10g (9.0.4)
Part Number B10381-01
Home |
Solution Area |
Contents |
Index |
| Oracle HTTP Server Administrator's Guide 10g (9.0.4) Part Number B10381-01 |
|
This appendix explains how to use Oracle Application Server SSO Plug-in to protect third-party HTTP listener and its applications. The Oracle Application Server SSO Plug-in works with the Sun ONE Web Server Enterprise Edition, version 4.1 and 6.0, on UNIX and Windows NT systems, and the Microsoft Internet Information Server (IIS), version 4.0 or 5.0, on Windows systems.
Topics discussed are:
Oracle Application Server SSO Plug-in is Oracle's single sign-on (SSO) solution for third-party listeners such as Sun ONE and IIS. The plug-in is designed to protect native third-party listener applications using the SSO infrastructure. With the help of the Oracle Application Server SSO Plug-in, you can be authenticated to different third-party listener applications using only one SSO password. You can integrate these SSO-protected third-party listener applications with SSO enabled Oracle HTTP Server applications or legacy Oracle SSO enabled application together as long as they are all protected on the same SSO server.
Oracle Application Server SSO Plug-in is a simple version of mod_osso, and only implements some of its basic functionality. Features such as dynamic authentication, global logout, idle timeout and global timeout, and basic authentication for legacy application are not implemented in the current Oracle Application Server SSO Plug-in release.
Figure B-1 illustrates the process involved when you request a URL protected by the Oracle Application Server SSO Plug-in.
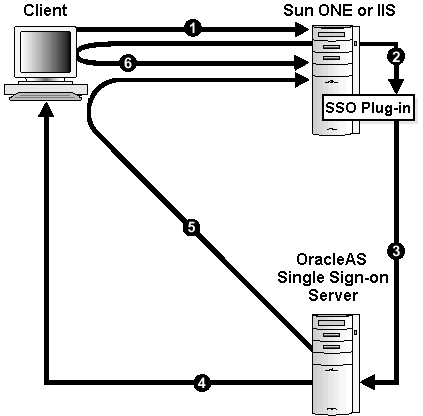
During the same session, if the user again seeks access to the same or to a different application, the user is not prompted for a user name and password; the application uses an HTTP header to obtain this information from the Oracle Application Server SSO Plug-in session cookie.
The plug-in is distributed on the OracleAS Repository Creation Assistant/Utilities CD, which is included in your Oracle Application Server CD Pack.
Install Oracle Application Server SSO Plug-in on a machine that has an Oracle Application Server installation. This installation is required only for the network and security dependent libraries and single sign-on registration tool; it is not required to be running. After the Oracle Application Server installation on UNIX systems, add ORACLE_HOME/lib to the LD_LIBRARY_PATH in the listener's start script. For example, the "start" script in Sun ONE. On Windows systems, the installation automatically sets the environment variable PATH. For example, ORACLE_HOME\bin.
Download, or copy, the required plug-in, and place the configuration file and shared libraries in directories that the third-party listener can access. For security reasons, ensure that all the configuration files and plug-in modules are given minimum privileges.
The plug-in consists of a single shared library, oracle_proxy.so on UNIX and oracle_proxy_nes.dll on Windows. To install the plug-in into the listener, place the library in a directory to which the listener has read and execute privileges.
The plug-in consists of a single .dll, oracle_proxy.dll. To install this plug-in, copy the .dll to a directory the listener can access.
The single sign-on registration process enables the single sign-on server and the listener to share information such as server location, protocol version, and common encryption key, before they communicate. After the registration process, this information is stored on the single sign-on server side as a single sign-on partner application entry. On the listener side, a single sign-on file called sso_conf is created. sso_conf is obfuscated for security purposes. Copy it to an appropriate location so that the listener can access it.
Oracle provides a Java-based single sign-on registration tool to automatically complete this process.
Register the third-party listener with a single sign-on server using the following command:
ORACLE_HOME/jdk/bin/java -jar ORACLE_HOME/sso/lib/ossoreg.jar [arguments]
where ORACLE_HOME is the home directory of your Oracle Application Server installation.
A different version ossoreg.jar could have very different command arguments. If needed, run the above command using "-help" first to get the complete usage information.
Table B-1 lists some important common arguments for the single sign-on registrar.
On UNIX:
ORACLE_HOME/jdk/bin/java -jar ORACLE_HOME/sso/lib/ossoreg.jar \ -ssoDBConnect <host.domain>:1521:iasdb -pass your_password \ -oracle_home_path ORACLE_HOME -site_name <host.domain>:7778 \ -config_mod_osso TRUE -mod_osso_url http://<host.domain>:7778 \ -u nobody -admin_id admin_name -admin_info admin@company.com \ -sso_partner_version v1.2 \ -virtualhost \ -config_file ORACLE_HOME/Apache/Apache/conf/osso/sso_conf
On Windows NT:
ORACLE_HOME/jdk/bin/java -jarORACLE_HOME/sso/lib/ossoreg.jar \-ssoDBConnect<host.domain>:1521:iasdb -passyour_password\-oracle_home_pathORACLE_HOME-site_name<host.domain>:8080 \ -config_mod_osso TRUE -mod_osso_url http://<host.domain>:8080 \ -u SYSTEM -admin_id admin_name -admin_info admin@company.com \ -sso_partner_version v1.2 \ -virtualhost \ -config_file ORACLE_HOME/Apache/Apache/conf/osso/sso_conf
Create a plug-in configuration file such as osso_plugin.conf. This is the file where you define all the plug-in functionality. It can also be referred as the osso property file. The syntax is exactly the same for all third-party listeners. This file must reside in a directory that is readable by the third-party listener. This file also contains the following:
LoginServerFile and IpCheck
Table B-2 lists the configuration directives for the SSO plug-in:
Use the following format to protect resources:
<OSSO url-matching-rule> SSO_configuration_directives </OSSO>
Use the following rules to define the url-matching-rule:
When multiple rules apply to the same URL, the following precedence applies:
Some examples of the precedence are:
/foo/bar/index.html would take precedence over /foo/bar/* /foo/bar/*.jsp would take precedence over /foo/bar/* /foo/bar/* would take precedence over /foo/*Example B-2 Simple Single Sign-on Configuration File, osso_plugin.conf
LoginServerFile=/path/sso_conf <OSSO /private/hello.html> IpCheck = false </OSSO> <OSSO /private1/*> </OSSO> <OSSO /private2/*.jsp> IpCheck = true </OSSO>
This section provides SSO plug-in configuration instructions for the Sun ONE Enterprise Server listener on UNIX and Windows NT systems.
|
Note: If you are configuring the Sun ONE listener on Windows NT, use forward slashes (/) in all paths. |
magnus.conf file, version 6, or obj.conf, version 4, in the Sun ONE listener /config directory.
On UNIX:
Init fn="load-modules" shlib="/path/oracle_proxy.so" funcs=osso_ init,oracle_single_sign_on,osso_redirect_service,osso_success_service"
On Windows NT:
Init fn="load-modules" shlib="/path/oracle_proxy_nes.dll" funcs=osso_ init,oracle_single_sign_on,osso_redirect_service,osso_success_service"
where /path/ is the path to the shared library for the plug-in. This line tells the listener where the proxy shared library is, and which functions are exposed by this library.
Init fn="osso_init" osso_properties="/path/osso_plugin.conf" log_ file="/path/plugin.log" log_level=error
where /path/osso_plugin.conf is the exact location of the plug-in configuration file you just created. Also this line can specify a log file and log level to log messages from the plug-in (optional).
<Object name=default> section of the obj.conf file, before all other lines:
AuthTrans fn="oracle_single_sign_on"
<Object name=default> section before all other lines that begin with the word Service:
Service type="oracle/sso_redirect" fn="osso_redirect_service"
/path/ is the path of your document root. For example: /home/Sun ONE/docs/ or $docroot.
<Object ppath="/path/osso_login_success"> Service fn="osso_success_service" </Object>
LD_LIBRARY_PATH variable in your start script to include the location of ORACLE_HOME/lib, where ORACLE_HOME is the Oracle Application Server installation home directory.
For version 6.0, the same shared library can be used as with version 4.1. The configuration is virtually the same, but the configuration files for Sun ONE have changed slightly in version 6.0. In this version, the two lines beginning with Init that need to be added must be added at the end of the magnus.conf file rather than to the obj.conf file. The other two lines that should be added to obj.conf remain the same.
This section provides instructions on configuring the IIS Listener to use the SSO plug-in. The plug-in consists of a single .dll, oracle_osso.dll. To install the plug-in, copy the .dll to the host on which IIS resides and perform the following steps:
HKEY_LOCAL_MACHINE\SOFTWARE\Oracle\IIS OSSO Adapter.
d:\osso\osso_plugin.conf, by adding this string value with the name cfg_file and a value pointing to the location of your configuration file.
log_file and log_level. This is optional.
oracle_osso.dll. Name the directory osso and give it execute access.
oracle_osso.dll as a filter in your IIS Web site. The name of the filter should be osso and its executable must point to the directory containing oracle_osso.dll.For example, d:\osso\oracle_osso.dll.
This section describes common problems and possible reasons.
SSO plug-in could not find the libraries it needs. Possible reason would be that you do not have ORACLE_HOME/lib included in your LD_LIBRARY_PATH on UNIX. On Windows, you do not have ORACLE_HOME/bin included in your PATH.
Single sign-on server configuration file, for example, sso_conf, is obfuscated using a certain account and this account has to be the one being used to start your listener. For example, use the value of User specified in magnus.conf for Sun ONE and usually SYSTEM for IIS.
Oracle Application Server SSO Plug-in is not designed to work in concert with other authentication modules. It is either a native listener authentication module, or third-party module.
|
|
 Copyright © 2002, 2003 Oracle Corporation. All Rights Reserved. |
|