23.6 Tunneling from DCC to Access Manager Over Oracle Access Protocol
Access Manager supports HTTP communication over the Oracle Access Protocol (OAP). In this case, a WebGate configured as a DCC uses the ECC servlets for credential collection during Access Manager authentication.
The following sections contain more details.
Note:
For details on the DCC, see Embedded Credential Collector Versus Detached Credential Collector.
23.6.1 How DCC Tunneling with OAP Works
The tunneling process works for DCC WebGates only.
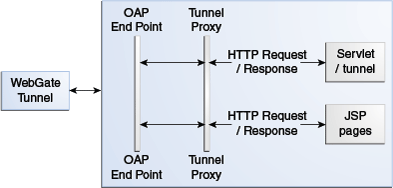
Figure 23-5 illustrates how the tunneling process works.
The following steps provide more details in regards to the OAP Tunneling process.
-
The URL to be tunneled is configured in the DCC WebGate profile.
-
This same URL is mapped to a servlet or JSP page in the Access Manager server.
-
On accessing the tunneled URL, the WebGate intercepts the HTTP request and converts it to an OAP request.
-
The OAP request is forwarded to the Access Manager server.
-
The Access Manager server (OAM proxy) receives the OAP request and passes it to the tunnel proxy.
-
The tunnel proxy will convert the OAP request to an HTTPServletRequest and invoke the corresponding servlet (or compiled servlet in the case of a JSP).
-
The response is converted back to an OAP message and passed to the OAP end point.
-
The OAM end point responds to the WebGate with the converted OAP message.
-
The WebGate converts the OAP message back to an HTTP response.
-
The WebGate provides the HTTP response to the caller (browser).
23.6.2 Configuring OAP Tunneling
To configure OAP Tunneling, a WebGate must be installed and configured to work with the Access Manager server as a DCC.
The Access Manager endpoint must be deployed on the Access Manager Server. After ensuring these prerequisites have been met, add a user-defined parameter to the WebGate profile that defines all URLs to be tunneled using the form TunneledUrls=<URL>,<URL1>. For example:
TunneledUrls=/oam,/sampleapp
Lastly, protect the Tunneled URLs with an Authentication Policy. For details, see Managing Authentication and Shared Policy Components.