10g (9.0.4)
Part Number B12118-01
Home |
Solution Area |
Contents |
Index |
| Oracle® Internet Directory Administrator's Guide 10g (9.0.4) Part Number B12118-01 |
|
Directory Security Concepts, 5 of 8
Authentication is the process by which the directory server establishes the true identity of the user connecting to the directory. It occurs when an LDAP session is established by means of the ldapbind operation. Thus every session has an associated user identity.
To verify the identities of users, hosts, and clients, Oracle Internet Directory enables three general kinds of authentication, and these are described in these topics:
This section describes the three kinds of authentication available within Oracle Internet Directory, and about how SASL-enabled clients authenticate to a directory server.
There are three direct authentication options:
When users authenticate anonymously, they simply leave the user name and password fields blank when they log in. Each anonymous user then exercises whatever privileges are specified for anonymous users.
When using simple authentication, the client identifies itself to the server by means of a DN and a password that are not encrypted when sent over the network.
This is a method for adding authentication support to connection-based protocols. To use SASL, a protocol includes a command for identifying and authenticating a user to a server and for optionally negotiating protection of subsequent protocol interactions. If the use of SASL is successfully negotiated, then a security layer is inserted between the protocol and the connection.
Oracle Internet Directory supports two authentication mechanisms with SASL:
See Also:
Indirect authentication occurs through any entity that has credentials in the directory--for example, an application such as the Oracle Internet Directory Self-Service Console, or a middle tier such as a firewall or a RADIUS server. The application or middle tier becomes a proxy user. A proxy user has the privilege to impersonate an end user, performing on that user's behalf those operations for which that user has privileges.
Figure 12-1 and the accompanying text explain how indirect authentication takes place.
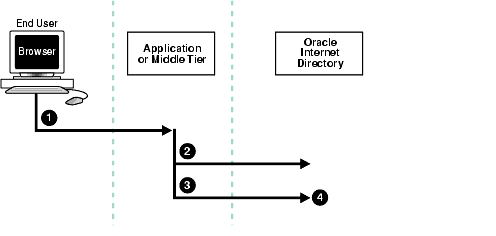
Indirect authentication takes place as follows:
The directory server can, in the same session, authenticate and authorize other end users. It can also switch the session from the end user to the application or middle tier that opened the session.
To close the session, the application or middle tier sends an unbind request to the directory server.
For example, suppose you have:
cn=User1, which has proxy access on the entire directory
cn=User2
When this end user sends to the application or middle tier a request containing a query to the directory, the application or middle tier authenticates the end user. The middle tier service then binds to the directory by using its own identity, cn=User1, then performs a second bind, this time by using only the DN of the end user, cn=User2. The Oracle directory server recognizes this second bind as an attempt by the proxy user to impersonate the end user. After the directory server verifies that cn=user1 has proxy access, it allows this second bind to succeed. It does not require any further validation of the end-user DN, such as a password. For the rest of the session, all LDAP operations are access-controlled as if cn=User2 were performing them.
If one user is being serviced by an application, and another user subsequently requests a service of that same application, then the application can establish a new connection and proceed as previously described without disrupting that prior session. If, however, no prior user is still being serviced, then the existing established connection can be re-used again and again without the need for a new connection.
Perhaps your enterprise stores user security credentials in a repository other than Oracle Internet Directory--for example, a database or another LDAP directory. With Oracle Internet Directory external authentication and password modification plug-ins, you can use these credentials for user authentication to Oracle components. You do not need to store the credentials in Oracle Internet Directory and then worry about keeping them synchronized.
|
|
 Copyright © 1999, 2003 Oracle Corporation. All Rights Reserved. |
|