10g (9.0.4)
Part Number B12118-01
Home |
Solution Area |
Contents |
Index |
| Oracle® Internet Directory Administrator's Guide 10g (9.0.4) Part Number B12118-01 |
|
Delegation of Privileges for an Oracle Technology Deployment, 2 of 5
Oracle Identity Management enables you to store all the data for users, groups, and services in one repository, and to delegate a particular administrator for each set of data. By providing both a centralized repository and customized delegated access, Oracle Identity Management is both secure and scalable.
This section contains these topics:
Using the delegation model, a global administrator can delegate to realm administrators the privileges to create and manage the identity management realms for hosted companies. Realm administrators can, in turn, delegate to end users and groups the privileges to change their application passwords, personal data, and preferences. Each type of user can thus be given the appropriate level of privileges.
To delegate the necessary privileges, you assign the user to the appropriate administrative group. For example, suppose that you store data for both enterprise users and the e-mail service in the directory, and need to specify a unique administrator for each set of data. To specify a user as the administrator of enterprise users, you assign that user to, say, the Enterprise User Administrators Group. To specify a user as the administrator of the e-mail services, you assign that user to, say, the E-mail Service Administrators Group.
Figure 17-1 shows the flow of delegation in an Oracle Application Server environment.
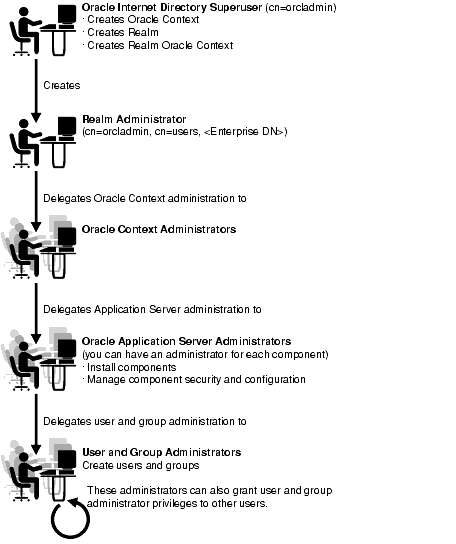
As Figure 17-1 shows, in an Oracle Application Server environment the directory super user creates:
The realm administrator, in turn, delegates administration of the Oracle Context to specific users by assigning those users to the Oracle Context Administrators Group. Oracle Context Administrators then delegate administration of the Oracle Application Server to one or more users by assigning them to the Oracle Application Server Administrators Group. These administrators install and administer Oracle Application Server components and delegate administration of user and group data to other administrators. The latter can, in turn, delegate others to administer user and group data.
When you first install Oracle Internet Directory, the default configuration establishes access control policies at various points in the directory information tree (DIT). Default access controls are placed on the User and Group containers as described later in this chapter. Likewise, default privileges for specific directory entities are discussed later in this chapter. In addition, certain default privileges are granted to everyone and to each user as described in Table 17-1.
You can customize this default configuration to meet the security requirements of your enterprise.
Administering the Oracle technology stack requires the privileges described in Table 17-2.
| Required Privileges | Description | More Information |
|---|---|---|
|
User and group management privileges |
These are delegated to either Oracle components that use the identity management infrastructure or to end users themselves |
|
|
Deployment-time privileges |
These are required to deploy any Oracle component. They may include privileges to create appropriate entries inside the directory, or to store metadata in a common repository. Such privileges need to be given, for example, to an administrator of OracleAS Portal. |
"Delegation of Privileges for Deployment of Oracle Components" |
|
Runtime privileges |
These are required to facilitate the runtime interactions of Oracle components within the identity management infrastructure. These include privileges to view user attributes, add new users, and modify the group membership. Such privileges need to be given to the administration tool specific to each Oracle component, enabling it to access or create entries inside Oracle Internet Directory. |
|
See Also:
"Migrating an Existing Directory into the Default Directory Structure" if you have an existing directory structure that you now want to migrate to an Oracle Application Server environment |
|
|
 Copyright © 1999, 2003 Oracle Corporation. All Rights Reserved. |
|