment report, and analyze what artifacts can be migrated to Access Manager 11.1.2.2.0. You can perform this task multiple times. |
|
|
5 |
Start the WebLogic Administration Server. |
|
|
6 |
If you wish to perform Incremental Migration, complete the additional steps. |
|
|
7 |
Create the properties file. |
|
|
8 |
Migrate Sun Java System Access Manager 7.1 to Access Manager 11.1.2.2.0 by running the migration tool. |
See, Migrating the Artifacts of Sun Java System Access Manager 7.1 to OAM 11.1.2.2.0 |
|
9 |
Complete the post-migration steps. |
|
|
10 |
Verify the migration. |
6.6 Prerequisites for Migration
You must complete the following prerequisites for migrating Sun Java System Access Manager 7.1 to Access Manager 11.1.2.2.0:
-
Read the system requirements and certification documents to ensure that your environment meets the minimum requirements for the products you are installing.
-
Oracle Fusion Middleware System Requirements and Specifications
This document contains information related to hardware and software requirements, minimum disk space and memory requirements, and required system libraries, packages, or patches.
-
Oracle Fusion Middleware Supported System Configurations
This document contains information related to supported installation types, platforms, operating systems, databases, JDKs, and third-party products.
-
For interoperability and compatibility issues that may arise when installing, refer to Oracle Fusion Middleware Interoperability and Compatibility Guide.
This document contains important information regarding the ability of Oracle Fusion Middleware products to function with previous versions of other Oracle Fusion Middleware, Oracle, or third-party products. This information is applicable to both new Oracle Fusion Middleware users and existing users who are upgrading their existing environment.
Note:
For information about Oracle Fusion Middleware concepts and directory structure, see "Understanding Oracle Fusion Middleware Concepts and Directory Structure" in the Oracle Fusion Middleware Installation Planning Guide for Oracle Identity and Access Management.
-
-
Verify that the Sun Java System Access Manager version that you are using is supported for migration. For information about supported starting points for Sun Java System Access Manager 7.1 migration, see Section 1.4, "Supported Starting Points for Migration and Coexistence".
6.7 Installing Oracle Identity and Access Management 11.1.2.2.0
As part of the migration process, you must freshly install Oracle Identity and Access Management 11.1.2.2.0 This 11.1.2.2.0 installation can be on the same machine where Sun Java System Access Manager 7.1 is installed, or on a different machine.
For more information about installing Oracle Identity and Access Management 11.1.2.2.0, see "Installing Oracle Identity and Access Management (11.1.2.2.0)" in the Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management.
6.8 Configuring Oracle Access Manager 11.1.2.2.0
After you install Oracle Identity and Access Management 11.1.2.2.0, you must configure Access Manager 11.1.2.2.0 in a domain.
For more information about configuring Access Manager 11.1.2.2.0, see "Configuring Oracle Access Management" in the Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management.
6.9 Generating the Assessment Report
This section describes how to generate an assessment report using the OpenSSO Agent assessment tool. The assessment report provides a preview of agents, policies, user stores, and authentication stores that are available in the Sun Java System Access Manager 7.1 deployment, and indicates which artifacts can be migrated to Access Manager 11.1.2.2.0.
You can generate an assessment report more than once before you can start the migration process.
This section includes the following topics:
Note:
Before you run the assessment tool, you must complete the following prerequisites:
-
Start the container on which Access Manager 7.1 is deployed.
-
Make sure that you use 1.6 or higher version of JDK.
-
Set the variable
JAVA_HOMEto the appropriate location where JDK 1.6 is installed.
6.9.1 Obtaining the Tool
Move from your present working directory to the location IAM_HOME/oam/server/tools/opensso_assessment using the following command:
On UNIX:
cd IAM_HOME/oam/server/tools/opensso_assessment/
On Windows:
cd IAM_HOME\oam\server\tools\opensso_assessment\
Extract the contents of the OpenssoAgentdiscTool.zip folder to a directory of your choice. It is recommended that you use the name OpenssoAgentdiscTool to the unzipped folder.
6.9.2 Specifying LDAP Connection Details
You must specify LDAP connection details in the properties file before you run the assessment tool by doing the following:
-
Open the
OpenSSOAgentDiscTool.propertiesfile from the following location:On UNIX:
unzipped_folder/resources/On Windows:
unzipped_folder\resources\ -
Set the appropriate values for the following properties:
-
openSSOLDAPServerURL=host:portIn this property,
hostandportrefer to the LDAP host and the port of the configuration store used in Sun Java System Access Manager 7.1. -
openSSOLDAPBindDN=login_idwhere
login_idis the bind DN of the LDAP server. You must have the administrative or root permissions to the configuration directory server of Sun Java System Access Manager 7.1. -
openSSOLDAPSearchBase=LDAP_search_basewhere
LDAP_search_baseis LDAP search base for the configuration store.
-
-
Save the file, and close.
Note:
If you do not specify the LDAP connection details, a message will be displayed in the UserStoresInfo.txt and AuthnStoreInfo.txt files. This message indicates that the information is not available. The same message will be displayed in the user stores and authentication stores sections in DashBoardInfo.txt file. You must then specify the right LDAP connection details in the OpenSSOAgentDiscTool.properties file, save the file, and run the assessment tool again.
If you specify any incorrect value for any of these parameters, you cannot run the assessment tool, and error is displayed accordingly.
6.9.3 Updating the Agent Profile of 2.2 Agents
Before you run the OpenSSO Agent assessment tool, you must update the agent profiles of 2.2 agents that you wish to migrate, with the appropriate values for the attributes agentRootURL and type of the agent under Agent Key Values(s). To do this, complete the following steps:
-
Log in to the Sun Java System Access Manager 7.1 administration console using the following URL:
http://host:port/amserver
-
Go to the Access Control tab, and click the realm under which the 2.2 agent is installed.
-
Go to the Subjects tab, and click the Agent tab.
-
Click on the link for the agent to be migrated.
-
Under Agent Key Value(s), if the values for the attributes
agentRootURLandTypeare not already present, enter these attributes with the appropriate values in the following format in the New Value field.agentRootURL=agent_webcontainer_URLType=WebAgent/J2EEAgentNote:
The above keys and values are case-sensitive.
Click Add after typing each attribute.
-
Click Save.
6.9.4 Running the OpenSSO Agent Assessment Tool
To run the OpenSSO Agent assessment tool, do the following:
-
Change your directory to the folder where you extracted the contents to, as described in Section 6.9.1, "Obtaining the Tool", using the following command:
cd <path to the unzipped folder>
-
Run the following command:
java -jar openssoagentdisc.jar <sam server URL> <username> <debugLevel>
where
<sam server URL>is the URL of the Sun Java System Access Manager 7.1 Server. You must specify it in the format:http://<host>:<port>/amserverwhere,<host>and<port>refer to hostname and port of the machine on which Sun Java System Access Manager 7.1 Server is running.<username>is the username of the Sun Java System Access Manager 7.1 Server<debugLevel>is optional. The value of this argument should be eithererrorormessage. If you do not specify this argument in the command, it takes the default valueerror.You are prompted to enter the following:
-
Enter server login password:Enter the password of the Sun Java System Access Manager 7.1 server admin user. This user is typically the amadmin.
-
Enter LDAP login password:Enter the login password of the LDAP server.
Note:
For more information about the arguments used in this command, run the following command in the unzipped directory:
java -jar openssoagentdisc.jar -help
-
6.9.5 Analyzing the Assessment Report
The assessment tool generates five Comma Separated Values (CSV) files in the following location:
unzipped_folder/consoleOutput/
These reports contain the information about agents, policies, user stores, and authentication stores of Sun Java System Access Manager 7.1 that are supported in Access Manager 11.1.2.2.0.
Table 6-3 lists the CSV files that are generated when you run the assessment tool.
Table 6-3 Report Files Generated
| File | Description |
|---|---|
|
|
This file contains information about the J2EE and web agents that are registered with Sun Java System Access Manager 7.1, and the list of agents supported in Access Manager 11.1.2.2.0. |
|
|
This file contains information about authentication stores. |
|
|
Contains brief information about agents, policies, user stores, and authentication stores. |
|
|
Contains information about policies. |
|
|
Contains information about user stores. |
Note:
You can open the CSV files directly as CSV or using Microsoft Excel. The data in the report is displayed in the hierarchical structure with realm or subrealm name at the top followed by the data related to agents, policies, authentication stores, and user stores.
6.10 Starting the WebLogic Administration Server
You must start the WebLogic Administration Server before you can run the migration tool.
To start the Administration Server, do the following:
On UNIX:
-
Move from your present working directory to the
MW_HOME/user_projects/domains/domain_name/bindirectory using the command:cd MW_HOME/user_projects/domains/domain_name/bin/
-
Run the following command:
startWebLogic.sh
When prompted, enter the username and password of the WebLogic Administration Server.
On Windows:
-
Move from the present working directory to the
MW_HOME\user_projects\domains\domain_name\bindirectory using the following command on the command line:cd MW_HOME\user_projects\domains\domain_name\bin\
-
Run the following command:
startWebLogic.cmd
When prompted, enter the username and password of the WebLogic Administration Server.
6.11 Additional Steps for Incremental Migration
This section describes additional steps to be completed if you wish to perform Incremental Migration. For other modes of migration like Complete and Delta Migration, ignore this section.
When you generate the assessment report (as described in Generating the Assessment Report), a file called IncrementalMigrationIncludeFile.txt is generated at the location AssessmentToolUnzippedFolder/consoleOutput/. The content of this file is as follows:
REALM#TopRealm##AGENT#j2eeAgent_1##N
REALM#TopRealm##AGENT#j2eeAgent_2##N
REALM#TopRealm##POLICY#Policy1##N
REALM#TopRealm##POLICY#Policy2##N
Each line contains the realm name, name of the agent or policy of Sun Java System Access Manager 7.1, and the flag which is set to N by default. The flag value Y stands for 'Yes', and N stands for 'No'. The flag specified indicates whether an agent or policy is included or excluded in the Incremental Migration.
Note:
The above values are case-insensitive.
If you wish to include some of the agents and policies in the Incremental Migration, set the flag of the those agents and policies to Y in the IncrementalMigrationIncludeFile.txt file. Also, specify the absolute path of this file for the property openSSOSMIncludeFilePath in the properties file that you create in the Section 6.12, "Creating the Properties File". This includes all the agents and policies in the migration whose flags are set to Y.
Note:
If the content of IncrementalMigrationIncludeFile.txt file is empty, and if you specify the absolute path of this file for the property openSSOSMIncludeFilePath in the properties file, no artifacts of Sun Java System Access Manager 7.1 will be migrated to Access Manager 11.1.2.2.0.
If you wish to exclude some of the agents and policies from the Incremental Migration, set the flag of the those agents and policies to Y in the IncrementalMigrationIncludeFile.txt file. Also, specify the absolute path of this file for the property openSSOSMExcludeFilePath in the properties file that you create in the Section 6.12, "Creating the Properties File". This excludes all the agents and policies from the migration whose flags are set to Y.
Note:
If the content of IncrementalMigrationIncludeFile.txt file is empty, and if you specify the absolute path of this file for the property openSSOSMExcludeFilePath in the properties file, all the artifacts of Sun Java System Access Manager 7.1 will be migrated to Access Manager 11.1.2.2.0, which in turn is a complete migration.
6.12 Creating the Properties File
Create a properties file at any accessible location. For example, create a properties file by name oam_migration.properties.
Enter the right values for the following properties in the properties file:
-
openSSOServerURL=SAM_server_URL -
openSSOAdminUser=SAM_admin_username -
openSSOAdminPassword= -
openSSOServerDebugLevel=error/message -
openSSOLDAPServerURL=LDAP host:port -
openSSOLDAPBindDN=LDAP_bind_DN -
openSSOLDAPBindPwd= -
openSSOLDAPSearchBase=LDAP_searchBase -
openSSOMigrationMode=Complete/Incremental -
openSSOSMIncludeFilePath=absolute_path_to_include_file -
openSSOSMExcludeFilePath=absolute_path_to_exclude_file
Table 6-4 describes the values you must specify for each of the properties in the properties file.
Table 6-4 Property File Values
| Property | Description |
|---|---|
|
|
Specify the URL of the Sun Java System Access Manager 7.1 Server. It must be specified in the format:
where
|
|
|
Specify the username of the Sun Java System Access Manager Administration Server. |
|
|
Do not specify any value for this property. The migration tool prompts you for the Sun Java System Access Manager admin password when you run the migration command, as described in step-4. |
|
|
Specify one of the following values:
This value represents the debug level. |
|
|
Specify the URL of the LDAP server. This must be specified in the format:
where
The |
|
|
Specify the bind DN of the LDAP server. This user must have the admin or root permissions to the configuration directory server of Sun Java System Access Manager. |
|
|
Do not specify any value for this property. The migration tool prompts you for the LDAP bind password when you run the migration command as described in step-4. |
|
|
Specify the LDAP search base for the configuration store. |
|
|
Specify the mode of migration by setting one of the following values for this property:
If you do not specify any value to this property, Complete Migration will be performed. Also, if there is a mistake in the value Note that these values are case sensitive. For more information about modes of migration, see Modes of Migration. |
|
|
If you wish to perform Incremental Migration and include some of the agents and policies of Sun Java System Access Manager 7.1 in the migration, you must use the The value of the If you wish to perform Incremental Migration with the If you specify both For complete migration, ignore this property. |
|
|
If you wish to perform Incremental Migration and exclude some of the agents and policies of Sun Java System Access Manager 7.1 from migration, you must use the The value of the If you wish to perform incremental migration with the If you specify both For complete migration, ignore this property. |
Note:
Do not specify any value for openSSOAdminPassword and openSSOLDAPBindPwd properties.
If the file path specified for openSSOSMExcludeFilePath or openSSOSMExcludeFilePath is incorrect, or if the provided file path is not readable due to permission issues, appropriate error message will be displayed. You can also view this in the log file.
If you perform Incremental Migration and IncrementalMigrationIncludeFile.txt file is empty, the mode changes to Complete, and Complete Migration is performed.
6.13 Migrating the Artifacts of Sun Java System Access Manager 7.1 to OAM 11.1.2.2.0
Before you start the actual migration of the artifacts from Sun Java System Access Manager 7.1 to Access Manager 11.1.2.2.0, make sure that you have generated the assessment report (as described in Section 6.9, "Generating the Assessment Report"), and analyzed what artifacts can be migrated to Access Manager 11.1.2.2.0.
To migrate Sun Java System Access Manager 7.1 to Access Manager 11.1.2.2.0, do the following:
-
If you wish to perform Incremental Migration, make sure you have completed the additional steps as described in Section 6.11, "Additional Steps for Incremental Migration".
-
Make sure you have created the properties file as described in Section 6.12, "Creating the Properties File".
-
Run the following command to launch the WebLogic Scripting Tool (WLST):
On UNIX:
-
Move from your present working directory to the
IAM_HOME/common/bindirectory by running the following command on the command line:cdIAM_HOME/common/bin -
Run the following command to launch the WebLogic Scripting Tool (WLST):
./
wlst.sh
On Windows:
-
Move from your present working directory to the
IAM_HOME\common\bindirectory by running the following command on the command line:cdIAM_HOME\common\bin -
Run the following command to launch the WebLogic Scripting Tool (WLST):
wlst.cmd
-
-
Run the following command to connect WLST to the WebLogic Server instance:
connect('wls_admin_username','wls_admin_password','t3://hostname:port');In this command,
wls_admin_usernameis the username of the WebLogic Administration Server.wls_admin_passwordis the password of the WebLogic Administration Server.hostnameis the machine where WebLogic Administration Server ia running.portis the Administration Server port -
Run the following command to migrate the artifacts of Sun Java System Access Manager 7.1 to Access Manager 11.1.2.2.0:
oamMigrate(oamMigrateType="OpenSSO",pathMigrationPropertiesFile="<absolute_path_of_properties_file>");
where
<absolute_path_of_properties_file>is the absolute path to the properties file that you created in step-1. For example:On UNIX:
oamMigrate(oamMigrateType="OpenSSO",pathMigrationPropertiesFile="abc/def/oam_migration.properties"On Windows:
oamMigrate(oamMigrateType="OpenSSO",pathMigrationPropertiesFile="abc\\def\\oam_migration.propertiesYou are prompted to enter the following:
-
Enter value for property : openSSOAdminPassword :Enter the password of the Sun Java System Access Manager 7.1 Administration Server.
-
Enter value for property : openSSOLDAPBindPwd :Enter the bind password of the LDAP server.
Note:
Complete migration is performed when you run
oamMigrate()command for the first time.After an initial migration (complete migration), you can re-execute this command to perform a delta migration.
For more information about complete and delta migration, see Section 6.2, "Modes of Migration".
-
When the migration is complete, the WLST console displays a message stating the result of the migration.
6.14 Performing Post-Migration Tasks
After you migrate Sun Java System Access Manager 7.1 to Access Manager 11.1.2.2.0, you must complete the following post-migration tasks:
-
This migration tool creates the
AMAgent.propertiesfile at the following location:<domain_home>/<domain_name>/output/OpenSSOMigration/AM7.1/<realm_name>/<agent_name>/AMAgent.propertiesYou must replace the
@DEBUG_LOGS_DIR@tag in theAMAgent.propertiesfile with the valid directory path to the debug logs on the agent host. To do this, complete the following steps:-
Open the
AMAgent.propertiesfile. -
In the property
com.sun.am.policy.agents.config.local.log.file =@DEBUG_LOGS_DIR@/amAgent, replace the tag@DEBUG_LOGS_DIR@with the valid directory path to the debug logs on the agent host.
-
-
You must back up the existing properties file, which is on the agent host, and copy the newly created
AMAgent.propertiesfile to the agent host. To do this, complete the following steps:-
Stop the agent web container instance.
-
Back up the existing properties file (that is the properties file which existed on the agent host before you started the migration process).
-
Copy the newly created
AMAgent.propertiesfile from the following location to the agent host:<domain_home>/<domain_name>/output/OpenSSOMigration/AM7.1/<realm_name>/<agent_name>/AMAgent.properties -
Start the agent web container instance.
After you do this, any access to a protected resource will redirect the user to the Access Manager 11.1.2.2.0 server for authentication.
-
-
The migration tool does not retrieve the passwords of the user stores that are migrated from Sun Java System Access Manager 7.1 to Access Manager 11.1.2.2.0. Therefore, after migration, you must manually update the passwords for all the user stores that are migrated. To do this, complete the following steps:
-
Log in to the Oracle Access Management 11.1.2.2.0 console using the following URL:
http://host:port/oamconsole
where
hostis the machine on which Access Manager 11.1.2.2.0 is running, andportis the port number. -
Go to the Launch Pad tab.
-
Click on User Identity Stores under the section Configuration. Manually update the password for all the migrated LDAP user stores that exist.
-
-
After migration, the minimum and maximum pool size for the migrated authentication stores will be set to 0, by default. Hence, you must manually set the appropriate values for Minimum Pool Size and Maximum Pool Size for the authentication stores in the Oracle Access Management 11.1.2.2.0 console. To do this, complete the following steps:
-
Log in to the Oracle Access Management 11.1.2.2.0 console using the URL:
http://host:port/oamconsole
-
Go to the Launch Pad tab.
-
Click on User Identity Stores under the section Configuration.
-
Select the authentication store to be edited.
-
Scroll down to Connection Details, and set the values Minimum Pool Size and Maximum Pool Size. For example, Minimum Pool Size=10 and Maximum Pool Size=50.
-
Click Apply.
-
-
Restart the Access Manager Managed Server(s) and the web container instances for the agents that you migrated, by completing the following steps:
-
Stop the web container instance for the migrated agent.
-
Stop the Access Manager Managed Server(s).
For information about stopping the Managed Server(s), see Appendix A, "Stopping the Managed Server(s)".
-
Start the Access Manager Managed Server(s).
For information about starting the Managed Server(s), see Appendix A, "Starting the Managed Server(s)".
-
Start the web container instance for the migrated agent.
-
6.15 Verifying the Migration
To verify the migration, do the following:
-
Log in to the Oracle Access Management 11.1.2.2.0 console using the following URL:
http://host:port/oamconsole
In this URL,
-
hostrefers to fully qualified domain name of the machine hosting the Oracle Access Management 11.1.2.2.0 console. -
portrefers to the designated bind port for the Oracle Access Management 11.1.2.2.0 console, which is the same as the bind port for the Administration Server.
Verify that the Sun Java System Access Manager 7.1 agents (2.2 agents), user stores, authentication stores, authentication modules, host identifiers, resources, policies with correct authentication scheme having correct authentication module are migrated to Access Manager 11.1.2.2.0.
-
-
Access any protected page using the URL. The URL now redirects you to the Oracle Access Management 11.1.2.2.0 Server login page. Upon successful authentication, it should perform a successful authorization and you should be able to access the resource successfully.