10g (9.0.4)
Part Number B12118-01
Home |
Solution Area |
Contents |
Index |
| Oracle® Internet Directory Administrator's Guide 10g (9.0.4) Part Number B12118-01 |
|
Directory Storage of Password Verifiers, 4 of 4
Oracle components store both passwords and password verifiers in Oracle Internet Directory. This section contains these topics:
Oracle components can store their password values in Oracle Internet Directory as password verifiers. A password verifier is a hashed version of a clear text password, which is then encoded as a BASE64 encoded string.
You can choose one of these hashing algorithms to derive a password verifier:
username@realm.
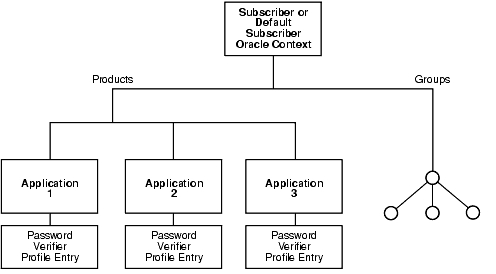
During Oracle application installation, the Oracle Universal Installer creates for that application a password verifier profile entry containing all the necessary password verification information. It places this entry as shown in Figure 16-1: immediately below the application entry, which resides under the products entry, which, in turn, resides under the realm-specific Oracle Context.
This verifier profile entry is applicable to users in the specified realm only. For verifier generation to take effect, you must set the orclcommonusersearchbase attribute in the common entry of the realm-specific Oracle context to the appropriate value.
Both the directory and Oracle components store the user password in the user entry, but in different attributes. Whereas the directory stores user passwords in the userPassword attribute, Oracle components store user password verifiers in the authPassword, orclPasswordVerifier, or orclpassword attribute. Table 16-1 describes each of the attributes used by Oracle components.
Each of these attribute types has appID as an attribute subtype. This attribute subtype uniquely identifies a particular application. For example, the appID can be the ORCLGUID of the application entry. This attribute subtype is generated during application installation.
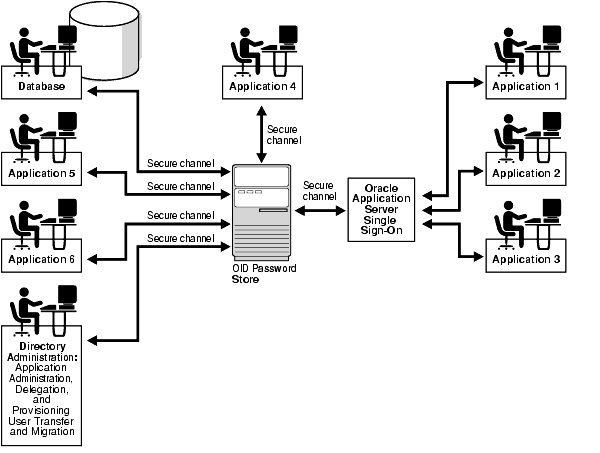
In Figure 16-2, various Oracle components store their password verifiers in Oracle Internet Directory. Oracle Application Server Single Sign-On uses the same password as that for the directory, and hence stores it in the authPassword attribute.The other applications use different passwords and hence store their verifiers in orclPasswordVerifier attribute.
The following is an example of an application verifier profile:
dn: cn=IFSVerifierProfileEntry,cn=IFS,cn=Products,cn=OracleContext,o=Oracle,dc=com objectclass:top objectclass:orclpwdverifierprofile cn:IFSVerifierProfileEntry orclappid:8FF2DFD8203519C0E034080020C34C50 orclpwdverifierparams;authpassword: crypto:SASL/MDS $ realm:dc=com orclpwdverifierparams;orclpasswordverifier: crypto:ORCLLM orclpwdverifierparams;authpassword: crypto:ORCLWEBDAV $ realm:dc=com$ usernameattribute: mail $ usernamecase: lower $ nodomain: TRUE
SASL/MD5 and ORCLWEBDAV verifiers are generated by using user name, realm, and password. The user name attribute to be used can be specified in the verifier profile entry. The case of the user name can also be specified as either upper or lower. The ORLWEBDAV verifier is generated by appending the name of the identity management realm to the user name. If this is not required, then the verifier profile entry must specify nodomain: TRUE.
In the previous example, ORCLWEBDAV verifier is generated by using the value of the mail attribute without appending the name of the realm. Also, the user name is converted to lower case before generating the verifier.
To save you from having to create a profile for each Oracle component, and to enable sharing of password verifiers across all components, Oracle Internet Directory provides a default set of password verifiers. The default verifier types are MD5, MD5-IFS (SASL/MD5 with the user name set to the value of the nickname attribute and realm = Authorized_Users), WEBDAV, ORCLLM, and ORCLNT.
Two profile entries are required: one for applications using personal identification numbers (PINs), which use numeric values only, and another for applications using alphanumeric passwords.
The verifiers for PIN-based applications--for example, the voice mail application in Oracle9iAS Unified Messaging--are stored in the orclpasswordverifier attribute. The verifiers for alphanumeric password-based applications--for example, Oracle Internet File System--can be stored in either:
authpassword attribute--If an application requires its verifier to be synchronized with the userpassword attribute
orclpasswordverifier attribute--If synchronization with the userpassword attribute is not required
These profile entries also contain the list of subscribed applications and these are specified as values in the uniquemember attribute in the profile entries. By default, the DN of the Oracle Application Server Single Sign-On identity is one of the subscribed applications. This means that Oracle Application Server Single Sign-On is a proxy member for all its partner applications. All applications not based on Oracle Application Server Single Sign-On must add their identities (DNs) to the uniquemember attribute in the appropriate profile entry.
The following is an example of the profile entries.
Cn=defaultSharedPwdProfileEntry, cn=common, cn=products, cn=oraclecontext Objectclass: orclpwdverifierprofile Cn: orclcommonpwdprofileentry Orclappid: orclcommonpwd Orclpwdverifierparams;authpassword: crypto:SASL/MD5 $ realm:Authorized_Users Orclpwdverifierparams;authpassword: crypto:ORCLWEBDAV $ realm:Authorized_Users Orclpwdverifierparams;authpassword: crypto:ORCLLM Orclpwdverifierparams;authpassword: crypto:ORCLNT Orclpwdverifierparams;orclpasswordverifier: crypto:SSHA Uniquemember: cn=SSO,cn=Products,cn=OracleContext Uniquemember: cn=IFS,cn=Products,cn=OracleContext Cn=defaultSharedPINProfileEntry, cn=common, cn=products, cn=oraclecontext Objectclass: orclpwdverifierprofile Cn: orclcommonpinprofileentry Orclappid: orclcommonpin Orclpwdverifierparams;orclpasswordverifier: crypto:MD5 Orclpwdverifierparams;orclpasswordverifier: crypto:SSHA Uniquemember: cn=SSO,cn=Products,cn=OracleContext Uniquemember: cn=Unified Messaging,cn=Products,cn=OracleContext
For PIN-based applications, authpassword is not an option. Such applications use the orclpasswordverifier attribute.
Figure 16-3 shows an example of password verification for an Oracle component. In this example, the Oracle component stores its password verifiers in the directory.
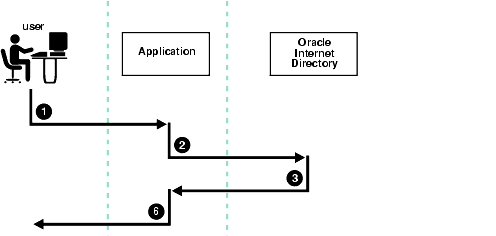
appID as the subtype of the verifier attribute. For example:
ldapcompare -p389 -D "DN_of_the_appplication_entity" -w "password" -b "DN_of_the_user" -a orclpasswordverifier; appID -v password_of_the_user
If an application does not use the compare operation, then it:
You can use Oracle Directory Manager to view and modify password verifier profile entries.
To view an application's password verifiers:
You can view and modify password verifier profiles by using command-line tools.
To view an application's password verifier, perform a search specifying the DN of the password verifier profile.
This example changes the hashing algorithm in an application password verifier profile entry. This password verifier synchronizes with the user's directory password.
ldapmodify -p 389 -h my_host -v <<EOF dn: cn=MyAppVerifierProfileEntry,cn=MyApp,cn=Products,cn=OracleContext,o=my_ company,dc=com changetype: modify replace: orclPwdVerifierParams orclPwdVerifierParams;authPassword: crypto:SASL/MD5 $ realm:dc=com EOF
|
|
 Copyright © 1999, 2003 Oracle Corporation. All Rights Reserved. |
|