52.3 Understanding OAuth Services Authorization for Mobile Clients
The Mobile OAuth Services authorization scenario supports mobile apps that run in a browser as well as device-native apps that do not use a browser or just use the browser during user authentication.
This scenario provides enhanced security support (in addition to the baseline security measures defined in the OAuth 2.0 specification) including:
-
Client apps must be registered with OAuth Services in the Identity Domain that your organization uses to manage Mobile OAuth Services clients.
-
Mobile applications must register with Oracle Access Management prior to using OAuth Services and each registration is specific to one app on the device. After the application registration, the mobile app will have a client token. It uses this token as the security credential for making Access Token requests. In comparison, the OAuth web client uses either a credential-like password or an assertion to identify itself.
-
This scenario supports user consent management. If consent management is enabled, the client app prompts the user to accept or decline the app's request to register with Access Manager.
Note:
This consent is controlled with the "Require User Consent for Client Registration" attribute under the Service Profiles. If set, the user will be asked to confirm app registration; if off, the user will not be asked. See Configuring Service Profiles.
-
Except for access tokens (and user tokens if server-side SSO is disabled), the server does not send security material, such as OAAM device and session handles to the client on the mobile device, but stores it in the Server-Side Device Store. Access tokens are both sent to the client and stored in the Server-Side Device Store to provide for validation and life cycle management.
-
The OAM server component can restrict token delivery to a specific app installed on a specific device by sending part of a token through HTTPS, and sending the other part through push notification using either the Apple Push Notification Service (APNS) or Google Cloud Messaging (GCM). Figure 52-2 illustrates this.
Figure 52-2 Using a Split Request to get a Client Verification Code
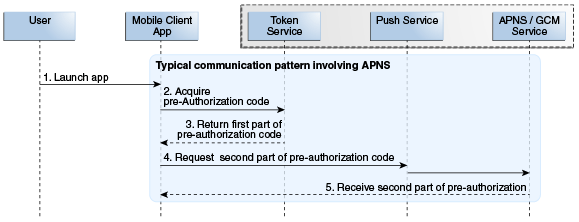
Description of "Figure 52-2 Using a Split Request to get a Client Verification Code"
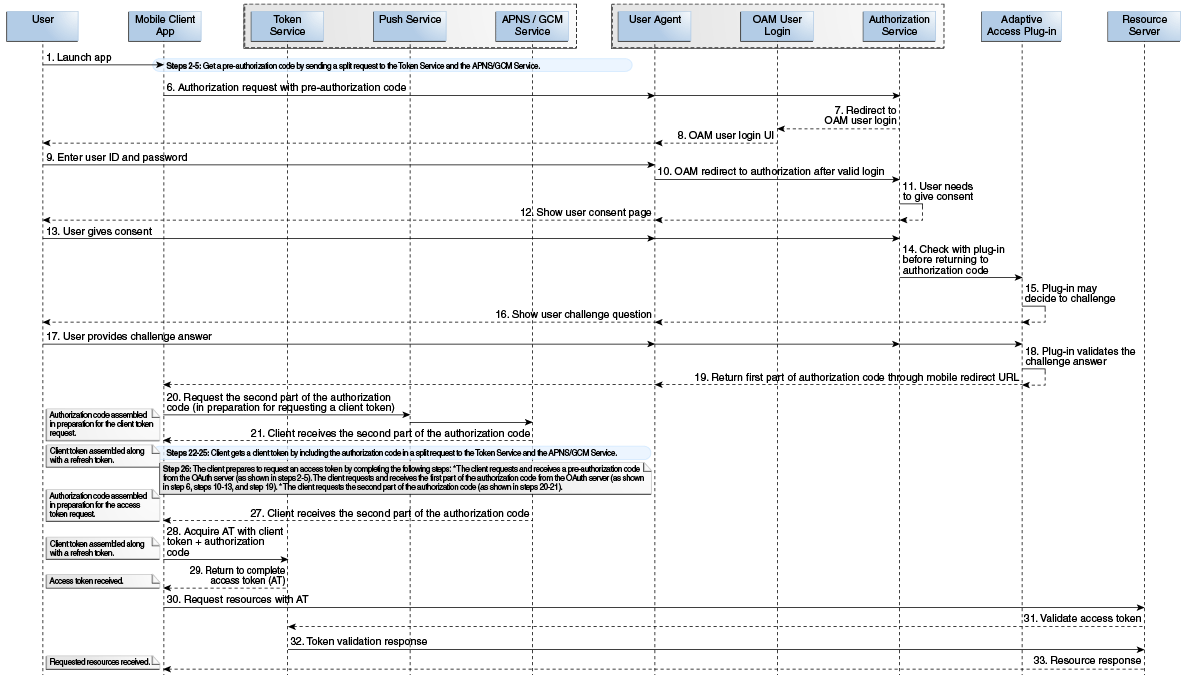
The following scenario describes the additional interactions that Oracle Access Management undertakes when authenticating with a mobile client. The process is illustrated in Figure 52-3.
-
The Resource Owner opens the Client mobile app.
An Oracle Access Management administrator has already registered this Client app as a Mobile OAuth Services Client.
-
The Mobile Client sends the client ID and the device token to OAuth Services and requests a client verification code.
-
OAuth Services returns half of the client verification code over HTTPS or HTTP.
See Figure 52-2. This behavior can be configured in the Mobile Service Settings section of the OAuth Services Profile configuration page.
-
If the security level is set to Advanced, all codes and tokens are returned using both HTTP and push notification.
-
If the security level is set to Standard mode, all codes and tokens are sent over HTTP only.
The rest of this scenario (beginning with step 4) contains details for when the security level is set to Advanced.
-
-
The Mobile client requests the second half of the client verification code from the OAuth Services push endpoint.
The push endpoint forwards the request to the APNS or the GCM service depending on the mobile device's operating system.
-
The APNS or GCM service sends the second half of the client verification code to the Client app.
-
The Mobile client requests an authorization code from OAuth Services by sending the client verification code and the device token.
-
OAuth Services redirects the request to Access Manager.
-
Access Manager sends a login page to the user-agent so that the user can log in.
-
The Resource Owner (user) enters a user ID and password.
-
Access Manager validates the login and redirects to OAuth Services.
-
OAuth Services is configured to obtain the user's approval to register the device. (It will not ask for the user's consent to register if Require User Consent for Client Registration is disabled on the OAuth Services Profile Configuration page.)
-
The consent page is sent to the Resource Owner.
-
The Resource Owner provides (or denies) consent.
-
OAuth Services checks the Oracle Adaptive Access Manager (OAAM) plug-in to determine if additional authentication steps are required.
-
The plug-in determines that an additional challenge question is required.
-
The OAAM challenge question is sent to the Resource Owner.
-
The Resource Owner provides the challenge answer which is forwarded to the OAAM plug-in.
-
The OAAM plug-in validates the challenge answer.
-
OAuth Services uses the mobile redirect URI to return half of the authorization code that the mobile app will need to request a client token.
-
The Mobile OAuth Services client requests the second half of the authorization code from OAuth Services push endpoint.
The push endpoint forwards the request to the APNS or GCM service.
-
The mobile client app receives the second half of the authorization code from the APNS or GCM service.
The mobile client app assembles the authorization code in preparation for requesting a client token.
-
After validating the authorization code, the Mobile OAuth client uses the code to request the first half of the client token from the OAuth Services token endpoint.
-
The token endpoint returns the first half of the client token to the mobile client.
-
The mobile client requests the second half of the client token from the OAuth Services push endpoint.
-
The APNS or GCM service sends the second half of the client token to the mobile client app.
The mobile client assembles the client token as well as a refresh token. The client can use the refresh token to request a new client token.
-
The mobile client prepares to request an access token by completing the following steps:
-
The Client requests and receives a client verification code from OAuth Services.
-
The Client requests and receives the first part of the authorization code from OAuth Services.
-
The resource owner does not need to log in if the user session is still valid.
-
User consent may be required based on the Resource Server scope to which the Client is requesting access.
-
The OAAM plug-in does not repeat its challenge.
-
The client requests the second part of the authorization code.
-
-
The APNS or GCM service returns the second half of the authorization code for the access token.
The Client assembles the authorization code in preparation for the access token request.
-
The mobile client requests an access token by sending the client token and the access token authorization code.
-
The token endpoint sends the access token to the client. This behavior depends on whether the Security Level setting in the Mobile Service Settings section of the OAuth Services Profile configuration page is set to Advanced or Standard.
-
The Mobile OAuth Services client requests access to the protected resources by sending the access token to the Resource Server.
-
The Resource Server validates the access token with the OAuth Services token service. The Resource Server can also validate the token locally. If the certificates are configured correctly, JWT token signing is verified at the Resource Server.
-
The OAuth Services token service sends a response to the Resource Server.
-
The Resource Server sends the requested resources to the mobile client.
Figure 52-3 The Complete Mobile App Authorization Request Flow
Description of "Figure 52-3 The Complete Mobile App Authorization Request Flow"