62 Working with Single Sign-On for Production Sites
Here is a simple example that helps you understand how you can enable single sign-on and sign-out for applications on live sites where you won’t be able to secure applications with ready-to-use CAS.
Topics:
62.1 Deploying the SSO Sample Application
All you need to do is unpack the WAR file, modify the context file, and deploy the application.
The SSO sample application consists of the following pages:
-
Protected area: A page that is protected by the WEM SSO filter. This page contains two single sign-out links.
Figure 62-1 Protected Page with Single Sign-Out Links
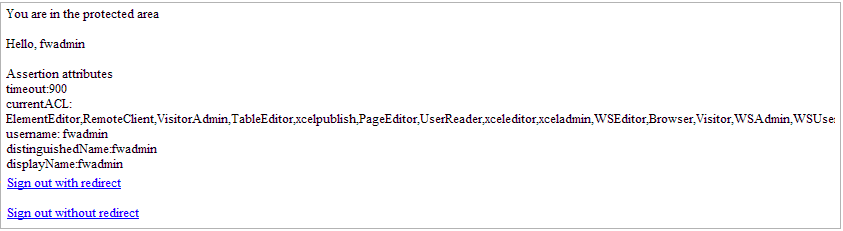
Description of "Figure 62-1 Protected Page with Single Sign-Out Links"The first link (single sign-out with redirect) is an HTML link that performs single sign-out on the CAS side and redirects the user back to the home page. The second link (single sign-out without redirect) is also an HTML link that performs single sign-out on the CAS side, but without leaving or reloading the current page.
-
Public area: A page that is excluded from the protection filter.
-
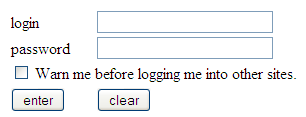
Public area with login form: This page is excluded from the protection filter, but has a login form, which allows performing a sign-in operation without leaving or reloading the current page.
Figure 62-2 Public Area with the Sign in Link

Description of "Figure 62-2 Public Area with the Sign in Link"
Note:
On successful login CAS redirects the user to the requested service. For security purposes, you may validate the requested service before redirecting the user. Do this by specifying the list of trusted and permitted urls using the Property Management Tool under the System Tools node in the Admin interface. Add the trusted urls (comma separated) to the valid.urls property. This property specifies that the trusted URLs users are permitted to use to access WebCenter Sites. Default value of this property is <wcsites.app.protocol>://<wcsites.app.host>:<wcsites.app.port>/<wcsites.app.contextroot>/*. See Property Files Reference for Oracle WebCenter Sites.
The URLs can be in either of the following formats:
-
Exact URL. For instance:
http://hostname:port/cs/wem/fatwire/wem/Welcome -
Matching URL. For instance:
http://hostname:port/SitesWebapp/*Where
/*at the end indicates any URL that has the same prefix as specified
Trusted resources using IP must have URLs specified as well.
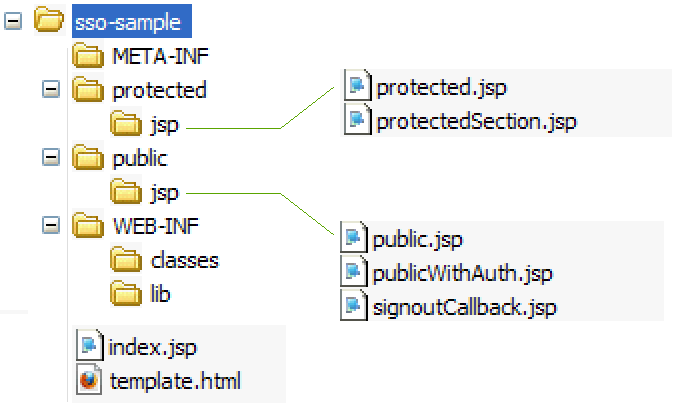
62.2 Understanding SSO Sample Application's Structure
With the SSO sample application’s basic code for configuring single sign-on and sign-out you can protect applications on production sites.
The following components provide access to the SSO sample application:
-
index.jsp: Starting page. This page contains links to the pages described as Protected area, Public area, and Public area with login form pages (see Deploying the SSO Sample Application). -
template.html: Used to provide a custom sign-in form for CAS. Its path is referenced in thewemLoginTemplateparameter incasLoginPathin theapplicationContext.xmlfile.
Configuration Files in /sso-sample/WEB-INF
WEB-INF contains the following configuration files:
-
applicationContext.xml: Spring web application configuration file, which configures the SSO subsystem. -
web.xml: Web application deployment descriptor.
Protected Files in /sso-sample/protected/jsp
Files in this area are protected by the SSO filter. By default, the following files are included in this folder:
-
protected.jsp: A page protected by the SSO filter. This page hosts two links for performing single sign-out. The first link leads to the CAS sign-out page with a redirect to the application's home page when sign-out is complete. The second link embeds an iframe into this page, which calls the CAS sign-out page with a redirect to thesignoutCallback.jsppage. Theprotected.jsppage also prints out all attributes from theAssertionobject, which describes the current logged in user. -
protected/jsp/protectedSection.jsp: Page that is referenced from thepublic.jsppage, when the Sign in link is clicked in an embedded iframe. As this page is protected, a login screen is presented in the embedded iframe.
Public Files in /sso-sample/public/jsp
Files in this area are not protected by the SSO filter. By default, the following sample files are included in the /public/jsp/ folder:
-
public.jsp: This page not protected by the CAS filter. -
publicWithAuth.jsp: This page displays the Sign in link. Clicking the link embeds an iframe into thepublicWithAuth.jspwith the iframe pointing to theprotectedSection.jsppage. As the page is protected, a login screen is presented in the embedded iframe. -
signoutCallback.jsp: This page is called from theprotected.jsppage upon sign-out completion when using iframe.
62.3 Implementing Single Sign-On
You can implement single sign-on for a website by either presenting the sign-in form when the visitor tries to access a protected page or embedding it into a public page.
-
The sign-in form is presented when the visitor tries to access a protected page. This is the default sign-in implementation. This sign in form could be either a default sign-in form shipped with CAS or a custom form provided by an application.
-
The sign-in form is embedded into a public page, and the sign-in function is performed without the user leaving the current page. This behavior can be implemented by embedding the iframe that points to a protected page. As the page is being protected, the sign-in form is presented to the visitor.
62.4 Implementing Single Sign-Out
You implement single sign-out either by retrieving the single sign-out URL or by using an iframe-embedding technique.
-
Retrieve the
single sign-outURL by invoking the following method:getSignoutUrl()orgetSignoutUrl(String callbackUrl)method ofcom.fatwire.wem.sso.SSO.getSSOSession()object.After performing single sign-out, CAS can optionally redirect to the visitor-supplied URL, which is set in the
callbackUrlparameter. -
Use an iframe-embedding technique if the sign-out is to be performed without leaving the current page. This technique involves embedding an iframe with the single sign-out URL as source. When the iframe is loaded, the sign-out URL is called (this is done primarily to avoid cross-domain restrictions in browsers).