50 Implement Oracle Fusion Data Security
This chapter includes the following sections:
50.1 Introduction to Oracle Fusion Data Security
Oracle Fusion Data Security is the technology that implements data security in Oracle Fusion Applications and is not used by function security (Oracle Platform Security Services (OPSS) is used for function security). Oracle Fusion Data Security integrates with Oracle Platform Security Services (OPSS) by granting actions to an OPSS principal. The grant defines who (the principal) can do what (the actions) on a given resource. A grant in Oracle Fusion Data Security can use any enterprise user or enterprise group as principals. Oracle Fusion Data Security assumes that the connection or session provided to it has been initialized properly with the appropriate user session user context, as described in Implementing Application User Sessions.
Note:
In this chapter, the user session is specifically an application user session (ApplCore). The application user session is the session that Oracle Fusion Data Security expects to see.
The goal of Oracle Fusion Data Security is to authorize a user to perform specified actions on selected data. It can secure rows and attributes of a database object and relies on OPSS to provide the authentication services for OPSS principals (users, groups, or roles). It answers the question "Who can do what on which set of data". Who refers to the OPSS user or group (or role), what is the action, and which is the subset of data that can be accessed.
You can use Oracle Fusion Data Security to either restrict the rows that are returned by a given query based on the intended business operation or you can restrict the actions that are available for a given row.
The purpose of data security is to model and enforce security authorization for a specific data record or a set of records. Data security provides access control within Oracle Fusion applications on the data a user can access and the actions a user can perform on that data. Oracle Fusion application rely on data security to restrict access to individual data that is displayed on a page that may display after the user has selected a menu or menu option.
The following are some use cases where Oracle Fusion Data Security can be utilized:
-
Grant read action on expense reports to managers of the current employee when the manager is granted Expenses Administrator role.
-
Administer the list of documents available to an end user in a Document Management System (DMS) based on Document Categories.
-
Show the list of Sales Opportunities available to a Sales Head of an organization based on region.
-
Allow a Human resources (HR) Benefits Administrator to only administer the employees whose last name begins with A-F.
-
Allow a HR Administrator to only administer the employees in a given region.
In Oracle Fusion Data Security, data that must be secured is identified as resources. These resources are database tables or views. Policies that control which data that a user has access and can perform actions, can be made on a row instance or condition. The following figure illustrates the logical data model implemented by Oracle Fusion Data Security.
Figure 50-1 Oracle Fusion Data Security — Logical Data Model
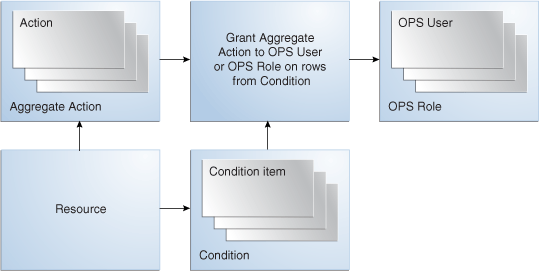
An instance is a row of data and is identified by the primary key value of the row in the resource's storage table. A condition is a group of row instances whose membership is determined by a rule in the form of a SQL predicate, which must be applicable to the WHERE clause of a single-table query against the resource's storage table.
For example, each row in the Purchase Order table is an instance of the Purchase Order resource. The purchase order number is the primary key that identifies a particular purchase order instance. You can create an condition with the predicate "PO_NUMBER=100", which contains just one row of data. Purchase orders from the West region can be put into a condition that is defined by the predicate "REGION='WEST'". A condition that contains all the rows of data in the resource's storage table can be defined by the predicate "1=1".
Memberships of a condition are dynamic in many ways, such as:
-
Condition membership rules may contain any valid SQL attributes, such as columns of a table. Adding new instances or updating existing instances may affect the membership of a condition. Using the above Purchase Order example, if the predicate is
"REGION='WEST'", new purchase orders in the region of West will automatically become a member of the condition. -
When an action is granted to an OPSS application role (also called a duty role by Oracle Fusion Applications) on a condition it can be parameterized. Using the Purchase Order example, the condition may be defined by the predicate
"REGION=&PARAM"where the parameterPARAMis associated with different regions. When an action is granted on a condition, it may be done for a particular value of the parameter, such as a sales manager in the West region may have an action granted on a Region condition with the parameter value West. -
The condition rules may not reveal any membership at all. It can just be a
WHEREclause to filter rows based on runtime user session variables.
To grant data security actions to a user, you must first identify the resources that you want to secure, define conditions on those resources, and then grant specific actions on these conditions to the application role to which the user belongs.
For additional information about Oracle Fusion Data Security, see the product-specific security guides.
Related Links
The following document provides additional information about Oracle Fusion Middleware topics discussed in this section:
-
For additional information about OPSS, see the Oracle Fusion Middleware Securing Applications with Oracle Platform Security Services guide, in the Oracle Fusion Middleware Online Documentation Library.
50.1.1 Terminology
Resource: A resource on which data security is enforced, such as a purchase order. Resources are stored in the Oracle Fusion Applications FND_OBJECTS table. Note that Oracle Fusion Applications database tables are sometimes called FND tables, where FND refers to resources in the "foundation" tables.
Instance: A particular item of an resource, such as PO_NUMBER 100. An instance generally corresponds to a row in the database. Row instances have one or more primary key values.
Condition: A group of row instances that are determined by a SQL predicate (WHERE clause expression) that queries the attributes of the resource itself. The WHERE clause can reference values from the database context to implement relative conditions where the condition members depend on the security context of the current user. The conditions may also be parameterized, meaning that the WHERE clause references PARAMETER values from the policies for parameterized conditions, as described in How to Use Parameterized Conditions When Securing a Business Object.
Conditions are stored in FND_OBJECT_INSTANCE_SETS table.
Action: Secures an action (also called a function, privilege, or permission) that can be performed on a resource. You typically build features using multiple implementation strategies, including various ADF Business Components operations through Java code. These features must be secured to prevent unauthorized execution of the code. These features generally perform events on resources and actions and they are the artifacts used to secure these events. Actions are stored in FND_FORM_FUNCTIONS table, and the action names within the table are not unique. Only an action used in combination with a resource is unique.
Aggregate Action: A group of actions. Roles specify the combination of actions necessary to perform a particular role on a row instance. For example, a Project Administrator role may include the View, Update, Slip, and Delete actions and a Project Worker role may include only the View and Update actions. Aggregate actions (also called a menu) are stored in FND_MENU and FND_MENU_ENTRIES tables.
Principal (Grantee): A user or a role in Oracle Platform Security Services (OPSS) to which Oracle Fusion Data Security has a reference. The grantee key in the FND_GRANTS table holds the GUID of the OPSS user or role.
User (OPSS User): Any person or application that accesses information in the database.
Role (OPSS Role): Composed of users, groups, and possibly other roles. Roles are used to associate users with actions.
Policy: Authorization for the grantee (OPSS user or role) of an aggregate action may be done on the specified row instance, all instances, or condition. The condition for a policy may be static or parameterized. A policy logically joins a principal, aggregate action, and condition. This has the following effects:
-
Any action granted on a row instance implies that the Oracle Fusion Data Security runtime system always has the ability to query the instances. This can be used by a standard Virtual Private Database (VPD) policy function to provide default query filtering. However, this does not mean that you have the ability to view or query because the ability to view a row of the resource is secured by an action.
-
In the context of a specific row instance, the policies specify the set of actions that can be performed on a data record.
Resource access can be tested using the Oracle Fusion Data Security authorization checking API. Policies are stored in FND_GRANTS table.
VPD - Virtual Private Database: Provides the ability to dynamically attach a predicate at runtime to all queries issued against a database object (table or view). This feature is available in Oracle RDBMS. For more information about implementing VPD, see Integrating Oracle Fusion Data Security with Virtual Private Database (VPD).
Security Policy Function: A PL/SQL function developed to return a predicate added by VPD to a query. This function is bound to a table or view for some or all of DML statement types: SELECT, INSERT, UPDATE, DELETE.
50.1.2 Integrating Oracle Fusion Data Security with Oracle Platform Security Services (OPSS)
When integrating Oracle Fusion Data Security with Oracle Platform Security Services (OPSS) to support making policies to OPSS principals, it is important to understand that OPSS principals may be defined in third-party systems and this data does not exist in the database. Only the necessary information (user/user-role mapping) for the current user session is propagated to the database at runtime during session creation to determine the various actions granted for that user session.
At runtime when a user session is created, the user information for that session and the flattened list of roles (to include role hierarchies) for the user of that session is propagated to the database. The roles available in a user session may be different from all the roles that a user may potentially have based on the authentication mechanism used, such as password vs. biometrics, authentication level of DMZ vs. non-DMZ, and so on. OPSS principal information is not stored in the Oracle Fusion Data Security schema.
50.1.3 Integrating Data Security Task Flows into Oracle Fusion Functional Setup Manager
Every Oracle Fusion application registers ADF task flows for setup activities with a product called Oracle Fusion Functional Setup Manager. These task flows are available from the Fusion Applications Setup and Maintenance work area and enable customers and implementers to set up and configure business processes and products. For more information about data security tasks, see the product-specific security guides.
If data security task flows are used in a web application, that web application must be configured to use ADF Security to enable authentication and authorization so that the correct data security predicates are generated.
Additionally, ADF Security controls access to a specific task flow, and users who do not have the required permission cannot view the task flow. For more information about how to implement function security permissions and roles, see Implementing Function Security .
The following table lists the task flows and their parameters.
Table 50-1 Data Security Task Flows and Parameters
| Task Flow Name | Task Flow XML | Parameters Passed | Behavior | Comments |
|---|---|---|---|---|
|
Manage Database Resources |
/WEB-INF/oracle/apps/fnd/ applcore/dataSecurity/ui/ taskflow/DBResourceTF.xml |
|
Goes to the Search page for database resources. |
None. |
|
Manage Database Resource |
/WEB-INF/oracle/apps/fnd/ applcore/dataSecurity/ui/ taskflow/CreateDBResourceTF.xml |
|
Goes to the Edit page for a database resource. |
None. |
|
Manage Database Resource Conditions |
/WEB-INF/oracle/apps/fnd/ applcore/dataSecurity/ui/ taskflow/CreateDBResourceTF.xml |
|
Goes to the Conditions tab of the database resource Edit page. |
Conditions are a child entity of database resource. There is no Search page for conditions across all database resources; therefore, DB resource ID is mandatory. |
|
Manage Database Resource Actions |
/WEB-INF/oracle/apps/fnd/ applcore/dataSecurity/ui/ taskflow/CreateDBResourceTF.xml |
|
Goes to the Actions tab of the database resource edit page. |
Actions are a child entity of database resource. There is no Search page for actions across all database resources; therefore, DB resource ID is mandatory. |
|
Manage Policy |
/WEB-INF/oracle/apps/fnd/ applcore/dataSecurity/ui/ taskflow/PolicyTF.xml |
|
This is the Create/Edit Policy page |
There is no Search here, except to pick a specific database resource and pick a specific role. |
50.1.4 Integrating Oracle Fusion Data Security with User Sessions
Oracle Fusion Data Security integrates with user sessions and relies on session context to be implemented properly.
For information about implementing user sessions, see Implementing Application User Sessions.
If a session has been created successfully, you will see the session created in the FND_SESSIONS table and the user session roles in the FND_SESSION_ROLES view.
When making policies to an OPSS principal, the GRANTEE_KEY must be a valid User / Role GUID as identified in the jazn-data.xml file. At runtime, the list of roles available to the user is determined by the roles granted to the user in the jazn-data.xml file and is populated in the FND_SESSION_ROLES view.
50.1.5 Integrating Oracle Fusion Data Security with Virtual Private Database (VPD)
Note that integrating with VPD is optional.
The database has a feature called Virtual Private Database (VPD). VPD allows an arbitrary WHERE clause to be appended to a table, view, or synonym. By doing so, the WHERE clause restricts the rows available. A PL/SQL function is written that returns the WHERE clause and a VPD policy is enabled on a particular table, view, or synonym that references that policy function. VPD policy functions based on fnd_data_security.get_security_predicate() are used to enforce data security rules.
Note:
If the base table holds PII data (personally identifiable information), the VPD policy must be created on the table and not on a view or synonym. If the policy is created only on a view or synonym, there is no protection against users accessing PII data from SQL*Plus. Setting the policy on the base table ensures that any PII data cannot be accessed by unauthorized users.
To integrate with VPD:
-
Create an action.
Use Setup and Maintenance - Manage Data Security Policies UI to create an action on the database resource that you want to secure.
-
When the base table contains no PII data, create a view or synonym.
If the table contains PII data, you will add the VPD policy directly to the table. Otherwise, create a view or synonym with the exact same name as the action.
-
Add a VPD policy to the table or view.
Add a VPD policy in the database that will associate the policy function with the table or view.
At runtime, in LOVs or UIs, wherever you want to display the rows that the user has select access to, they simply select off that view.
50.2 Managing Data Security Artifacts in the Oracle Fusion Data Security Policy Tables
Oracle Fusion Data Security artifacts include resources, row instances, conditions, actions, aggregate actions, and so on. Data security artifacts are stored in the Oracle Fusion Data Security repository and are customized using Oracle Authorization Policy Manager, which can be accessed by the developer through Oracle Fusion Functional Setup Manager, from the Manage Data Security task available in the Setup and Maintenance work area of any Oracle Fusion Setup application.
Note:
After the developer selects the Manage Data Security task in Oracle Fusion Functional Setup Manager, the environment redirects to the data security customization user interface provided by Oracle Authorization Policy Manager. In this document, although the data security customization tool is identified as Oracle Authorization Policy Manager, be aware that the tool must be accessed through Oracle Fusion Functional Setup Manager.
For details about creating and editing policies, see the "Managing Data Security Policies" topic in the Oracle Authorization Policy Manager online help. For supplemental task instructions, see the "Customizing Security for Oracle ADF Application Artifacts" chapter of the Extensibility Guide for Developers.
50.2.1 How to Get Started Managing Data Security
The user who logs in to view and manage database resources and policies must be authorized based on one of the roles described in Table 50-2.
Use cases:
-
Application developer must be able to manage database resources for all Oracle Fusion resources.
-
Product-family administrator must be able to manage only the database resources for their specific product family.
To use the standard Application Developer role:
The Oracle Fusion reference implementation predefines an Application Developer job role that inherits all the roles described in Table 50-2. You must contact a system administrator for Oracle Fusion Human Content Management (HCM) and request to be provisioned with the Application Developer job role. During the role provisioning process, you will be notified about the details of your account and password.
-
Login to Functional Setup Manager with your account user name and password.
Alternatively, to use your own Product Family Administration role:
For example, if you have a CRM product family administration role, you must be able to manage the CRM database resources, but you will not be allowed to access the HCM resources.
If you have your own Product Family Administration role:
-
In Oracle Authorization Policy Manager, login as the user who is assigned to the appropriate duty role for your product family.
-
Inherit the appropriate duty role for your product family from the duty roles listed in Table 50-2.
-
Define the relationship between duty role and enterprise role.
How Oracle Authorization Policy Manager supports managing policies for database resources:
-
Oracle Fusion Applications delivers the duty roles and policies as specified.
-
Oracle Authorization Policy Manager authors enterprise roles and maps the duty roles listed in Table 50-2. A security manager uses Oracle Authorization Policy Manager to define the relationship between a duty role and enterprise roles.
-
A security manager can create their own enterprise roles if required. They can determine which database resources can be managed by specific data security administrators by including the duty roles into their custom enterprise roles. Security managers are expected to use Oracle Authorization Policy Manager to perform enterprise role to duty role mapping.
-
Policies runtime is based on role GUIDs only.
Reasoning:
Data security policies are granted to duty roles as the default approach. This makes it possible for the security manager to quickly assemble the duties to an enterprise role and use the Oracle Fusion reference implementation quickly. Granting them to an enterprise role means that the security manager must duplicate the policies to any new enterprise roles they create. Enterprise roles are highly guarded and should be created and used only if absolutely needed.
50.2.2 What You May Need to Know About Administering Oracle Fusion Data Security Policy Tables
The data security administration UI is secured so that only administrators are permitted to create and manage security policies.
Note:
You cannot view the database resources or manage policies from the Functional Setup Manager if you have not been granted the appropriate data security manage permissions. Contact your security administrator for details.
The following table lists the duty roles that have been predefined by the Oracle Fusion security reference implementation to allow users to manage data security. These roles are administered at the product family level to manage resources and policies for that specific product family. The security reference implementation provides role-based access control in Oracle Fusion Applications, and is composed of predefined security policies that protect functions, data, and segregation of duties. Note that the table also identifies the duty roles associated with Oracle Authorization Policy Manager (APM) which allow developers to manage product family data security policies using the Manage Data Security Policies task.
Table 50-2 Duty Roles to Manage Data Security Policies
| # | Family | Duty Role |
|---|---|---|
|
1 |
CRM |
Customer Relationship Management Database Resource Administration Duty |
|
2 |
HCM |
Human Capital Management Database Resource Administration Duty |
|
3 |
FSCM |
Financials and Supply Chain Manufacturing Database Resource Management Duty |
|
4 |
APM - CRM |
APM - CRM Database Resource Administration Duty |
|
5 |
APM - HCM |
APM - HCM Database Resource Administration Duty |
|
6 |
APM - FSCM |
APM - FSCM Database Resource Administration Duty |
50.3 Integrating with ADF Business Components
In Oracle Fusion applications, the data to be secured is typically defined in the application's data model project by an ADF Business Components entity object. Oracle Fusion Data Security integrates with ADF Business Components so that when you are defining an ADF Business Components entity object you can:
-
Identify the actions that are available on a given row
-
Have the ability to check at runtime if the user has access to this row based on the policies that are available to that user.
At runtime, authorization check is done automatically by ADF Business Components for standard operations that the Oracle Fusion application developer has declaratively enabled for business components, such as read, update, and removeCurrentRow. To perform a security check on non-standard operations you must call Oracle Fusion Data Security APIs directly.
Developers declaratively enable security for the desired operations on the ADF Business Components entity objects of their data model project. You may not identify operations directly on an ADF Business Components view object; however, when a view object references an entity object whose operations have been secured, the entity security policies also apply to the view object. In this regard, application developers must opt into security for individual business objects.
Oracle Fusion Data Security provides an implementation of a data security provider interface defined by ADF Business Components to perform the authorization check. The ADF Business Components data security provider interface provides a mechanism to filter rows based on a permission and to perform permission checks for certain actions. At runtime, Oracle Fusion Data Security uses an implementation of this interface to secure access to ADF Business Components entity objects and view objects.
50.3.1 How to Configure the ADF Data Model Project
To make the Oracle Fusion Data Security Provider as your data model project's data security provider, you can edit the Oracle Fusion application's adf-config.xml file to define the dataSecurityProviderClass attribute for the sec:JaasSecurityContext element, as shown in the following example.
For example, the adf-config.xml file would contain the sec:JaasSecurityContext element definition shown in the following example.
In Oracle JDeveloper, the design time tools for ADF Business Components are shaped so that the Oracle Fusion Data Security Provider will be automatically registered as the default when you launch JDeveloper with the Oracle Fusion Applications Developer role selected. This occurs when the developer runs the Configure ADF Security wizard for the ADF data model project.
At runtime, the ADF Business Components invocation of Oracle Fusion Data Security Provider happens automatically only for standard operations that have been enabled for entity objects of the data model project. For custom operations that are available on the entity object, you must invoke the Oracle Fusion Data Security authorization checking API manually, as described in How to Perform Authorization Checks for Custom Operations.
There may be other reasons to invoke Oracle Fusion Data Security APIs manually to determine the SQL predicate for a given action or to do an authorization check. For example, you might query VPD policies written based on fnd_data_security.getSecurityPredicate() to enforce data security rules.
Example 50-1 Making the Oracle Fusion Data Security Provider the Data Security Provider
dataSecurityProviderClass= "oracle.apps.fnd.applcore.dataSecurity.util.FndDataSecurityProvider"
Example 50-2 sec:JaasSecurityContext Element Example
<sec:JaasSecurityContext intialContextFactoryClass= "oracle.adf.share.security.JAASIntialContextFactory" jaasProviderClass="oracle.adf.share.security.providers.jps.JpsSecurity.Context" dataSecurityProviderClass= "oracle.apps.fnd.applcore.dataSecurity.utl.FndDataSecurityProvider" authorizationEnforce="true" authenticationRequire="true"/>
50.3.2 How to Secure Rows for Read, Update and Delete Access
At design time, you secure the read, update, and delete operations on a given entity object using Security section in the General page of the entity object overview editor. The overview editor exposes a set of standard operations (read, update, removeCurrentRow) as checkboxes that you can select. Until you select these operations, read, update, and delete access will not be enforced and therefore rows queried by entity-based view objects will remain accessible to users. Thus, to secure rows of data, the application developer must opt into security by enabling security for the standard row-level operations on the entity object, as shown in the following figure.
Figure 50-2 Entity Object Overview Editor — Security Section
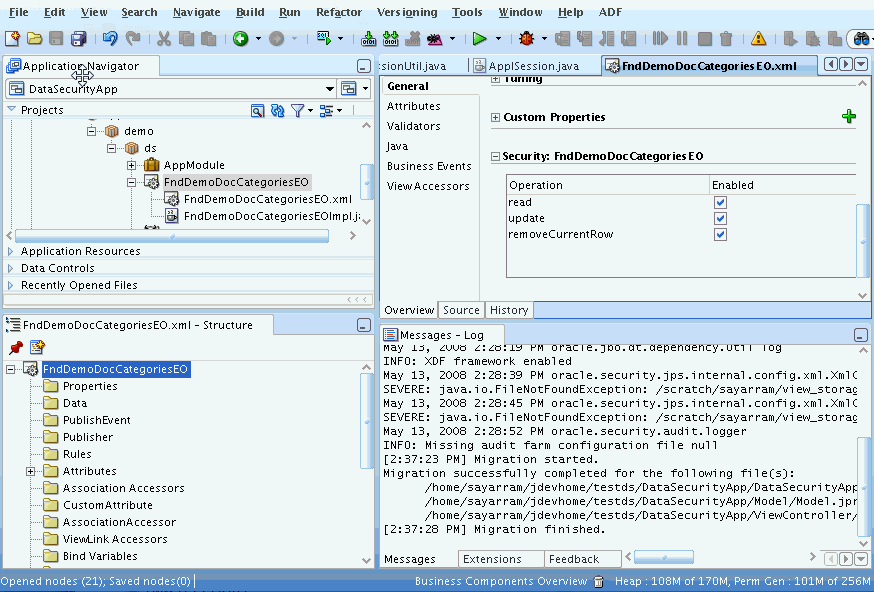
To secure the entity object standard operations:
50.3.3 How to Secure Rows for Custom Operations and Specific View Objects
Certain situations exists where it is preferable to secure operations at the level of view objects instead of a single entity object which protects access from all view objects derived from the entity object. In this sense, security at the level of view objects provides a more granular level of access control. Additionally, in cases where custom action checks needs to be performed, it is necessary to secure the view instance by applying a named view criteria defined for the purpose.
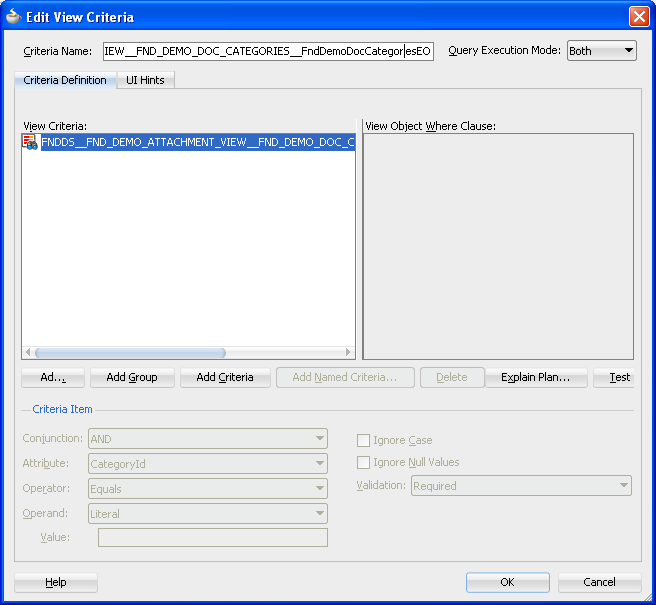
In the case of securing rows at the level of specific view objects, you use the View Criteria section of the General page of the overview editor for the view object to create the named view criteria. The following figure shows a view criteria that has been added in the overview editor for the view object.
Figure 50-3 View Object Overview Editor — View Criteria Selection
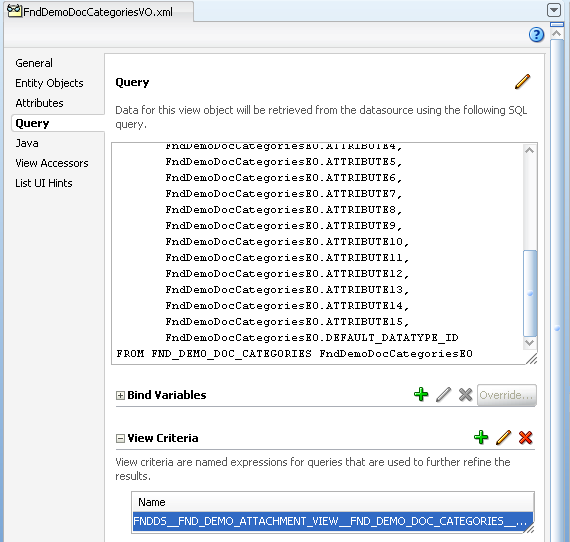
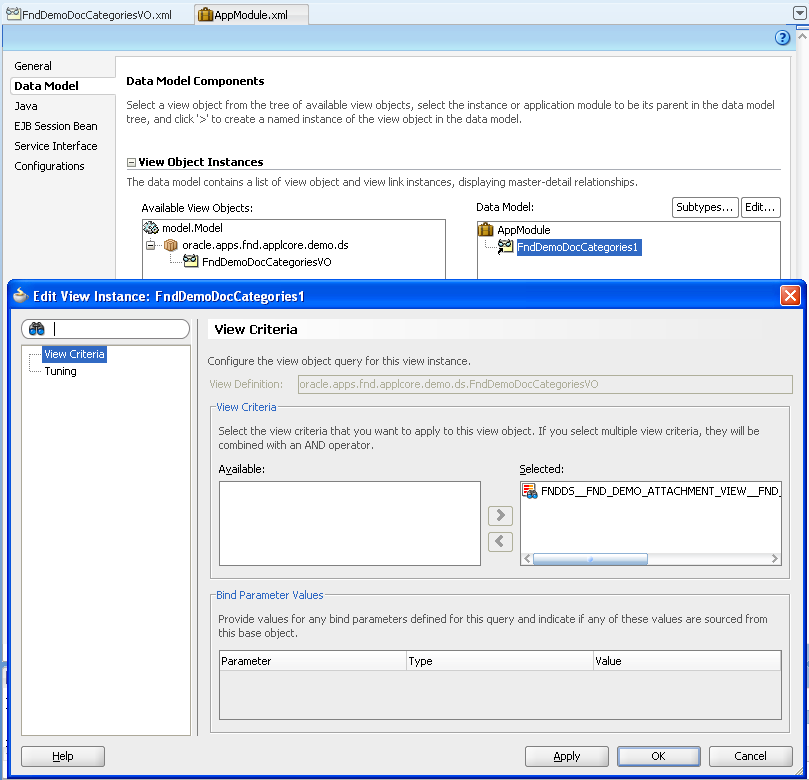
Once you have defined the view criteria, you must apply it to the view instance that you want the application module data model to filter, as described in the following procedure.
To secure rows displayed to a user from a view object for a custom action:
50.3.4 What You May Need to Know About Naming Actions
This means that when you define actions in Oracle Fusion Data Security, the actions for those business objects must be named as read, update, or delete to correspond to the entity object security operations that get enabled. Note that the action name corresponding to the removeCurrentRow operation is identified as delete by Oracle Fusion Data Security.
Similarly, when you create custom actions in Oracle Fusion Data Security, the action name that you define must match the custom action specified on the entity object.
50.3.5 What You May Need to Know About Column-Level Security
Oracle Fusion Data Security Provider only implements row-level authorization check. It does not implement a column-level authorization checking API. Even though Oracle Fusion Data Security can be used to perform column-level security using custom actions, it is not integrated with ADF Business Components directly using the data security provider interface. Wherever column-level security is needed, you must use a custom action.
50.3.6 What You May Need to Know About Translatable Entity Objects
The default Oracle Fusion Data Security provider implementation assumes that the object name in FND_OBJECTS for the entity object being secured is the database table/view name backing this entity object. If the entity object is a translatable entity object (MLS entity), then the backing database table/view name is identified by Oracle Fusion Middleware Extensions for Applications custom property fnd:OA_BASE_TABLE.
If the default behavior used to identify the backing database table/view name is not sufficient, one can use the entity object overview editor to set a custom property on the entity object. This custom property will identify the name of the object from the Oracle Fusion Data Security repository that will be used to secure this entity. The custom property OA_DS_BASE_TABLE should be set in the Custom Properties section in the General page of the entity object overview editor to accomplish this.
50.3.7 What Happens at Runtime: How Oracle Fusion Data Security Filters View Instance Rows
Based on standard operations that you enable for entity object security, the appropriate row-level permission checks are done at runtime. To enable these checks to happen automatically, JDeveloper registers the Oracle Fusion Data Security Provider with ADF Business Components in the adf-config.xml file when you secure an operation on the entity object.
At runtime, in the case of standard entity object operations that have been secured, ADF Business Components invokes the Oracle Fusion Data Security Provider in two steps:
-
The security provider first identifies the
WHEREclause (if any) that must be added to the SQL statement for the entity object on which thereadoperation has been secured. This is done before executing the query. -
After the query has been executed, ADF Business Components then invokes the Oracle Fusion Data Security Provider again to perform the authorization check for the
updateandremoveCurrentRowoperations to determine whether user has update and delete access to that row.
The implementation for securing data by applying a view criteria on the view object instance is handled in the Oracle Fusion Middleware Extensions for Applications layer. It requires the use of Oracle Fusion Middleware Extensions for Applications base classes to achieve this behavior. The OAViewCriteriaAdapter class is the default view criteria adapter class set as the ADF Business Components application module in the OAApplicationModuleImpl class. This functionality is provided in the OAViewCriteriaAdapter.getCriteriaClause() method to fetch the security predicate. In this implementation, the method uses the metadata on the view criteria to invoke Oracle Fusion Data Security APIs that fetch the security predicate.
In the case of a custom operation secured by a custom action, multiple data security view criteria can be applied to the view object. When multiple view criteria are applied, the WHERE clause corresponding to each view criteria is AND'ed. This is standard behavior for ADF Business Components. However, when a single data security view criteria for a given permission is applied, the instance sets corresponding to that permission are OR'ed. When multiple permission checks are applied, the instance sets of a permission are AND'ed with the instance sets of another permission. For example, for an object, for permission perm1, the user has instance sets IS1, IS2. For the same object for privilege priv2, the user has instance sets IS3, IS4. If both perm1 and perm2 checks are applied simultaneously (using view criteria), the WHERE clause would be (IS1 OR IS2) AND (IS3 OR IS4).
50.3.8 How to Perform Authorization Checks for Custom Operations
At runtime, the ADF Business Components invocation of Oracle Fusion Data Security Provider happens automatically only for standard operations. For custom operations that are available on the entity object, you must invoke the authorization check API manually as shown in the following example.
Note that the allowsOperation() method expects as input the secured operation name rather than the name of the action that secures it. In the case of the standard operations, the operation name for deleting an entity row is removeCurrentRow (where delete is the action name).
There may be other reasons to invoke Oracle Fusion Data Security APIs manually to determine either the SQL predicate for a given action or to do an authorization check. For example, VPD policies written based on fnd_data_security.getSecurityPredicate() to enforce data security rules.
Example 50-3 Manually Invoking the Authorization Checking API
if(row.getSecurityHints().allowsOperation("ApprovePO").hasPermission())
// code for PO approval
else
// display error message
50.3.9 How to Test Permissions Using Expression Language Expressions in the User Interface
You can test data security actions for standard operations (read, update, removeCurrentRow) or custom operations on an entity row using Expression Language or Groovy expression exposed on the entity row.
The Expression Language and Groovy expressions described below work by default when the view object is an updateable view object based on an entity object. If the view object is a read-only view object (based on an entity object) or an expert mode view object, then Expression Language or Groovy expression will not work unless you create a transient attribute with a custom Groovy expression that invokes Data Security to check the operation. The transient attribute can be used to control the rendering of some other attribute in the read-only view object on the page.
-
The following example shows the Expression Language expression to use on ADF bindings for view object attributes.
For example, your UI might have a button to control the grant for the
UpdateEmployeeSalarycustom action; the Expression Language expression on the button may be defined as shown in the following example.When this expression is invoked, Oracle Fusion Data Security Provider checks to see if the user identified by the
PersonIdattribute has access to the current row forUpdateEmployeeSalaryoperation. Note that even though the attribute name is included in the Expression Language expression, it is really doing a row-level security check.Do not use the expression shown in the following example as Oracle Fusion Data Security Provider does not implement a column-level security check interface. If you want to perform a column-level security, use the expression shown in the previous example with a custom action.
-
The following example shows the expression to use for table iterators:
Do not use the expression shown in the following example as Oracle Fusion Data Security Provider does not implement column-level security check interface. If you want to do column-level security, use the expression shown in the previous example with a custom action.
-
When using Expression Language, be careful if you decide to set the expression on the
renderedattribute. When PPR is enabled, ADF Faces does not handle therenderedattribute on a UI component well.Tip:
PPR is enabled by default in Oracle Fusion Applications.
If you want to use Data Security expressions on the
renderedattribute, you must manually identify the partial trigger UI components on the page and then set thepartialTriggersattribute on the parent UI component of the UI component that has the data security Expression Language expression. Do not usevisibleattribute on the UI component as this could potentially be a security hole when the UI component and its data is rendered by the server and sent to the client. Thevisibleattribute is a client-side attribute to show or hide the UI component on the browser. -
When using Groovy expressions, use the expression shown in the following example if the view object is an updateable view object based on an entity object.
-
When using Groovy expressions, use the expression shown in the following example if the view object is a read-only view object based on an entity object or an expert mode view object. Create a transient attribute on the view object of type Boolean and Value Type Expression. The transient attribute can be used to control the rendering of some other attribute in the read-only view object on the page.
For example, you have a read-only view object with the attributes
PersonId,Name,Gender, andAgeand you want to control the rendering of theGenderattribute on the UI. First, you should create a transient attribute by nameTransientGenderAttrand set the Groovy expression as mentioned above. The following example shows an EL expression to conditionally render the UI component for theGenderattribute:You must make sure that the parent UI component of this UI component has the
partialTriggersset to the appropriate UI component IDs. Also, in this scenario, make sure to have the binding available for the transient attribute in the view object, and to set therendered="false"on the UI component for the transient attribute, or comment out the UI component in the JSF page.
Example 50-4 Using Expression Language on View Object Attributes
#{bindings.<attrName>.hints.allows.<operationName>}
Example 50-5 Correct Expression Language Expression Example
#{bindings.PersonId.hints.allows.UpdateEmployeeSalary}
Example 50-6 Incorrect Expression Language Expression Example
#{bindings.<attrName>.hints.<attrName>.allows.<operationName>}
Example 50-7 Using Expression Language for Table Iterators Example
#{row.hints.allows.<operationName>}
Example 50-8 Incorrect Expression Language Expression Example
#{row.hints.<attrName>.allows.<operationName>}
Example 50-9 Groovy Expression Example
object.getSecurityHints().allowsOperation("updateCategory").hasPermission()
Example 50-10 Groovy Expression if View Object is Read-Only Example
oracle.apps.fnd.applcore.dataSecurity.dataSecurityService.applicationModule.DataSecurityAMImpl.
testPrivilege("VIEW_PERSON_NAME_LIKE_T","PER_EL_TEST_PERSONS", PersonId.toString(),
null,null,null,null,object.getViewObject().getDBTransaction());
Example 50-11 Implementing Attribute Security Example
<af:panelFormLayout id="pfl1" partialTriggers="it6 cb3 cb1 cb4 cb5">
<af:inputText value="#{bindings.Gender.inputValue}"
label="#{bindings.Gender.hints.label}"
required="#{bindings.Gender.hints.mandatory}"
columns="#{bindings.Gender.hints.displayWidth}"
maximumLength="#{bindings.Gender.hints.precision}"
shortDesc="#{bindings.Gender.hints.tooltip}" id="it4"
rendered="#{bindings.TransientGenderAttr}">
<f:validator binding="#{bindings.Gender.validator}"/>
</af:inputText>
<af:inputText value="#{bindings.TransientGenderAttr.inputValue}"
label="#{bindings.TransientGenderAttr.hints.label}"
required="#{bindings.TransientGenderAttr.hints.mandatory}"
columns="#{bindings.TransientGenderAttr.hints.displayWidth}"
maximumLength="#{bindings.TransientGenderAttr.hints.precision}"
shortDesc="#{bindings.TransientGenderAttr.hints.tooltip}"
rendered="false"
id="it1">
</af:inputText>
<f:facet name="footer">
<af:panelGroupLayout layout="vertical" id="pgl1">
<af:panelGroupLayout layout="horizontal" id="pgl2">
<af:commandButton actionListener="#{bindings.First.execute}"
text="#{applcoreBundle.FIRST}"
disabled="#{!bindings.First.enabled}"
partialSubmit="true" id="cb3"/>
<af:commandButton actionListener="#{bindings.Previous.execute}"
text="#{applcoreBundle.PREVIOUS}"
disabled="#{!bindings.Previous.enabled}"
partialSubmit="true" id="cb1"/>
<af:commandButton actionListener="#{bindings.Next.execute}"
text="#{applcoreBundle.NEXT}"
disabled="#{!bindings.Next.enabled}"
partialSubmit="true" id="cb4"/>
<af:commandButton actionListener="#{bindings.Last.execute}"
text="#{applcoreBundle.LAST}"
disabled="#{!bindings.Last.enabled}"
partialSubmit="true" id="cb5"/>
</af:panelGroupLayout>
<af:commandButton text="#{applcoreBundle.SUBMIT}" id="cb2"/>
</af:panelGroupLayout>
</f:facet>
</af:panelFormLayout>
50.4 Use Oracle Fusion Data Security to Grant Access to Secured Business Objects
To secure the business object in the extended application, where it has been exposed as an ADF entity object, is a multi-step process:
-
A database resource definition must be created in the FND_OBJECTS table to identify the same table or view backing the ADF entity object. The database resource in Oracle Fusion Data Security is the data resource on which data security is enforced.
-
After the business object is defined as an Oracle Fusion Data Security database resource, then a security policy must be created to grant access to the data records. The security policies for the database resource specify access permissions such as read, update, and delete permissions on specific sets of data records exposed by the business object.
-
Finally, to enforce the newly created data security policy, the entity object in the data model project must enforce OPSS authorization checking on the data operations that access the protected data records exposed by the business object, as described Integrating with ADF Business Components.
As an Oracle Fusion Applications security guideline, a new data security policy must be created instead of modifying predefined data security policies of the security reference implementation. For example, a new data security policy is required to expose additional data records or operations for an existing business object. Additionally, a custom duty role must be created as the recipient of the new data security access permissions because granting permissions to a predefined duty role would alter the segregation of duties defined by the security reference implementation.
The general process for defining data security policies to grant access to business objects that you add to your Oracle Fusion application is as follows.
-
Identify the business object that you want to secure:
-
Register your database view or table that you want to secure with Fusion Oracle Data Security.
-
Populate the
FND_OBJECTSandFND_OBJECTS_TLtables appropriately.
-
-
Identify the conditions that you want to make available on the registered business object:
Tip:
Conditions may be static or parameterized. For details about parameterizing conditions, see How to Use Parameterized Conditions When Securing a Business Object.
-
Populate the
FND_OBJECT_INSTANCE SETSandFND_OBJECT_INSTANCE_SETS_TLtables appropriately.
-
-
Identify the actions that you want to secure this business object:
-
Populate
FND_FORM_FUNCTIONSandFND_FORM_FUNCTIONS_TLtables appropriately.
-
-
Group the actions appropriately to form aggregate actions:
-
Identify the name of the aggregate action and register it.
-
Register the various actions that are part of the aggregate action.
-
Compile the aggregate actions for faster reference.
You must do this to avoid hierarchical queries against the
FND_MENU_ENTRIEStable as aggregate actions may nest other aggregate actions. To compile the menus, invokefnd_function.fast_compileorfnd_function.compile_all_from_scratch.Note:
Menu hierarchies, such as sub-menus, are currently not supported. Menus may only include functions. This is because Seed Data Loaders do not support hierarchies now.
However, this step is still required as runtime queries are fired against the
fnd_compiled_menu_functionstable instead of thefnd_menu_entriestable. -
Populate
FND_MENUS,FND_MENUS_TL, andFND_MENU_ENTRIEStables appropriately.
-
-
Identify the Oracle Platform Security Services (OPSS) principals (OPSS users and roles) for which you want to make policies.
OPSS principals do not exist in the database and are managed by OPSS Policy Store, which may be a third-party system.
-
Make appropriate aggregate action policies on the business resource to OPSS users and roles.
Policies can be made on a row instance, on the resource globally, or for a condition, which may be parameterized.
-
Populate the
FND_GRANTStable appropriately.
-
50.4.1 How to Create Data Security Policies for Custom Business Objects
Data security policies are stored in the Oracle Fusion Data Security repository and are defined and edited using Oracle Authorization Policy Manager. You have access to this tool through Oracle Fusion Functional Setup Manager, from the Manage Data Security task available in the Setup and Maintenance work area of any Oracle Fusion Setup application, however, you will need specific permissions. When you have the necessary permissions, Oracle Authorization Policy Manager allows you to access the data security customization user interface.
Note:
For complete details about Oracle Authorization Policy Manager tasks that you can perform with the Manage Data Security Policies user interface, see the "Customizing Security for Oracle ADF Application Artifacts" chapter of the Extensibility Guide for Developers.
Before you begin:
Contact your security administrator to receive the duty role membership that entitles you to perform the Manage Data Security Policies tasks in Oracle Authorization Policy Manager.
You must have configured your user interface project to use application user sessions to support the data security runtime. For more information about implementing application user sessions, see Configuring Your Project to Use Application User Sessions.
You must enable security on your application. For more information about enabling security, see How to Enforce Authorization for Securable ADF Artifacts.
Collect the following information that you will use to define the data security policy in Oracle Authorization Policy Manager:
-
The primary key of the database table or view that the custom business object represents
You specified the primary key of the database table or view when you registered the database resource in Oracle Authorization Policy Manager.
-
The names of the conditions for which you want the security policy to control access
When you registered the database resource, you may have created named conditions to control access to instance sets composed of multiple rows (Oracle Fusion Data Security does not require that you create a named condition when you want to grant access to instance sets composed either of a single row or of all rows of the database resource).
-
The names of the actions for which you want to associate with a particular named condition (or instance set) to control access
When you registered the database resource, you named actions to identify the securable operations of the custom business object. Action names must be identical to the names of the operations the business object supports. For example, the names of actions corresponding to the supported standard operations are view, edit, and delete. However, if your data model project defines custom operations, actions may have names corresponding to operations named, for example, as
view_US_ONLY,edit_US_ONLY, ordelete_US_ONLY. -
The names of the custom duty roles for which you want to grant access to the conditions and actions of the database resource associated with the custom business object
As an Oracle Fusion Applications security guideline, predefined duty roles defined by the security reference implementation must not be modified. You must use Oracle Authorization Policy Manager to create a new duty role rather than grant data security permissions to predefined duty roles.
In Oracle Authorization Policy Manager, the general steps for defining a data security policy are as follows:
-
Using the Manage Data Security Policies user interface in Oracle Authorization Policy Manager, register the custom business object as a database resource.
-
Define the instance set of data records that you want to associate with specific securable operations of the ADF business component.
The security policy identifies named conditions from the security repository to specify the row instance set available to the end user provisioned to the role with the permission to perform the intended ADF business component operation.
In Oracle Authorization Policy Manager, a condition you create defines an instance set of multiple rows specified either by simple filters (XML-defined) or complex SQL queries whose values can be parameterized. No condition definition is needed in the case of a single row instance or all the row instances of the database resource.
-
Define the list of actions that you want to be able to grant to the role.
Actions are database equivalent create, read, update, delete (CRUD) operations and correspond to the names of securable operations of the business object that the end user may invoke. The data security policy you define will associate one or more actions with an instance set.
-
If the custom business object is not supported by a data role template, define the data security policy:
-
Enter a name and start date for the data security policy.
-
Select one or more job roles or duty roles to which the policy grants access. The roles you select entitle all end users assigned to those roles with access to the data.
In Oracle Authorization Policy Manager, duty role names that you enter are identified as OPSS internal roles called application roles. Similarly, job role names are identified as OPSS external roles called enterprise roles.
-
Specify an instance set on the database resource for which the security policy will control access. This may be a single row, all rows, or multiple rows (specified by a previously defined named condition).
-
Specify one or more actions to secure on the database resource for the currently specified instance set.
-
Repeat the steps to grant actions access to additional instance sets for the current data security policy and roles.
The following figure illustrates the Actions tab in the Edit Data Security page after several actions have been selected. Available actions will be limited to the actions that had been defined for the database resource.
Figure 50-6 Creating a Data Security Policy - Selecting Actions
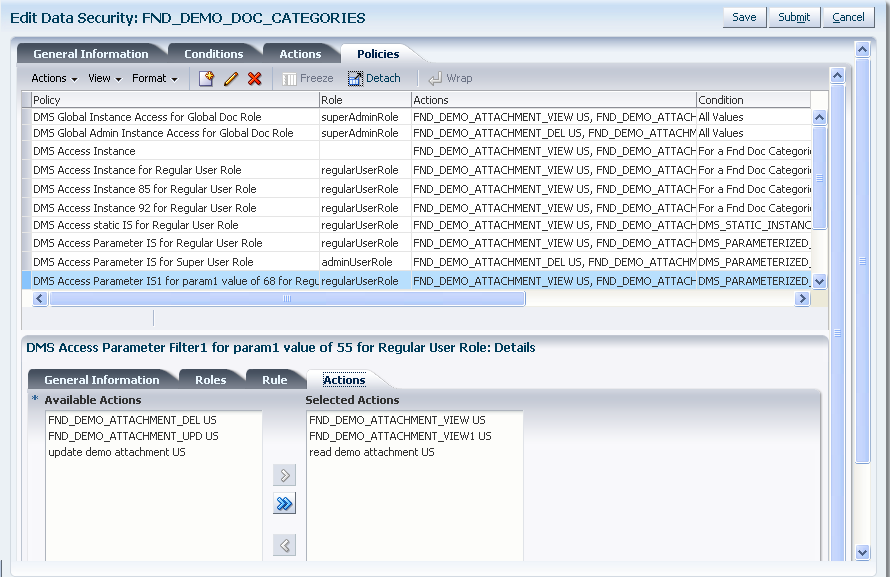
-
Example: Securing a document categories business object
The following scenario describes the general steps that you would follow using Oracle Authorization Policy Manager to secure a document categories business object. For detailed information about the data security management tasks you can perform in Oracle Authorization Policy Manager, see the "Customizing Security for Oracle ADF Application Artifacts" chapter of the Extensibility Guide for Developers.
The document categories business data is stored in the FND_DEMO_DOC_CATEGORIES table. The following table lists the document category definitions for the table.
Table 50-3 FND_DEMO_DOC_CATEGORIES Table Definition
| Name | Value |
|---|---|
|
CATEGORY_ID |
NOT NULL NUMBER |
|
APPLICATION_ID |
NUMBER |
|
CREATION_DATE |
NOT NULL DATE |
|
CREATED_BY |
NOT NULL NUMBER |
|
LAST_UPDATE_DATE |
NOT NULL DATE |
|
LAST_UPDATED_BY |
NOT NULL NUMBER |
|
LAST_UPDATE_LOGIN |
NUMBER |
|
NAME |
NOT NULL VARCHAR2(30) |
|
START_DATE_ACTIVE |
DATE |
|
END_DATE_ACTIVE |
DATE |
|
ATTRIBUTE_CATEGORY |
VARCHAR2(30) |
|
ATTRIBUTE1 thru ATTRIBUTE15 |
VARCHAR2(150) |
|
DEFAULT_DATATYPE_ID |
NUMBER |
The following example assumes that you have the necessary permission to perform the Manage Data Security Policies task in Oracle Authorization Policy Manager.
To secure a document categories business object in Oracle Authorization Policy Manager:
-
Create a resource named
FND_DEMO_DOC_CATEGORIESand identify its primary key ascategory_id. -
Create a static condition named
DMS_STATIC_INSTANCE_SET, which secures categories 33, 34, and 35.The predicate for this condition is
'category_id in (33,34,35)'. -
Create a dynamic condition named
DMS_PARAMETERIZED_ISto secure categories, which can be identified at grant time.The predicate for this condition is
'category_id in (&GRANT_ALIAS.PARAMETER1,&GRANT_ALIAS.PARAMETER2)', where&GRANT_ALIASrefers to the Policies table. -
Identify the actions securing this entity object for read, update, and delete operations as read, update, delete. Additionally, custom actions with the names
FND_DEMO_ATTACHMENT_VIEW,FND_DEMO_ATTACHMENT_UPD, andFND_DEMO_ATTACHMENT_DELmay be created for testing. -
Identify aggregate actions for which policies are made for this entity:
-
Create an aggregate action named
FND_DEMO_ATTACHMENT_VIEWfor the read operation, which contains actions namedreadandFND_DEMO_ATTACHMENT_VIEW. -
Create an aggregate action named
FND_DEMO_ATTACHMENT_ADMIN, which allows a user to administer this resource. It has read, update, and delete actions. This aggregate action contains read, update, delete,FND_DEMO_ATTACHMENT_VIEW,FND_DEMO_ATTACHMENT_UPD, and FND_DEMO_ATTACHMENT_DELactions.
-
-
Compile the menus in the database by executing:
fnd_function.compile_all_from_scratch;
-
Create OPSS principals.
For this example the user names created are
joeUserandadmin. The role names created areregularUserRoleandadmin. -
Make policies to OPSS principals
adminandregularUserRolefor theFND_DEMO_DOC_CATEGORIESbusiness resource.-
Grant
FND_DEMO_ATTACHMENT_ADMINaggregate action on the resource globally to OPSSadminrole. -
Grant
FND_DEMO_ATTACHMENT_VIEWaggregate action toregularUserRolefor staticDMS_STATIC_INSTANCE_SETand dynamic (DMS_PARAMAETERIZED_ISwith parameters 37 and 38) conditions.
-
50.4.2 How to Use Parameterized Conditions When Securing a Business Object
Parameterized conditions allow conditions to be specified generally but granted specifically. Parameterized conditions are useful because they reduce the number of predicates that the database must parse, as well as reducing the number of conditions that the administrator needs to manage.
The following example shows how a parameterized condition can be reused.
An administrator can reuse the first condition for several different policies granted to different locations and the second condition can be reused for policies granted to different titles. For example, one policy might use OIS1 to grant to 'WEST' by putting 'WEST' in FND_GRANTS.PARAMETER1, while another policy would reuse the same OIS1 to grant to 'EAST'. At runtime, the FND_DATA_SECURITY package substitutes the PARAMETER values from the FND_GRANTS table to the OISs granted.
When the data security system runs the predicates that have been defined in the conditions, it does a simple replace-style parsing of the predicate. For example, &TABLE_ALIAS is replaced by the table alias of the resource table, if it was passed to the get_security_predicate() call, and &GRANT_ALIAS is replaced by the policy table alias.
Caution:
The &TABLE_ALIAS and &GRANT_ALIAS column qualifiers must be included in the predicates of all conditions to keep possible duplicate column names from causing collisions.
Example 50-12 Reusing Parameterized Conditions
Condition. Employees in a particular region.
Predicate: "&TABLE_ALIAS.REGION = &GRANT_ALIAS.PARAMETER1"
50.4.2.1 Converting Non-String Parameter Values Into Character Values
The policy parameters hold only string values so you must convert non-string values into character values.
To convert non-string values into character values:
-
integer-
NUMBERwith no decimal point. For example, 123.To store the number in the policy
PARAMETERcolumn, useto_char()without a format mask. -
float-
NUMBERthat can have a decimal point. For example, 123.456.This should be stored in the canonical format, using
FND_NUMBER.NUMBER_TO_CANONICAL(). (The canonical format is based on theFND_NUMBERpackage'FM999999999999999999999.99999999999999999999'.)You should use canonical format because the string must be stored in a format that doesn't need to be converted if the data is passed between systems that use different decimal characters or other number formatting.
-
date-
DATEcalendar date, optional time. For example, 2009/04/30 11:32:32.This should be stored in canonical format, using
FND_DATE.DATE_TO_CANONICAL(). (The canonical format is based on theFND_DATEpackage,'YYYY/MM/DD HH24:MI:SS'.You should use canonical format because the string must be stored in a format that doesn't need to be converted if the data is passed between systems that use different date formats.
-
varchar2-
VARCHAR2character string. For example, FND_THING_NAME.This can be stored without any conversion.
However, translated values should not be stored here. This is for internal developer key values. There is no facility for having different multilingual values in different languages because predicates should not be comparing translated values.
50.4.2.2 Writing Performance Type Conversions in Predicates
Use the following rules when writing performance type conversions in your predicates.
Integer Equality:
The following example shows the correct Integer equality format to use.
The following example shows Integer equality formats that you should NOT use.
You must use to_char() as it is built-in and performs much faster than fnd_data_security.to_init().
When used with data security parameters, to_number() causes Invalid Number exceptions. This in turn, will make SQL statements abort if the to_number() gets run on policy parameters, which store non-numeric data such as DATE or VARCHAR2 data. The policies table will almost certainly contain some non-numeric data in a policy.
It may be decided to run a to_number(&GRANT_ALIAS.PARAMETER1) in a big statement on more policy rows than intended, and filter the rest of the rows later in the execution. This will definitely cause your SQL statement to fail so therefore, you must not have to_number() around any of the policy parameters in your predicate.
Tip:
The routine fnd_data_security.to_init() was written to avoid this problem; it is basically a wrapper over to_number(), which traps the Invalid Number exception. Therefore, if the execution plan involves operating against policies that don't apply, they won't cause the whole statement to fail. However, because of performance issues, to_char() is the preferred solution.
Integer Range:
The following example shows the correct Integer range format to use.
The following example shows Integer range formats that you should NOT use.
As explained previously, to_number() can fail with an Invalid Number exception if other policy rows are processed that have non-numeric parameters. to_char() does not produce the correct ordering. For example, '3' > '25'.
Float Equality:
The following example shows the correct Float equality format to use.
The following example shows Float equality formats that you should NOT use.
Using to_number() without a format could fail if the environment is set up to use comma as the decimal character and the parameter is stored with a period as the decimal character. Using to_char() without an explicit format could convert to a comma-format number, which would not match the period-format number. Because of these potential problems, you must explicitly provide the canonical format.
Float Range:
The following example shows the correct Float range format to use.
The following example shows Float range formats that you should NOT use.
You should not use to_char() because it does not order correctly.
You should use fnd_data_security.to_decimal() instead of fnd_data_security.to_init() because the data may contain decimals, which to_init() cannot handle.
Date Equality:
The following example shows the correct Date equality format to use.
The following example shows Date equality formats that you should NOT use.
As mentioned previously, to_char() performs best because it is built-in. The format mask is also required to make sure the canonical format is used.
Date Range:
The following example shows the correct Date range format to use.
The following example shows Date range formats that you should NOT use.
In this case, you can use to_char() with a format mask because the canonical format maintains proper ordering of the character domain.
Example 50-13 Integer Equality Format
to_char(&TABLE_ALIAS.ITEM_ID) = &GRANT_ALIAS.PARAMETER1
Example 50-14 Incorrect Integer Equality Formats
&TABLE_ALIAS.ITEM_ID = to_number(&GRANT_ALIAS.PARAMETER1) &TABLE_ALIAS.ITEM_ID = fnd_data_security.to_int(&GRANT_ALIAS.PARAMETER1)
Example 50-15 Integer Range Format
&TABLE_ALIAS.LEVEL >= fnd_data_security.to_init(&GRANT_ALIAS.PARAMETER1)
Example 50-16 Incorrect Integer Range Formats
&TABLE_ALIAS.LEVEL >= to_number(&GRANT_ALIAS.PARAMETER1) to_char(&TABLE_ALIAS.LEVEL) >= &GRANT_ALIAS.PARAMETER1
Example 50-17 Float Equality Format
to_char(&TABLE_ALIAS.TEMP,'FM999999999999999999999.99999999999999999999') = &GRANT_ALIAS.PARAMETER1
Example 50-18 Incorrect Float Equality Formats
to_char(&TABLE_ALIAS.TEMP) = &GRANT_ALIAS.PARAMETER1 &TABLE_ALIAS.TEMP = to_number(&GRANT_ALIAS.PARAMETER1) &TABLE_ALIAS.TEMP = fnd_data_security.to_decimal(&GRANT_ALIAS.PARAMETER1)
Example 50-19 Float Range Format
&TABLE_ALIAS.TEMP > fnd_data_security.to_decimal(&GRANT_ALIAS.PARAMETER1)
Example 50-20 Incorrect Float Range Formats
to_char(&TABLE_ALIAS.TEMP,'FM999999999999999999999.99999999999999999999') > &GRANT_ALIAS.PARAMETER1 to_char(&TABLE_ALIAS.TEMP) > &GRANT_ALIAS.PARAMETER1 &TABLE_ALIAS.TEMP > to_number(&GRANT_ALIAS.PARAMETER1) &TABLE_ALIAS.TEMP > fnd_data_security.to_init(&GRANT_ALIAS.PARAMETER1)
Example 50-21 Date Equality Format
to_char(&TABLE_ALIAS.ACTION_DATE,'YYYY/MM/DD HH24:MI:SS') = (&GRANT_ALIAS.PARAMETER1)
Example 50-22 Incorrect Date Equality Formats
to_char(&TABLE_ALIAS.ACTION_DATE) = (&GRANT_ALIAS.PARAMETER1) &TABLE_ALIAS.ACTION_DATE = fnd_data_security.to_date(&GRANT_ALIAS.PARAMETER1) &TABLE_ALIAS.ACTION_DATE = to_date(&GRANT_ALIAS.PARAMETER1)
Example 50-23 Date Range Format
to_char(&TABLE_ALIAS.HIRE_DATE,'YYYY/MM/DD HH24:MI:SS') > (&GRANT_ALIAS.PARAMETER1)
Example 50-24 Incorrect Date Range Formats
&TABLE_ALIAS.HIRE_DATE > fnd_data_security.to_date(&GRANT_ALIAS.PARAMETER1) to_char(&TABLE_ALIAS.HIRE_DATE) > (&GRANT_ALIAS.PARAMETER1) &TABLE_ALIAS.HIRE_DATE > to_date(&GRANT_ALIAS.PARAMETER1)
50.4.3 How to Create Test Users in JDeveloper
For development purposes, you can use the OPSS jazn-data.xml flat file to create users and roles for testing.
For an example of the identity store in the flat file used by JDeveloper, see the Enabling ADF Security in a Fusion Web Application chapter of the Developing Fusion Web Applications with Oracle Application Development Framework, in the Oracle Fusion Middleware Online Documentation Library.
50.4.4 What You May Need to Know About Creating Application Roles
Before testing the application in the staging environment, any custom application roles that you created will need to be created in the LDAP application policy store. These new application roles will receive new GUIDs and any data security policies defined for application roles of the same name must have their GUIDs reconciled. For details about reconciling GUIDs in the data security repository, see the Reconciling GUIDs section in the Administrator's Guide.
50.5 Getting Security Information from the Application User Session Context
Oracle Fusion Data Security is a layer that interacts with Oracle Platform Security Services. Hence data security information can be obtained from security context as required while developing the application.
50.5.1 How to Use the DataSecurityAM API to Get Session Context Information
The DataSecurityAMImpl class is in the oracle.apps.fnd.applcore.dataSecurity.dataSecurityService.applicationModule package. It is the container for all data security resources provided by Oracle Fusion Middleware Extensions for Applications. This class contains core methods to:
-
Check action for the current user, as shown in the following example.
Where
DataContextis a container class that represents the resource and optionally the primary keys of that resource for which data security check must be done. It has the following attributes:ObjectName,PK1,PK2,PK3,PK4,PK5.Note:
PrivilegeandDataContextclasses are in theoracle.apps.fnd.applcore.dataSecurity.utilpackage.If the action is granted to an Oracle Platform Security Services (OPSS) role in
FND_GRANTStable, then the system retrieves all the OPSS roles that the user has access to, and checks if one of them matches with the OPSS role to which the action has been granted. -
Get the security predicate associated with a given action on a given resource for the current user, as shown in the following example.
-
Get all the actions available on a given row instance for the current user, as shown in the following example.
-
Get all the aggregate actions available on a given row instance for the current user, as shown in the following example.
As shown in the following example, static APIs are also provided in the DataSecurityAMImpl class for the above core methods that take in a DBTransaction object.
Example 50-25 Check Action Method
/** * Test if an action is accessible for a given data context for the user * in the current session context. * @param privilege the privilege to test * @param dataContext data context (object and primary key) to use for * testing the privilege. * If null, then no data context is used. * @return true if privilege is accessible, false otherwise. */ public boolean testPrivilege(Privilege privilege, DataContext context)
Example 50-26 Get Security Predicate Method
/**
* Return the security predicate for a given action on a resource
* for the user in the current session context.
* @param privilege privilege to use to determine the predicat.
* @param dataContext the data context, which provides the object name.
* @param grantInstanceType the grant instance type, (such as "UNIVERSAL").
* @param statementType the statement type, (such as "OTHER").
* @param tableAlias alias for the table.
* @return the security predicate.
*/
public String getSecurityPredicate(Privilege privilege, DataContext dataContext
grantInstanceType, String statementType, String tableAlias)
Example 50-27 Get All Actions Available Method
/** * Provides the list of action names granted to the user for * the specified dataContext (Object/PK) in the current session context. * @param dataContext data context (object and primary key) to use for * identifying the granted actions. * @return list of action names. */ public String[] getPrivileges(DataContext dataContext)
Example 50-28 Get All Aggregate Actions Method
/** * Provides the list of aggregate action names granted to the user for * the specified dataContext (Object/PK) in the current session context. * @param dataContext data context (object and primary key) to use for * identifying the granted aggregate actions. * @return list of aggregate action names. */ public String[] getAggregatePrivileges(DataContext dataContext)
Example 50-29 Static API Examples
public static boolean testPrivilege(Privilege privilege, DataContext context,
DBTransaction dbTxn)
public static String getSecurityPredicate(Privilege privilege,
DataContext dataContext, String grantInstanceType, String statementType,
String tableAlias, DBTransaction dbTxn)
public static String[] getAggregatePrivileges(DataContext dataContext,
DBTransaction dbTxn)
public static String[] getPrivileges(DataContext dataContext, DBTransaction dbTxn)
50.5.2 How to Use the PL/SQL Data Security API to Check User Privileges
Oracle Fusion Middleware Extensions for Applications provides the FND_DATA_SECURITY PL/SQL package for the data security system.
FUNCTION check_privilege determines whether the user is granted a particular action for a particular row instance, as shown in the following example. The user is determined from the user session context.
This API returns a 1 byte result code:
T - Action is granted.
F - Action is not granted.
E - Error
U - Unexpected error.
PROCEDURE get_security_predicate gets the union of all predicates for the user on an action, as shown in the following example. The user is determined from the user session context.
p_grant_instance_type can take on one of the following values:
INSTANCE - Returns predicate for policies with instance_type = 'INSTANCE' or 'GLOBAL'.
SET - Returns predicate for policies with instance_type = 'SET'.
Note:
'SET' mode does not support aliases.
UNIVERSAL - (Default) Returns predicate for policies with any instance_type.
p_table_alias is appended in front of the column references in the returned x_predicate. It is normally used when two security predicates are going to be ANDed together to use with a select that joins two secured tables. The value passed here should correspond to the table alias that the statement uses for the p_object_name passed to this routine. The default, NULL, means there is no table alias so none is appended.
p_statement_type can take on one of the following values:
OTHER - (Default). The predicate returned is not attached by policy to the base table as is done for VPD. In practice, this allows the predicate to have a sub select against the base table, which allows aliases and may improve performance.
VPD - Pass this type if the predicate is attached by policy to the base table. Use this when VPD uses the returned predicate to control access. In practice, this means the predicate cannot have sub selects against the base table, prevents aliases and may lower performance.
EXISTS - Pass this type if the predicate is simply used to determine if there are any rows at all that are available. The predicate returned is in the format like 'EXISTS...'.
X_return_status is the result of all the operations:
T - Successfully got predicate
E - Error
U - Unexpected error
L - Value too long - predicate too large for database VPD
The return value is all the available predicates from the policies on this action for this user. They are OR'ed together to form a SQL predicate that can be dropped into the WHERE clause to limit rows returned to those that are allowed by the security. Does not include WHERE.
Example 50-30 FUNCTION check_privilege API
FUNCTION check_privilege
(
p_api_version IN NUMBER,
/* API Version of this procedure - currently 1.0 (Required) */
p_privilege IN VARCHAR2,
/* Name of the action (Required) */
p_object_name IN VARCHAR2,
/* Resource on which the policy should be checked from FND_Objects table
(Required) */
p_instance_pk1_value IN VARCHAR2 DEFAULT NULL,
/* p_instance_pk(1...5)_value (Required)
Primary key values for the row instance, with order corresponding
to the order of the PKs in the FND_Objects table. Most resources have
only a few primary key columns so let the higher, unused columns
default to NULL.
NOTE: The caller must pass an actual primary key and it must be the
primary key of an actual instance (row). */
p_instance_pk2_value IN VARCHAR2 DEFAULT NULL,
p_instance_pk3_value IN VARCHAR2 DEFAULT NULL,
p_instance_pk4_value IN VARCHAR2 DEFAULT NULL,
p_instance_pk5_value IN VARCHAR2 DEFAULT NULL
)RETURN VARCHAR2;
Example 50-31 PROCEDURE get_security_predicate
PROCEDURE get_security_predicate
(
p_api_version IN NUMBER,
/* API version of this procedure - Currently 1.0 (Required) */
p_privilege IN VARCHAR2 DEFAULT NULL,
/* Name of action. (Optional) */
/* NULL represents all actions so the predicate will not take the
action into account. */
p_object_name IN VARCHAR2,
/* Object on which the predicate should be checked from FND_Objects table. */
p_grant_instance_type IN VARCHAR2 DEFAULT 'UNIVERSAL',
/* SET, INSTANCE (Optional) */
p_statement)_type IN VARCHAR2 DEFAULT 'OTHER',
/* (Optionsl) statement type: 'OTHER', 'VPD', 'EXISTS' = to check existence. */
x_predicate OUT NOCOPY VATRCHAR2,
x_return_status OUT NOCOPY VARCHAR2,
p_table_alias IN VARCHAR2 DEFAULT NULL
/* (Optional) */
);
50.6 Understanding Data Security Performance Best Practices
The WHERE clause associated with a given resource is constructed by doing an OR of all the predicates associated with the conditions granted to a user or role. Therefore, it is important that the predicate for a condition be efficient so that it returns as few rows as possible and that it also uses an index.
Data security should only be used when the combined predicates (Applications Code + Data Security Predicates) are efficient, and return only relevant rows. Most queries should only return either one row or just a few rows. The maximum number of rows that data security should consider operating on is 100 rows. If you are seeing performance problems with queries that apply data security to more than 100 rows, the query must be made more selective. Blind queries against tables secured with data security are not allowed.
Note:
Data security is not designed as a means to limit the number of rows returned; there must always be another selective WHERE clause before the data security predicate.
Condition predicates must be as fast as possible. All predicates that apply to a particular context must go into the SQL statement that gets executed; therefore, all predicates need to be efficient, whether they reject no rows, a few rows, or many rows. Any sub selects in predicates should be on well-indexed columns. Predicates must execute in linear time, doing simply indexed selects. Predicates that involve connect-by or other network, hierarchical operations are not supported. The suggested approach to hierarchical data representations is building and selecting against a compiled representation of the data.
You should use conditions rather than row instance policies. Row instance policies are policies where each policy maps to exactly one row in the resource table. They generally don't scale well because they require one policy row for every resource table row. Performance is best when the number of policies that apply in any particular context is low. Condition policies involve just one policy, which specifies an unlimited number of rows. If the normal use case would involve more than a few row instance policies, then you probably need to be change the design to use conditions.
Note:
There are no plans to provide any APIs to answer the question "What users have access to a particular function on a particular row instance?" The reason being is that the condition predicates can reference context that can be driven by the user, like profiles. The only way to answer that question would be to loop through every user and set up their context (including profiles, and so on), and then see if they had access. That is not practical given the large number of users that are possible. For the same reason, data security does not try to answer the question "Does a particular user have access to a particular function?"
50.7 Validating Data Security with Diagnostic Scripts
Oracle Fusion Applications provides WLST (Oracle WebLogic Scripting Tool) scripts written in the Python programming language to help administrators verify that data security setup and configuration definitions are correct for a newly deployed application. Other WLST scripts help administrators verify that applications context setup and configuration definitions are correct for a newly deployed application and that the applications context is created for a logged-in user.
The data security diagnostic scripts may be run in the WLST scripting environment or from the Diagnostic Dashboard application of any Oracle Fusion application. The Diagnostic Dashboard provides administrators with a graphical user interface to execute and monitor diagnostic tests.
For more information about the Diagnostic Dashboard, see the "Running and Working with Diagnostic Tests Manually" section in the Administrator's Guide.
50.7.1 How to Validate Data Security Configuration with Diagnostic Scripts
The WLST script datasecurityDiagnostics.py is provided to help administrators verify that data security setup and configuration definitions are correct for a newly deployed application. Additionally, the script generates a report that system integrators, developers and security managers can further use to diagnose runtime issues related to a logged-in user's ability to access data.
To accomplish these tasks, the script performs these specific functions:
-
Validates data security configuration in the
adf-config.xmlfile, which is archived in the application EAR file. The scripts checks the configuration values of the<sec:JaasSecurityContext>element to verify that the data security provider is properly configured and outputs the result to the output fileDataSecurityDiagResults.out. -
Validates that GUID consistency is enabled in the
weblogic-application.xmlfile. The script checks the value of thejps.approle.preserveguidapplication parameter and outputs the result to the output fileDataSecurityDiagResults.out. The application parameter must be set toTRUEto support deploying the policy store from a test to a production environment. This ensures the GUID for each application role remain the same when migrated from XML to LDAP or LDAP to LDA. -
Optionally, takes the running application's session cookie value as an input parameter and, using this session cookie, the script gets the corresponding session object from the data source, inspects the session attributes and outputs the session information to the output file
DataSecurityDiagResults.out. Using the session cookie, the script gets role information corresponding to the session's logged-in user, along with their access privileges to various database objects and outputs it to the output fileDataSecurityDiagResults.out.Note: If you only want the script to perform the application configuration validation checks, you can skip this step by pressing Enter when prompted to enter the value for session cookie.
Important Note
Before invoking a WLST script you must run the following wlst.sh script on Oracle WebLogic Server to ensure that the required JARs are added to the class path.
>sh $ORACLE_HOME/common/bin/wlst.sh
After you invoke the wlst.sh script, you can connect to Oracle WebLogic Server in offline mode, that is, the data security script does not require a connection to a running server to operate.
To invoke the data security diagnostic script:
At the offline prompt, enter the following command:
>wls:/offline> execfile('datasecurityDiagnostics.py')
The script prompts you for the following information before outputting the results:
-
Output file's directory path where you want the script's output file to be saved.
-
Application name for which you want to run the script. The application name is the deployment name in Oracle WebLogic Server. For example,
SalesApp#V3.0. Note that the version part of the application name is specified with a#symbol: for example,#V3.0inSalesApp#V3.0. -
Application source path of the deployed application. For example,
/scratch/myself/view_storage/myself_main_gene_testing/system11.1.1.4.37.56.69/DefaultDomain/servers/DefaultServer/upload/DemoSecurity/V2.0/app/DemoSecurity.ear. The source path can be obtained from Oracle WebLogic Server Administration Console, under the Deployments section for the application. -
Session cookie value created for the logged-in user for whom you want to validate data security roles and privileges. Optional (you can press Enter to skip). To obtain the session cookie, you must log into the application as the user whose roles and privileges you want to examine. After logging into the application, from the browser, open the cookies window (for example, in Internet Explorer, you can display cookies from the Temporary Internet Files and History Settings dialog). Under the site
oracle.com, locate the cookie named<DATABASE_SID>_FND_SESSIONand copy the value, which is the required session cookie. If you do not find this named session cookie, it means that the applications context is not created for your application.Tip:
You can run the application context diagnostic script by pressing Enter when the data security script prompt you to enter the value for session cookie for your application. This will invoke the applications context script and validate the applications context configuration. For details about the applications context script, see How to Validate Applications Context.
50.7.2 How to Validate Applications Context
The WLST script applsessionDiagnostics.py is provided to help administrators verify that applications context setup and configuration definitions are correct for a newly deployed application and that the applications context is created for a logged-in user. Additionally, the script generates a report that system integrators, developers and security managers can further use to diagnose the runtime issues related to an Application Session.
To accomplish these tasks, the script performs these specific functions:
-
Validates the session filters and filter mapping definitions in the
web.xmlfile, which is archived in the application EAR file. The scripts checks for the presence of the<filter-name>ApplSessionFilter</filter-name>element and verifies that theApplSessionFiltermapping definition appears immediately after theJpsFiltermapping definition, and then outputs the result to the output fileApplsessionDiagResults.out. -
Connects to the database and gets the Oracle Fusion Applications FND table metadata for the application context. The script checks the value of the
Name,Datatype,Precision, andisNullableattributes for each column in the tables, validates the database schema for each table, and then outputs the result to the output fileApplsessionDiagResults.out. -
Optionally, takes the running application's session cookie value as an input parameter and, using this session cookie, the script gets the corresponding session object from the data source, inspects the session attributes and outputs the applications context session properties to the output file
ApplsessionDiagResults.out. Using the session cookie, the script gets the applications context properties corresponding to the session's logged-in user, determines whetherApplSessionis created properly, and outputs the result to the output fileApplsessionDiagResults.out.Note: If you only want the script to perform the application configuration validation and the database metadata validation checks, you can skip this step by pressing Enter when prompted to enter the value for session cookie.
-
Connects to the database and validates the
FUSION.FND_SESSION_MGMTPL/SQL package to check for its consistency. The script checks whether a valid package header and package body is defined for the package and outputs the result to the output fileApplsessionDiagResults.out.
Before you begin:
Before invoking a WLST script you must run the following wlst.sh script on Oracle WebLogic Server to ensure that the required JARs are added to the class path. Use the following command:
>sh $ORACLE_HOME/common/bin/wlst.sh
After you invoke the wlst.sh script, you can connect to Oracle WebLogic Server in offline mode, that is, the data security script does not require a connection to a running server to operate.
To invoke the application context diagnostic script:
At the offline prompt, enter the following command:
>wls:/offline> execfile('applsessionDiagnostics.py')
The script prompts you for the following information before outputting the results:
-
Output file's directory path where you want the script's output file to be saved.
-
Application name for which you want to run the script. The application name is the deployment name in Oracle WebLogic Server. For example,
SalesApp#V3.0. Note that the version part of the application name is specified with a#symbol: for example,#V3.0inSalesApp#V3.0. -
Application source path of the deployed application. For example,
/scratch/myself/view_storage/myself_main_gene_testing/system11.1.1.4.37.56.69/DefaultDomain/servers/DefaultServer/upload/DemoSecurity/V2.0/app/DemoSecurity.ear. The source path can be obtained from Oracle WebLogic Server Administration Console, under the Deployments section for the application. -
Session cookie value created for the logged-in user for whom you want to validate data security roles and privileges. Optional (press Enter to skip). To obtain the session cookie, you must log into the application as the user whose roles and privileges you want to examine. After logging into the application, from the browser, open the cookies window (for example, in Internet Explorer, you can display cookies from the Temporary Internet Files and History Settings dialog). Under the site
oracle.com, locate the cookie named<DATABASE_SID>_FND_SESSIONand copy the value, which is the required session cookie. If you do not find this named session cookie, it means that the applications context is not created for your application.
50.8 Integrating with Data Security Task Flows
The Oracle Fusion Middleware Extensions for Applications data security task flows are a set of four task flows that provide a simplified user interface for implementing role-based security in Fusion applications. Consider integrating data security task flows into an Oracle Fusion application when your application needs to support an authorized end user's ability to secure business objects in their business domain. For example, these task flows can give Human Resources managers the ability to secure employee records to grant HR representatives access to defined groups of employee records.
Oracle Fusion Middleware Extensions for Applications data security task flows use Oracle Fusion Applications security technology to implement data security policies in Oracle Fusion Applications FND tables and function security policies in the LDAP policy store. At runtime, the task flows implementation performs the necessary backend operations to both secure data exposed by a business object (data security) and to secure the user interface (function security) that displays the business objects.
The following task flows are available and may be integrated using Oracle JDeveloper:
-
Object-centric task flow lets the end user display and secure a single business object. The flow displays the end user's business object selection and then displays all the application roles that may be granted access to that object. This task flow simplifies the task of securing a business object across the organization.
-
Role-centric task flow (also called the Profile task flow) lets the end user select an application role profile and secure multiple business objects pertaining to that profile. The flow displays the end user's application role profile selection and displays all the securable business objects that the profile may access. This task flow is also called the profile task flow since every end user is assigned to a profile that corresponds to an enterprise role mapped to a hierarchy of application roles.
Note that the role-centric task flow and the object-centric task flow present the end user with different views of the same security functionality. Both enable data security and functionality security policies for permissions that the end user selects across business objects.
-
Instance-level task flow lets the end user select an instance of a securable business object (one row) for which they have access and then confer access rights to another user or group of users. This task flow provides a way for end users to share access rights with other members of their organization. The scope of this task flow is different from the role-centric and object-centric task flows in that security is limited to the business object instance. The business object itself must already have grants made to the end user who wishes to share access.
-
Role management task flow lets the end user create and edit application roles. This task flow is particularly useful when the user creates custom business objects and wishes to grant permission to that object for a custom application role.
50.8.1 About Integrating the Data Security Task Flows into Your Application
The process of integrating the data security task flows into an Oracle Fusion application involves understanding the input parameters of the task flow. Your application will use a managed bean to initialize the task flow's parameters before the application displays the task flow to the end user. The way your application references the values of the input parameters on the bean depends on how you want to display the task flow. Your application can display the data security task flow one of two ways:
-
You can display the task flow in the application's primary browser window.
-
You can display the task flow in the application's secondary browser window that displays a new web page and allows the user to view the primary window while working in the task flow.
For example, the object instance task flow user interface is well-suited to run in a dialog. When you run this task flow in a dialog, the user can select an object in the primary browser window, make grants on the selection in the secondary window, and repeat for other objects without needing to reopen the primary window. The other task flows, including the object-centric task flow, profile (role-centric) task flow, and role management task flow, are large enough that you may want to display them in the primary window.
The steps to integrate the data security task flows into your application will depend on the method you choose to display the task flow. However, review the following general steps for an overview of the process.
Before you begin:
Add the data security task flows to your project. Decide whether you want your application to display the task flow in the primary window or in a popup dialog
To integrate the data security task flows, follow these general steps.
-
Decide whether you want your application to display the task flow in the primary window or in a popup dialog.
-
Create a task flow reference in your application to bind the data security task flow to the ADF Model layer.
In JDeveloper, the reference will be generated for you when you drag and drop the data security task flow. The way you drag and drop the data security task flow depends on the way your application displays the task flow:
-
How to Configure Data Security Task Flows to Display in the Primary Window
-
How to Configure the Object Instance Task Flow to Display in a Dialog
-
Define the data security task flow's input parameters so they have page flow scope.
Page flow scope will allow the values to be passed into the task flow from a managed bean. The ADF Model layer component that you use to define the parameters depends on the way your application displays the task flow:
-
Create a managed bean and define an initialization method to populate the input parameters for the data security task flows, as shown in Table 50-4.
The method you define will initialize the values before your application displays the task flow. When displaying the page inside your application's primary window, the initialization method must also return the value of the flow control outcome you configure in your application's task flow to invoke the data security task flow. The outcome return value is not needed when displaying a dialog, since the dialog is not invoked the same way.
-
Create a navigation button that invokes the initialization method in your method bean.
The ADF Faces component you use to create the button depends on how you want the data security task flow to display:
-
-
Authorize the data security task flows to make grants in the LDAP policy store. For details see How to Grant the Data Security Task Flows Access to the Application Policy Store.
-
Authorize end user to access the task flow. For details see How to Grant the End User Access to the Data Security Task Flows.
-
Configure the application to access the domain LDAP policy store. For details see How to Map the Application to an Existing Application Stripe.
The following table describes the input parameters that your managed bean must initialize for each task flow.
Table 50-4 Data Security Task Flows and Their Input Parameters
| Task Flow Name | Task Flow XML | Parameters Passed | Behavior |
|---|---|---|---|
|
Object-centric task flow (also referred to as ( |
/WEB-INF/oracle/apps/fnd/ applcore/dataSecurity/ui/ taskflow/ObjectLevelFT.xml |
Specify the name of the object for which the grant will be managed: objectName Specify the list of role categories from which the available application roles will be fetched: roleCategories Specify the list of securable actions to be displayed in the UI for the object: actions Specify disableViewAll Specify disableUpdateAll |
Create and manage grants to multiple application roles for a single business object. |
|
Role-centric task flow (also referred to as |
/WEB-INF/oracle/apps/fnd/ applcore/dataSecurity/ui/ taskflow/ProfileTF.xml |
Specify the list of role categories from which the available application roles will be fetched: roleCategories Specify the list of securable actions to be displayed in the UI for the object: actions Specify disableViewAll Specify disableUpdateAll |
Create and manage grants to a single application role profile for multiple business objects. |
|
Instance-level task flow (also referred to as |
/WEB-INF/oracle/apps/fnd/ applcore/dataSecurity/ui/ taskflow/ObjectInstTF.xml |
Specify the name of the parent object from which the object instance will be fetched: objectName Specify the primary key of the object instance for which grants will be shared: instancePk1 instancePk2 instancePk3 instancePk4 instancePk5 Specify the list of securable actions to be displayed in the UI for the object: actions Specify the ID of the customized task flow: taskflowId Specify the holder of the customized task flow parameters: parameterMap |
Confer existing grants for a single instance of a business object to another user (or user group). |
|
Role management task flow (also referred to as |
/WEB-INF/oracle/apps/fnd/ applcore/dataSecurity/ui/ taskflow/RoleManagementTF.xml |
Specify the list of role categories from which the available application roles will be fetched: roleCategories Specify the title of the task flow UI: title |
Create and edit custom application roles. |
50.8.2 How to Configure Data Security Task Flows to Display in the Primary Window
When you integrate the task flow as a primary window, your application's task flow invokes the data security task flow using a task flow call activity. A control flow case defines the transition (identified with a particular outcome value) between your application's view activity (for the calling web page) and the call activity. A navigation button in the calling web page invokes a method on the managed bean that initializes the task flow's input parameters and returns the expected value of the control flow case outcome. Your application's task flow invokes the data security task flow through the call activity reference that matches the returned outcome.
To integrate a data security task flow with your application so it appears in the primary browser window of the application:
50.8.2.1 Create a Task Flow Call Activity in Your Application's Task Flow
You can use a task flow call activity to call any one of the data security task flows from your application's unbounded or bounded task flow. The task flow call activity allows you to call the data security task flows located within the same or a different application.To pass parameters into the data security task flow, you specify input parameter values on the task flow call activity. These values must correspond to the input parameter definitions on the called data security task flow.
The following example shows the task flow call activity definition with a reference to the object-centric data security task flow. The task flow call activity also defines the input parameter values required by the object-centric task flow.
The following example shows the task flow call activity definition with a reference to the role-centric data security task flow. The task flow call activity also defines the input parameter values required by the role-centric task flow.
The following example shows task flow call activity definition with a reference to the role management data security task flow. The task flow call activity also defines the input parameter values required by the role management task flow.
To create the task flow call activity:
Example 50-32 ObjectLevelTF Reference in Calling Task Flow Configuration File
<task-flow-call id="ObjectLevelTF">
<task-flow-reference>
<document>/WEB-INF/oracle/apps/fnd/applcore/dataSecurity/ui/taskflow/
ObjectLevelTF.xml</document>
<id>ObjectLevelTF</id>
</task-flow-reference>
<input-parameter>
<name>objectName</name>
<value>#{pageFlowScope.objectName}</value>
</input-parameter>
<input-parameter>
<name>roleCategories</name>
<value>#{pageFlowScope.roleCategories}</value>
</input-parameter>
<input-parameter>
<name>actions</name>
<value>#{pageFlowScope.actions}</value>
</input-parameter>
<input-parameter>
<name>disableViewAll</name>
<value>#{pageFlowScope.disableViewAll}</value>
</input-parameter>
<input-parameter>
<name>disableUpdateAll</name>
<value>#{pageFlowScope.disableUpdateAll}</value>
</input-parameter>
</task-flow-call>
Example 50-33 ProfileTF Reference in Calling Task Flow Configuration File
<task-flow-call id="ProfileTF">
<task-flow-reference>
<document>/WEB-INF/oracle/apps/fnd/applcore/dataSecurity/ui/
taskflow/ProfileTF.xml</document>
<id>ProfileTF</id>
</task-flow-reference>
<input-parameter>
<name>roleCategories</name>
<value>#{pageFlowScope.roleCategories}</value>
</input-parameter>
<input-parameter>
<name>actions</name>
<value>#{pageFlowScope.actions}</value>
</input-parameter>
<input-parameter>
<name>disableViewAll</name>
<value>#{pageFlowScope.disableViewAll}</value>
</input-parameter>
<input-parameter>
<name>disableUpdateAll</name>
<value>#{pageFlowScope.disableUpdateAll}</value>
</input-parameter>
</task-flow-call>
Example 50-34 RoleManagementTF Reference in Calling Task Flow Configuration File
<task-flow-call id="RoleManagementTF">
<task-flow-reference>
<document>/WEB-INF/oracle/apps/fnd/applcore/dataSecurity/ui/
taskflow/RoleManagementTF.xml</document>
<id>RoleManagementTF</id>
</task-flow-reference>
<input-parameter>
<name>roleCategories</name>
<value>#{pageFlowScope.roleCategories}</value>
</input-parameter>
<input-parameter>
<name>title</name>
<value>#{pageFlowScope.title}</value>
</input-parameter>
</task-flow-call>
50.8.2.2 Initialize the Data Security Task Flow Using a Managed Bean
Managed beans are Java classes that you register with the application in your calling task flow's configuration file. You will create a method on a managed bean to:
-
Initialize the input parameters of the data security task flows.
-
Return a value that matches the outcome of the calling task flow.
When your application runs, and the end user clicks the button in the calling web page, the method is invoked and the properties are declared, allowing the called data security task flow input parameters to be populated with the declared values.
The following example shows the additional source code that your managed bean must include to initialize the object-centric (ObjectLevelTF) task flow.
The following example shows the additional source code that your managed bean must include to initialize the role-centric (ProfileTF) task flow.
The following example shows the additional source code that your managed bean must include to initialize the role management (RoleManagementTF) task flow.
To populate task flow input parameters with a managed bean:
Example 50-35 Source for Populating the ObjectLevelTF Input Parameters
//Source for managed bean method to populate and pass ObjectLevelTF parameters
String objectName = "TEST_DS_EMP";
List actions = new ArrayList<ActionMap>();
//for action1
List<String> instanceSets1 = new ArrayList<String>();
instanceSets1.add("TEST_EMP_IS1");
instanceSets1.add("TEST_EMP_IS2");
instanceSets1.add("TEST_EMP_IS3");
ActionMap action1 = ActionMap.getActionMapForObjectUI("View", "VIEW_M",
"ViewPermSet", false, instanceSets1);
actions.add(action1);
//for action 2
List<String> instanceSets2 = new ArrayList<String>();
instanceSets2.add("TEST_EMP_IS2");
instanceSets2.add("TEST_EMP_IS3");
instanceSets2.add("TEST_EMP_IS4");
ActionMap action2 = ActionMap.getActionMapForObjectUI("Update", "UPDATE_M",
"UpdatePermSet", false, instanceSets2); actions.add(action2);
//populate role categories
List roleCategories = new ArrayList<String>();
roleCategories.add("Category1");
roleCategories.add("Category2");
roleCategories.add("Category3");
//set the paramters in pageflow scope
AdfFacesContext context = AdfFacesContext.getCurrentInstance();
Map pageFlowScope = context.getPageFlowScope();
pageFlowScope.put("objectName", objectName);
pageFlowScope.put("roleCategories",roleCategories);
pageFlowScope.put("actions", actions); pageFlowScope.put("disableViewAll", false);
pageFlowScope.put("disableUpdateAll", false);
Example 50-36 Source for Populating the ProfileTF Input Parameters
//Source for managed bean method to populate and pass ProfileTF parameters
List roleCategories = new ArrayList<String>();
roleCategories.add("Category1");
roleCategories.add("Category2");
List actions = new ArrayList<ActionMap>();
//for action1
List<ProfileActionObject> profileObjects1 = new ArrayList<ProfileActionObject>();
profileObjects1.add(ProfileActionObject.getProfileActionObject("View",
"TEST_DS_EMP", "VIEW_EMP_M","ViewEmpPermSet"));
profileObjects1.add(ProfileActionObject.getProfileActionObject("View",
"TEST_DS_EMP1", "VIEW_EMP1_M","ViewEmp1PermSet"));
profileObjects1.add(ProfileActionObject.getProfileActionObject("View",
"TEST_DS_EMP2", "VIEW_EMP2_M","ViewEmp2PermSet"));
ActionMap action1 = ActionMap.getActionMapForProfileUI("View", profileObjects1);
actions.add(action1);
//for action 2
List<ProfileActionObject> profileObjects2 = new ArrayList<ProfileActionObject>();
profileObjects2.add(ProfileActionObject.getProfileActionObject("Update",
"TEST_DS_EMP1", "UPDATE_EMP1_M","UpdateEmp1PermSet"));
profileObjects2.add(ProfileActionObject.getProfileActionObject("Update",
"TEST_DS_EMP2", "UPDATE_EMP2_M","UpdateEmp2PermSet"));
ActionMap action2 = ActionMap.getActionMapForProfileUI("Update",profileObjects2);
actions.add(action2);
AdfFacesContext context = AdfFacesContext.getCurrentInstance();
Map pageFlowScope = context.getPageFlowScope();
pageFlowScope.clear();
pageFlowScope.put("roleCategories", roleCategories);
pageFlowScope.put("actions", actions);
pageFlowScope.put("disableViewAll", false);
pageFlowScope.put("disableUpdateAll", false);
Example 50-37 Source for Populating the RoleManagementTF Input Parameters
//Source for managed bean method to populate & pass RoleManagementTF parameters
AdfFacesContext context = AdfFacesContext.getCurrentInstance();
Map pageFlowScope = context.getPageFlowScope();
pageFlowScope.clear();
List roleCategories = new ArrayList<String>();
roleCategories.add("Category1");
roleCategories.add("Category2");
roleCategories.add("Category3");
pageFlowScope.put("roleCategories", roleCategories);
pageFlowScope.put("title", "Role Management");
50.8.2.3 Register the Managed Bean with Your Application's Task Flow
To declare the manage bean in the calling task flow's configuration file, you must enter a bean identifier name, the class path for the bean, and you must specify backing bean scope. The following example uses the bean identifier roleManageBean to match the Action attribute definition specified on the button component shown in Example 50-39.
To register the managed bean with the calling task flow:
- Open your application's task flow (the calling task flow) in the diagram editor.
- In the editor for the task flow, click the Source tab.
- In the source for the calling task flow, declare the managed bean by creating the
<managed-bean>element similar to the sample shown in the previous example.
Example 50-38 Managed Bean Declaration in Calling Task Flow Configuration File
<adfc-config xmlns="http://xmlns.oracle.com/adf/controller" version="1.2">
<task-flow-definition id="MyCallingTaskFlow">
<default-activity id="__1">CallRoleManageTF</default-activity>
<managed-bean id="__4">
<managed-bean-name id="__5">roleManageBean</managed-bean-name>
<managed-bean-class id="__2">
oracle.apps.fnd.applcore.dataSecurity.view.RoleManage</managed-bean-class>
<managed-bean-scope id="__3">backingBean</managed-bean-scope>
</managed-bean>
</task-flow-definition>
...
</adfc-config>
50.8.2.4 Creating a Command Button to Invoke the Task Flow in the Primary Window
Create an ADF command button component in the web page associated with the source activity of the control flow case you create in the calling task flow. When the end user clicks the button, the button will cause the data security task flow to display. You will need to configure the Action attribute of the button so a click by the end user invokes the initialization method of your managed bean.
The following example shows a command button component with an Action attribute that invokes the method initializeRoleManagement() on the bean referenced by the bean identifier roleManageBean. The name of the identifier corresponds to the managed bean declaration you create when you edit the calling task flow configuration file, as described in Registering the Managed Bean with Your Application's Task Flow.
Example 50-39 Button Component with Action Attribute to Invoke Bean Method
<af:commandButton text="Manage Roles" id="cb1"
action="#{backingBeanScope.roleManageBean.initializeRoleManagement}"/>
50.8.3 How to Configure the Object Instance Task Flow to Display in a Dialog
When you integrate a data security task flow as a dialog, your application's task flow invokes the task flow using an executable in the ADF Model layer. This executable is defined by JDeveloper when you drop the data security task flow as region onto a dialog component that you add to your application's calling web page. The web page the defines the region is associated with a view activity in your application task flow; no task flow control flow case is needed to invoke the data security task flow.
A popup button in the calling web page defines a listener that invokes a method on the managed bean to initialize the task flow's input parameters. The button then displays the dialog with a region that invokes the task flow using the executable defined on the calling page's definition. When the user clicks the dialog close button, a listener (for the dialog's close button) saves the end user's sections from data security UI.
To integrate the object instance task flow (ObjectInstTF) with your application so it appears in a dialog (as a secondary browser window):
- In your application's task flow, double-click the view activity associated with the web page that end users will use to open the dialog.
- In the web page, drop an ADF command button component.
- Drop an ADF popup component onto the button and configure a popup fetch listener to invoke an initialization method on a managed bean.
- Drop an ADF dialog inside the popup component and configure a dialog listener to invoke a method to save grants made by the user.
- Drop the object instance task flow as a region onto the dialog component.
- Edit the page definition file for the calling page to specify the data security task flow's input parameter values on the task flow executable.
- Create a managed bean and define a method to initialize the task flow parameters before the dialog displays.
- Define another method on the managed bean to trigger the task flow save action and save the grants into the database.
- Register the managed bean in your application's task flow configuration file.
50.8.3.1 Create the Task Flow Executable in the Region Page Definition FIle
When you drop a data security task flow onto a web page to create an ADF region, JDeveloper adds an af:region tag to the page. The af:region tag references an object that implements RegionModel, as shown in Example 50-*.JDeveloper also adds a task flow binding to the <executables> element of the page definition file for the page that defines the ADF region. The task flow binding provides a bridge between the ADF region and the data security task flow. It binds a specific instance of an ADF region to the data security task flow and maintains all information specific to the task flow. The taskFlowId attribute specifies the directory path and the name of the source file for the bounded task flow.To pass parameters into the data security task flow, you must specify input parameter values on the task flow binding. These values must correspond to the input parameter definitions on the called data security task flow.
The following example shows task flow binding in the page definition file with a reference to the object-instance data security task flow. The task flow binding also defines the input parameter values required by the object-instance task flow.
To create the task flow binding definition:
Example 50-40 ObjectInstTF Call Entry in Page Definition File
<taskFlow id="ObjectInstTF1"
taskFlowId="/WEB-INF/oracle/apps/fnd/applcore/dataSecurity/ui/
taskflow/ObjectInstTF.xml#ObjectInstTF"
Refresh="ifNeeded"
xmlns="http://xmlns.oracle.com/adf/controller/binding">
<parameters>
<parameter id="objectName" value="#{pageFlowScope.objectName}"
xmlns="http://xmlns.oracle.com/adfm/uimodel"/>
<parameter id="actions" value="#{pageFlowScope.actions}"
xmlns="http://xmlns.oracle.com/adfm/uimodel"/>
<parameter id="instancePK1" value="#{pageFlowScope.instancePK1}"
xmlns="http://xmlns.oracle.com/adfm/uimodel"/>
<parameter id="instancePK2" value="#{pageFlowScope.instancePK2}"
xmlns="http://xmlns.oracle.com/adfm/uimodel"/>
<parameter id="instancePK3" value="#{pageFlowScope.instancePK3}"
xmlns="http://xmlns.oracle.com/adfm/uimodel"/>
<parameter id="instancePK4" value="#{pageFlowScope.instancePK4}"
xmlns="http://xmlns.oracle.com/adfm/uimodel"/>
<parameter id="instancePK5" value="#{pageFlowScope.instancePK5}"
xmlns="http://xmlns.oracle.com/adfm/uimodel"/>
<parameter id="taskflowId" value="#{pageFlowScope.taskflowId}"
xmlns="http://xmlns.oracle.com/adfm/uimodel"/>
<parameter id="parameterMap" value="#{pageFlowScope.parameterMap}"
xmlns="http://xmlns.oracle.com/adfm/uimodel"/>
</parameters>
</taskFlow>
50.8.3.2 Creating a Command Button to Invoke the Popup Dialog
Your web page should display a button that will invoke the popup operation.
Create an ADF command button component in the web page associated with the view activity of the calling task flow. Then drop an ADF popup component in the panel that contains the button. Then drop an ADF showPopupBehavior operation onto the button and set it to the ID of the popup component. Finally, drag a dialog onto the popup component.
You will also need to specify a listener for both the popup component and the dialog component. These listeners invoke methods on the managed bean to initialize the input parameters and save the user selections.
The following example shows a command button component with the showPopupBehavior operation nested on the button. The popup component appears in the same panel as the button and defines the popupFetchListener property to identify the launchPolicy() method on the bean referenced by the bean identifier objectInstanceBean. The dialog component defines the dialogListener property to identify the okCreatePolicy() method on the bean referenced by the same bean identifier. The name of the identifier corresponds to the managed bean declaration you create when you edit the calling task flow configuration file.
Note that the ADF region component element shown in the example will be created when you drop the data security object instance task flow as a region.
Button Component with Show Popup Operation to Invoke Dialog
...
<af:panelHeader id="phl12" text="Test Instance UI">
<af:panelGroupLayout id="pgl13" layout="horizontal">
<af:commandButton id="cb6" text="Launch Object Instance Popup"
partialSubmit="true">
<af:showPopupBehavior popupId="objInst"/>
</af:commandButton>
<af:popup id="objInst" contentDelivery="lazyUncached"
popupFetchListener="#{backingBeanScope.objectInstanceBean.launchPolicy}"
childCreation="deferred">
<af:dialog id="polDiag" modal="true" title="Object Instance UI"
affirmativeTextAndAccessKey="Save and Close" resize="on"
contentWidth="600" contentHeight="330"
stretchChildren="first"
dialogListener="#{backingBeanScope.objectInstanceBean.okCreatePolicy}">
<af:region value="#{bindings.ObjectInstTF1.regionModel}" id="r1"/>
</af:dialog>
</af:popup>
</af:panelGroupLayout>
</af:panelHeader>
50.8.3.3 Initialize the Object-Instance Task Flow Using a Managed Bean
Managed beans are Java classes that you register with the application in your calling task flow's configuration file. You will define two methods on a managed bean:
-
A popup fetch listener method to add properties to the managed bean that will initialize the input parameters of the data security task flows.
-
A dialog listener method to save the grants made by the end user to the database when the user closes the dialog.
When your application runs, and the end user clicks the button in the calling web page, the popup fetch listener method is invoked and the properties are declared, allowing the called data security task flow input parameters to be populated with the declared values.
The following example shows additional source code that your managed bean must include to initialize the object-instance (ObjectInstlTF) task flow.
The following example shows the source code you must add for the method your dialog listener invokes. In this case, the method is named okCreatePolicy() to match the method invoked by the dialog listener in Example 50-*.
To populate task flow input parameters with a managed bean:
Example 50-41 Source for Populating the ObjectInstTF Input Parameters
//Source for manaaged bean to populate and pass ObjectInstTF parameters
public void launchPolicy(PopupFetchEvent popupFetchEvent)
{
List actions = new ArrayList<ActionMap>();
ActionMap action1 = ActionMap.getActionMapForInstanceUI("View", "VIEW_EMP_M");
actions.add(action1);
ActionMap action2 = ActionMap.getActionMapForInstanceUI("Update",
"UPDATE_EMP_M");
actions.add(action2);
ActionMap action3 = ActionMap.getActionMapForInstanceUI("Create",
"CREATE_EMP_M");
actions.add(action3);
ActionMap action4 =
ActionMap.getActionMapForInstanceUI("Delete", "DELETE_EMP_M");
actions.add(action4);
ActionMap action5 =
ActionMap.getActionMapForInstanceUI("CustomFSOnlyAction",
"CUSTOMFSONLYACTION_EMP_M");
actions.add(action5);
AdfFacesContext context = AdfFacesContext.getCurrentInstance();
Map pageFlowScope = context.getPageFlowScope();
pageFlowScope.clear();
pageFlowScope.put("actions", actions);
pageFlowScope.put("objectName", "TEST_DS_EMP");
pageFlowScope.put("instancePK1", "2");
pageFlowScope.put("instancePK2", null);
pageFlowScope.put("instancePK3", null);
pageFlowScope.put("instancePK4", null);
pageFlowScope.put("instancePK5", null);
// If you want to use a customized task flow instead of people picker to select
// users, you need specify values for the taskflowId and parameterMap.
// Map<String, Object> paraMap = new HashMap<String, Object>();
// paraMap.put("pageTitle", "Custom User Selection");
// pageFlowScope.put("parameterMap", paraMap);
//Taskflow name
// pageFlowScope.put("taskflowId", "/WEB-INF/CustomDSUserTF.xml#CustomDSUserTF");
}
Example 50-42 Source for Saving the ObjectInstTF Grants
//Source for managed bean to save end user grant
public void okCreatePolicy(DialogEvent dialogEvent)
{
DataSecurityUIUtils.saveInstanceGrants(dialogEvent);
//Add your custom code if needed
}
50.8.3.4 Register the Managed Bean with Your Application's Task Flow
To declare the manage bean in the calling task flow's configuration file, you must enter a bean identifier name, the class path for the bean, and you must specify backing bean scope. The following example uses the bean identifier objectInstanceBean to match the bean references specified in the listener properties shown in Example 50-*.
To register the managed bean with the calling task flow:
- Open your application's task flow (the calling task flow) in the diagram editor.
- In the editor for the task flow, click the Source tab.
- In the source for the calling task flow, declare the managed bean by creating the
<managed-bean>element similar to the sample shown in the previous example.
Example 50-43 Managed Bean Definition in Calling Task Flow Configuration File
<adfc-config xmlns="http://xmlns.oracle.com/adf/controller" version="1.2">
<task-flow-definition id="MyCallingTaskFlow">
<default-activity id="__1">CallObjectInstTF</default-activity>
<managed-bean id="__4">
<managed-bean-name id="__5">objectInstanceBean</managed-bean-name>
<managed-bean-class id="__2">
oracle.apps.fnd.applcore.dataSecurity.view.DSObjectInstance</managed-bean-class>
<managed-bean-scope id="__3">backingBean</managed-bean-scope>
</managed-bean>
</task-flow-definition>
...
</adfc-config>
50.8.4 How to Grant the Data Security Task Flows Access to the Application Policy Store
A grant must be added to the jazn-data.xml policy store to allow your application to provision the LDAP policy store. The LDAP policy store is secured so that only authorized applications can make API calls needed to create and update grants in the store. For this purpose, a code source grant must be made to authorize the implementation code of the data security task flows to make credential store and policy store API calls. The following example shows the code source grant where <application-name> is the application name specified in the jazn-data.xml policy store.
To enable the application to access and update the domain policy store:
Example 50-44 Grant to Enable Policy Store Provisioning by Data Security Task Flow Source Code
<grant>
<grantee>
<codesource>
<url>file:${domain.home}/servers/${weblogic.Name}/tmp/_WL_user/<application-name>/-</url>
</codesource>
</grantee>
<permissions>
<permission>
<class>oracle.security.jps.service.policystore.PolicyStoreAccessPermission</class>
<name>context=APPLICATION,name=<application-name></name>
<actions>getApplicationPolicy,grant,revoke,alterAppRole,createAppRole,
alterAppRoleCategory</actions>
</permission>
</permissions>
</grant>
50.8.5 How to Grant the End User Access to the Data Security Task Flows
The data security task flows, when integrated into your application, behave like other web application resources secured by ADF Security. By default, ADF Security locks down application resources and therefore requires that you grant access rights to the members of the application roles for the task flows.
To grant view access to the task flows, you define a OPSS permission grant defined by the oracle.adf.controller.security.TaskFlowPermission class. The following example shows the permission definition that grants the users (identified by <grantee> in your application) view access rights to the task flows.
Note that the resources in the permission grant are identified by regular expression metacharacters .* (dot followed by an asterisk). This expression denote any number of arbitrary characters and effectively grants view rights on all task flows in the Oracle Fusion Applications data security path /WEB-INF/oracle/apps/fnd/applcore/dataSecurity/ui/taskflow/.
The grantee of the permission are the application roles that your application specifies. If you are using custom application roles not defined by Oracle Fusion Applications, a security manager will need to configure these application roles using Oracle Authorization Policy Manager. For example, an application role requires a role category definition.
To enable function security for the data security task flows:
Example 50-45 Grant to View Data Security Task Flows
<grant>
<grantee>
...
</grantee>
<permissions>
<permission>
<class>oracle.adf.controller.security.TaskFlowPermission</class>
<name>/WEB-INF/oracle/apps/fnd/applcore/dataSecurity/ui/taskflow/.*</name>
<actions>view</actions>
</permission>
</permissions>
</grant>
50.8.6 How to Map the Application to an Existing Application Stripe
Before you deploy the application, you need to identify the application stripe in the production environment. When deployed, the application will make use of the application roles and security policies defined by the application stripe. The following example shows the web.xml entry to identify the existing application stripe.
To map the application to the deployed application stripe:
Example 50-46 web.xml Parameter Identifies Deployed Application Stripe
<init-param>
<param-name>application.name</param-name>
<param-value><application-name></param-value>
</init-param>