10g (9.0.4)
Part Number B12118-01
Home |
Solution Area |
Contents |
Index |
| Oracle® Internet Directory Administrator's Guide 10g (9.0.4) Part Number B12118-01 |
|
Oracle Delegated Administration Services, 2 of 8
Oracle Delegated Administration Services is a set of pre-defined, Web-based units for performing directory operations on behalf of a user. It frees directory administrators from the more routine directory management tasks by enabling them to delegate specific functions to other administrators and to end users. It provides most of the functionality that directory-enabled applications require, such as creating a user entry, creating a group entry, searching for entries, and changing user passwords.
You can use Oracle Delegated Administration Services to develop your own tools for administering application data in the directory. Alternatively, you can use the Oracle Internet Directory Self-Service Console, a tool based on Delegated Administration Services. This tool comes ready to use with Oracle Internet Directory.
This section contains these topics:
Applications built by using Oracle Delegated Administration Services enable you to grant a specific level of directory access to each type of user. For example, look at Figure 30-1, which shows the various administrative levels in a hosted environment.
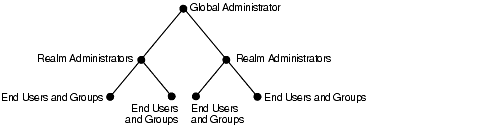
The global administrator, with full privileges for the entire directory, can delegate to realm administrators the privileges to create and manage the realms for hosted companies. These administrators can, in turn, delegate to end users and groups the privileges to change their application passwords, personal data, and preferences. Each type of user can thus be given the appropriate level of privileges.
Oracle Delegated Administration Services uses an Oracle Application Server Containers for J2EE (OC4J) that is enabled for small Java programs, called servlets. Together, the OC4J and the servlets:
Figure 30-2 shows the flow of information between components in a Oracle Delegated Administration Services environment.
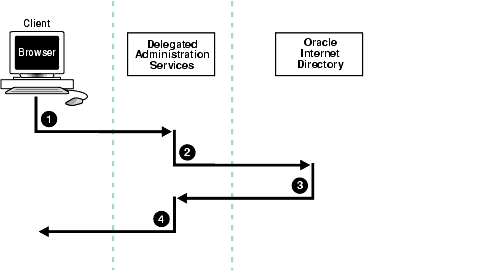
As Figure 30-2 shows:
When a user logs into an Oracle component, that component may need to obtain information from the directory on the end user's behalf--for example, the password verifier. To do this, the component typically logs into the directory as a proxy user, a feature that enables it to switch its identity to that of the end user.
A problem, however, is that the greater the number of components logging into the directory as proxy users, the greater the risk of a malicious user accessing the directory as a proxy user. To prevent this security problem, the Oracle Delegated Administration Services centralizes proxy user access.
In a Oracle Delegated Administration Services environment, each component, instead of logging into the directory as a proxy user, logs into the central Oracle Delegated Administration Services. Oracle Delegated Administration Services then logs into the directory as a proxy user, switches its identity to that of the end user, and performs operations on that user's behalf. Centralizing proxy user directory access in this way replaces the less secure strategy of granting proxy user access to every component accessing the directory.
Figure 30-3 shows the proxy user feature in an Oracle Delegated Administration Services environment. End users or delegated administrators log in to a central Oracle Delegated Administration Services. They do this by using the Oracle Internet Directory Self-Service Console, the consoles of other Oracle components such as OracleAS Portal, or those of third-party applications. The Oracle Delegated Administration Services then logs into Oracle Internet Directory as a proxy user.
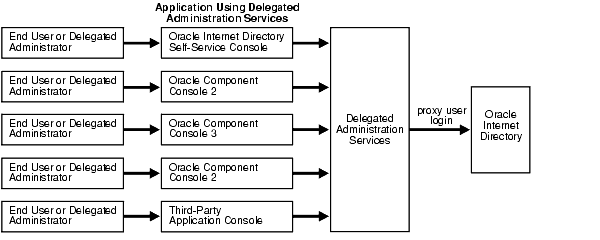
|
|
 Copyright © 1999, 2003 Oracle Corporation. All Rights Reserved. |
|