Release 3.0.8
Part Number A87566-01
Library |
Service |
Contents |
Index |
| Oracle Portal Configuration Guide Release 3.0.8 Part Number A87566-01 |
|
This chapter provides information about Oracle Portal after installation and the configuration tasks that you can perform.
|
See: For information about installing Oracle Portal with Oracle9i Application Server, see the "Oracle9i Application Server Installation Guide". |
Specific topics covered include:
Oracle Portal is installed primarily in the Oracle8i database, with some supporting components installed on the middle-tier in Oracle9i Application Server.
If you install Oracle Portal in the default mode, five schemas are created. The default base schema name is portal30 which you can change at installation time.
With each Oracle Portal installation, a default set of login accounts is created. If the product is installed in a schema named portal30, the following default accounts are created:
|
See also: Task topics in the "Working with Users" folder from the Oracle Portal Online Help content area. |
The following groups are created at installation time:
|
See also: Task topics in the "Working With Users" folder from the Oracle Portal Online Help content area. |
After Oracle Portal is installed, access it by entering the following URL in your browser:
http://<hostname>:<portnumber>/pls/<dad>
You are prompted to enter the Single Sign-On (SS0) username and password before gaining access to Oracle Portal. The defaults are as follows:
Username: portal30
Password: portal30
|
See also:
|
You can simplify the full URL created by the Oracle Portal installation to a more memorable or meaningful URL using the Apache Redirect directive. In this way, end users can access Oracle Portal by entering a simple URL.
By default, the URL for a new Oracle Portal installation requires you to enter:
http://<hostname>:<portnumber>/pls/<dad>
You can simplify this URL to:
http://<hostname>/<redirectpath>
http.conf. By default this file is located in the following directory:
<ORACLE_HOME>/Apache/Apache/conf/
Redirect /<DADnamepath> http://<hostname>:<portnumber>/pls/<dad>
Redirect /portalhome http://mysite.oracle.com:80/pls/portal30
In this example, end users can enter the following:
http://mysite.oracle.com/portalhome
to access the full URL which is as follows:
http://mysite.oracle.com:80/pls/portal30
This technique also works with any valid path that is appended to the URL. For example, if you want to display the Oracle Portal Online Help Content Area, enter:
http://mysite.us.oracle.com/portalhome/url/folder/ONLINE_HELP
You can choose to install and display the Oracle Portal user interface in any of the 24 supported languages from your browser. To install support for a given language, run the wwvseedus.sql and langinst.csh scripts. Once the language is installed you use the Set Language portlet to choose which language Oracle Portal should use.
The supported languages and their abbreviations are listed in the following table:
To install support for a given language in Oracle Portal:
<ORACLE_HOME>/portal30/admin/plsql directory.
langinst.csh <-s portal_schema> <-p portal_password> <-o sso_schema> <-d sso_ password> <-c portal_connect_string> -l <language> -available
langinst.cmd <-s portal_schema> <-p portal_password> <-o sso_schema> <-d sso_ password> <-c portal_connect_string> -l <language> -available
langinst.csh -s portal30 -p portal30 -o portal30_sso -d portal30_sso -c orcl -l cs -available
| Parameter | Description |
|---|---|
|
|
The database schema for the Oracle Portal database objects. Default = PORTAL30 |
|
|
The Oracle database password for the Oracle Portal schema. Default = <portal_schema> |
|
|
The Oracle database schema for Login Server objects. Default = <portal_schema>_SSO |
|
|
The Oracle database password for Login Server schema. Default = <sso_schema> |
|
|
The connect string for the database in which the Oracle Portal schema is installed. Provide the connect string only if the schema is located on a remote database. |
|
|
The abbreviation for the language you want to install. See Table 2-5, "Supported languages and abbreviations" above. |
|
|
(Required) Ensures that the tabs are translated. |
Typically, the Set Language portlet is added to your content area home page, but you can add it to any page. Refer to the Oracle Portal online help content area for instructions on how to add portlets to pages.
This section describes how to use Oracle Universal Installer to deinstall Oracle products (which deinstalls them from the Oracle Universal Installer inventory) instead of removing them manually.
To deinstall Oracle Portal:
The Welcome window for Oracle Universal Installer appears.
The Inventory dialog box appears.
The Inventory Confirmation window appears.
The products are deinstalled from your computer. The Inventory dialog box appears without the deinstalled products.
Deleting a single Oracle Portal schema or the Login Server is performed from the Oracle Portal Configuration Assistant - Step 1 of 6: Installation Options.
To deinstall an Oracle Portal schema or the Login Server:
Choose Start -> Programs -> Oracle Home -> Oracle Portal Configuration Assistant
Go to the $OH/assistants/opca directory and run the launch.sh script
Click the option to Deinstall Oracle Portal or the Login Server.
If you want to allow users to create new accounts for themselves through a link on the Login Portlet, you do so by installing the self-registration feature as follows:
wwsso_api_user_admin. This synonym must be called wwsso_api_user_admin.
wwsso_api_user_admin package in the Login Server SSO schema to the user administration access schema.
wwctx_api_vpd package. This synonym must be called wwctx_api_vpd.
wwctx_api_vpd package in the Login Server SSO schema to the user administration access schema.
<ORACLE_HOME>portal30/admin/plsql directory of the directory in which Oracle Portal is installed.
selfreg.csh -s <portal_schema> -p <portal_password> -ua <sso_uadmin_schema> -c <portal_connect_string> -dblink <sso_uadmin_dblink>
selfreg.cmd -s <portal_schema> -p <portal_password> -ua <sso_uadmin_schema> -c <portal_connect_string> -dblink <sso_uadmin_dblink>
selfreg.csh -s myportal -p myportal -ua myportal_sso_ua -c orcl -dblink uadmin_ link
|
See: "Customizing the Login Portlet" topic in the Oracle Portal Online Help Content Area to continue. |
You can switch on and off Beta features from the Oracle Portal 3.0.8 Global Settings page, in the following way:
Oracle Portal and the Login Server can be configured to run in HTTPS mode if your portal requires increased security. For optimal performance, you can also choose to have a mixed configuration where Oracle Portal is run in HTTP mode and the Login Server is run in HTTPS mode.
Secure Socket Layer (SSL) is responsible for securing Web HTTP communication between a browser and a Web server in plain HTTP over SSL (named HTTPS). Enabling SSL to work with the Oracle HTTP Server is handled by the mod_ssl package which is provided with the Apache Web server. It uses the URL scheme HTTPS rather than HTTP and a different server port.
For more information about enabling and disabling SSL, visit the Apache interface to mod_SSL at the following location:
http://www.modssl.org
Certificates are encrypted files which allow a client and server to pass sensitive data without the fear of that data being read by unauthorized clients. Oracle Portal supports the x.509 certificate standard. This is the most popular standard, and is the type of certificate supplied by most major certificate authorities.
Certificates can be either 40 bit or 128 bit encryption strengths. The greater the number of bits, the more secure the certificates. There are three major types of certificates which operate differently depending upon the certificate type which include:
These certificates can be purchased from many different authorities. Oracle Portal currently supports Thawte, Verisign, and Netscape certificate providers.
|
Note: Do not purchase certificates with the V3 extension as these are not supported by Oracle Portal. |
In addition to the certificate, you also need specific signature, and/or chain files from the provider of your certificate. These files are available from your provider's Web site or customer service.
The Certificate Authority (CA) file is the base signature file for the certificate file you have purchased. This file validates the certificate you are using. It informs clients that they can trust the certificate they have received. You require a CA file for any type of certificate you use.
The certificate chain file links your certificate to the CA file. You require one of these files if you are using a Global Site ID or if you are using other types of certificates from another provider.
There are several files involved with the certificates. Put these files in the appropriate directory. You can setup the configuration differently, however, this is the standard configuration.
With HTTPS, you must use certificates for increased security in Oracle Portal. In this case, the Parallel Servlet must be aware of which port(s) are operating under HTTPS. To set this up, edit the zone.properties file which is located in the following location by default:
| Operating System | Location |
|---|---|
|
Windows NT/2000 |
<ORACLE_HOME>\Apache\Jserv\servlets\zone.properties |
|
UNIX |
<ORACLE_HOME>/Apache/Jserv/etc/zone.properties |
Add the following line to the zone.properties file:
servlet.page.initArgs=httpsports=<port1>:<port2>:. . . :<portn>
Each port in this list operates using the HTTPS protocol, and must have a certificate created on the Oracle HTTP Server powered by Apache on that port.
|
See also:
|
The JServ configuration file, zone.properties, is used by the servlets at initialization time. The Parallel Page Engine uses this file to get certain information for it to run properly. The file indicates which ports are configured for HTTPS in order for the Parallel Page Engine to know which ports are secure ports and thus use the appropriate protocol on each port. You can add as many ports as needed for secure communication by separating the port numbers with a colon (:).
The line in the zone.properties file should look similar to the following:
|
One Port |
|
|
Multiple Ports |
|
This section addresses how to configure Oracle Portal for HTTPS. It is possible to configure the system so that only the Login Server is configured for HTTPS, or configure it such that both Oracle Portal and the Login Server use HTTPS.
The Apache mod_ssl documentation describes how to configure the server to support HTTPS ports. After configuring the server to support HTTPS ports, run the ssodatan or ssodatax script(s), specifying the appropriate protocol and ports. For example, if you wanted to configure the Login Server to use HTTPS, but have Oracle Portal on HTTP, then run the ssodatan script as follows:
ssodatan -w http://Oracle Portal.acme.com/pls/Oracle Portal30/ -l https://login.acme.com/pls/Oracle Portal30_sso/ -s Oracle Portal30 -o Oracle Portal30_sso
The following sections address the particular requirements for configuring Oracle Portal for HTTPS.
The Oracle HTTP Server configuration file, httpd.conf, contains all of the configuration information for the Oracle HTTP Server powered by Apache, including the certificate configuration. Enter the path locations for the following configuration lines. These configuration lines should already exist in comment form (;).
|
Note:
Do not use the environment variables such as your |
The following subsections indicate the configuration entries required in the httpd.conf file, corresponding to each type of certificate. These configuration entries have been used successfully to set up Verisign certificates.
The usage varies slightly depending upon the certificate type you are installing. For example, if the certificate you are using has a chain file, then follow the Global Site ID configuration described below. If your certificate only uses a CA certificate file, then use the Secure Site ID configuration.
|
Note: The Chain file and CA Certificate file appear to be inverted with their configuration entries. This is intentional, and necessary for Oracle Portal to work properly. |
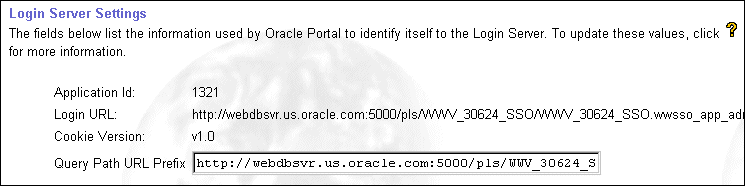
Oracle Portal maintains the URL prefix of the Login Server which accesses certain information through HTTP calls from the database, using the UTL_HTTP package. These calls must be done through HTTP rather than HTTPS.
Thus, if Oracle Portal and the Login Server are configured to use HTTPS, access to an HTTP port on the Login Server is still required to support these interfaces. The calls made across this interface are required for the following reasons:
To set this URL prefix, which is called the Login Server Query Path URL, complete these steps:
Text description of the illustration logssl.gif
By default, it is the same prefix as specified for the Login Server when running the ssodatan or ssodatax scripts. However, if these scripts specify an HTTPS protocol, then manually update this parameter to use an HTTP protocol.
If you are using SSL, the default port is 443. With Oracle Portal versions prior to 3.0.8, you need to create two enabler configuration entries, and two corresponding partner configuration entries on the Login Server. Specify the :443 port for one entry, and exclude it for the additional entry.
To add the additional entry, follow the basic procedure of adding the partner entry on the Login Server using the Login Server Administration user interface, and then add the configuration entry on the Oracle Portal side by using the ssodatax script.
If using Oracle Portal version 3.0.8 or later, you only need a single entry - one which excludes the :443 from the URL.
In the Oracle HTTP Server configuration file, httpd.conf, comment out the following line to permit Microsoft Internet Explorer browsers to work in HTTPS mode:
SetEnvIf User-Agent ".*MSIE.*" nokeepalive ssl-unclean-shutdown
If you want to setup a virtual host, it can be done in one of two ways:
When the IP name is used, several aliases use the same IP address. In this case, Apache (or any browser supporting virtual name addresses) looks at the Host field in the HTTP request and determines which of the virtual addresses should be emulated.
However, when SSL is used, the IP name is encrypted. This causes the problem, because the software does not know which decryption key to use since the keys differ by virtual name. If there were 1000 separate virtual addresses supported, then on average the software would try 500 different keys to determine which key to use to decode the message. This is not practical, at least for performance reasons.
https://ssladdress.com/virtualname1/<page desired>).
|
|
 Copyright © 2001 Oracle Corporation. All Rights Reserved. |
|