Release 2 (9.0.2)
Part Number A96114-01
Home |
Solution Area |
Contents |
Index |
| Oracle9iAS Single Sign-On Application Developer's Guide Release 2 (9.0.2) Part Number A96114-01 |
|
The Oracle9iAS Single Sign-On Software Development Kit (SDK) consists of application programming interfaces (APIs) for PL/SQL and Java. These APIs are used to create partner applications--that is, applications enabled for Single Sign-On. Chapter 4, "Using the PL/SQL and Java APIs", provides code that shows how the APIs might be implemented.
The chapter covers the following topics:
Applications that use the SDK to enable Single Sign-On are required to implement the functions and procedures in the package WWSEC_SSO_ENABLER if PL/SQL is the language of implementation. The classes in oracle.security.sso.enabler are used if Java is the language of choice. Applications that are integrated with the SDK are called partner applications. They incorporate logic that enables them to delegate authentication, but not authorization, to the Single Sign-On server.
Figure 3-1 illustrates the authentication steps in SDK-enabled Single Sign-On. To understand how the process differs from mod_osso authentication, see "How Mod_osso Works" in Chapter 2, "Developing Applications Using Mod_osso."
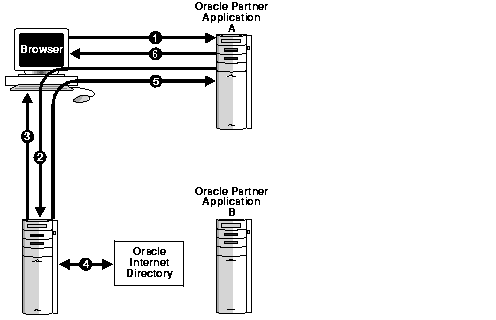
If the authenticated user requests Partner Application B, he need not authenticate again. The Single Sign-On server retrieves his credentials from the Single Sign-On cookie upon redirect (Step 2).
This section covers the following topics:
The functions and procedures in this section are part of the WWSEC_SSO_ENABLER package. This package is used to enable a PL/SQL application to become a partner application.
The section covers the following functions and procedures:
This function generates a redirect URL, along with SITE2PSTORETOKEN, that the Single Sign-On server parses.
FUNCTION GENERATE_REDIRECT ( P_LSNR_TOKEN IN VARCHAR2 , P_URL_REQUESTED IN VARCHAR2 , P_URL_CANCEL IN VARCHAR2 , P_FORCED_AUTH IN NUMBER DEFAULT SIMPLE_AUTH ) RETURN VARCHAR2;
WWSEC_SSO_ENABLER.GENERATE_REDIRECT ( p_lsnr_token => listener token p_url_requested => requested url p_url_cancel => cancel url p_forced_auth => forced authentication flag redirecturl => redirect url );
This procedure parses the URL cookie that is generated by the GENERATE_REDIRECT function on the Single Sign-On server side.
PROCEDURE parse_url_cookie ( P_LSNR_TOKEN IN VARCHAR2 , P_ENC_URL_COOKIE IN VARCHAR2 , P_URL_REQUESTED OUT VARCHAR2 , P_SSO_USERNAME OUT VARCHAR2 , P_SSO_USER_DN OUT VARCHAR2 , P_SSO_USER_GUID OUT VARCHAR2 , P_SUBSCRIBER_NAME OUT VARCHAR2 , P_SUBSCRIBER_DN OUT VARCHAR2 , P_SUBSCRIBER_GUID OUT VARCHAR2 , P_USER_IPADDRESS OUT VARCHAR2 , P_SSO_TIMEREMAINING OUT NUMBER , P_NLS_LANGUAGE OUT VARCHAR2 , P_NLS_TERRITORY OUT VARCHAR2 );
WWSEC_SSO_ENABLER.PARSE_URL_COOKIE ( p_lsnr_token => listener token p_enc_url_cookie => encrypted URL cookie p_url_requested => requested URL p_sso_username => authenticated SSO username p_sso_user_dn => authenticated SSO user DN p_sso_user_guid => authenticated SSO user GUID p_subscriber_name => subscriber name p_subscriber_dn => subscriber DN p_subscriber_guid => subscriber GUID p_user_ipaddress => ipaddress of the sso user's machine p_sso_timeremaining => remaining Single Sign-On session duration p_nls_language => language selection of sso user p_nls_territory => territory selection of sso user );
This function returns the partner application registration information specified by the listener token.
PROCEDURE GET_ENABLER_CONFIG ( P_LSNR_TOKEN IN VARCHAR2, P_SITE_TOKEN OUT VARCHAR2, P_SITE_ID OUT VARCHAR2, P_LS_LOGIN_URL OUT VARCHAR2, P_LS_LOGOUT_URL OUT VARCHAR2, P_URL_COOKIE_VERSION OUT VARCHAR2, P_ENCRYPTION_KEY OUT VARCHAR2, P_IPADDR_CHECK OUT VARCHAR2 );
WWSEC_SSO_ENABLER_PRIVATE.GET_ENABLER_CONFIG ( p_lsnr_token => listener token p_site_token => site token p_site_id => site token p_ls_login_url => login url of SSO Server p_ls_logout_url => Single Sign-Off URL of SSO Server p_url_cookie_version => url cookie version p_encryption_key => encryption key p_ipaddr_check => if ip address should be verified
This procedure stores the partner application registration information, specified by the listener token, in the enabler configuration table.
PROCEDURE CREATE_ENABLER_CONFIG ( P_LSNR_TOKEN IN VARCHAR2, P_SITE_TOKEN IN VARCHAR2, P_SITE_ID IN VARCHAR2, P_LS_LOGIN_URL IN VARCHAR2, P_LS_LOGOUT_URL IN VARCHAR2, P_URL_COOKIE_VERSION IN VARCHAR2, P_ENCRYPTION_KEY IN VARCHAR2, P_IPADDR_CHECK IN VARCHAR2 );
WWSEC_SSO_ENABLER.CREATE_ENABLER_CONFIG ( p_lsnr_token => listener token p_site_token => site token p_site_id => site token p_ls_login_url => login url of SSO Server p_ls_logout_url => Single Sign-Off URL of the Single Sign-On server p_url_cookie_version => URL cookie version p_encryption_key => Encryption key p_ipaddr_check => If IP address should be verified )
This procedure modifies the partner application registration information specified by the listener token.
PROCEDURE MODIFY_ENABLER_CONFIG ( P_LSNR_TOKEN IN VARCHAR2, P_SITE_TOKEN IN VARCHAR2, P_SITE_ID IN VARCHAR2, P_LS_LOGIN_URL IN VARCHAR2, P_LS_LOGOUT_URL IN VARCHAR2, P_URL_COOKIE_VERSION IN VARCHAR2, P_ENCRYPTION_KEY IN VARCHAR2, P_IPADDR_CHECK IN VARCHAR2 );
WWSEC_SSO_ENABLER.MODIFY_ENABLER_CONFIG ( p_lsnr_token => listener token p_site_token => site token p_site_id => site token p_ls_login_url => login url of SSO Server p_ls_logout_url => Single Sign-Off URL of SSO Server p_url_cookie_version => url cookie version p_encryption_key => encryption key p_ipaddr_check => if IP address should be verified or not )
This procedure deletes the partner application registration information specified by the listener token.
PROCEDURE DELETE_ENABLER_CONFIG ( P_LSNR_TOKEN IN VARCHAR2 );
Parameter |
Description |
|---|---|
|
|
Listener token to get the necessary partner application registration configuration |
WWSEC_SSO_ENABLER.DELETE_ENABLER_CONFIG ( p_lsnr_token => listener token );
This function returns the encrypted cookie body.
FUNCTION ENCRYPT_COOKIE ( p_lsnr_token in varchar2, p_cookie in varchar2 ) return varchar2;
| Parameter | Description |
|---|---|
|
|
Listener token to get the necessary partner application registration configuration |
Example WWSEC_SSO_ENABLER.ENCRYPT_COOKIE ( p_lsnr_token => listener token p_enc_cookie => cookie value to be encrypted )
This function returns the decrypted cookie value from the encrypted cookie.
( P_LSNR_TOKEN IN VARCHAR2, P_ENC_COOKIE IN VARCHAR2 ) RETURN VARCHAR2;
| Parameter | Description |
|---|---|
|
|
Listener token to get the necessary partner application registration configuration |
|
|
Cookie value to be encrypted |
WWSEC_SSO_ENABLER.DECRYPT_COOKIE ( p_lsnr_token => listener token p_enc_cookie => cookie value to be encrypted )
The Single Sign-On SDK contains two tables for partner applications: SEC_WWSEC_ENABLER_CONFIG_INFO$ and WWSEC_SSO_LOG$. The first stores configuration information that enables the application to determine which Single Sign-On server to connect to. The second stores client-side debug information, which can be accessed when debugging is enabled.
CREATE TABLE wwsec_enabler_config_info$ ( lsnr_token VARCHAR2(255) , site_token VARCHAR2(255) , site_id VARCHAR2(255) , ls_login_url VARCHAR2(1000) , urlcookie_version VARCHAR2(80) , encryption_key VARCHAR2(1000) , encryption_mask_pre VARCHAR2(1000) , encryption_mask_post VARCHAR2(1000) , url_cookie_ip_check VARCHAR2(1) );
CREATE TABLE wwsec_sso_log$ ( , SUBSCRIBER_ID NUMBER NOT NULL , id NUMBER , msg VARCHAR2(1000) , log_date DATE );
Table 3-9 lists and describes the exceptions raised by PL/SQL functions and procedures.
Java APIs can be used in place of PL/SQL APIs to create partner applications. To learn how to use the Java APIs, see Oracle9iAS Single-On API Reference (Javadoc).
|
|
 Copyright © 2002 Oracle Corporation. All Rights Reserved. |
|