Release 2 (9.0.2)
Part Number A90146-01
Home |
Solution Area |
Contents |
Index |
| Oracle9i Application Server Security Guide Release 2 (9.0.2) Part Number A90146-01 |
|
As described in the introductory chapter of this document, security can be organized into the three categories of authentication, authorization, and encryption. Oracle HTTP Server provides support for all three of these categories. It is based on the Apache Web server and its security infrastructure is primarily provided by the Apache module, mod_auth, and the Oracle modules, mod_ossl and mod_osso. The module mod_auth provides authentication based on user name and password pairs, mod_ossl provides confidentiality and authentication with X.509 client certificates over SSL, and mod_osso enables single sign-on for Web applications.
This chapter provides an overview of Oracle HTTP Server security features and configuration information for setting up a secure Web site using them. It contains these topics:
Chapter 3, "Configuring Oracle9iAS Single Sign-On" for information about configuring the Oracle module, mod_osso, that enables single sign-on for Web applications.
See Also:
Based on the Apache model, Oracle HTTP Server provides access control, authentication, and authorization methods that can be configured with access control directives that are used in the httpd.conf file. When URL requests arrive at Oracle HTTP Server, they are processed in a number of steps determined by the default design of the server and by what configuration parameters you set in the configuration files. The steps for handling URL requests are implemented through a module or plug-in architecture that is common to many Web listeners. Figure 4-1 shows how URL requests are handled by the server. Each step in this process is handled by a different server module depending on how the server is configured. For example, if only basic authentication is used, then the step labeled "Authentication" in Figure 4-1 represents the module, mod_auth.
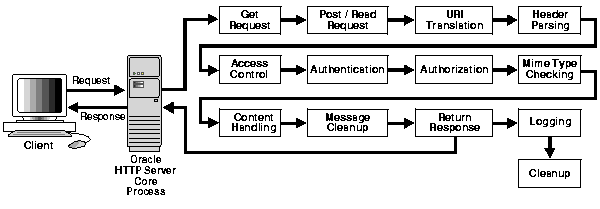
Oracle HTTP Server provides user authentication and authorization at two stages:
Parameters for all Oracle HTTP Server configuration directives that are described in this chapter must be entered in the main HTTP server configuration file called httpd.conf, which is located in the following directory:
ORACLE_HOME/Apache/Apache/conf/httpd.conf
ORACLE_HOME\Apache\Apache\conf\httpd.conf
The following sections explain how host-based access control and user authentication is handled in the HTTP server and how to configure them.
Early in the request processing cycle access control is applied, which can inhibit further processing based on the host name, IP address, or other characteristics such as browser type. You use the deny, allow, and order directives to set this type of access control. These restrictions are configured with Oracle HTTP Server configuration directives and can be based on particular files, directories, or URL formats using the <files>, <directory>, and <location> configuration directives as shown in the sample below:
<Directory /internalonly/>order deny, allow deny from all allow from 192.168.1 us.oracle.com</Directory>
In this example, requests originating from any IP address in the 192.168.1.* range or with the host name us.oracle.com are allowed access to files in the directory /internalonly/.
If you want to match objects at the file system level, then you must use <Directory> or <Files>. If you want to match objects at the URL level, then you must use <Location>. However, if you want to direct proxy control, then you must use <Directory>.
To set up access control for virtual hosts, place the AccessConfig directive inside a virtual host container in the server configuration file, httpd.conf. When used in a virtual host container, the AccessConfig directive specifies an access control policy contained in a file. The following example shows an excerpt from an httpd.conf file which provides the syntax for using AccessConfig this way:
... <VirtualHost ip.address.of.host.some_domain.com>... virtual host directives ... AccessConfig conf/access.conf</VirtualHost>
Using host-based access control schemes you can control access to restricted areas based on where HTTP requests originate. Oracle HTTP Server uses mod_access and mod_setenvif to perform host-based access control. When you enter configuration directives into the httpd.conf that use these modules, the server fulfills or denies requests based on the address or name of the host, or based on the HTTP request header contents.
You can use host-based access control to protect static HTML pages, CGI applications, or components.
Oracle HTTP Server supports four host-based access control schemes:
All of these allow you to specify the machines from which access to protected areas is granted or denied. Your decision to choose one or more of the host-based access control schemes is determined by which scheme most efficiently protects your restricted content and applications, or which scheme is easiest to maintain.
Controlling access with IP addresses is a preferred method of host-based access control. It does not require DNS lookups that consume time, system resources, and make your server vulnerable to DNS spoofing attacks. However, if IP addresses change without warning, your server is left unprotected.
To configure IP address-based access control, use the syntax shown in the following example:
<Directory /secure_only/> order deny,allow deny from all allow from 207.175.42.154 192.220.208.9 </Directory>
In this example, requests originating from all IP addresses except 207.175.42.154 and 192.220.208.9 are denied access to the /secure_only/ directory.
Domain name-based access control can be used with IP address-based access control to solve the problem of IP addresses changing without warning. When you combine these methods, if an IP address changes, then the secure areas of your site are still protected because the domain names you want to keep out will still be denied access.
To combine domain name-based with IP address-based access control, use the syntax shown in the following example:
<Directory /co_backgr/> order allow,deny allow from all # 141.217.24.179 is the IP for malicious.cracker.com deny from malicious.cracker.com 141.217.24.179 </Directory>
In this example all requests for directory /co_backgr/ are accepted except those that originate from the domain name malicious.cracker.com or the IP address 141.217.24.179. Although this is not a foolproof precaution against domain name or IP address spoofing, it protects your site from malicious.cracker.com even if they change their IP address.
You can control access based on subsets of networks, specified by IP address. The syntax is shown in the following example:
<Directory /payroll/> order deny,allow deny from all allow from 10.1.0.0/255.255.0.0 </Directory>
In this example, access is allowed from a network/netmask pair. A netmask shows how an IP address is to be divided into network, subnet, and host identifiers. Netmasks enable you to refer to only the host ID portion of an IP address.
The netmask in the example above, 255.255.0.0, is the default netmask setting for a Class B address. The binary ones (decimal 255) mask the network ID and the binary zeroes (decimal 0) retain the host ID of a given IP address.
You can use arbitrary environment variables for access control, instead of using IP addresses or domain names. Two directives, BrowserMatch and SetEnvIf, can be used for this type of access control.
Use BrowserMatch when you want to base access on the type of browser used to send a request. For example, if you want to allow access only to requests that come from a Netscape browser, then use the syntax shown in the following example:
BrowserMatch ^Mozilla netscape_browser <Directory /mozilla-area/> order deny,allow deny from all allow from env=netscape_browser </Directory>
Use SetEnvIf when you want to base access on header information contained in the HTTP request. For example, if you want to deny access from any browsers using HTTP version 1.0 or earlier, then use the syntax shown in the following example:
SetEnvIf Request_Protocol ^HTTP/1.1 http_11_ok <Directory /http1.1only/> order deny,allow deny from all allow from env=http_11_ok </Directory>
User authentication is a term for a process used to ensure that users are who they claim to be. Basic authentication uses a user name and password. SSL uses an exchange of keys and client certificates. Oracle9iAS Single Sign-On initially uses a user name and password that are stored on Oracle Internet Directory, but after initial authentication, it places a cookie in the user's browser. During subsequent user logins to applications that are registered to use single sign-on, the browser cookie authenticates users transparently until the cookie expires.
The type of user authentication that you choose to use depends on the type of content you want to protect. Typically, basic authentication that is based on user name and password pairs is adequate for static content that only requires minimal security within an intranet. For Internet communications, SSL, which encrypts data and supports X.509 client certificates, is usually used for transmitting sensitive information such as passwords and authenticating users to Web applications and databases. To provide additional security and convenience, Oracle HTTP Server also supports single sign-on, which allows users to log in to multiple Web applications using a single user name and password.
The following sections describe how to use basic authentication and SSL with Oracle HTTP Server:
Chapter 3, "Configuring Oracle9iAS Single Sign-On" for information about how single sign-on works and how to register Oracle HTTP Server to use the Oracle module mod_osso that supports communication with the Oracle9iAS Single Sign-On server.
See Also:
Basic authentication prompts for a user name and password before serving an HTTP request. When a browser requests a page from a protected area, Oracle HTTP Server responds with an Unauthorized message (status code 401) containing a WWW-Authenticate: header and the name of the realm configured by the configuration directive, AuthName. When the browser receives this response, it prompts for a user name and password. After the user enters a user name and password combination, the browser sends this information back to the server in an Authorization header. In the Authorization header message, the user name and password are encoded as a base 64 encoded string.
Frequently, basic user authentication and authorization are implemented together. User authentication, the second stage of security provided by Oracle HTTP Server, is based on user names and passwords that are checked against a list of known users and passwords. These user name and password pairs may be stored in a variety of forms, such as a text file, database, or directory service. Then configuration directives are used in httpd.conf to configure this type of user authentication on the server. For example, mod_auth uses the AuthUserFile directive to set up basic authentication.
Any authentication scheme that you devise requires that you use a combination of the configuration directives listed in Table 4-1.
User authorization involves checking the authenticated user against an access control list that is associated with a specific server resource such as a file or directory. To configure user authorization, place the require directive in the httpd.conf file, usually within a virtual host container. User authorization is commonly used in combination with user authentication. After the server has authenticated a user's user name and password, then the server compares the user to an access control list associated with the requested server resource. If Oracle HTTP Server finds the user or the user's group on the list, then the resource is made available to that user.
SSL is an encrypted communication protocol that is designed to securely send messages across the Internet. It resides between Oracle HTTP Server on the application layer and the TCP/IP layer, transparently handling encryption and decryption when a secure connection is made by a client.
SSL provides secure communication between client and server by allowing mutual authentication, the use of digital certificates for integrity, and encryption for confidentiality. The protocol is designed to support a range of choices for specific algorithms used for cryptography, message digests, and certificates. This allows algorithm selection for specific servers to be made based on legal, export, or other concerns, and also enables the protocol to take advantage of new algorithms. Choices are negotiated between client and server at the start of establishing a protocol session.
One common use of SSL is to secure Web HTTP communication between a browser and a Web server. This case does not preclude the use of non-secured HTTP. The secure version is simply HTTP over SSL (named HTTPS). The differences are that HTTPS uses the URL scheme https:// rather than http://, and its default communication port is 443.
mod_ossl is the Oracle Secure Sockets Layer (SSL) implementation in use with the Oracle database. mod_ossl replaces mod_ssl in the Oracle HTTP Server distribution. Oracle no longer supports mod_ssl. A tool is provided to enable you to migrate from mod_ssl to mod_ossl, and convert your text certificates to Oracle wallets.
mod_ossl supports SSL v. 3.0, and provides:
Table 4-2 identifies the differences between the Oracle module, mod_ossl, and mod_ssl.
| Feature | mod_ossl | mod_ssl |
|---|---|---|
|
SSL versions supported |
3.0 |
2.0, 3.0, TLS 1.0 |
|
Certificate management |
Text file |
|
|
Per-directory SSL renegotiation |
no |
yes |
|
1
Oracle Wallet Manager is a tool that manages certificates for mod_ossl. 2 Supports obfuscated passwords. |
The mod_ssl directives listed below are not supported by mod_ossl.
Chapter 5 for information about Oracle Wallet Manager and how to use it to request, store, and manage certificates.
See Also:
Directives are classified according to the context in which they can be used: global, per-server, and per-directory.
Note that each class is a subset of the class above it. For example, directives from the per-directory class can also be used in the per-server and global contexts, and directives from the per-server class can be used in the global context.
To configure SSL for your HTTP server, you enter the mod_ossl directives you want to use in the httpd.conf file. Each directive is described below.
|
See Also:
"Specifying Configuration Parameters in httpd.conf" for general information about how to use these parameters in the main HTTP server configuration file. |
|
Description: |
Specifies the location of the wallet with its WRL.
Oracle Corporation recommends that you use wallets created with the Auto Login feature of Oracle Wallet Manager. Wallets that are created with the Auto Login feature do not require a password, so when they are used, the |
|
Syntax: |
The format of |
|
Example: |
Other values of wrl may be used as permitted by the Oracle SSL product. |
|
Default: |
None |
|
Context: |
server configuration, virtual host |
|
See Also:
"Using Auto Login" for information about using the Auto Login feature of Oracle Wallet Manager. |
|
Description: |
Wallet password needed to access the wallet specified within the same context. You can choose either a cleartext wallet password or an obfuscated password. The obfuscated password is created with the command line tool If you must use a regular wallet, Oracle Corporation recommends that you use the obfuscated password instead of a cleartext password. |
|
Syntax: |
If no password is required do not set this directive. Note: If a wallet created with the Auto Login feature of Oracle Wallet Manager is used, then do not set this directive because these wallets do not require passwords. |
|
Default: |
None |
|
Context: |
server configuration, virtual host |
|
Description: |
Specifies the directory where PEM-encoded Certificate Revocation Lists (CRLs) are stored. These CRLs come from the CAs (Certificate Authorities) that you accept certificates from. If a client attempts to authenticate itself with a certificate that is on one of these CRLs, then the certificate is revoked and the client cannot authenticate itself with your server. |
|
Syntax: |
|
|
Example: |
SSLCARevocationPath /ias2/Apache/conf/ssl.crl/ |
|
Default: |
None |
|
Context: |
server config, virtual host |
|
Description: |
Specifies the file where you can assemble the Certificate Revocation Lists (CRLs) from CAs (Certificate Authorities) that you accept certificates from. These are used for client authentication. Such a file is the concatenation of various PEM-encoded CRL files in order of preference. This directive can be used alternatively or additionally to SSLCARevocationPath. |
|
Syntax: |
|
|
Example: |
SSLCARevocationFile /ias2/Apache/conf/ssl.crl/ca_bundle.crl |
|
Default: |
None |
|
Context: |
server config, virtual host |
|
Description: |
Number of seconds before an SSL session in the session cache expires. |
|
Syntax: |
|
|
Default: |
300 |
|
Context: |
server configuration |
|
Description: |
Specifies the SSL cipher suite that the client can use during the SSL handshake. This directive uses a colon-separated cipher specification string to identify the cipher suite. Table 4-4 shows the tags you can use in the string to describe the cipher suite you want. The tags are joined together with prefixes to form the cipher specification string. |
|
|
Valid Values: |
Adds the cipher to the list and place them in the correct location in the list Remove the cipher from the list (can be added later) Remove the cipher from the list permanently |
|
|
Example: |
In this example, all ciphers are specified except low strength ciphers and those using the Diffie-Hellman key negotiation algorithm. |
|
|
Syntax: |
|
|
|
Default: |
None |
|
|
Context |
server configuration, virtual host, directory |
|
|
Note:
|
|
Description: |
Specifies whether or not a client must present a certificate when connecting. |
|
Valid Values: |
|
|
Syntax: |
|
|
Default: |
None |
|
Context |
server configuration, virtual host |
|
Description: |
Controls various runtime options on a per-directory basis. In general, if multiple options apply to a directory, the most comprehensive option is applied (options are not merged). However, if all of the options in an |
|
Valid Values: |
|
|
Valid Values: (for SSLOptions continued) |
|
|
Syntax: |
|
|
Default: |
None |
|
Context |
server configuration, virtual host, directory |
|
Description: |
Denies access unless an arbitrarily complex boolean expression is true. The expression must match the syntax below (given as a BNF grammar notation): |
|
|
expr ::= "true" | "false" "!" expr expr "&&" expr expr "||" expr "(" expr ")" |
|
|
comp ::=word "==" word | word "eq" word word "!=" word |word "ne" word word "<" word |word "lt" word word "<=" word |word "le" word word ">" word |word "gt" word word ">=" word |word "ge" word word "=~" regex word "!~" regex wordlist ::= word wordlist "," word |
|
|
word ::= digit cstring variable function |
|
|
digit ::= [0-9]+ |
|
|
cstring ::= "..." |
|
|
variable ::= "%{varname}" Table 4-6 and Table 4-7 list standard and SSL variables. These are valid values for varname. |
|
|
function ::= funcname "(" funcargs ")" For funcname, the following function is available: file(filename) The file function takes one string argument, the filename, and expands to the contents of the file. This is useful for evaluating the file's contents against a regular expression. |
|
Syntax: |
|
|
Default: |
None |
|
Context |
directory |
If you are using an Oracle Wallet that has been created with Auto Login enabled (an SSO wallet), then you do not need to use this utility. However, if you must use a regular wallet with a password, then Oracle Corporation recommends that you use the password obfuscation tool iasobf, which is located in the HTTP server bin directory to generate an obfuscated wallet password from a cleartext password.
To generate an obfuscated wallet password, the command syntax is:
iasobf -p password
The obfuscated password is printed to the terminal. The arguments are optional. If you do not type them, the tool will prompt you for the password.
|
See Also:
All of the following documents can be found in the Oracle9iAS Documentation Library unless otherwise specified.
|
|
|
 Copyright © 2002 Oracle Corporation. All Rights Reserved. |
|