Security Configuration Using the Sample Application
When operating in a development or test environment you might find it convenient to use the security configuration provided when you use the default directory server and the sample application. You then add user definitions and credentials specific to your business, and customize the existing application roles and permission grants to meet your requirements.
After the authentication, policy, and credential providers are fully configured and populated with data specific to your business, they provide all user, policy, and credential information needed by the Oracle Business Intelligence components during authentication and authorization.
Oracle BI EE security with the embedded directory server and sample application has three security providers that are integrated to ensure safe, controlled access to system and data resources. These security providers are configured during installation as follows:
-
See Default Authentication Provider.
The authentication provider is DefaultAuthenticator, which authenticates against Oracle WebLogic Server embedded directory server (identity store). The default identity store is managed using Oracle WebLogic Server Administration Console.
-
The policy store provider is the database specified during the initial BI configuration. It contains the application role definitions with their corresponding Oracle Business Intelligence permission grants, and the mapping definitions between groups and application roles. The assigning of a group to an application role serves to convey the corresponding permissions to members of the group. The default policy store provider is managed using Fusion Middleware Control.
-
Credential Store Provider
The credential store provider is the database specified during the initial BI configuration. It contains the passwords and other security-related credentials either supplied or system-generated. The default credential store is managed using Fusion Middleware Control.
The table summarizes the security providers and their initial state after installation.
| Security Provider Type | Purpose | Default Provider | Options |
|---|---|---|---|
|
Authentication provider |
Used to control authentication. |
|
Oracle Business Intelligence can be reconfigured to use different authentication providers and directory servers. See System Requirements and Certification. |
|
Policy store provider |
|
|
Oracle Business Intelligence can be configured to use Oracle Internet Directory. |
|
Credential store provider |
Trusted store for holding system passwords and other security-related credentials. The data stored here is used for connecting to external systems, opening repositories, or for SSL. |
|
Oracle Business Intelligence can be configured to use Oracle Internet Directory. |
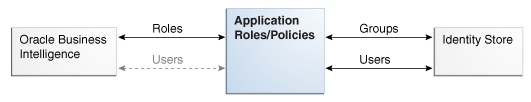
The diagram shows the relationship between Oracle Business Intelligence and the authentication and policy store providers.
Default Authentication Provider
An authentication provider accesses user and group information and is responsible for authenticating users..
An identity store contains user name, password, and group membership information and in Oracle Business Intelligence. The default security configuration authenticates against the Oracle WebLogic Server embedded directory server using an authentication provider named DefaultAuthenticator
When a user logs in to a system with a user name and password combination, Oracle WebLogic Server validates identity based on the combination provided. During this process, a Java principal is assigned to the user or group that is undergoing authentication. The principal can consist of one or more users or groups and is stored within subjects. A subject is a JAAS element used to group and hold identity information.
Upon successful authentication, each principal is signed and stored in a subject. When a program call accesses a principal stored in a subject, the default authenticator provider verifies the principal has not been altered since signing, and the principal is returned to the program making the call. For example, in the Oracle WebLogic Server default authenticator, the subject contains a principal for the user (WLSUserPrincipal) and a principal for the group (WLSGroupsPrincipals) of which the user is a member. If an authentication provider other than the installation default is configured, consult that provider's documentation because how identity information is stored might differ.
Groups and Members
Groups are logically ordered sets of users. Creating groups of users who have similar system resource access needs enables easier security management. Managing a group is more efficient than managing a large number of users individually. Groups are then assigned to application roles to grant rights. Oracle recommends that you organize your users into groups for easier maintenance.
No default groups are created during the installation of BI.
Default Users and Passwords
When you configure your BI deployment a WebLogic domain is created and populated with a single user that is specified as part of the configuration steps.
-
This user name is entered by the person performing the configuration and can be any desired name.
-
The password entered during installation can be changed later using the administration interface for the identity store provider.
-
During the configuration of the BI service instance, the WebLogic domain administrator is automatically made the owner of the service instance and made a member of the application role that confers administrative privileges (e.g. BIServiceAdministrator or BIAdministrator)
Policy Store Provider
The policy store provider contains the Oracle Business Intelligence application-specific policies, application roles, permission grants, and membership mappings.
A policy store can be database-based or LDAP-based, but the installation default provides a policy store that is database-based.
Catalog privileges and permissions are not maintained in the policy store provider.
Oracle Business Intelligence Permissions
All Oracle Business Intelligence permissions and permission sets are provided; you cannot create additional permissions or permission sets. If you chose to configure your service instance based on the Sample Application, sample application policies and application roles are pre-configured to assign these permission sets according to the access requirements of the Oracle Business Intelligence common user types: administrator, author, and consumer. If you chose to import an 11g upgrade bundle into your service instance, the 11g permission grants will be used along with any new permission sets that were not available in 11g. Permission grants can be changed as needed using Fusion Middleware Control.
Note:
Permission set grants can be viewed in Fusion Middleware Control but can only be changed using WLST.