55.2 Understanding Identity Context
Access Manager enables context-aware access management by incorporating Identity Context as a built-in service of the Oracle Access Management platform.
Figure 55-1 illustrates the flow of the Identity Context process, implemented by multiple system components. Each application delivery component has its own security policy infrastructure responsible for protecting its individual slice of the application. This specific use case involves the end user device, a Web Server running static GUI pages, an Application Server running the Portal Server rendering dynamic content, a Service Bus Server exposing the Web service endpoint, a database server containing transactional data, and an LDAP server containing identity profile data.
Figure 55-1 End to End Identity Context Process
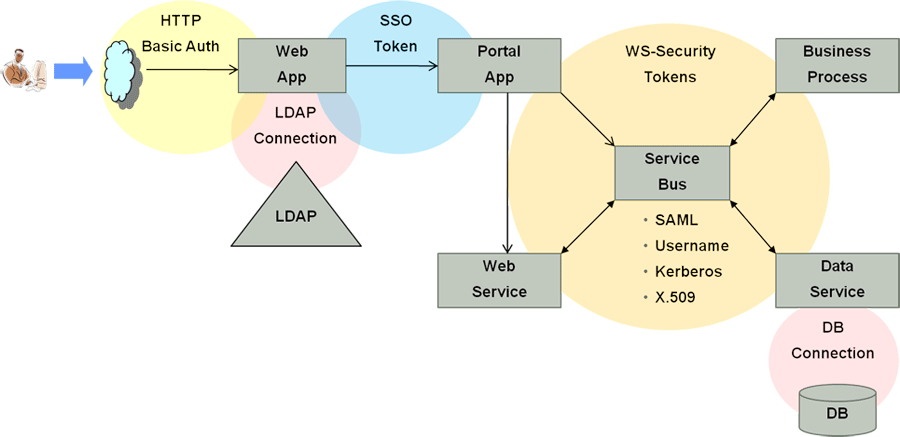
Description of "Figure 55-1 End to End Identity Context Process"
Each component of the process has its own security infrastructure where the authorization policies governing access to protected resources are defined administratively and enforced at runtime. Additionally, some or all of the components may have externalized policy management to an external authorization server such as Oracle Entitlements Server - which is the case if the applications were built leveraging Oracle Platform Security Services. Figure 55-2 illustrates the functional architecture of Identity Context based on the Oracle applications of which it is comprised.
Figure 55-2 End To End Identity Context Process Components
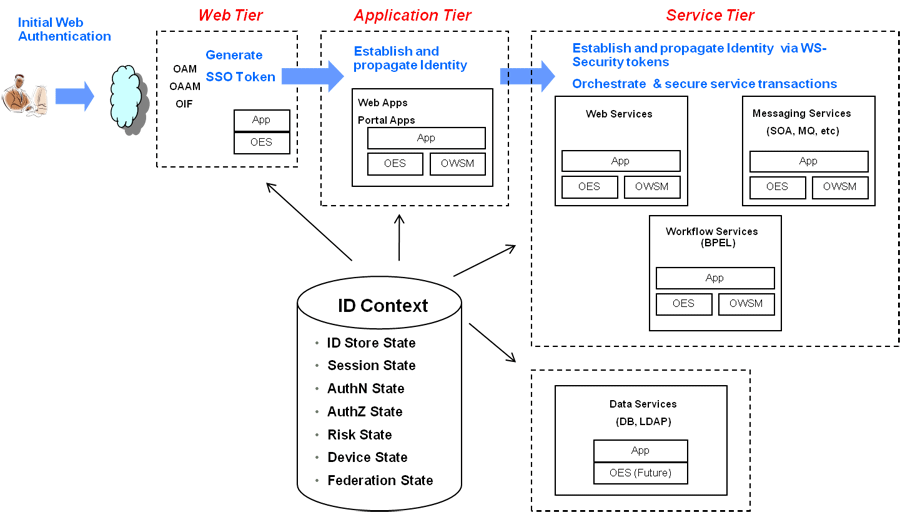
Description of "Figure 55-2 End To End Identity Context Process Components"
As seen in the illustrations, context-aware security policy management is achieved by leveraging the Oracle Access Management platform. This platform contains native support for working with and enforcing Identity Context attributes (including risk score, trusted device data, authentication data, and the like) without changing end-user applications.