13 Switching to External Authentication
For maximum security in production environments, Oracle recommends integrating Oracle WebCenter Sites with Oracle Access Management, for an advanced identity management solution and a seamless single sign-on user experience. You also have the option of integrating WebCenter Sites with an external LDAP authentication provider directory.
The following topics describe how to configure WebCenter Sites for authentication against either external identity management solution:
- Switching to Authentication Against an LDAP Directory
This topic describes how to switch WebCenter Sites to authentication against an external LDAP authentication provider directory. This is a recommended solution for production environments if integration with Oracle Access Management is not viable. - Switching to Authentication Against Oracle Access Manager
You can configureWebCenter Sites for authentication against Oracle Access Manager. This solution is recommended for production environments.
Parent topic: Configuring WebCenter Sites Components
13.1 Switching to Authentication Against an LDAP Directory
This topic describes how to switch WebCenter Sites to authentication against an external LDAP authentication provider directory. This is a recommended solution for production environments if integration with Oracle Access Management is not viable.
- (Optional) Modify
ldap.caseAwareproperty value totrue, if the LDAP server you are using is case sensitive.By default the value ofldap.caseAwareis set tofalse. Sign in will fail if you are using a case-sensitive LDAP server and this property is set tofalse. To modify theldap.caseAwarevalue toTruefollow the steps:-
Sign in to the WebCenter Sites Admin interface and navigate to
Admin treetab>System Tools>Property Managementoption. -
Search for
ldapand change the value fromFalsetoTrue. -
Restart the Managed server.
Note:
During the integration of Sites with LDAP, if the users data in LDAP is separated by a comma the data does not get fetched. for example:test,user. To retrieve the data, you need to change the syntax in thedir.inifile located at..sites/installdirectory from"syntax.escape=\\ tosyntax.escape=\#". -
- Access the LDAP Configurator at
http://sites-host:sites-port/sites-context/ldapconfig, follow the instructions on the screen, and enter the values for your environment. - For LDAP rollback, restart the WebCenter Sites Managed Server, and go to the same LDAP Configurator URL.
Now there is only manual LDAP integration. Nothing is written to your LDAP Server, only an LDIF file is created under the
DOMAIN_HOME/wcsites/wcsites/config/ldapfolder (This is the default install location of WebCenter Sites application. All customizations and path modifications should be made after successful LDAP integration). Thepeopleparent,groupparent,username, and other fields are not prepopulated, as in the previous release. - (Optional) Modify the
LDIFfile located inNEW_DOMAIN_HOME/wcsites/wcsites/config/with values appropriate for your environment.Because the fields are not prepopulated, follow this example for
ORACLEDIR:ldap server type -- ORACLEDIR ldap DSN -- dc=oracle,dc=com ldap host -- localhost ldap port -- 389 ldap username -- cn=orcladmin ldap password -- password ldap peopleParent -- cn=Users,dc=oracle,dc=com ldap groupparent -- cn=Groups,dc=oracle,dc=com - If you choose Oracle Virtual Directory as your LDAP authentication provider, WebCenter Sites generates an
LDIFfile, which you can import to your Oracle Internet Directory server and then create an adaptar in Oracle Virtual Directory to connect to the Oracle Internet Directory server.You cannot import an LDIF file directly to an Oracle Virtual Directory LDAP server because it does not have a storage of its own.
- Import the
LDIFfile into the external LDAP authentication provider. - Restart the WebLogic Managed Server running this WebCenter Sites instance.
13.2 Switching to Authentication Against Oracle Access Manager
You can configureWebCenter Sites for authentication against Oracle Access Manager. This solution is recommended for production environments.
oamconsole and some configuration changes in the Sites.- Sign in to Oracle Access Manager Server through
oamconsole, for example:http://<oam_host:oam_port>/<oam console>/and configure a WebGate. See Integrating OAM with Oracle WebCenter Sites. - Deploy the
oamlogin.warandoamtoken.warapplication files located underNEW_ORACLE_HOME/wcsites/webcentersites/sites-homeon the WebLogic domain containing the targetWebCenter Sites instance. - Create the
wemsites_settings.propertiesproperty file underDOMAIN_HOME/wcsites/wcsites/config/. - Enter the values in the
wemsites_settings.propertiesfile as follows:Elements Properties oamredirecthttp://oam_server_host:oam_port/oam/server/auth_cred_submitoamlogoutoamlogout=http://oam_server_host:oam_port/oam/server/logoutforgotpasswordhelpdesk-email-address - Set the following properties in
NEW_DOMAIN_HOME/wcsites/wcsites/config/SSOConfig.xml. See Step 12 of Integration Steps.Elements Properties serviceUrlhttp://{ohs_server_host}:{ohs_port}/{sites_context_root}/RESTticketUrlhttp://{oamtoken_server_host}:{oamtoken_port}/oamtokensignoutURL
Use this URL when invokingWebCenter Sites logout. It includes the encoded URL where the browser will return after all logout processing has been completed by Oracle Access Manager.http://{oam_server_host}:{oam_port}/oam/server/logout?end_url={end_url}end_urlFor test (staging) and production (delivery) environments:
http%3A%2F%2F{ohs_server_host}%3A{ohs_port}%2F{sites_context_root}%2Fwem%2Ffatwire%2Fwem%2FWelcomedbUsernameName of theWebCenter Sites general Administrator user account. dbPasswordPassword for the WebCenter Sites general Administrator user account. Note:
Theohs_serverhost andohs_portcan be WebLogic host and port or any other HTTP server host and port depending on your configuration. For more information on OHS configuration, see Step 2 to Step 9 of Integration Steps. Add the below example for configuration inOAM OHS,mod_wl_ohs.conffile.<IfModule weblogic_module> <Location /oamlogin> SetHandler weblogic-handler WebLogicHost SITES_HOST WebLogicPort SITES_PORT </Location> </IfModule> <IfModule weblogic_module> <Location /sites> SetHandler weblogic-handler WebLogicHost SITES_HOST WebLogicPort SITES_PORT </Location> </IfModule> - Copy the
obAccsessClient.xmlandcwallet.ssofiles from your Oracle Access Manager instance into theNEW_DOMAIN_HOME/wcsites/wcsites/config/oblix/lib/directory on the targetWebCenter Sites instance.Note:
These files are auto-generated after the WebGate is configured. - Edit the
oamtoken.xmlfile in thesites-configdirectory by setting the compatibility mode andoblixpath. The compatibility mode should be set to11gand theoblixpath to thesites-configfolder under which you have theoblix/libfolder. - In the Oracle Access Manager configuration for WebCenter Sites, update the protected, public, and excluded resources as follows:
Figure 13-1 List of Protected, Public, and Excluded Resources for WebCenter Sites
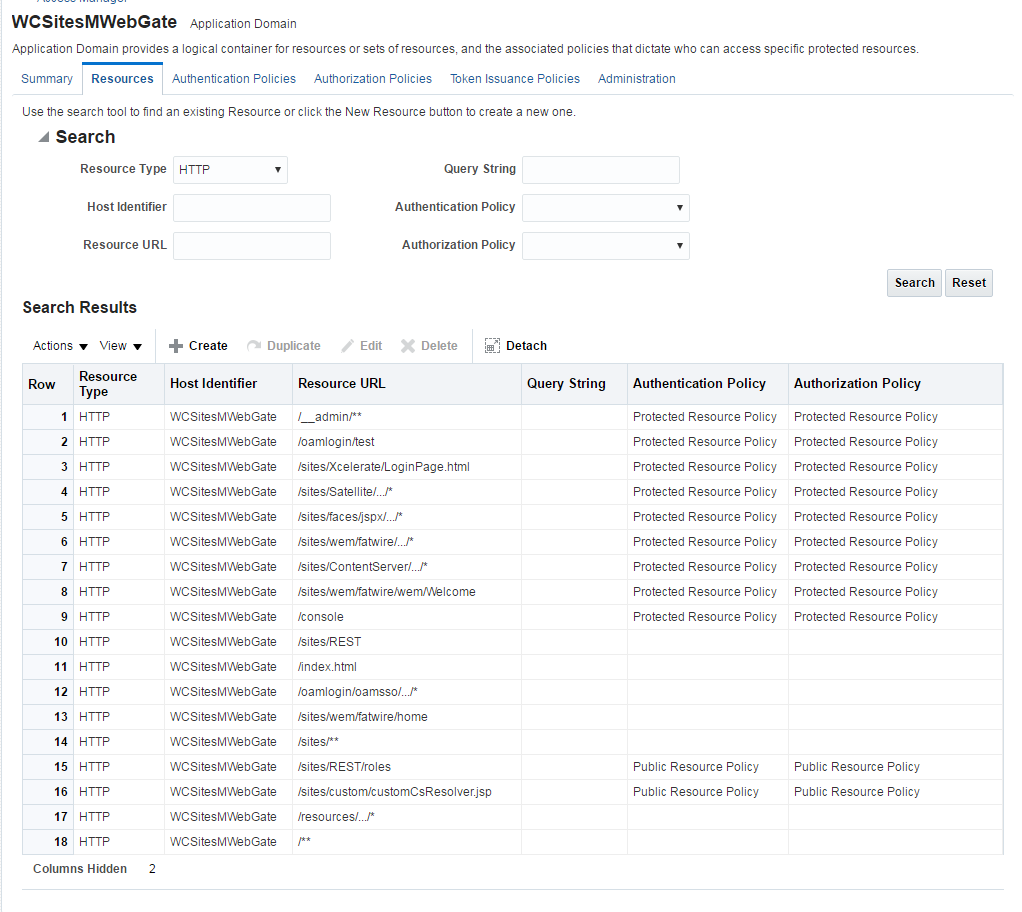
Description of "Figure 13-1 List of Protected, Public, and Excluded Resources for WebCenter Sites" - To integrate the OAMSDK Client with WebLogic Server as the
oamtoken.warapplication, edit thejps-config.xmlfile for the WebCenter Sites domain. By default, the WebLogic domain runs with this file, which is part of the WebLogic Server 12 c startup script:-Doracle.security.jps.config=NEW_ORACLE_HOME/user_projects/domains/DOMAIN_NAME/config/fmwconfig/jps-config.xml- Add a service instance, as the following example shows, next to existing service instances in the existing
jsp-config.xmlfile:<serviceInstance name="credstore.oamtoken" provider="credstoressp" location="./oamtoken"><description>File Based Credential Store Service Instance</description><property name="location" value="./oamtoken"/></serviceInstance>locationis the path to the directory that contains thecwallet.ssofile. The preceding example sets this path with reference to the currentjsp-config.xmlfile. Make sure theomtokenfolder is created with respect to the current directory and thecwallet.ssofile is placed there. Thelocationvalue can also be an absolute path to where thecwallet.ssofile is placed - Add
<serviceInstanceRef ref="credstore.oamtoken"/>under<jpsContext name="default">. - Add following
<jpsContext>element under<jpsContexts default="default">:<jpsContext name="OAMASDK"><serviceInstanceRef ref="credstore.oamtoken"/></jpsContext>
- Add a service instance, as the following example shows, next to existing service instances in the existing
- Add permissions so that code in
oamtoken.warcan be used.The WebGate instance created in Oracle Access Manager is accessed by the client. You need to add the credential to the WebCenter Sites domain so that the security restriction can be taken care of.- Launch the WebLogic Scripting Tool with the
wlst.shscript:cd NEW_ORACLE_HOME/oracle_common/common/bin/./wlst.sh - Connect to the Administration Server for the WebCenter Sites domain:
connect('user-name','password','sites-host:admin-port') - Grant the permissions:
grantPermission(codeBaseURL="file:/scratch/idc/newoam/rend/Oracle_Home/user_projects/domains/renddomain/servers/wcsites_server1/tmp/_WL_user/oamtoken/-",permClass="oracle.security.jps.service.credstore.CredentialAccessPermission",permTarget="context=SYSTEM,mapName=OAMAgent,keyName=*",permActions="*")The preceding path is basically the path where WebLogic Server has deployed theoamtoken.warapplication. - Restart the target WebCenter Sites Managed Server.
- Launch the WebLogic Scripting Tool with the
- (Optional) If trust betweenWebCenter Sites and Oracle Access Manager has not been established, modify the configuration of theWebCenter Sites web tier as follows:
- Sign in to the Oracle Access Manager Console.
- In the WebGate authorization policy (under the protected resource policy), go to the Responses tab.
- Enable (select) the Identity Assertion check box.
- Click Apply to save your changes.
- (Optional) If WebCenter Sites is deployed on a cluster is using OAM Integration. Following steps are required to be replicated on
oamticketcachecache.- In the config directory, we have
cas-cache.xmlwhere oamticketcache is configured by default. - Uncomment the commented section in the cache named
oamticketcachethe section appear as:<cacheEventListenerFactory class="net.sf.ehcache.distribution.RMICacheReplicatorFactory" properties="replicateAsynchronously=true, replicatePuts=true, replicateUpdates=true, replicateUpdatesViaCopy=false, replicateRemovals=true"/> <bootstrapCacheLoaderFactory class="net.sf.ehcache.distribution.RMIBootstrapCacheLoaderFactory" properties="bootstrapAsynchronously=false, maximumChunkSizeBytes=5000000" propertySeparator="," /> - Change the
cacheManagerPeerProviderFactoryas follows, make sure port is unique.<cacheManagerPeerProviderFactory class="net.sf.ehcache.distribution.RMICacheManagerPeerProviderFactory" properties="peerDiscovery=automatic, multicastGroupAddress=230.0.0.8, multicastGroupPort=40002, timeToLive=1" /> - The port should be different for
cacheManagerPeerProviderFactoryandcacheManagerPeerListenerFactoryas specified in the earlier steps. - All the cluster nodes should have same port for both the properties.
- In the config directory, we have
- For working on the
SSOConfig.xmlfile, follow the steps:- Modify the
SSOConfig.xmlfile of theWebCenter Sites deployment. This file controls the loaded authentication classes and the properties that are required by those classes. - Shutdown the Sites server.
- Backup the
SSOConfig.xmlfile located in theWEB-INF/classesdirectory of the deployed WebCenter Sites application.For example:/u01/software/Apps/OraMiddleware/user_projects/domains/OAMSitesDomain/wcsites/wcsites/config/SSOConfig.xml. - Modify
SSOConfig.xmlas follows:Note:
Further steps explains on setting properties for the following:serviceUrl,ticketUrl,signoutURL,dbUsername, anddbPassword. See Step 5. - The
signoutUrlproperty specifies the URL to be used when invoking WebCenter Sites logout. It includes the encoded URL where the browser will return after all logout processing has been completed by OAM. - For Sites management, use the following value for end_url: http%3A%2F%2F{ohs_server_host}%3A{ohs_port}%2F{sites_context_root}%2Fwem%2Ffatwire%2Fwem%2FWelcome
- For Sites delivery, use the following value for end_url: http%3A%2F%2F{ohs_server_host}%3A{ohs_port}%2F{sites_context_root}%2Fwem%2Ffatwire%2Fwem%2FWelcome
For the
dbUsernameanddbPasswordproperties, you can enter the credentials of the WebCenter Sites general administrator, which by default is fwadmin/xceladmin. The values for these properties will be encrypted on startup of the WebCenter Sites application.Note:
In the code example below, you will set the following properties:csServerUrl,serviceUrl, ticketUrl,signoutURL,dbUsername,dbPassword. See Step 5.<?xml version="1.0" encoding="UTF-8"?> <!-- Copyright (c) 2010 FatWire Corporation. All Rights Reserved. Title, ownership rights, and intellectual property rights in and to this software remain with FatWire Corporation. This software is protected by international copyright laws and treaties, and may be protected by other law. Violation of copyright laws may result in civil liability and criminal penalties. --> <beans xmlns="http://www.springframework.org/schema/beans" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:jdbc="http://www.springframework.org/schema/jdbc" xmlns:p="http://www.springframework.org/schema/p" xmlns:context="http://www.springframework.org/schema/context" xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans-3.1.xsd http://www.springframework.org/schema/jdbc http://www.springframework.org/schema/jdbc/spring-jdbc-3.1.xsd http://www.springframework.org/schema/context http://www.springframework.org/schema/context/spring-context-3.1.xsd"> <bean id="propertyConfigurer" class="org.springframework.beans.factory.config.PropertyPlaceholderConfigurer" /> <!-- Root Context: defines shared resources visible to all other web components --> <jdbc:initialize-database data-source="dataSource" enabled="true" ignore-failures="ALL"> <!-- For installer the first jdbc:script will opened. Installer will configure it automatically --> <jdbc:script location="classpath:crawler_oracle_db.sql" /> <!--jdbc:script location="classpath:crawler_hsql_db.sql" /--> <!--jdbc:script location="classpath:crawler_sql_server_db.sql" /--> <!--jdbc:script location="classpath:crawler_oracle_db.sql" /--> <!--jdbc:script location="classpath:crawler_db2_db.sql" /--> </jdbc:initialize-database> <!-- Section# 1 Installer will consume below configuration to configure a datasource name created on the appservers --> <bean id="dataSource" class="org.springframework.jndi.JndiObjectFactoryBean"> <property name="jndiName" value="wcsitesDS"/> </bean> <!-- Single Sign On provider --> <bean id="ssoprovider" class="com.fatwire.wem.sso.oam.OAMProvider"> <property name="config" ref="ssoconfig" /> </bean> <!--It is invoked by the OAM filter to resolve an OAM authenticated user against a remote Site CS instance.--> <bean id="oamIdentity" class="com.fatwire.auth.identity.RemoteUsernameResolver" > <property name="csServerUrl" value="http://{ohs_server_host}:{ohs_port}/{sites_context_root}/custom/customCsResolver.jsp"/> </bean> <!-- Single Sign On filter --> <bean id="ssofilter" class="com.fatwire.wem.sso.oam.filter.OAMFilter"> <property name="config" ref="ssoconfig" /> <property name="provider" ref="ssoprovider" /> <property name="identityResolver" ref="oamIdentity" /> <!-- Set "trustConfigured" to "true" in case of trust relationship configured between WebGate and WLS. It will turn off check for OAM_ASSERTION header. --> <property name="trustConfigured" value="false" /> </bean> <!-- Single Sign On listener --> <bean id="ssolistener" class="com.fatwire.wem.sso.oam.listener.OAMListener"> </bean> <!-- Single Sign On configuration --> <bean id="ssoconfig" class="com.fatwire.wem.sso.oam.conf.OAMConfig"> <!-- URL prefix for REST service endpoint --> <property name="serviceUrl" value="http://{ohs_server_host}:{ohs_port}/{sites_context_root}/REST" /> <!-- URL prefix for Token Service servlet --> <property name="ticketUrl" value="http://{oamtoken_server_host}:{oamtoken_port}/oamtoken" /> <!-- URL to be called when WEM logout is required. --> <property name="signoutUrl" value="http://{oam_server_host}:{oam_port}/oam/server/logout?end_url=http%3A%2F%2F{ohs_server_host}%3A{ohs_port}%2F{sites_context_root}%2Fwem%2Ffatwire%2Fwem%2FWelcome"/> <!-- Do not proxy tickets, tt's the last server in thecall chain --> <property name="proxyTickets" value="false" /> <!-- Database Credentials needed by user lookup inOAMFilter --> <property name="dbUsername" value="fwadmin" /> <property name="dbPassword" value="xceladmin"/> <!-- Your application protected resources (relative to applicationUrl) --> <property name="protectedMappingIncludes"> <list> <value>/__admin</value> <value>/__admin/**</value> </list> </property> <!-- Your application protected resources excludes (relative to applicationUrl) --> <property name="protectedMappingExcludes"> <list> <value>/__admin/layout</value> </list> </property> <property name="applicationProxyCallbackPath" value="/sso/proxycallback" /> <property name="gateway" value="false" /> </bean> <context:component-scan base-package="com.fatwire.crawler.remote.dao" /> <context:component-scan base-package="com.fatwire.crawler.remote.support" /> <context:component-scan base-package="com.fatwire.crawler.remote.di" /> <context:component-scan base-package="com.fatwire.crawler.remote.resources.support" /> </beans>
- Modify the