Release 3.0.9
Part Number A90343-01
Library |
Solution Area |
Contents |
Index |
| Oracle9iAS Single Sign-On Application Developer's Guide Release 3.0.9 Part Number A90343-01 |
|
This chapter describes the components of Oracle9iAS Single Sign-On, the kinds of applications to which it can provide access, and the authentication methods it uses. It explains the process and architecture through which Oracle9iAS Single Sign-On authenticates users to applications.
This chapter contains these topics:
Oracle9iAS Single Sign-On has two components:
The first time that a user seeks access to an application, the Login Server:
In subsequent user logins, the login cookie provides the Login Server with the user's identity, and indicates that authentication has already been performed. If there is no login cookie, the Login Server presents the user with a login challenge.
To guard against sniffing, the Login Server can send the login cookie to the client browser over an encrypted SSL channel.
The login cookie expires with the session, either at the end of a time interval specified by the administrator, or when the user exits the browser. It is never written to disk.
A partner application can expire its session through its own explicit logout.
The Oracle9iAS Single Sign-On API enables:
There are two kinds of applications to which Oracle9iAS Single Sign-On provides access:
Partner applications are integrated with the Login Server. They contain a Oracle9iAS Single Sign-On API that enables them to accept a user's identity as validated by the Login Server.
External applications are web-based applications that retain their authentication logic. They do not delegate authentication to the Login Server and, as such, require a user name and password to provide access. Currently, these applications are limited to those which employ an HTML form for accepting the user name and password. The user name may be different from the SSO user name, and the Login Server provides the necessary mapping.
Oracle9iAS Single Sign-On can use one of these authentication methods:
Whenever a user accesses either a partner application or an external application, the Login Server first authenticates that user.
This section contains these topics:
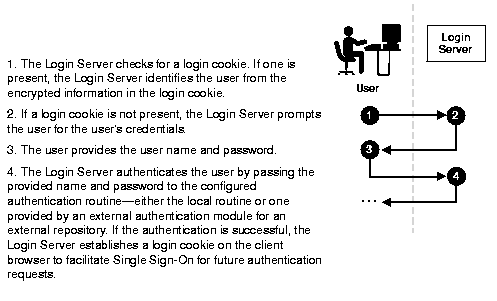
The Login Server authenticates a user as follows:
When a user seeks access to a partner application, the following:
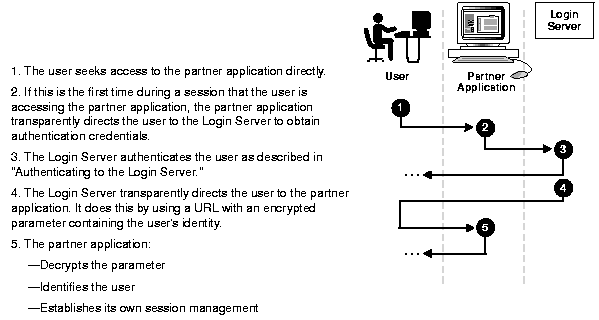
If, during the same session, the user again seeks access to the same or to a different partner application, the Login Server does not prompt the user for user name and password. Instead, the Login Server obtains that information from the login cookie on the client browser.
You can accessing an external application through Oracle9iAS Portal. In this scenario, Oracle9iAS Portal functions as a partner application.
This section contains these topics:
When a user seeks access to an external application by way of Oracle9iAS Portal, Oracle9iAS Single Sign-On authenticates the user to Oracle9iAS Portal through this process:
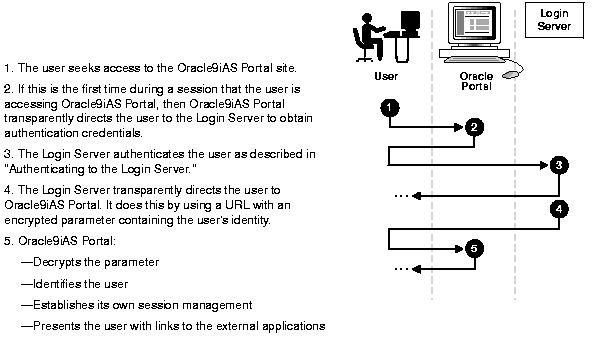
If, during the same session, the user again seeks access to Oracle9iAS Portal, the Login Server does not prompt the user for user name and password. Instead, it obtains that information from the login cookie on the client browser.
Oracle9iAS Single Sign-On uses the process described in the next figure under these conditions:
Oracle9iAS Single Sign-On uses the process described in the next figure if the user:
If the user has not stored a user name and password in the Login Server password store, then Oracle9iAS Single Sign-On follows the process described in "Authenticating to an External Application for the First Time".
|
|
 Copyright © 2001 Oracle Corporation. All Rights Reserved. |
|