28.3 Understanding OpenSSO Agent Registration Parameters
Whether you migrate existing OpenSSO Agents to Access Manager or register a fresh OpenSSO Agent, the Oracle Access Management Console provides centralized registration and management of OpenSSO Agents.
28.3.1 OpenSSO Agent Registration Parameters
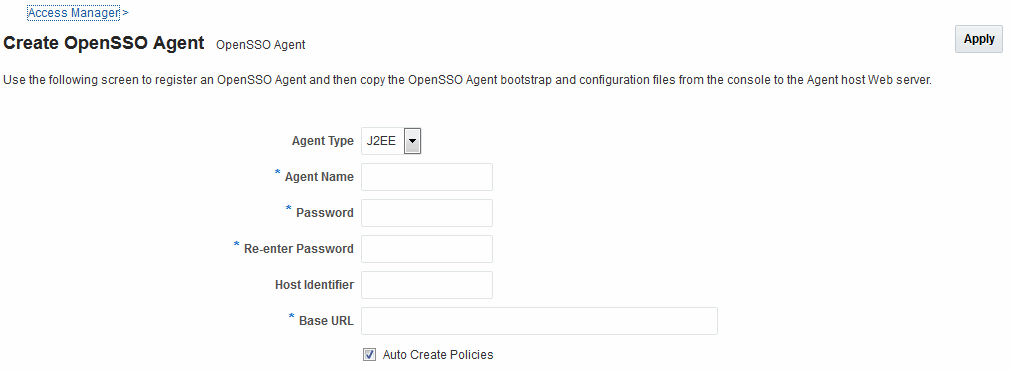
Administrators can enter information in the New OpenSSO Agent page during new OpenSSO agent registration.
Figure 28-2 shows the New OpenSSO Agent page.
Table 28-5 describes the elements on the New OpenSSO Agent page.
Table 28-5 Elements on the New OpenSSO Agent Page
| Element | Description |
|---|---|
|
Agent Type |
OpenSSO agent types can be either:
Note: Both agent types provide access protection when you also choose SSO only. |
|
Agent Name |
Unique name for this agent. |
|
Password Re-enter Password |
A required, unique password for this OpenSSO agent, which can be assigned during this registration process. The entry will appear in obfuscated format in the console, in oam-config.xml, and in OpenSSOAgentBootstrap.properties. When a registered agent connects to an OAM Server, the user is prompted for the password. The password is used for authentication to prevent unauthorized agents from connecting and obtaining policy information. |
|
Host Identifier |
A name that identifies the host and port for the OpenSSO agent. Default: Agent Name See Also: "About Virtual Web Hosting". |
|
Base URL |
The protocol, host, and port of the computer on which the OpenSSO agent is installed. For example, http://host.example.domain.com:port or https://example.domain.com:port. |
|
Auto Create Policies |
During agent registration, you can have authentication and authorization policies created automatically. This option is checked (enabled) by default. The agent name is used as the Application Domain name by default. Default: Enabled See Also: "Generated Artifacts: OpenSSO". Notes: An Application Domain in Access Manager corresponds to a Realm in OpenSSO. If you already have an Application Domain and policies, you can simply add new resources to it. If you clear this option (no check), no Application Domain or policies are generated automatically. |
OpenSSO Agent Properties
OpenSSO Agent properties are stored in the following files, which are updated during agent registration and configuration changes and consumed during run time:
-
OpenSSOAgentBootstrap.properties
-
OpenSSOAgentConfiguration.properties
These files are stored on the console host (AdminServer) and must be relocated to the OpenSSO Agent /config directory as shown in Table 28-6.
Table 28-6 Relocating OpenSSO Artifacts
| From AdminServer . . . | To OpenSSO Agent /config Directory |
|---|---|
|
$<MW_HOME>/Oracle_IDM1/oam/server/rreg/client/rreg/output |
$Policy-Agent-base/AgentInstance-Dir/config/ |
For details about the generated Application Domain for an Open SSO Agent, see "Generated Artifacts: OpenSSO".
28.3.2 The Expanded OpenSSO Agent Page and Parameters
The expanded OpenSSO Agent page is available when managing the agent using the Oracle Access Management Console. During registration, only a small subset of available parameters is displayed to streamline the process.
Whether you registered the agent using the Oracle Access Management Console or the remote registration utility, you can view the full agent configuration page in the console. Default values populate the page after initial registration and are displayed when you open the Agent's page, as shown in Figure 28-3.
Figure 28-3 Expanded OpenSSO Web Agent Registration Page
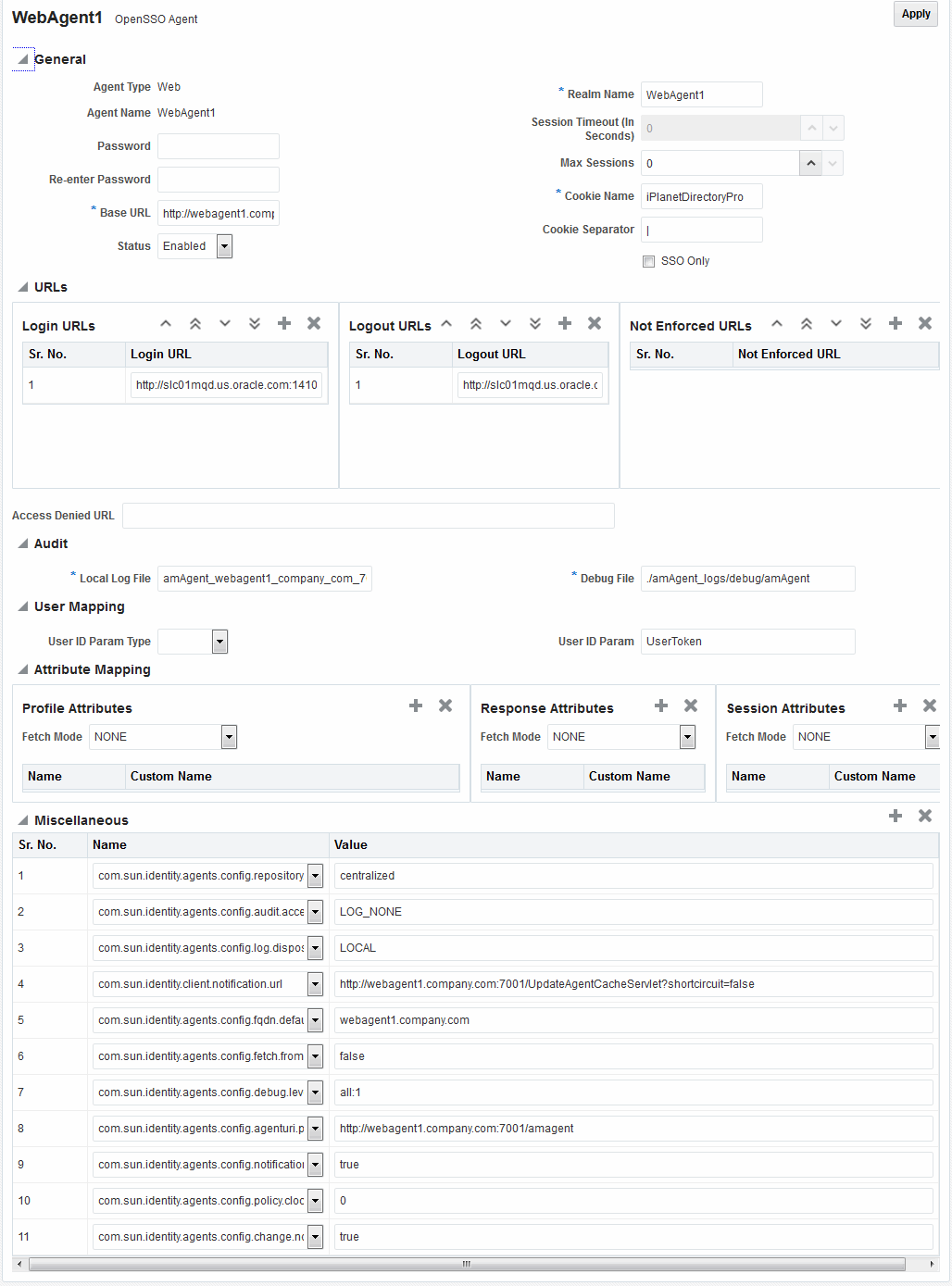
Description of "Figure 28-3 Expanded OpenSSO Web Agent Registration Page"
Information on the J2EE Agent registration page is nearly the same as details for Web Agents. The J2EE Agent registration page is shown in Figure 28-4.
Figure 28-4 Expanded OpenSSO J2EE Agent Registration Page
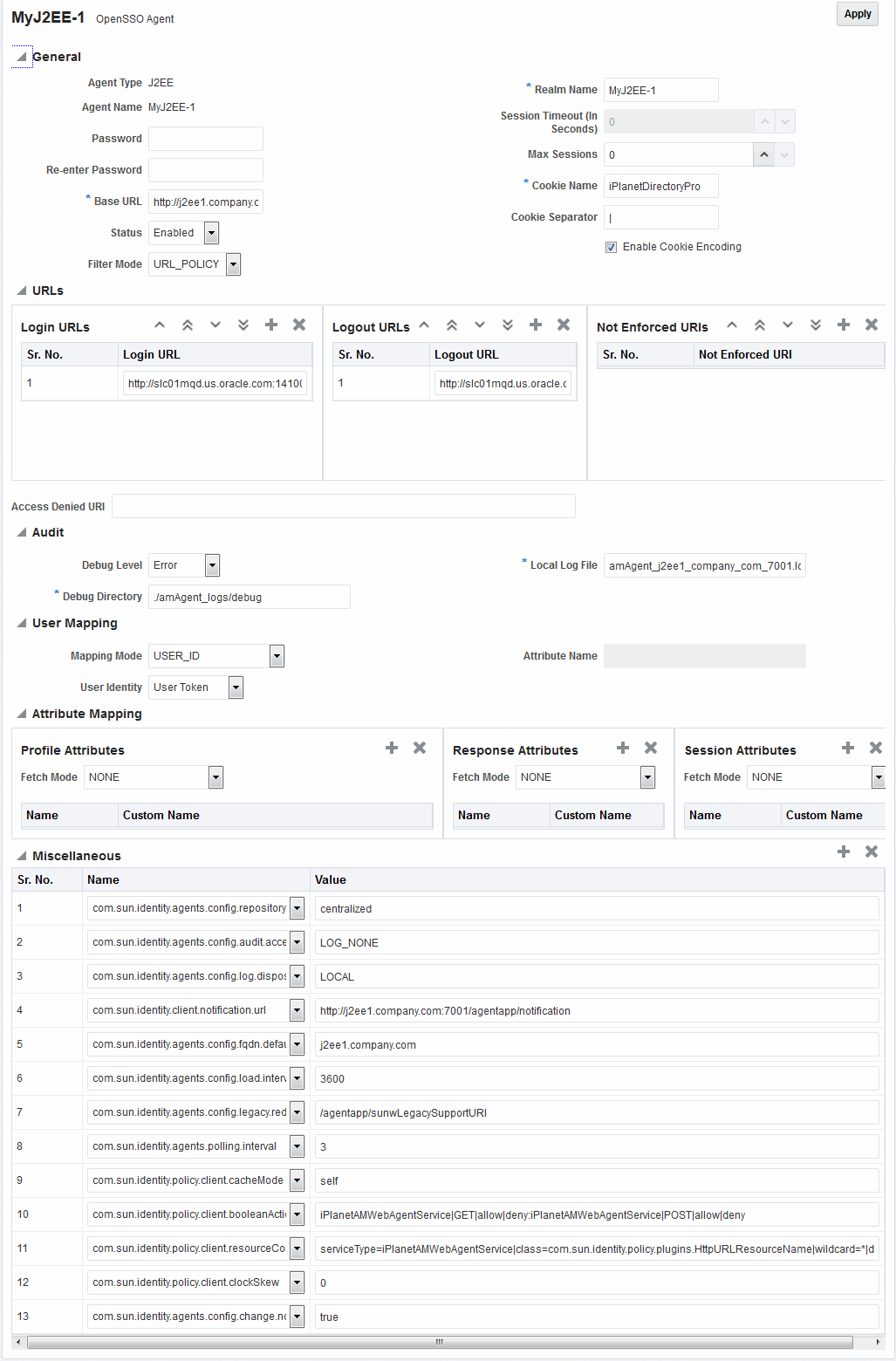
Description of "Figure 28-4 Expanded OpenSSO J2EE Agent Registration Page"
Table 28-7 describes all elements on expanded OpenSSO Agent registration pages.
Table 28-7 Expanded OpenSSO Agent Registration Elements
| Element | Description |
|---|---|
|
Status |
The state of this agent registration: Enabled or Disabled. Default: Enabled See Also: Table 28-5 |
|
Filter mode J2EE Agent Type only |
The Agent filter is installed within the protected application. It facilitates the enforcement of security policies, governing the access to all resources within the protected application. Every application protected by the J2EE Agent must have its deployment descriptors changed to reflect that it is configured to use the agent filter. Applications that do not have this setting are not protected by J2EE the Agent and might malfunction or become unusable if deployed on a deployment container where the Agent realm is installed. Filter modes must be set for the J2EE Agent by choosing one of the following options: SSO_ONLY or URL_Policy. Default: URL_Policy
Process overview: Authentication Only (SSO_ONLY J2EE Filter Mode)
Process overview: Authentication and Authorization with URL_Policy J2EE Filter Mode
Note: The following Filter Modes are not supported: NONE, J2EE_Policy, All. See Also: "Understanding OpenSSO Agent Registration Parameters". |
|
Session Timeout in seconds (User) |
Click the arrows to specify the period, after which the session times out and the user must re-authenticate. You must set "Max Sessions" to a non-zero value to enable this setting. Default: 0 |
|
Max Sessions |
Maximum number of sessions allowed per user. Default: 0 |
|
Cookie Name |
The default name of the OpenSSO cookie is: Default: iPlanetDirectoryPro |
|
Cookie Separator |
Defines the character to be used as a separator when multiple values of the same attribute are being set as a cookie. For example, the pipe symbol "|", can be used. Default: |
|
Enable Cookie Encoding J2EE-type Agent Only |
Identifies whether cookie encoding is enabled or not. Default: Enabled |
|
SSO Only Web-type Agent Only |
Enables OpenSSO Agent to bootstrap and authenticate with the OAM Server using the OpenSSO proxy provided by Access Manager: The end user accesses the application or resource protected by the OpenSSO Agent, which redirects the unauthenticated user to the OAM Server for authentication. After successful authentication, the OpenSSO proxy redirects the user back to the protected application or resource and sets the OpenSSO Session ID in the response cookie. The authenticated user with a valid OpenSSO session accesses the application or resource protected by the OpenSSO Agent, which validates the session against the OAM Server using the OpenSSO Proxy. The end user gets access based on Access Manager authorization policy. |
|
Urls |
|
|
Login URLs |
Enter the login URL, which must include the appropriate protocol (HTTP or HTTPS), host, domain, and port in the following form:
http://example.domain.com:port
Default: Note: The port number is optional. |
|
Logout URLs |
The Logout URL triggers the logout handler, which requires the user to re-authenticate the next time he accesses a resource protected by Access Manager. When yo enter the Logout URL, it must include the appropriate protocol (HTTP or HTTPS), host, domain, and port. For example:
http://example.domain.com:port/opensso/UI/Logout
Default: http://oamhost:port/opensso/UI/Logout Note: The port number is optional. The user must be logged out from resources protected by other agents (WebGate and MOD_OSSO, for instance). Agent logout is not required other than in the multi-domain environment. |
|
Not enforced URLs Web-type Agent Only |
The URLs you enter in this list have no policy enforcement. These equate to Public URLs, with no protection and access is allowed by all. |
|
Access Denied URI |
The URI to which the user is directed if access to the requested resource is denied. This is available for both Web and J2EE Agents, each with its own format requirements: Web Agent (full URL): http://host:port/context/accessDeniedURL.html J2EE Agent (relative URI): /context/accessDeniedURL.htm Default: (blank) |
|
Audit |
|
|
Debug Level J2EE-type Agent Only |
When set, the OAM Server logs messages for:
Default: Error See Also: Logging Component Event Messages |
|
Debug Directory J2EE-type Agent Only |
The filesystem directory path for audit logs from the OAM Server:
|
|
Debug File Web-type Agent Only |
Defines the filesystem directory path to the local component event logging file. Default: |
|
Local Log File |
Defines the filesystem directory path to the local component event logging file. Default: |
|
User Mapping |
|
|
Mapping Mode |
Default: User_ID |
|
User Identity |
Default: User ID |
|
User Attribute Name |
Default: |
|
Attribute Mapping |
Attribute retrieval fetches and sets user attributes in the HTTP request for consumption by the applications. The following Attribute Mapping panels are available:
Fetch Mode: Certain applications rely on the presence of user-specific profile information in some form to process user requests appropriately. The agent can make these attributes from the user's profile available in various forms. when you specify a Fetch Mode for Profile, Response, or Session Attributes:
Default: None |
|
Profile Attributes |
User profile information can be populated under specific names for the currently authenticated user. For example: Fetch Mode: REQUEST_ATTRIBUTE Name (Map key): cn Value: CUSTOM-Common-Name Name (Map key): mail Value: CUSTOM-Email Default: No data |
|
Response Attributes |
Obtains user-specific information by fetching policy response attributes, assigns a mode to the policy response attribute property, and maps the policy response attributes to be populated under specific names for the currently authenticated user. Fetch Mode: REQUEST_ATTRIBUTE Name (Map key): cn Value: CUSTOM-Common-Name Name (Map key): mail Value: CUSTOM-Email_Addr Default: No data |
|
Session Attributes |
The attributes in the session object maintained by the OAM Server. These are sent as part of a session validation response to the Agents. Fetch Mode: REQUEST_ATTRIBUTE Name (Map key): UserToken Value: CUSTOM-userid Default: No data |
|
Miscellaneous |
Most agent properties are hot-swap enabled. Changing configuration properties can have unexpected results. Hot-swappable properties take effect immediately. Therefore, mistakes are instantly implemented.Most agent properties are presented in a format that is most useful for configuring using Oracle Access Management Console. However, this format is not used in the OpenSSOAgentBootstrap.properties file. List Properties: Certain properties are specified as lists composed of a key that represents the property name; a positive number (starting from 0) that increments by 1 for every value specified in the list; and a value. For example: com.sun.identity.agents.config.notenforced.uri[0]=/agentsample/public/* com.sun.identity.agents.config.notenforced.uri[1]=/agentsample/images/* com.sun.identity.agents.config.notenforced.uri[2]=/agentsample/index.html Map Constructs: Certain properties are specified as map constructs composed of a key that represents the property name; a name string that forms the lookup key as available in the map; and the value associated with the name in the map. For example: com.sun.identity.agents.config.filter.mode[app1]=ALL com.sun.identity.agents.config.filter.mode[app2]=SSO_ONLY Note: For a given name, there can only be one entry in the configuration for a given configuration key. If multiple entries with the same <name> for a given configuration key are present only one of the values will be loaded in the system and the other values are discarded. Application-Specific Properties: Certain properties can be configured for specific applications. Thee agent can use different values of the same property for different applications as defined in the configuration file. Application Specific configuration properties must follow the rules and syntax of the map construct. The following settings for a single property serve as an example which illustrates that for applications other than the ones deployed on the root context and the context /Portal, the value of the property defaults to value3. com.sun.identity.agents.config.example[Portal] = value1 com.sun.identity.agents.config.example[DefaultWebApp] = value2 com.sun.identity.agents.config.example = value3 Global Properties: Properties that are not configured for specific applications apply to all the applications on that deployment container. Such properties are called global properties. Serial number: Assigned automatically Name: Select from one of the following Value: Enter the appropriate value for the Name you chose. Note: To enable OpenSSO Agent configuration hotswap, make sure the opensso agents have the following properties in the Miscellaneous properties section of their profile in the OpenSSO Proxy on OAM Server, and the agent servers are restarted: J2ee Agents: Web Agents:
Not Supported, Web Agents: |
|
See Also: |
|
|
Element |
Description |
|
See Also: |
|
|
Status |
The state of this agent registration: Enabled or Disabled. Default: Enabled |
|
Filter mode J2EE Agent Type only |
The Agent filter is installed within the protected application. It facilitates the enforcement of security policies, governing the access to all resources within the protected application. Every application protected by the J2EE Agent must have its deployment descriptors changed to reflect that it is configured to use the agent filter. Applications that do not have this setting are not protected by J2EE the Agent and might malfunction or become unusable if deployed on a deployment container where the Agent realm is installed. Filter modes must be set for the J2EE Agent by choosing one of the following options: SSO_ONLY or URL_Policy. Default: URL_Policy
Process overview: Authentication Only (SSO_ONLY J2EE Filter Mode)
Process overview: Authentication and Authorization with URL_Policy J2EE Filter Mode
Note: The following Filter Modes are not supported: NONE, J2EE_Policy, All. See Also: "Understanding OpenSSO Agent Registration Parameters". |