2 Getting Started with Oracle GoldenGate
Oracle GoldenGate supports two architectures, the Classic Architecture and the Microservices Architecture (MA).
-
A static extraction of data records from one database and the loading of those records to another database.
-
Continuous extraction and replication of transactional Data Manipulation Language (DML) operations and data definition language (DDL) changes (for supported databases) to keep source and target data consistent.
-
Extraction from a database and replication to a file outside the database.
Oracle GoldenGate Architectures Overview
The following table describes the two Oracle GoldenGate architectures and when you should use each of the architectures.
| ... | Classic Architecture | Microservices Architecture |
|---|---|---|
| What is it? |
Oracle GoldenGate classic architecture provides the processes and files required to effectively move data across a variety of topologies. These processes and files form the main components of the classic architecture and was the product design until this release. |
Oracle GoldenGate Microservices Architecture is a new microservices architecture that provides REST-enabled services as part of the Oracle GoldenGate environment. The REST-enabled services provide remote configuration, administration, and monitoring through HTML5 web pages, command line, and APIs. |
| When should I use it? |
Oracle GoldenGate can be installed and configured to use the Oracle GoldenGate classic architecture for the following purposes:
|
Oracle GoldenGate can be installed and configured to use the Oracle GoldenGateMicroservices Architecture for the following purposes:
|
| Which databases are supported? | Classic Architecture supports all supported databases as per the certification matrix. | MA only supports the Oracle database. |
- Oracle GoldenGate Supported Processing Methods and Databases
- Components of Oracle GoldenGate Classic Architecture
You can use the Oracle GoldenGate Classic Architecture to configure and manage your data replications from the command line. - Components of Oracle GoldenGate Microservices Architecture
You can use Oracle GoldenGate Microservices Architecture to configure and manage your data replication using an HTML user interface.
2.1 Oracle GoldenGate Supported Processing Methods and Databases
Oracle GoldenGate enables the exchange and manipulation of data at the transaction level among multiple, heterogeneous platforms across the enterprise. It moves committed transactions with transaction integrity and minimal overhead on your existing infrastructure. Its modular architecture gives you the flexibility to extract and replicate selected data records, transactional changes, and changes to DDL (data definition language) across a variety of topologies.
Note:
Support for DDL, certain topologies, and capture or delivery configurations varies by the database type. See Using Oracle GoldenGate for Oracle Database and Using Oracle GoldenGate for Heterogeneous Databases for detailed information about supported features and configurations.
With this flexibility, and the filtering, transformation, and custom processing features of Oracle GoldenGate, you can support numerous business requirements:
-
Business continuance and high availability.
-
Initial load and database migration.
-
Data integration.
-
Decision support and data warehousing.
This diagram shows Oracle GoldenGate supported topologies.
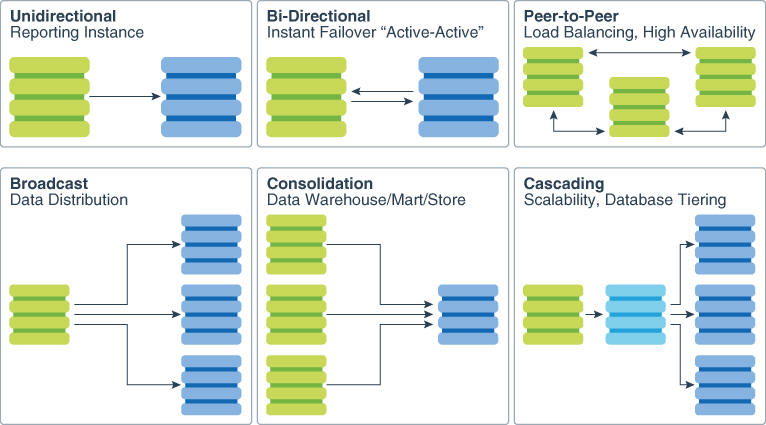
Description of the illustration goldengate_configs2.jpg
Here is a list of the supported processing methods.
| Database | Log-Based Extraction (capture) | Non-Log-Based Extraction (1) (capture) | Replication (delivery) |
|---|---|---|---|
|
DB2 for i |
N/A |
N/A |
X |
|
DB2 LUW |
X |
N/A |
X |
|
DB2 z/OS |
X |
N/A |
X |
|
Oracle Database |
X |
N/A |
X |
|
MySQL |
X |
N/A |
X |
|
SQL Server |
X |
X |
X |
|
Informix |
N/A |
N/A |
X |
Footnote 1 Non-Log-Based Extraction uses a capture module that communicates with the Oracle GoldenGate API to send change data to Oracle GoldenGate.
Parent topic: Getting Started with Oracle GoldenGate
2.2 Components of Oracle GoldenGate Classic Architecture
You can use the Oracle GoldenGate Classic Architecture to configure and manage your data replications from the command line.
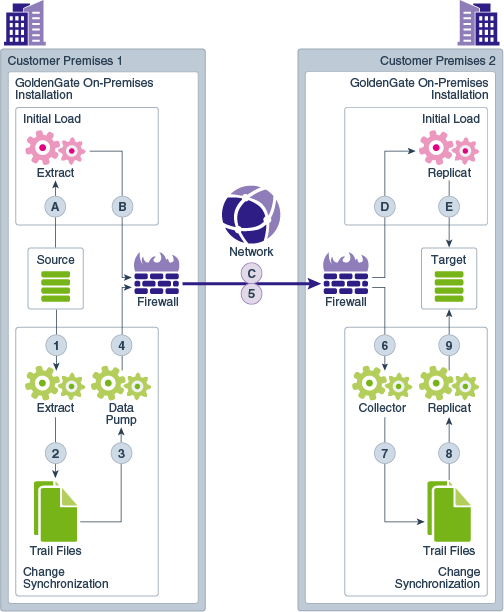
Note:
This is the basic configuration. Depending on your business needs and use case, you can configure different variations of this model.Topics:
- What is a Manager?
Manager is the control process of Oracle GoldenGate. Manager must be running on each system in the Oracle GoldenGate configuration before the Extract or Replicat processes can be started. - What is a Data Pump?
Data pump is a secondary Extract group within the source Oracle GoldenGate configuration. - What is a Collector?
The Collector is started by the manager process and is a process that runs in the background on the target system. It reassembles the transactional data into a target trail. - What is GGSCI?
You can use the Oracle GoldenGate Software Command Interface (GGSCI) commands to create data replications. This is the command interface between you and Oracle GoldenGate functional components.
Parent topic: Getting Started with Oracle GoldenGate
2.2.1 What is a Manager?
Manager is the control process of Oracle GoldenGate. Manager must be running on each system in the Oracle GoldenGate configuration before the Extract or Replicat processes can be started.
Manager must also remain running while the Extract and Replicat processes are running so that resource management functions are performed. One Manager process can control many Extract or Replicat processes.
Manager performs the following functions:
-
Starts Oracle GoldenGate processes
-
Starts dynamic processes
-
Maintains port numbers for processes
-
Purges Trail files based on retention rules
-
Creates event, error, and threshold reports
One Manager process can control many Extract or Replicat processes. On Windows systems, Manager can run as a service. See olink:GWUAD-GUID-5005AF6D-76D2-4C72-80E2-AD33C24F0C26 for more information about the Manager process and configuring TCP/IP connections.
Parent topic: Components of Oracle GoldenGate Classic Architecture
2.2.2 What is a Data Pump?
Data pump is a secondary Extract group within the source Oracle GoldenGate configuration.
If you configure a data pump, the Extract process writes all the captured operations to a trail file on the source database. The data pump reads the trail file on the source database and sends the data operations over the network to the remote trail file on the target database. Though configuring a data pump is optional, it is highly recommended for most configurations. If a data pump is not used, the Extract process must streams all the captured operations to a trail file on the remote target database. In a typical configuration with a data pump, however, the primary Extract group writes to a trail on the source system. The data pump reads this trail and sends the data operations over the network to a remote trail on the target. The data pump adds storage flexibility and also serves to isolate the primary Extract process from TCP/IP activity.
In general, a data pump can perform data filtering, mapping, and conversion
-
Perform data manipulation: Data Pump can be configured to perform data filtering, mapping, and conversion.
-
Perform no data manipulation: Data Pump can be configured in pass-through mode, where data is passively transferred as-is, without manipulation. Pass-through mode increases the throughput of the Data Pump, because all of the functionality that looks up object definitions is bypassed.
Though configuring a data pump is optional, Oracle recommends it for most configurations. Some reasons for using a data pump include the following:
-
Protection against network and target failures: In a basic Oracle GoldenGate configuration, with only a trail on the target system, there is nowhere on the source system to store the data operations that Extract continuously extracts into memory. If the network or the target system becomes unavailable, Extract could run out of memory and abend. However, with a trail and data pump on the source system, captured data can be moved to disk, preventing the abend of the primary Extract. When connectivity is restored, the data pump captures the data from the source trail and sends it to the target system(s).
-
You are implementing several phases of data filtering or transformation. When using complex filtering or data transformation configurations, you can configure a data pump to perform the first transformation either on the source system or on the target system, or even on an intermediary system, and then use another data pump or the Replicat group to perform the second transformation.
-
Consolidating data from many sources to a central target. When synchronizing multiple source databases with a central target database, you can store extracted data operations on each source system and use data pumps on each of those systems to send the data to a trail on the target system. Dividing the storage load between the source and target systems reduces the need for massive amounts of space on the target system to accommodate data arriving from multiple sources.
-
Synchronizing one source with multiple targets. When sending data to multiple target systems, you can configure data pumps on the source system for each target. If network connectivity to any of the targets fails, data can still be sent to the other targets.
Parent topic: Components of Oracle GoldenGate Classic Architecture
2.2.3 What is a Collector?
The Collector is started by the manager process and is a process that runs in the background on the target system. It reassembles the transactional data into a target trail.
When the Manager receives a connection request from an Extract process, the Collector scans and binds to an available port and sends the port number to the Manager for assignment to the requesting Extract process. The Collector also receives the captured data that is sent by the Extract process and writes them to the remote trail file.
Note:
Collector can be run manually, if needed. This is known as a static Collector (as opposed to the regular, dynamic Collector). Several Extract processes can share one static Collector; however, a one-to-one ratio is optimal. A static Collector can be used to ensure that the process runs on a specific port.Parent topic: Components of Oracle GoldenGate Classic Architecture
2.2.4 What is GGSCI?
You can use the Oracle GoldenGate Software Command Interface (GGSCI) commands to create data replications. This is the command interface between you and Oracle GoldenGate functional components.
GGSCI is the Oracle GoldenGate command-line interface. You can use GGSCI to issue the complete range of commands that configure, control, and monitor Oracle GoldenGate.
To start GGSCI, change directories to the Oracle GoldenGate installation directory, and then run the ggsci executable file.
For more information about Oracle GoldenGate commands, see Reference for Oracle GoldenGate.
Parent topic: Components of Oracle GoldenGate Classic Architecture
2.3 Components of Oracle GoldenGate Microservices Architecture
You can use Oracle GoldenGate Microservices Architecture to configure and manage your data replication using an HTML user interface.
There are five main components of the Oracle GoldenGate MA. The following diagram depicts illustrates how replication processes operate within a secure REST API environment.
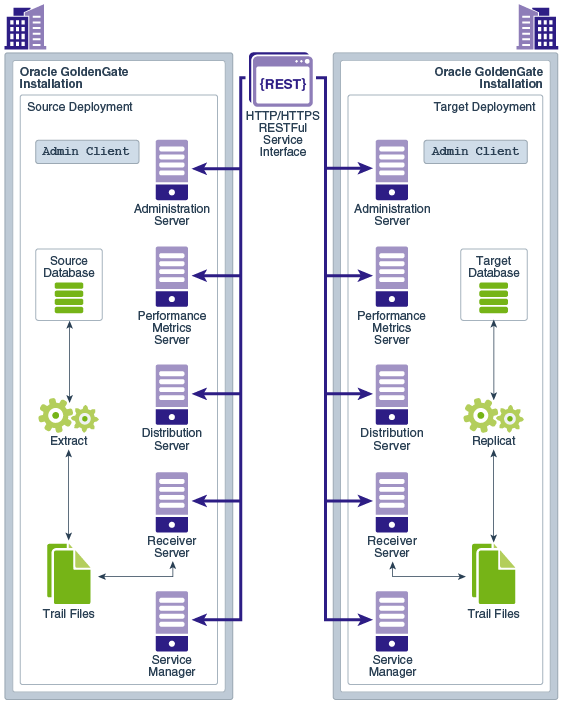
The Oracle GoldenGate MA provides all the tools you need to configure, monitor, and administer deployments and security. It is designed with the industry-standard HTTP(s) communication protocol and the JavaScript Object Notation (JSON) data interchange format. In addition, the architecture provides you with the ability to verify the identity of clients with basic authentication or Secure Sockets Layer client certificates.
The following diagram shows a variety of clients (Oracle products, command line, browsers, and programmatic REST API interfaces) that you can use to administer your deployments using the service interfaces.
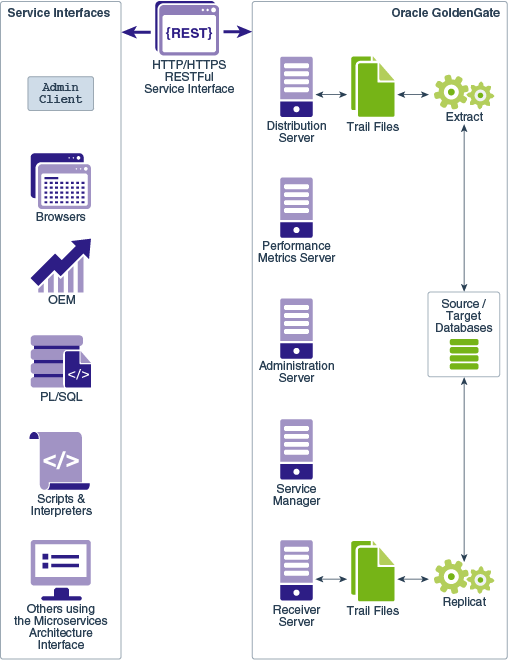
Topics:
- What is a Service Manager?
A Service Manager acts as a watchdog for other services available with Microservices Architecture. - What is an Administration Server?
The Administration Server supervises, administers, manages, and monitors processes operating within an Oracle GoldenGate deployment for both active and inactive processes. - What is a Distribution Server?
A Distribution Server is a service that functions as a networked data distribution agent in support of conveying and processing data and commands in a distributed deployment. It is a high performance application that is able to handle multiple commands and data streams from multiple source trail files, concurrently. - What is a Receiver Server?
A Receiver Server is the central control service that handles all incoming trail files. It interoperates with the Distribution Server and provides compatibility with the classic architecture pump for remote classic deployments. - What is a Performance Metrics Server?
The Performance Metrics Server uses the metrics service to collect and store instance deployment performance results. This metrics collection and repository is separate from the administration layer information collection. - What is the Admin Client?
The Admin Client is a command line utility (similar to the classic GGSCI utility).You can use it to issue the complete range of commands that configure, control, and monitor Oracle GoldenGate. - What are the Key Microservices Architecture Directories and Variables?
The Microservices Architecture is designed with a simplified installation and deployment directory structure. - Roadmap for Implementing the Microservices Architecture
Microservices Architecture is based on the REST API. After installing the Microservices Architecture, it is accessible through an HTML5 interface, REST APIs, and the command line.
Parent topic: Getting Started with Oracle GoldenGate
2.3.1 What is a Service Manager?
A Service Manager acts as a watchdog for other services available with Microservices Architecture.
A Service Manager allows you to manage one or multiple Oracle GoldenGate deployments on a local host.
Service Manager is run as a system service and maintains inventory and configuration information about your deployments and allows you to maintain multiple local deployments. Using the Service Manager, you can start and stop instances, and query deployments and the other services.
2.3.2 What is an Administration Server?
The Administration Server supervises, administers, manages, and monitors processes operating within an Oracle GoldenGate deployment for both active and inactive processes.
The Administration Server operates as the central control entity for managing the replication components in your Oracle GoldenGate deployments. You use it to create and manage your local Extract and Replicat processes without having to have access to the server where Oracle GoldenGate is installed. The key feature of the Administration Server is the REST API service Interface that can be accessed from any HTTP or HTTPS client, such as the Microservices Architecture service interfaces or other clients like Perl and Python.
In addition, the Admin Client can be used to make REST API calls to communicate directly with the Administration Server, see What is the Admin Client?
The Administration Server is responsible for coordinating and orchestrating Extracts, Replicats, and paths to support greater automation and operational managements. Its operation and behavior is controlled through published query and service interfaces. These interfaces allow clients to issue commands and control instructions to the Administration Server using REST JSON-RPC invocations that support REST API interfaces.
The Administration Server includes an embedded web application that you can use directly with any web browser and does not require any client software installation.
Use the Administration Server to create and manage:
-
Extract and Replicat processes
-
Add, alter, and delete
-
Register and unregister
-
Start and stop
-
Review process information, statistics, reports, and status including LAG and checkpoints
-
Retrieve the report and discard files
-
-
Configuration (parameter) files
-
Checkpoint, trace, and heartbeat tables
-
Supplemental logging for procedural replication, schema, and tables
-
Tasks both custom and standard, such as auto-restart and purge trails
-
Credential stores
-
Encryption keys (
MASTERKEY) -
Add users and assign their roles
2.3.3 What is a Distribution Server?
A Distribution Server is a service that functions as a networked data distribution agent in support of conveying and processing data and commands in a distributed deployment. It is a high performance application that is able to handle multiple commands and data streams from multiple source trail files, concurrently.
Distribution Server replaces the classic multiple source-side data pumps with a single instance service. This server distributes one or more trails to one or more destinations and provides lightweight filtering only (no transformations).
Multiple communication protocols can be used, which provide you the ability to tune network parameters on a per path basis. These protocols include:
-
Oracle GoldenGate protocol for communication between the Distribution Server and the Collector in a non services-based (classic) target. It is used for inter-operability.
Note:
TCP encryption does not work in a mixed environment of Classic and Microservices architecture. The Distribution Server in Microservices Architecture cannot be configured to use the TCP encryption to communicate with the Server Collector in Classic Architecture running in a deployment. Also, the Receiver Server in Microservices Architecture cannot accept a connection request from a data pump in Classic Architecture configured with
RMTHOST ... ENCRYPTparameter running in a deployment. -
WebSockets for HTTPS-based streaming, which relies on SSL security.
-
UDT for wide area networks.
-
Proxy support for cloud environments:
-
SOCKS5 for any network protocol.
-
HTTP for HTTP-type protocols only, including WebSocket.
-
-
Passive Distribution Server to initiate path creation from a remote site. Paths are source-to-destination replication configurations though are not included in this release.
Note:
There is no content transformation by this service.
2.3.4 What is a Receiver Server?
A Receiver Server is the central control service that handles all incoming trail files. It interoperates with the Distribution Server and provides compatibility with the classic architecture pump for remote classic deployments.
A Receiver Server replaces multiple discrete target-side Collectors with a single instance service.
Use Receiver Server to:
-
Monitor path events
-
Query the status of incoming paths
-
View the statistics of incoming paths
-
Diagnose path issues
WebSockets is the default HTTPS initiated full-duplex streaming protocol used by the Receiver Server. It enables you to fully secure your data using SSL security. The Receiver Server seamlessly traverses through HTTP forward and reverse proxy servers as illustrated in Figure 2-1.
Figure 2-1 Receiver Server Communication
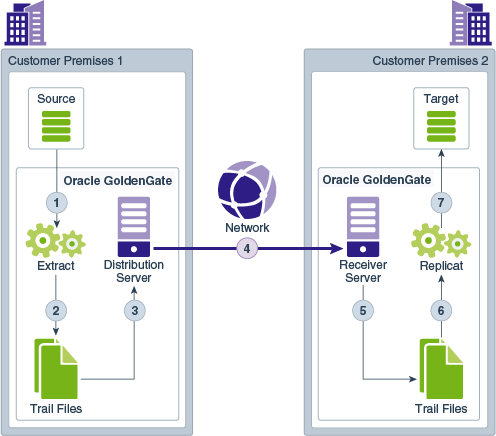
Additionally, the Receiver Server supports the following protocols:
-
UDT—UDP-based protocol for wide area networks. For more information, see http://udt.sourceforge.net/.
-
Classic Oracle GoldenGate protocol—For classic deployments so that the Distribution Server communicates with the Collector and the Data Pump communicates with the Receiver Server.
Note:
TCP encryption does not work in a mixed environment of Classic and Microservices architecture. The Distribution Server in Microservices Architecture cannot be configured to use the TCP encryption to communicate with the Server Collector in Classic Architecture running in a deployment. Also, the Receiver Server in Microservices Architecture cannot accept a connection request from a data pump in Classic Architecture configured with RMTHOST ... ENCRYPT parameter running in a deployment.
2.3.5 What is a Performance Metrics Server?
The Performance Metrics Server uses the metrics service to collect and store instance deployment performance results. This metrics collection and repository is separate from the administration layer information collection.
You can monitor performance metrics using other embedded web applications and use the data to tune your deployments for maximum performance. All Oracle GoldenGate processes send metrics to the Performance Metrics Server. You can use the Performance Metrics Server in both Microservices Architecture and Classic Architecture.
Use the Performance Metrics Server to:
-
Query for various metrics and receive responses in the services JSON format or the classic XML format
-
Integrate third party metrics tools
-
View error logs
-
View active process status
-
Monitor system resource utilization
2.3.6 What is the Admin Client?
The Admin Client is a command line utility (similar to the classic GGSCI utility).You can use it to issue the complete range of commands that configure, control, and monitor Oracle GoldenGate.
Note:
Ensure that theOGG_HOME, OGG_VAR_HOME, and OGG_ETC_HOME are set up correctly in the environment.For more information on environment variables, see Setting Environment Variables.
The way that you use the Admin Client while similar is different in some ways in support of the MA design:
Table 2-1 Admin Client Operation versus GGSCI Operation
| GGSCI | Admin Client |
|---|---|
|
Connects to local deployment |
Connects to any MA deployment |
|
Requires local machine access, typically SSH |
Requires HTTP or HTTPS access |
|
Application logic executed locally |
Application logic executed remotely |
|
Requires connection to DBMS |
No connection to DBMS required |
|
Uses operating system security |
Uses MA security |
|
Authenticated and authorized once |
Authenticated and authorized for each operation |
|
No special connect semantics |
Requires a |
|
Supports |
Supports |
|
|
|
|
Non-secure communications |
Encrypted communications using SSL |
|
Uses pump processes |
Use Distribution Server |
The Admin Client was designed with GGSCI as the basis. The following table describes the new, deleted, and deprecated commands in the Admin Client:
Table 2-2 Admin Client Commands
| New Commands | Deleted Commands and Processes: | Deprecated Commands |
|---|---|---|
CONNECT DISCONNECT [START | STATUS | STOP] SERVICE [ADD | ALTER | DELETE | INFO | [KILL START | STATS | STOP] [EDIT | VIEW] GLOBALS CD |
* MGR * JAGENT * CREATE DATASTORE SUBDIRS FC DUMPDDL INFO MARKER |
ADD CREDENTIALSTORE [CREATE | OPEN] WALLET |
2.3.7 What are the Key Microservices Architecture Directories and Variables?
The Microservices Architecture is designed with a simplified installation and deployment directory structure.
This directory structure is based on the Linux Foundation Filesystem Hierarchy Standard. Additional flexibility has been added to allow parts of the deployment subdirectories to be placed at other locations in the file system or on other devices, including shared network devices. The design is comprised of a read only home directory where you install Oracle GoldenGate and create a custom deployment specific directories as in the following:
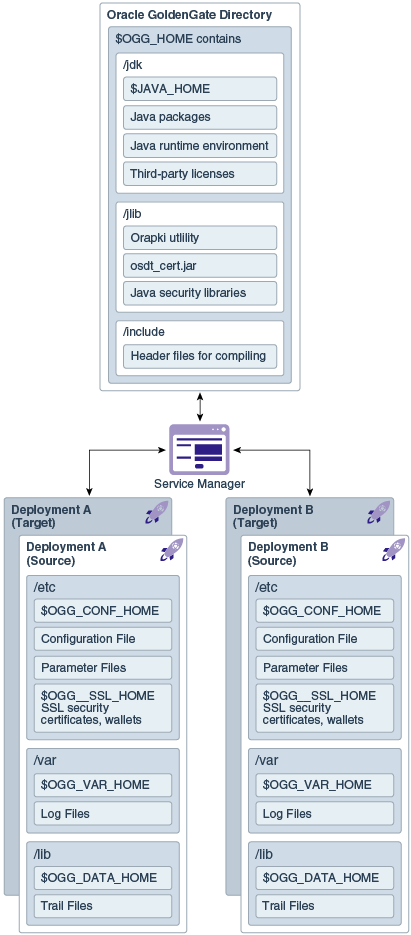
The following table describes the key MA directories and the variables that are used when referring to those directories in an Oracle GoldenGate installation. When you see these variables in an example or procedure, replace the variable with the full path to the corresponding directory path in your enterprise topology.
Table 2-3 Directories in an MA Installation and Deployment
| Directory Name | Variable | Description | Default Directory Path |
|---|---|---|---|
|
Oracle Database home |
|
The Oracle database home that is created on a host computer is the directory that you choose to install the product. This read-only directory contains binary, executable, and library files for the product. |
|
|
Oracle GoldenGate home |
|
The Oracle GoldenGate home that is created on a host computer is the directory that you choose to install the product. This read-only directory contains binary, executable, and library files for the product. |
|
|
Deployment configuration home |
|
The location in which each deployment information and configuration artifacts are stored. |
|
|
Deployment security home |
|
The location in which each deployment security artifacts (certificates, wallets) are stored. |
|
|
Deployment data home |
|
The location in which each deployment data artifacts (trail files) are stored. |
|
|
Deployment variable home |
|
The location in which each deployment logging and reporting processing artifacts are stored. |
|
|
Deployment etc home |
|
The location in which your deployment configuration files are stored including parameter files. |
|
You can change the default location of all of these to customize where you want to store these files.
In a configuration where the OGG_VAR_HOME is a local directory and the OGG_HOME is a shared read-only remote directory, many deployments with local OGG_VAR_HOME can share one read-only shared OGG_HOME.
This directory design facilitates a simple manual upgrade. To upgrade, you stop the services and then set the OGG_HOME in the web interface (or via a REST command) and then restart the processes. On the restart, Oracle GoldenGate picks up the updated environment variables. You simply switch a deployment to use a new Oracle GoldenGate release by changing the OGG_HOME directory path in your Service Manager to a new Oracle GoldenGate home directory, which completes the upgrade. You then must restart the MA servers, Extract processes, and Replicat processes.
2.3.8 Roadmap for Implementing the Microservices Architecture
Microservices Architecture is based on the REST API. After installing the Microservices Architecture, it is accessible through an HTML5 interface, REST APIs, and the command line.
-
The Database to which Oracle GoldenGateMicroservices Architecture connects to.
-
Oracle GoldenGate users must be configured.
This topic describes the roadmap for implementing Microservices Architecture components and clients.
Table 2-4 Roadmap for Implementing Oracle GoldenGateMicroservices Architecture
| Task | More Information |
|---|---|
|
Installing the MA |
|
|
Starting the Service Manager |
|
|
Starting the Servers |
|
|
(Optional) Starting the Admin Client |