10g (9.0.4)
Part Number Part No. B10325-02
Home |
Solution Area |
Contents |
Index |
| OracleŽ Application Server Containers for J2EE Security Guide 10g (9.0.4) Part Number Part No. B10325-02 |
|
This chapter describes security issues affecting J2EE applications in Oracle Application Server Containers for J2EE (Oracle Application Server Containers for J2EE).
This chapter contains these topics:
When the JAAS Provider is integrated with applications developed for the Java 2 Platform, the following Oracle components are available to developers:
RealmLoginModule
See Also:
The JAAS Provider is designed to work with the J2EE declarative security model. This declarative model requires little or no programming to use JAAS security in your application. Instead, most security decisions are made as part of the deployment process, making it easy to make changes without requiring re-coding. If the declarative model is not sufficient, the JAAS Provider also supports programmatic security in the same manner that JAAS is used in any J2SE environment.
If your application relies on the declarative security model (where J2EE security roles are defined in deployment descriptors, such as web.xml), the developer must determine if the application uses application-specific roles. If so, the developer must define these roles so that they can be mapped to the J2EE logical roles during the deployment phase.
If your application uses JAAS programmatically, then the developer must create a JAAS LoginContext and explicitly call the login() method to invoke a JAAS LoginModule.
Using the declarative security model, the deployer must make the following security-related decisions:
hr_manager is running the application; the deployer must define that role.
JAZNUserManager). For example, the J2EE logical role called hr_manager may be mapped to a given set of users defined by the OC4J user manager.
For information on making and implementing these decisions, see Chapter 3, "Configuring And Deploying the JAAS Provider"; for a full discussion of deployment, see the Oracle Application Server Containers for J2EE User's Guide.
Oracle Application Server Containers for J2EE is a J2EE container that accepts HTTP and RMI client connections. These connections permit access to servlets, Java Server Pages (JSPs), and Enterprise JavaBeans (EJBs).
J2EE containers separate business logic from resource and lifecycle management. This enables developers to focus on writing business logic, rather than writing enterprise infrastructure. For example, Java servlets simplify Web development by providing an infrastructure for component, communication, and session management in a Web container integrated with a Web server.
The JAAS Provider is integrated with Oracle Application Server Containers for J2EE to enhance application security. This integration provides the following benefits:
run-as identity support, delegation support (from servlet to Enterprise JavaBeans)
Another key component of JAAS integration in the J2EE environment is JAZNUserManager. JAZNUserManager is an implementation of the Oracle Application Server Containers for J2EE UserManager interface.
The OC4J principals.xml file is less secure and less flexible than authentication with JAZNUserManager. JAZNUserManager provides the following:
We strongly encourage you to migrate your existing applications from using
Note::
principals.xml to using JAZNUserManager. For instructions, see "Migrating Principals from the principals.xml File (XML-based Provider Only)".
In addition to the features mentioned in "Replacing principals.xml", JAZNUserManager provides many other features, including:
RealmLoginModule integration in non-SSO environments
The JAAS Provider integrates with three different login authentication environments in a J2EE application.
The following sections discuss how the JAAS Provider integrates with each of these authentication types.
SSO lets a user access multiple accounts and applications with a single set of login credentials. Figure 6-1 shows JAAS integration in an application running in an SSO-enabled J2EE environment.
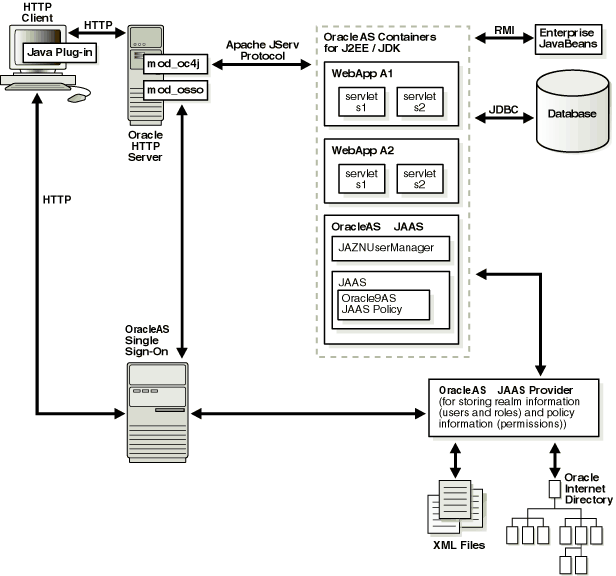
This section describes the responsibilities of Oracle components when an HTTP client request is initiated in an SSO-enabled J2EE environment.
runas-mode in the <jazn-web-app> element.
If the runas-mode is set to false, then the following happens:
If the runas-mode is set to true, then the following happens:
PrivilegedAction block through Subject.doAs(). The JAZNUserManager enforces security constraints.
Subject.doAs() is called, JAAS consults the JAAS Provider for permissions associated with the SSO user through the getPermissions() method.
AccessControlContext based on the permissions returned from getPermissions().
AccessControlContext of the SSO user.
SecurityManager.checkPermission().
SecurityManager.checkPermission() returns safely and the client HTTP request proceeds.
SSL is an industry standard protocol for managing the security of message transmission on the Internet. Figure 6-2 shows JAAS integration in an application running in an SSL-enabled J2EE environment.
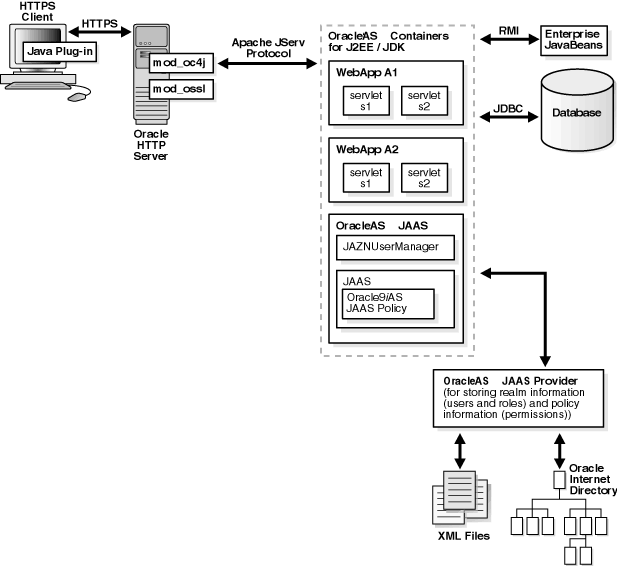
This section describes the responsibilities of Oracle components when an HTTP client request is initiated in an SSL-enabled J2EE environment. In this environment, OracleAS Single Sign-On is not used. A login module (for example, RealmLoginModule) is used.
runas-mode specified in the <jazn-web-app> element.
If runas-mode is set to false, then the target servlet is invoked.
If runas-mode is set to true, then the following happens:
PrivilegedAction block through Subject.doAs(). The JAZNUserManager enforces security constraints.
Subject.doAs() is called, the method consults for permissions associated with the SSL user through the getPermissions() method.
AccessControlContext based on the permissions returned from getPermissions().
AccessControlContext of the SSL user.
SecurityManager.checkPermission().
SecurityManager.checkPermission() returns safely and the client HTTP request proceeds.
Basic authentication bypasses OracleAS Single Sign-On. Figure 6-3 shows specific JAAS integration in an application configured for Basic authentication in a J2EE environment.
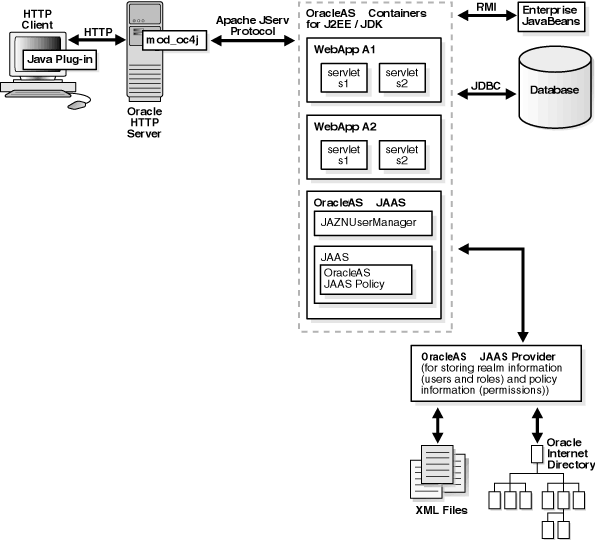
This section describes the responsibilities of Oracle components when an HTTP client request is initiated in a J2EE environment configured for Basic authentication. In this environment, OracleAS Single Sign-On is not used. A login module (for example, RealmLoginModule) is used.
runas-mode in the jazn-web-app element.
If the runas-mode is set to false, then the following happens:
If the runas-mode is set to true, then the following happens:
service() method within a PrivilegedAction block through Subject.doAs(). The JAZNUserManager enforces security constraints.
Subject.doAs() is called, JAAS consults the JAAS Provider for permissions associated with the SSO user through the getPermissions() method.
AccessControlContext based on the permissions returned from getPermissions().
AccessControlContext of the user.
SecurityManager.checkPermission().
SecurityManager.checkPermission() returns safely and the client HTTP request proceeds.
Two distinct role types are available to application developers creating JAAS-integrated applications in J2EE environments: J2EE roles and JAAS roles. When these role types are mapped together using Oracle Application Server Containers for J2EE group mappings, users can access an application with a defined set of role permissions for as long as the user is mapped to this role.
This section describes these role types and how which they are mapped together.
The J2EE development environment includes a portable security roles feature defined in the web.xml file for servlets and Java Server Pages (JSPs). Security roles define a set of resource access permissions for an application. Associating a principal (in this case, a JAAS user or role) with a security role assigns the defined access permissions to that principal for as long as they are mapped to the role. For example, an application defines a security role called sr_developer:
<security-role> <role-name>sr_developer</role-name> </security-role>
You also define the access permissions for the sr_developer role.
<security-constraint> <web-resource-collection> <web-resource-name>access to the entire application</web-resource-name> <url-pattern>/*</url-pattern> </web-resource-collection> <!-- authorization --> <auth-constraint> <role-name>sr_developer</role-name> </auth-constraint> </security-constraint>
JAAS roles and users are defined depending on the provider type, LDAP-based or XML-based.
For example, with the XML-based provider type, developer is listed as a role element in the jazn-data.xml file:
<role> <name>developer</name> <members> <member> <type>user<type> <name>john<name> </member> </members> </role>
Oracle Application Server Containers for J2EE enables you to map portable J2EE security roles defined in the J2EE web.xml file to groups in an orion-application.xml file.
The roles and users defined in your provider environment are mapped to the Oracle Application Server Containers for J2EE developer group role in the orion-application.xml file.
For example, the sr_developer security role is mapped to the group named developer.
<security-role-mapping name="sr_developer"> <group name="developer" /> </security-role-mapping>
Notice that a <group> in a <security-role-mapping> element corresponds to a role in the JAAS provider. Therefore, this association permits the developer group to access the resources allowed for the sr_developer security role.
In this paradigm, the user john is listed as a member of the developer role. Because the developer group is mapped to the J2EE security role sr_developer in the orion-application.xml file, john has access to the application resources defined by the sr_developer role.
Authentication is the process of verifying the identity of a user in a computing system, often as a prerequisite to granting access to resources in a system. User authentication in the J2EE environment is performed by the following:
RealmLoginModule or other login module (for non-SSO environments)
Before HTTP requests can be dispatched to the target servlet, the JAZNUserManager gets the authenticated user information (set by mod_osso) from the HTTP request object and sets the JAAS subject in Oracle Application Server Containers for J2EE.
You can choose to configure the JAZNUserManager so that a filter enables the target servlet to run with the permissions and roles associated with an authenticated identity or run-as identity. To do this, configure the jazn-web-app element.
|
See Also:
"JAZNUserManager" for further information on options and configuration of the |
The following javax.servlet.HttpServletRequest APIs retrieve authentication information within the servlet:
getRemoteUser for the authenticated username
getAuthType for the authentication scheme
getUserPrincipal for the authenticated principal object
getAttribute("java.security.cert.X509certificate") for the SSL client certificate
Authorization begins with a call to Subject.doAs().
Authorization is the process of granting the permissions and privileges entitled to the user. This section discusses authentication within servlets.
If the servlet is configured to permit doAs(), the JAZNUserManager invokes an authenticated target servlet within a Subject.doAs() block to enable JAAS-based authorization in the target servlets.
Authorization is achieved through the following:
|
|
 Copyright © 1996, 2003 Oracle Corporation. All Rights Reserved. |
|