| Oracle® Collaboration Suite Administrator's Guide 10g Release 1 (10.1.1) for Windows or UNIX Part Number B14476-03 |
|
|
View PDF |
| Oracle® Collaboration Suite Administrator's Guide 10g Release 1 (10.1.1) for Windows or UNIX Part Number B14476-03 |
|
|
View PDF |
Oracle Collaboration Suite includes an integrated console interface for all tasks involving user account management. The console interface is fully integrated with Oracle Delegated Administration Services, a component of Oracle Identity Management. Oracle Delegated Administration Services, in turn, stores user and group information in the Oracle Internet Directory database.
Whenever a user logs in to the console, they will see one of two possible interfaces, depending on their user credentials. End-users with normal permissions will see the Oracle Internet Directory Self-Service Console, a ready-to-use application designed to allow users to edit their personal information, change or reset their password, and other basic user management tasks.
When an administrator (a user with the 'allow application provisioning' privilege set) logs in to the console, they will see the Oracle Internet Directory Provisioning Console, a ready-to-use application designed to allow administrators to create user accounts, create groups, manage existing users and groups, set defaults for various user attributes, enable and disable accounts, and manage identity management realms.
This chapter contains the following topics:
Introduction to the Oracle Internet Directory Provisioning Console
Configuring User Account Creation Using the Provisioning Console
Managing Identity Management Realms Using the Provisioning Console
The system that stores and manages user accounts and group definitions is Oracle Identity Management. Oracle Identity Management is a component of Oracle Application Server 10g. The primary tool for creating user accounts in Oracle Identity Management is the Oracle Internet Directory Provisioning Console. The Provisioning Console is a tool which interfaces with Oracle Delegated Administration Services, a component of Oracle Identity Management. Oracle Delegated Administration Services, in turn, stores user and group information in the Oracle Internet Directory database.
Oracle Delegated Administration Services is a component of Oracle Identity Management. It is a set of service units that enable directory administrators to delegate responsibilities to lower administrators or to end users.
The Oracle Internet Directory Provisioning Console is a tool that is built using Oracle Delegated Administration Services units. The Oracle Delegated Administration Services units are like building blocks. The Provisioning Console is a particular tool built using those units. It comes prepackaged, but you can, if you wish, build your own tool using the same Oracle Delegated Administration Services units out of which the Provisioning Console is built.
See Also:
For information about building provisioning interfaces using Oracle Delegated Administration Services, see: Oracle Identity Management Application Developer's GuideProvisioning
Use the Provisioning Console to create one user account at a time, or to bulk-provision large numbers of users at once. Generally by importing or entering the appropriate information, user accounts in Oracle Internet Directory allow access to some or all of the Oracle Collaboration Suite components that you have deployed. When a user account is created, it will be provisioned for each Oracle Collaboration Suite component according to the provisioning policies you set. By default, each new user is provisioned for all available applications.
The privilege to create or import users, and set Oracle Collaboration Suite application provisioning policies, can be delegated. You or your delegated administrators control all user and group permissions for Oracle Collaboration Suite.
Policies
During installation and configuration of Oracle Collaboration Suite, each application in the suite registers with Oracle Identity Management, and creates a provisioning profile for itself. The provisioning profile contains all the configuration information concerning the specific application. Once the provisioning registration is completed successfully, the application becomes a provisionable target.
When they register with Oracle Internet Directory, each application that is installed uploads configuration data into the central directory by instantiating template files. The template files are written to Oracle Internet Directory using standard LDIF files, and also by using the provisioning registration tool (ORACLE_HOME/bin/oidprovtool).
When you create, modify, or delete user accounts and groups, the Provisioning Console follows the provisioning policy and displays the set of user account fields appropriate for each installed Oracle Collaboration Suite component.
Apart from specifying the default provisioning policy during the initial registration, the application can also implement a policy that is triggered for every user that is created. This policy can inspect whether the user should be provisioned for the particular application or not, based on specified business requirement logic. This policy is supported in form of a plug-in that the application provides out-of -the box or which your organization can write after installation and initial configuration. The administrator always has the privilege to override a provisioning policy at the time of provisioning a user account.
For more information on managing default application provisioning attributes, see "Setting Default Provisioning Policies".
Delegating Access
The Provisioning Console also enables you to delegate administrative privileges to various administrators and to end users. It provides a single graphical interface for delegated administrators and end users to manage data in the directory. The various provisioning controls are shown or hidden based on assigned privileges. If the user logging in has the "Allow Application Provisioning" privilege, then that user will see the Provisioning Console, with the full set of user provisioning controls. If the user does not have provisioning privilege, then they will only see the Self-Service Console, which provides controls for managing their own personal information. "Allow Application Provisioning" privileges can be granted using the "Assign Privileges" functionality.
During installation, the orcladmin super-user is bootstrapped as an "Allow Application Provisioning" enabled user. You can use this account to delegate this privilege to others, as described above.
Architecture
Figure 4-1 shows how the Self-Service Console interacts with Oracle Delegated Administration Services.
Figure 4-1 Interactions of Oracle Internet Directory Self-Service Console with Oracle Delegated Administration Services
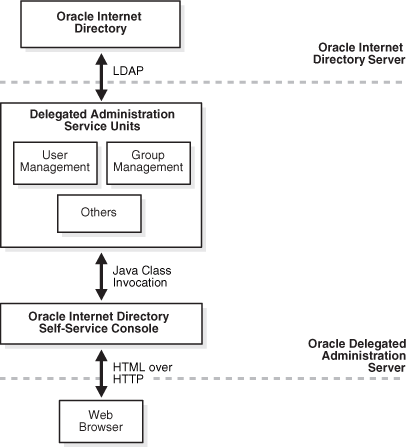
As an administrator, you can perform all of the tasks of an end user, as well as those for which you have the necessary administrative privileges.
In Oracle Collaboration Suite, the provisioning process includes the following steps, which are performed by the Provisioning Console:
Creating the user in the central directory
Enrolling the user in various applications—that is, creating application-specific user values and entitlements
Synchronizing the user information with the various applications
For example, provisioning a user to access Oracle Mail involves:
Creating the user in the central directory
Enrolling the user in Oracle Mail. This involves setting up an e-mail account, specifying the quota for that user, and creating the necessary public folders.
The user information in the central directory is kept in sync with the application user information with help of provisioning event propagation from the central directory to the various applications.
You can change information for users and groups from any of the following:
Oracle Delegated Administration Services
Oracle Human Resources or other applications integrated with Directory Integration and Provisioning
Oracle Directory Manager
Oracle Enterprise Manager tools—for example, Enterprise Security Manager
Third-party standard LDAP tools
When you create a user using the Provisioning Console, the user account is provisioned for Oracle Collaboration Suite components according to your policy. However, some Oracle Collaboration Suite components create internal user account objects which are separate from the information stored in the Oracle Internet Directory. Generally, the create is event-based, but on demand also exists in case an application was unavailable during the create process: this is called Automatic Enrollment, or "on-demand enrollment".
Automatic Enrollment
This method is sometimes called "on-demand enrollment." Instead of continuously synchronizing with the central directory, the application creates the user footprint when the user first accesses the application. Oracle Application Server Single Sign-On (SSO) uses this method to enroll a user accessing an application.
Once users have been added to Oracle Internet Directory, they can be automatically provisioned to the Calendar server. Several provisioning models are available: on-demand, bulk, and notification-Based. These three models can be customized with defined provisioning policies that help manage if users will be provisioned to calendar, and moreover, the node to which these users will be added.
For more information about provisioning users in Oracle Calendar Server, including information about provisioning models and provisioning policies, see Oracle Calendar Administrator's Guide Chapter 6, "Managing User Accounts"
After users have been created in Oracle Internet Directory, users are automatically provisioned in Oracle Content Services every 15 minutes by the Oracle Internet Directory Credential Manager Agent. This agent is specific to Oracle Content Services and can be managed from the Content Services Home page in the Oracle Collaboration Suite Control.
Additionally, once a user has been created in Oracle Internet Directory, logging in to Oracle Content Services as that user will immediately provision the user in Oracle Content Services, irrespective of the time interval specified for the Agent.
For more information about provisioning users in Oracle Content Services, including information about changing the default time period for the Oracle Internet Directory Credential Manager Agent, see "Provisioning Users in Oracle Content Services" in Chapter 1 of Oracle Content Services Administrator's Guide.
When users are created in Oracle Internet Directory using Oracle Delegated Administration Services, they can also be provisioned in Oracle Mail. Alternatively, users can be created in Oracle Internet Directory but the administrator can opt not to provision the user in Oracle Mail, in which case users can be provisioned in Oracle Mail using either the Oracle WebMail client or the oesucr command-line utility.
For more information about provisioning users in Oracle Mail, see "Managing Oracle Mail Users" in Chapter 2 and "oesucr" in Appendix D of Oracle Mail Administrator's Guide.
Once a user has been provisioned for voice or fax access through the Provisioning Console, an Oracle Voicemail & Fax plug-in automatically enables the user for voice access or fax access, or both. Users can also be provisioned individually or in bulk using the Oracle Voicemail & Fax Accounts Manager, a command-line tool.
Once an account is created, it can be managed in one of several ways, through the Provisioning Console, Grid Control, or the Voicemail & Fax Accounts Manager. Although there are some differences in the functionality of the three methods, they generally allow you to create and delete voice mail accounts, add and delete phone numbers, and manage the properties of the voice mail accounts.
See Chapter 5, "Managing Oracle Voicemail & Fax Accounts," in Oracle Voicemail & Fax Administrator's Guide for information about managing user accounts using Enterprise Manager or the Voicemail & Fax Accounts Manager.
After you have provisioned users in Oracle Internet Directory, you should assign at least one of them administrative privileges for managing Oracle Real-Time Collaboration. You do this by assigning a user the business administrator role using the rtcctl modifyRoles command. This user will have access to all of the tabs available in the Oracle Real-Time Collaboration Web Client, including the Monitor, Reports, Sites and System tabs.
You can also assign users the business monitor role (the user has access to Monitor and Reports tabs), or assign users a business monitor or business administrator role for a specific Oracle Real-Time Collaboration site.
For an overview of the tasks each user role can do, see "Oracle Real-Time Collaboration Administration Tools". See "Setting User Roles" in Chapter 4 of Oracle Real-Time Collaboration Administrator's Guide for details about how to assign user roles with modifyRoles.
This section explains how to log in to the Provisioning Console.
To log in to the Provisioning Console:
Visit the URL of the Provisioning Console. For example, if the Provisioning Console is installed on host1.acme.com and the Oracle HTTP Server is running on port 7778, then the URL to the Provisioning Console is http://host1.acme.com:7778/oiddas/
In the upper right corner, select Login. This takes you to the Single Sign-On page.
In the Single Sign-On page, in the User Name field, enter your Single Sign-On user name. For example, jdoe.
Note:
When Oracle Collaboration Suite is installed, the super-user root administrator accountorcladmin is created. You should use this account when you first log in to the Provisioning Console to create accounts. Once you have delegated user account privileges to other users, you should reserve the orcladmin account for procedures that require super-user access.In the Password field, enter your Single Sign-On password.
If you are in a hosted environment in which there are multiple realms, then the Company field appears. Otherwise, it does not appear. If the Company field appears, then enter the name of your company.
See Also:
For more information about setting up multiple realms, see "Setting Up and Enabling Multiple Realms"Select Login. The Provisioning Console is displayed (see Figure 4-2).
Figure 4-2 Oracle Internet Directory Provisioning Console
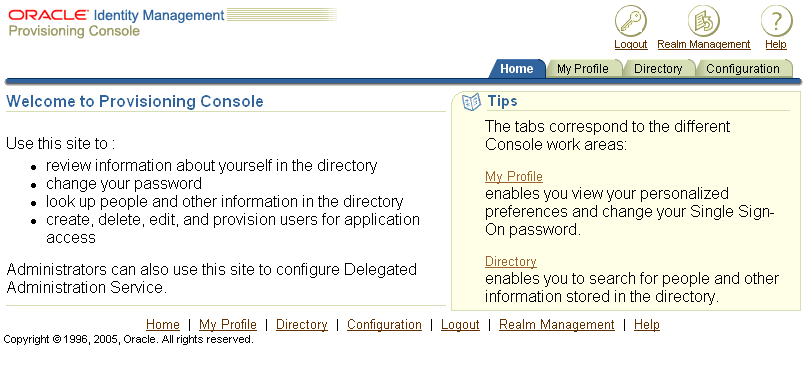
You can use the Provisioning Console to establish the ways that users create user entries. You can also use it to create, modify, and delete user entries, change user passwords and assign privileges to users.
To create a user, you must complete the following step in a multi-step wizard process:
Specify the base user information.
Select the applications for which the user should be provisioned.
Specify the application-specific user attributes.
Verify all the entered information in the previous screens.
Submit the information for user creation and provisioning of the Oracle Collaboration Suite applications.
When you submit the user information in step 5, the Provisioning Console requests the provisioning of the user for the various Oracle Collaboration Suite applications. Some of the Oracle Collaboration Suite applications have application-specific user attributes that the application registered as provisioning configuration during the Oracle Collaboration Suite installation. The Provisioning Console exposes these attributes in step 3 with their default values, which you may then alter as appropriate.
When provisioning users for Oracle Collaboration Suite, for each deployed Oracle Collaboration Suite component, you must either enter a minimum amount of information for that user to be provisioned, or, disable provisioning of that user for that component in step 2. The Provisioning Console exposes all user provisioning fields for each deployed component in step 3. For a listing and description of the fields exposed by default for each Oracle Collaboration Suite component, see "Oracle Collaboration Suite Application-Specific User Attributes". Aside from those listed in the tables, other Oracle Collaboration Suite applications do not require any additional fields for user creation.
This section contains the following topics:
Select the Directory tab, then select Users.
Choose Create to display the Create User: General window (Figure 4-3).
Figure 4-3 Provisioning Console Create User: General Window
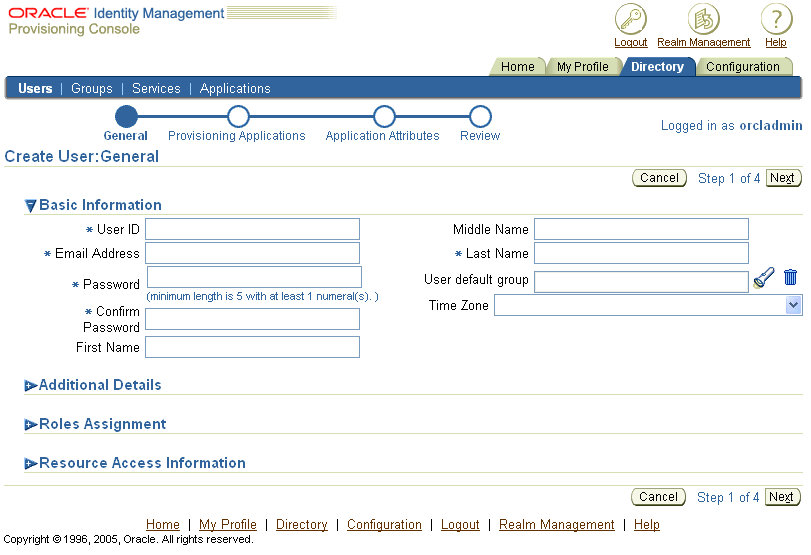
In the Create User: General window, enter the appropriate information. Fields designated with an asterisk (*) are mandatory.
Select Next to display the Create User: Application Provisioning window (Figure 4-4).
Figure 4-4 Provisioning Console Create User: Application Provisioning Window
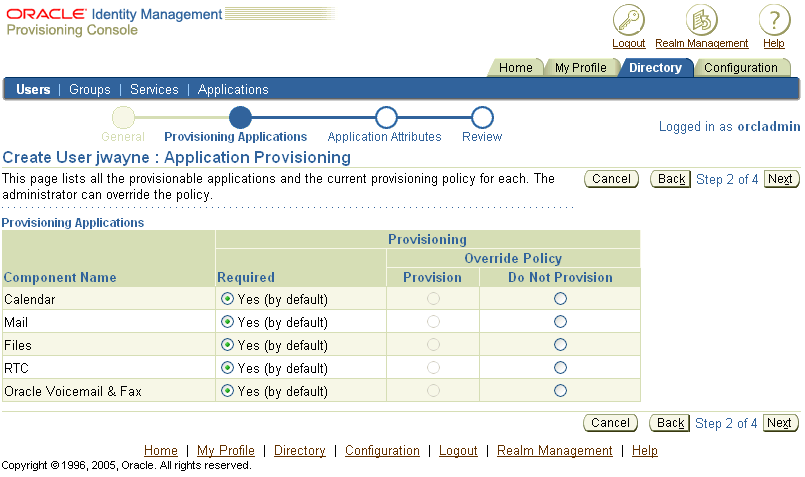
In the Create User: Application Provisioning window, deployed Oracle Collaboration Suite components are listed, along with a default provisioning policy and override options.
Note:
The default provisioning policy determines which Oracle Collaboration Suite components are provisioned by default whenever a new user is created. To change the default provisioning policy, see "Setting Default Provisioning Policies".Select a policy override option to override provisioning policy for any component.
Select Next to display the Create User: Application Attributes window (Figure 4-5).
Figure 4-5 Provisioning Console Create User: Application Attributes Window
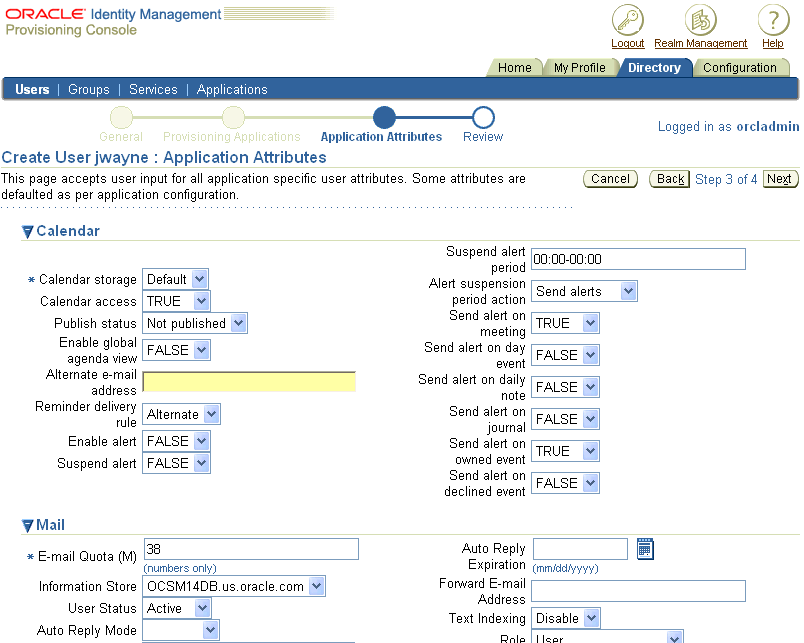
In the Create User: Component Attributes window, required and optional fields are displayed for all Oracle Collaboration Suite Components for which this user is being provisioned.
You must complete at least the required fields shown in this window. For details about all of the Oracle Collaboration Suite Component fields, see Table 4-2, "Oracle Calendar User Attributes", Table 4-3, "Oracle Mail User Attributes", and Table 4-4, "Oracle Voicemail & Fax User Attributes".
Note:
Context-sensitive help is available for all of the standard Oracle Collaboration Suite Components. To view context-sensitive help, for a given component, select Help within that component's field selection region of the Create User: Component Provisioning window.Select Next to display the Create User: Review window (Figure 4-6).
Figure 4-6 Provisioning Console Create User: Review Window
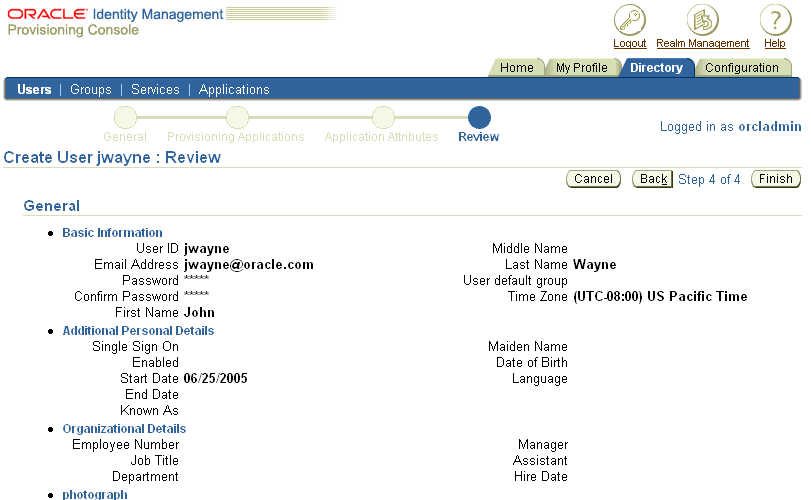
In the Create User: Review window, all of your selections from the previous steps are displayed. Confirm that all of the entries are correct and select Finish to create the user.
If you need to make any corrections, select Back to return to previous Create User windows. You will not lose information entered in later Create User windows unless you completely exit the Create User tab of Provisioning Console.
You can upload an LDIF (LDAP Data Interchange Format) file to the Provisioning Console to create, edit, or delete users in bulk mode.
Note:
The LDIF file may contain only base user attributes and no application specific attributes. So, if an application has mandatory attributes that cannot be set to the default value for certain users, the automatic provisioning of those users will fail.It is possible to create a plug-in which will override default attribute information according to business requirements. The LDIF file import process will honor that plug-in while creating and provisioning users. For more information on managing default application provisioning attributes, see "Setting Default Provisioning Policies".
To create, edit, or delete users in bulk mode:
Select the Directory tab, then Users.
Select Bulk to display the Bulk User Management window.
Select Browse to browse for an LDIF-formatted file containing the properly formatted user entries.
Note:
The LDIF file must be formatted according to Lightweight Directory Access Protocol (LDAP) LDIF file format standards. Every user entry must contain at least the required fields for all applications for which that user is being provisioned.Select or de-select the Ignore Failed Users box. It is selected by default. If you select this option, the bulk create process will attempt to create, edit, or delete users regardless of failures. Failed user accounts will be placed in a file you can download at the end of the process. If you do not select the Ignore Failed Users box, the bulk management process will abort at the first failed user. If you are testing bulk user creation for the first time, Oracle recommends you deselect this box, to avoid cases where hundreds of errors are generated due to a repeating formatting error, missing default field, or other common problem.
Select OK to begin importing user entries.
See Also:
For more information about creating and formatting an LDIF file for bulk user creation, see the Oracle Internet Directory Administrator's GuideNote:
If you do not have the privileges to edit a user entry, then the Edit button does not appear, and you cannot perform this operation. See Assigning Privileges to Users and "Assigning Privileges to Groups" for information on setting privileges.Select the Directory tab, then Users, and perform a search for the user whose entry you want to modify.
Select the user whose entry you want to modify, then choose Edit to display the Edit User window.
In the Edit User: General window, enter the appropriate information. Fields designated with an asterisk (*) are mandatory.
Select Next to display the Edit User: Component Provisioning window.
In the Edit User: Component Provisioning window, all deployed Oracle Collaboration Suite components are listed. You may select any provisioned component and De-Provision that component.
Select Next to display the Edit User: Application Attributes window.
In the Edit User: Application Attributes window, required and optional fields are displayed for all Oracle Collaboration Suite Components that have been provisioned for this user.
You must complete at least the required fields shown in this window. For details about all of the Oracle Collaboration Suite Component fields, see Table 4-2, "Oracle Calendar User Attributes", Table 4-3, "Oracle Mail User Attributes", and Table 4-4, "Oracle Voicemail & Fax User Attributes".
Note:
Context-sensitive help is available for all of the standard Oracle Collaboration Suite Components. To view context-sensitive help, for a given component, select Help within that component's field selection region of the Create User: Component Provisioning window.Select Next to display the Edit User: Review window.
In the Edit User: Review window, all of your selections from the previous steps are displayed. Confirm that all of the entries are correct and select Finish to edit the user.
If you need to make any corrections, select Back to return to previous Edit User windows. You will not lose information entered in later Edit User windows unless you completely exit the Edit User tab of the Provisioning Console.
You can assign or revoke privileges for users. The privileges available are described in Table 4-1, "User Privileges".
Note:
You can also assign and revoke privileges for groups. Many organizations find that it is easier to manage privileges for users by assigning them to groups which have the desired privileges, rather than assigning and revoking privileges directly for each user.For instructions on how to assign and revoke privileges to groups, see "Assigning Privileges to Groups".
Table 4-1 User Privileges
| Privilege | Description of Access Granted |
|---|---|
|
Allow user creation |
Create user entries |
|
Allow user editing |
Modify user entries |
|
Allow user deletion |
Delete user entries |
|
Allow group creation |
Create group entries |
|
Allow group editing |
Modify group entries |
|
Allow group deletion |
Delete group entries |
|
Allow privilege assignment to users |
Assign access rights to users |
|
Allow privilege assignment to groups |
Assign access rights to groups |
|
Allow service management |
Enable group members to manage services for users. If this is selected, then a Services link becomes available in the Directory tab page when the latter is accessed by group members. |
|
Allow account management |
Enable group members to manage accounts for users. If this is selected, then an Accounts link becomes available in the Directory tab page when the latter is accessed by group members. |
|
Allow Oracle Delegated Administration Services configuration |
Configure Oracle Delegated Administration Services user interface |
|
Allow resource management for Oracle Reports- and Forms-based applications |
Enable users to configure resources—such as databases or applications—to which access is allowed |
|
Allow User Management and Application Provisioning |
Allows provisioning users; also automatically enables user account creation, editing, and deletion access |
To assign or revoke privileges to a user:
Select the Directory tab, then Users.
Perform a search for the entry of the user account to which you want to assign or revoke privileges.
From the search results list, select the desired user, then choose Privileges. The Assign Privileges to User window displays a list of privileges.
Select the privileges you want to assign to this user. De-select privileges you want to revoke from this user.
Note:
Any user account may inherit privileges from a group in which it is a member. Even if you leave a privilege de-selected on this screen, if the user belongs to a group that has that privilege, the user will have access to that privileged function.Select Submit to assign or revoke privileges as shown.
You can change the password of a user other than yourself if:
You have the necessary access rights
You have configured user entries so that the userpassword attribute is available for modification. The steps for specifying a user attribute for modification is described in "Configuring the Self-Service Console for User Management".
To change another user's password:
Select the Directory tab, then select Users.
Perform a search for the entry of the user whose password you want to change.
From the results of your search, select the user entry, then choose Edit to display the Edit User window.
In the Edit User window, enter and confirm the password you want to assign to the user.
Choose Submit.
Note:
If you do not have the privileges to edit a user entry, then the Edit button does not appear, and you cannot perform this operation.If a user's account has been locked for any reason—for example, if the user entered an incorrect password for a specified number of times while signing in—then you can unlock it without resetting the user password. This saves you from having to explicitly tell the user the new password. Instead, the user can simply log in by using the old password.
To unlock a user's account:
Select the Directory tab, then select Users.
Perform a search for the user account that has become locked. A checkmark appears in the Locked column for any user account which has become locked.
Select the account that you want to unlock.
Select Unlock.
You can temporarily disable any user account. While an account is disabled, the user cannot log in. However, the user will continue to be available in the applications. E-mail messages sent to a disabled Oracle Mail user will accumulate in the user's Inbox. Disabled Oracle Calendar users will still be available to be added to appointments and meetings.
If a user's account has been disabled, you can enable it. To enable or disable user accounts:
Select the Directory tab, then select Users.
Perform a search for the user account that you wish to enable or disable. A checkmark appears in the Enabled column for any user account which enabled, and there is no checkmark in this column for any user account which has become suspended.
Select the user account that you want to enable or disable.
Select Enable to enable the user account. Select Disable to Disable the user account.
When you create a user account, you provision that account for one or more Oracle Collaboration Suite applications. You can later provision the user for additional Oracle Collaboration Suite applications.
At any time, you can de-provision a user account from one or more provisioned applications. De-provisioning means that the user will no longer be able to access the application. De-provisioning is different from disabling in the following ways:
A disabled user continues to exist in the application; other users of that application will see the disabled user ID in contact lists, calendar appointments, shared folders, and so forth.
A de-provisioned user is no longer available in the de-provisioned application. E-mail messages sent to a user ID which has been de-provisioned from Oracle Mail will be rejected by the system. Users cannot add a user de-provisioned from Oracle Calendar to appointments or meetings.
A de-provisioned user account remains in Oracle Internet Directory. The account can later be re-provisioned for an application, and regain access to stored data such as Oracle Mail e-mail messages, and Oracle Content Services stored files.
Note:
For Oracle Content Services, de-provisioning a user is the same as disabling a user.To de-provision a user from one or more applications:
Using the Provisioning Console, select the Directory tab and then search for the user you wish to de-provision.
Select the user and click Edit. The Edit User: General window is shown.
Select Next. The Edit User: Application Provisioning window is shown (Figure 4-7). In this window, all available applications are shown. Select each provisioned application in the De-Provision column to de-provision those applications.
Figure 4-7 Provisioning ConsoleEdit User: Application Provisioning Window
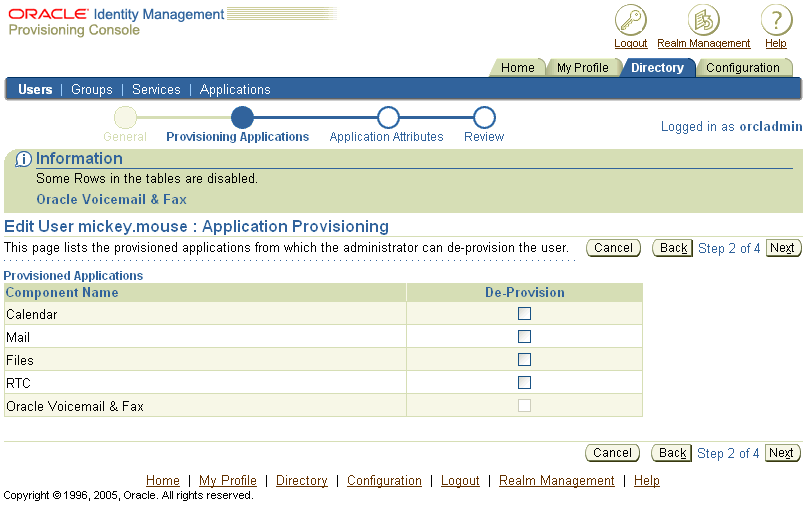
Click Next. The Edit User: Application Attributes window opens. De-provisioned applications will not show attributes on this page.
Click Next. The Edit User: Review window opens. At the bottom of the page, a section titled 'Applications to be De-Provisioned lists all applications that will be de-provisioned.
Click Finish. The user will be de-provisioned from applications, and any other changes you have made while editing the user account will be saved.
When a user is de-provisioned from Oracle Voicemail & Fax, the Oracle Internet Directory user object allocated for this user is deleted. The user's existing voice mail messages stored in the system will not be impacted by this function. However, the user's greeting messages and the language preferences (if any) are deleted. The user will need to be 're-provisioned' for Oracle Voicemail & Fax in order to be 're-enabled'.
The user object is deleted to ensure that the system can re-use the phone number of a disabled user. Users cannot log into Oracle Voicemail & Fax or use any of the Oracle Voicemail & Fax services while their accounts are de-provisioned.
You can delete a user account. When you delete a user account, the user is de-provisioned from all provisioned applications. Additionally, the base user information is removed from Oracle Internet Directory. Once a user account has been deleted, the only way to recover that user account is to restore a backup of Oracle Internet Directory, and then re-provision the user account for applications.
When a user account is deleted, certain types of stored application data is retained in the system. This data includes e-mail messages stored by Oracle Mail, files stored in Oracle Content Services, and voice mail messages stored by Oracle Voice Mail & Fax.
Applications which do not directly store user data, or which are not directly provisioned for users, are not listed below. For example, users are not directly provisioned for Oracle Discussions; rather, Oracle Discussions data are stored in the Oracle Mail schema, and you perform data deletion processes by using the Oracle Mail deletion procedure.
Note:
Your organization may be legally required to retain certain types of electronic communications and records for certain amounts of time. Oracle has designed the user deletion process in Oracle Collaboration Suite to assist you with this task.Most types of user data are retained in the system unless explicitly deleted, either by a user or by performing special data removal procedures for each Oracle Collaboration Suite application which retains user data after an account is deleted.
Note:
If you do not have the privileges to delete a user entry, then the Delete button does not appear, and you cannot perform this operation.To delete a user entry:
Select the Directory tab, then Users.
In the Search for user window, perform a search for the user whose entry you want to delete.
Select the user account and click Delete. A confirmation page loads.
Select Yes to delete the account. Select No to cancel.
Deleting a user causes all Oracle Calendar user data to be deleted. See "Calendar User Account Deprovisioning" in Chapter 7 of Oracle Calendar Administrator's Guide for more information about Oracle Calendar de-provisioning.
Because all files in Oracle Content Services reside in Libraries, users do not own content. All content belongs to the Library in which it is located. When users are deleted from Oracle Content Services, any data that was uploaded by that user remains in the Oracle Content Services repository.
In some cases, you may want to delete the Personal Library of a deleted user. To do this, you must sign on to Oracle Content Services as a user with the Library Administrator role and switch to Administration Mode. You can then navigate to the appropriate Personal Library and delete it.
For complete information on removing user data from Oracle Mail, see "Clearing Data from the Oracle Collaboration Suite Database" in Appendix D of Oracle Mail Administrator's Guide.
For information about removing Oracle Real-Time Collaboration user data, see "Deleting User Data from the Oracle Real-Time Collaboration Database" in Appendix D of Oracle Real-Time Collaboration Administrator's Guide.
When a user is deleted from Oracle Voicemail & Fax, the user's existing voice mail messages stored in the system will not be deleted. However, the user's greeting messages and the language preferences (if any) are deleted. The user will need to be 're-provisioned' for Oracle Voicemail & Fax in order to regain access to stored voice mail messages.
Oracle Calendar, Oracle Mail, and Oracle Voicemail & Fax have user attributes in addition to the General user attributes. When you create or modify user entries, after you specify the General user attributes, you can specify these application-specific attributes.
Table 4-2, "Oracle Calendar User Attributes", Table 4-3, "Oracle Mail User Attributes", and Table 4-4, "Oracle Voicemail & Fax User Attributes" list those attributes, along with their default and available values and a description of each attribute.
See Also:
"Managing Oracle Collaboration Suite Application-Specific Attribute Defaults" for instructions on how to change the application-specific attribute default valuesTable 4-2 Oracle Calendar User Attributes
| Component/Field | Default Value | Available Values | Description |
|---|---|---|---|
|
Calendar StorageFoot 1 |
Based on policy |
Default, select from list of available storage |
Which Calendar storage to use for storing this user's Calendar data |
|
Calendar Access |
TRUE |
TRUE, FALSE |
Use this option to enable or disable the user's access to Calendar |
|
Publish Status |
Not Published |
Not Published, Published |
Determines whether this user's agenda information is visible to other calendar users |
|
Enable Global agenda view |
TRUE |
TRUE, FALSE |
Determines whether the user's agenda information can be made visible to other people on the web |
|
Reminder Delivery Rule |
Alternate |
Alternate, Primary |
Determines whether e-mail reminders should be sent to the user's alternate or primary e-mail address |
|
Alternate E-mail Address |
null |
user entry |
Specifies the user's alternate e-mail address for reminder delivery |
|
Enable Alert |
FALSE |
TRUE, FALSE |
Use this option to enable or disable alerts |
|
Suspend Alert |
FALSE |
TRUE, FALSE |
Temporarily disable alerts for a specified period |
|
Suspend Alert period |
00:00-00:00 |
Hours:minutes-Hours:minutes |
Specify duration for alerts to be suspended |
|
Alert Suspension Period Action |
Send Alerts |
Discard Alerts, Hold Alerts, Send Alerts |
During alert suspension period, option determines what should happen to outgoing alerts |
|
Send Alert on Meeting |
TRUE |
TRUE, FALSE |
Determines whether this user will receive an alert when a meeting is created or modified |
|
Send Alert on Day Event |
FALSE |
TRUE, FALSE |
Determines whether this user will receive an alert when a day event is created or modified |
|
Send Alert on Daily Note |
FALSE |
TRUE, FALSE |
Determines whether this user will receive an alert when a daily note is created or modified |
|
Send Alert on Journal |
FALSE |
TRUE, FALSE |
Determines whether this user will receive an alert when a journal entry is created or modified |
|
Send Alert on Owned Event |
TRUE |
TRUE, FALSE |
Determines whether this user will receive an alert when an event owned by this user is created or modified |
|
Send Alert on Declined Event |
FALSE |
TRUE, FALSE |
Determines whether this user will receive an alert when an event that was previous declined is modified |
Table 4-3 Oracle Mail User Attributes
| Component/Field | Default Value | Available Values | Description |
|---|---|---|---|
|
E-mail Quota (M)Foot 1 |
38 |
Numbers (Megabytes) |
Size of user's allocated storage on the server |
|
Information Store |
null |
Default, <list of available>? |
If there are multiple Information storage units, select one for this user |
|
User Status |
Active |
Active, Inactive |
An Active user is a user with all permissions to access. An Inactive user cannot access the mail system at all. However, messages sent to an Inactive account are stored in the information store and can be accessed once the account is activated. |
|
Auto Reply Mode |
null |
Echo, Reject, Reply, Vacation |
Users can modify their reply mode. Echo replies with a copy of the sender's message along with the Auto Reply Text. Reject rejects all incoming messages. Reply replies to every incoming message with the Auto Reply Text only. Vacation replies with only one message per sender, with the Reply Text. |
|
Auto Reply Text |
null |
user entry |
If the Auto Reply Mode is set to Reply, this text will be included in the Reply message. |
|
Auto Reply Expiration |
null |
mm/dd/yyyy |
This date sets when Auto Reply Mode will switch back to normal delivery mode. |
|
Forward E-mail Address |
null |
user entry |
When Forward E-mail Address attribute is set with an e-mail address, all messages will be forwarded to this e-mail address. If this attribute is blank, messages will not be forwarded. |
|
Text Indexing |
none |
Disable, Enable |
This setting determines whether Search functions will access message body and attachments, or just sender and subject lines. |
|
Role |
User |
Domain Administrator, System Administrator, User |
Specifies the permissions for this user: A domain administrator will have permissions to administer and configure Oracle Mail within a particular domain; A system administrator will have permissions to administer and configure the entire Oracle Mail system; A user will only have permissions to access, read, and send e-mail and voice mail messages. |
|
Archive Policy |
Null |
<any existing archive policy name> |
Enter an archive policy name to enable an offsite, third-party message storage solution. See "Oracle Mail Archive Policies" in chapter 8 of the Oracle Mail Administrator's Guide for details. |
Table 4-4 Oracle Voicemail & Fax User Attributes
| Component/Field | Default Value | Available Values | Description |
|---|---|---|---|
|
International Phone NumberFoot 1 |
null |
user entry |
Enter a unique phone number for this voice mail user. |
|
Group NameFootref 1 |
null |
list of available groups |
Assign the user to one of the available groups. |
|
Voicemail PasswordFootref 1 |
null |
user entry |
Create or reset the user's password. |
|
Confirm PasswordFootref 1 |
null |
user entry |
Enter the password again in this box. The password must match the Voicemail Password exactly. |
|
Voice Preferred Language |
null |
American English, Arabic, Brazilian Portuguese, British English, Danish, Dutch, Finnish, French, German, Greek, Italian, Japanese, Korean, Mandarin-China, Mandarin-Taiwan, Norwegian, Portuguese, Spanish, Swedish, Turkish |
Select the language to be used for the voice mail user's voice prompts. |
|
Phone Access Allowed |
null |
true, false, Group Default |
You can enable or deny voice mail access to the user or have the user inherit this setting from the user's group. |
|
Faxin Access Allowed |
null |
true, false, Group Default |
You can enable or deny fax access to the user or have the user inherit this setting from the user's group. |
|
Message Waiting Indicator |
null |
true, false, Group Default |
If the user's phone has a message waiting indicator and this option is enabled, the system turns the message waiting indicator on to let the user know there is a new voice mail message. Setting it to the Group Default causes the user to inherit the setting from the user's group. |
|
Additional Voice Quota |
null |
Numbers (bytes) |
Voice mails are counted against the user's e-mail quota. You can use this setting to allocate additional storage for both e-mail and voice mail messages. This can help prevent large voice mail messages from filling up the user's e-mail quota. |
This section describes how to use the Provisioning Console to create, modify, and delete group entries and to assign privileges to groups. It contains the following topics:
To create a group entry:
Select the Directory tab, then select Groups.
Choose Create. This displays the Create Group window.
In the Create Group window, in the Basic Information section, in the Name field, enter the name for this group.
In the Display Name field, enter the friendly name for this group. For example, if the RDN is OracleDBCreators, then you could enter the display name as Oracle Database Creators.
Optionally, in the Description field, enter a brief description of this group.
To hide this group entry from all but its owners, in the Group Visibility field, select Private. Otherwise, accept the default, namely, Public.
Configure owners of this group. Note that the creator of the group is automatically a group owner.
To add a user as an owner of this group:
In the Owners section, choose Add User. This displays the Search and Select: User window.
Search for the entry of the user you want to add as an owner of the group.
Choose Select. This returns you to the Create Group window. The user you specified is listed in the Owners section.
To add a group as an owner of this group:
In the Owners section, choose Add Group. This displays the Search and Select: Group window.
Search for the entry of the group you want to add as an owner of the group.
Choose Select. This returns you to the Create Group window. The group you specified is listed in the Owners section.
To remove a user or group as an owner of this group, select the user or group, then choose Remove.
Configure members of this group.
To add a user as a member of this group:
In the Members section, choose Add User. This displays the Search and Select window.
Search for the entry of the user you want to specify as a member of this group.
Choose Select. This returns you to the Create Group window. The user you specified is listed in the Members section.
To remove a user from this group, in the Members section, select the user's name and choose Remove.
To add a group as a member of this group:
In the Members section, choose Add Group. This displays the Search and Select window.
Perform a search for the entry of the group you want to specify as a member of this group, then choose Select. This returns you to the Create Group window. The group you specified is listed in the Members section.
You can assign roles to this group.
To specify the roles that you want to assign to this group, in the Roles Assignment section, in the Select column, select the role that you want to assign to this group.
To remove the role from the group, in the Roles Assignment section, in the Select column, deselect the role that you want to remove from this group.
To modify a group entry:
Select the Directory tab, select Groups, then perform a search for the group entry you want to modify.
From the search results, select the group entry you want to modify.
Choose View Manage. This displays the Manage Group window.
Choose Edit. The Edit Group window appears.
In the Edit Group window, modify the fields as described in "Creating Group Entries".
Choose Submit.
To delete group entries:
Select the Directory tab, select Groups, then perform a search for the group whose entry you want to delete.
From the search results, select the group whose entry you want to delete.
Choose View/Manage. This displays the Manage Group window.
In the Manage Group window, choose Delete. The Confirmation of Deletion window appears.
In the Confirmation window, choose either Yes or No.
You can assign or revoke privileges for groups. The privileges available are described in Table 4-5, "Group Privileges".
Note:
You can also assign and revoke privileges for users directly. However, many organizations find that it is easier to manage privileges for users by assigning them to groups which have the desired privileges, rather than assigning and revoking privileges directly for each user.For instructions on how to assign and revoke privileges to users, see "Assigning Privileges to Users".
Table 4-5 Group Privileges
| Privilege | Description of Access Granted |
|---|---|
|
Allow user creation |
Create user entries |
|
Allow user editing |
Modify user entries |
|
Allow user deletion |
Delete user entries |
|
Allow group creation |
Create group entries |
|
Allow group editing |
Modify group entries |
|
Allow group deletion |
Delete group entries |
|
Allow privilege assignment to users |
Assign access rights to users |
|
Allow privilege assignment to groups |
Assign access rights to groups |
|
Allow service management |
Enable group members to manage services for users. If this is selected, then a Services link becomes available in the Directory tab page when the latter is accessed by group members. |
|
Allow account management |
Enable group members to manage services for users. If this is selected, then an Accounts link becomes available in the Directory tab page when the latter is accessed by group members. |
|
Allow Oracle Delegated Administration Services configuration |
Configure Oracle Delegated Administration Services user interface |
|
Allow resource management for Oracle Reports- and Forms-based applications |
Enable users to configure resources—such as databases or applications—to which access is allowed |
|
Allow User Management and Application Provisioning |
Allows provisioning users; also automatically enables user account creation, editing, and deletion access |
To assign or revoke privileges to a group:
Select the Directory tab, then Groups.
Perform a search for the entry of the group to which you want to assign or revoke privileges.
From the search results list, select the desired group, then choose Assign Privileges. The Assign Privileges to Group window displays a list of privileges.
Select the privileges you want to assign to this group. De-select privileges you want to revoke from this group.
Select Submit to assign or revoke privileges as shown.
There are several options for customizing the user account creation process. This section contains the following topics:
Several of the Oracle Collaboration Suite applications provide a list of custom user attributes which are exposed when you provision a user for that application. Each application attribute has a default value. Complete lists of attributes and their default values for each application are shown in Table 4-2, "Oracle Calendar User Attributes", Table 4-3, "Oracle Mail User Attributes", and Table 4-4, "Oracle Voicemail & Fax User Attributes".
You can set the default attribute for each custom field. The default settings will appear in the Component Attributes window any time a new user is created. Changing defaults will not affect existing users, even if those users were created using previous default values.
To make changes to the default attribute values:
Select the Directory tab, and then select Applications. The Manage Defaults: Select Application screen is shown.
Select the applications corresponding to the default attributes you wish to modify. You cannot select an application which has no user attributes. Select Continue to display the Manage Defaults: Attributes screen.
On the Manage Defaults: Attributes screen, enter the new default value for any attribute displayed. When you are finished making changes, select Submit to apply your changes.
When a user creates or edits a user entry, the Self-Service Console displays various categories—including, for example, basic information, password, and photo—each with its own set of attributes. You can specify which of these categories the console displays, how it displays them and their corresponding attributes, and which can be edited by users themselves.
Specifically, you can:
Associate object classes with user entries, and add and modify these object classes
Specify the categories of attributes you want to enable users to add or modify
Customize the way the Self-Service Console displays those categories and attributes
To configure user entries:
Select the Configuration tab, then select User Entry. This displays the Configure User Object Classes window listing the existing object classes associated with user entries.
To add an object class for user entries:
In the Configure User Object Classes window, choose Add Object Class. This displays the All Object Classes window.
Select an object class you want to add, then choose Add. This returns you to the Configure Object Class window. The object class you just chose is now listed as an object class for user entries.
To add more object classes, repeat these steps, or, to move to the next step, choose Next to display the Configure User Attributes window.
The Configure User Attributes window lists some—but not all—of the attributes of the object classes you specified in Step 2. There may be other attributes belonging to those object classes as well. You can add as many of those other attributes as you wish by following the instructions in this step. You can modify how the attributes are displayed or delete attributes.
To add attributes to user entries:
In the Configure User Attributes window, choose Add New Attribute. This displays the Add New Attribute window.
In the Add New Attribute window, enter values for the fields.
Choose Done. This returns you to the Configure User Attributes window. The attribute you just chose is now listed in the attribute list.
To add more attributes, repeat these steps.
To modify the display of attributes:
In the Configure User Attributes window, in the Directory Attribute Name column, select the attribute you want to modify, then choose Edit. This displays the Editing Attribute window.
In the Editing Attribute window, enter values for the fields.
Choose Done. This returns you to the Configure User Attributes window. The attribute configurations you just made are now reflected in the Directory Attribute Name list.
To configure or modify more attributes, repeat these steps.
To delete attributes of user entries, in the Configure User Attributes window, in the Directory Attribute Name list, select the attribute you want to configure, then choose Delete.
To customize the display of categories, in the Configure User Attributes window choose Next to display the Configure Attribute Categories window. This window contains a table listing the existing categories, the name displayed to the user, and the display order of each category.
To add a new category, choose Create. This displays the Create window. In the UI Label field, enter the name of the category as you would like it displayed in the interface.
To modify the display name of a category, in the UI Label column, edit the field for each attribute you want to modify.
To set the display order of categories, choose Order Category. The Order Category window displays the various categories you just specified. Use the up and down arrows to move the categories into the desired order.
To set the display order of attributes for each category, select the category, then choose Edit. In the Order Category window, use the arrow buttons to set the display order of the attributes, or to remove an attribute from being displayed.
To delete a category, select the category, then choose Delete.
When you have finished configuring attribute categories, choose Next to display the Configure Search Table Columns window.
When a user performs a search, the results are displayed in a table. You can specify the number of columns in that table and their headings. To configure search table columns:
In the Configure Search Table Column window, in the All Attributes box, select one or more attributes that you want to be represented in the search results. These will serve as column headings in the search results table.
Use the left-right arrows to move the attributes to the Selected Attributes box.
In the Selected Attributes box, order the attributes by using the up-down arrows to the right of the box. The first attribute in the list represents the column farthest to the left in the search results table.
When you have finished configuring the search results table, choose Next to display the Configure Roles window.
To enable users to assign roles to users, in the Configure Roles window, in the Enable Roles category, select Enable Role assignment in the user management interface.
You can specify the roles that users can assign to other users.
To add a role that users can assign to other users:
Choose Add Role to display the Search and Select: Roles window.
In the Group Name Begins With field, enter the first few letters of the name of the administrative group you want to add.
From the search results, select the name of the administrative group you want to add, then choose Select. This returns you to the Configure Roles window. The administrative group you just selected appears in the Roles list.
To delete a role, select it from the table and choose Delete.
When you have finished configuring user entries, choose Finish.
A provisioning policy is a set of rules that determines whether, and how, a given user will be provisioned for available Oracle Collaboration Suite applications. Oracle Delegated Administration Services implements the policy each time a user account is created, edited, or deleted. The action of creating or modifying a user account triggers the provisioning policy.
A default provisioning policy is set during installation of Oracle Collaboration Suite. This property, the DEFAULT_PROVISIONING_POLICY may be updated using the provisioning tool $ORACLE_HOME/bin/oidprovtool. The default provisioning policy for Oracle Collaboration Suite specifies that new users should be provisioned for all available (configured) Oracle Collaboration Suite applications. When you create a new user individually using the Provisioning Console, you can override this policy for each available Oracle Collaboration Suite application.
See Also:
For more information about default provisioning policies and theoidprovtool, see Appendix C, "User Provisioning Java API".You can create a new default provisioning policy that is triggered for every user that is created for some Oracle Collaboration Suite applications. This policy can inspect whether the user should be provisioned for the particular application or not, based on specified business requirement logic. It can also be used to set or override the default values of application-specific user attributes.
Custom policies are supported in the form of a plug-in that a developer can write after installation and initial configuration. When administrators create new accounts, they always have the privilege to override the policy.
See Also:
"Java Plug-ins for User Provisioning"Table 4-6 shows the way the various Oracle Collaboration Suite applications use the provisioning framework to perform user provisioning. This is the out-of-the-box behavior. You can alter this behavior and implement business policies by implementing or altering the pre- and post-data entry plug-ins. However, you cannot alter the provisioning plug in. If an application already has a pre- or post-data entry plug-in, you should not attempt to modify the existing plug-in; doing so could cause the plug-in to stop working, disabling provisioning. However, you can write your own pre- and post-data entry plug-ins for those applications which do not already have them.
Table 4-6 Oracle Collaboration Suite Application Provisioning Plug-in Implementation
| Application | Provisioning Mode | Provisioning Plug-in Type | Pre-Data Entry Plug-in | Post-Data Entry Plug-in |
|---|---|---|---|---|
|
Oracle Mail |
Synchronous |
Data Access Plug-in |
Yes |
Yes |
|
Oracle Voicemail & Fax |
Synchronous |
Data Access Plug-in |
Yes |
Yes |
|
Oracle Content Services |
Asynchronous |
PLSQL |
No |
No |
|
Oracle Real-Time Collaboration |
Asynchronous |
PLSQL |
No |
No |
|
Oracle Calendar |
Asynchronous |
PLSQL |
No |
Yes |
|
Oracle Mobile Collaboration |
Asynchronous |
PLSQL |
No |
No |
Managing Provisioning Profiles
Use the Provisioning Subscription Tool to perform these activities:
Create a new provisioning profile. A new provisioning profile is created and set to the enabled state so that the Oracle Directory Integration and Provisioning platform can process it
Modify an existing provisioning profile
Enable or disable an existing provisioning profile
Delete an existing provisioning profile
Get the current status of a given provisioning profile
Clear all of the errors in an existing provisioning profile
Use the Oracle Internet Directory Server Manageability functionality in the Oracle Collaboration Suite Control to monitor provisioning profiles.
The Provisioning Subscription Tool shields the location and schema details of the provisioning profile entries from the callers of the tool. From the callers' perspective, the combination of an application and a subscriber uniquely identify a provisioning profile. The constraint in the system is that there can be only one provisioning profile for each application for each subscriber.
Note:
To run shell script tools on the Windows operating system, you need one of the following UNIX emulation utilities:Cygwin 1.3.2.2-1 or later. Visit: http://sources.redhat.com
MKS Toolkit 6.1. Visit: http://www.datafocus.com/
The name of the executable is oidProvTool, located in ORACLE_HOME/bin. To invoke this tool, use this command:
oidprovtool param1= param1_value param2= peram2_value param3= peram3_value ...
The Provisioning Subscription Tool accepts the following parameters:
Table 4-7 Provisioning Subscription Tool Parameters
| Name | Description | Operations | Mandatory/Optional |
|---|---|---|---|
|
|
The subscription operation to be performed. The legal values for this parameter are: create, enable, disable, delete, status and reset. Only one operation can be performed for each invocation of the tool. |
All |
M |
|
|
Host-name of the directory server on which the subscription operations are to be performed. If not specified, the default value of 'localhost' is assumed. |
All |
O |
|
profile_status |
The status of the profile ( |
Create |
O |
|
profile_mode |
|
Create |
O |
|
profile_debug |
The debugging level with which the profile is executed by the Oracle directory integration and provisioning server. |
All |
O |
|
sslmode |
Indicator of whether to execute the Provisioning Subscription Tool in SSL mode. A value of |
All |
O |
|
|
The TCP/IP port on which the Oracle directory server is listening for requests. If not specified, the default value of `389' is assumed. |
All |
O |
|
|
The LDAP distinguished name (DN) of the user on whose behalf the operation is to be performed. Not all users have the necessary permissions to perform Provisioning Subscription operations. Please see the administrative guide to grant or deny LDAP users the permission to perform Provisioning Subscription operations. |
All |
M |
|
|
The password of the user on whose behalf the operation is to be performed. |
All |
M |
|
|
The LDAP distinguished name of the application for which the Provisioning Subscription Operation is being performed. The combination of the application_dn and the organization_dn parameters help the subscription tool to uniquely identify a provisioning profile. |
All |
M |
|
|
The LDAP distinguished name of the organization for which the Provisioning Subscription Operation is being performed. The combination of the application_dn and the organization_dn parameters help the subscription tool to uniquely identify a provisioning profile. |
All |
M |
|
|
Database schema name for the PLSQL package. Format of the value should be: [Schema].[PACKAGE_NAME] |
Create only |
M |
|
|
The type of the interface to which events have to be propagated.Valid Values: PLSQL (if not specified this is assumed as the default) |
Create only |
O |
|
|
Database connect string Format of this string:[HOST]:[PORT]:[SID]:[USER_ID]:[PASSWORD] |
Create only |
M |
|
|
The version of the interface protocol. Valid Values: 1.0 or 1.11.0 will be the old interface. If not specified, this is used as the default. |
Create only |
O |
|
|
Additional information for the interface. This is not currently used. |
Create only |
O |
|
|
The scheduling information for this profile. The value is the length of the time interval in seconds after which DIP will process this profile. If not specified, a default of 3600 is assumed. |
Create only |
O |
|
|
The number of times the Provisioning Service should retry a failed event delivery. If not specified, a default value of 5 is assumed. |
Create only |
O |
|
|
Events for which DIP should send notification to this application. Format of this string:"[USER]GROUP]:[<Domain of interest>]:[DELETE]ADD]MODIFY(<list of attributes separated by comma>)]"Multiple values may be specified by listing the parameter multiple times each with different values. If not specified the following defaults are assumed:USER:<org. DN>:DELETEGROUP:<org. DN>:DELETEqQthat is, send user and group delete notifications under the organization DN. |
Create only |
O |
Oracle Collaboration Suite sets up basic password policies by default during installation. For example, by default all passwords expire (and must be changed) after 60 days. You can change the password policies by using Oracle Directory Manager to edit the Oracle Internet Directory.
To change the password policies:
Start the Oracle Directory Manager:
Unix:
ORACLE_HOME/bin/oidadmin
Windows:
Start > Programs > Oracle Application Server > OracleHome > Integrated Management Tools > Oracle Directory Manager
When you start Oracle Directory Manager, it will prompt you for connection information. Enter the following information to connect to your Oracle Internet Directory, typically hosted in the Oracle Collaboration Suite Database on your Oracle Collaboration Suite Infrastructure:
Host: <infrahost.yourdomain.com> Port: 389 Username: cn=orcladmin Password: <password>
Port 389 is the default port used by Oracle Internet Directory. You may be using a different port. If so, enter the correct Oracle Internet Directory port.
If you have configured your Oracle Internet Directory to be accessed using Secure Socket Layers (SSL), select the SSL Enabled checkbox. Otherwise, leave it blank.
Select Login to log in to the Oracle Internet Directory. When the connection is successful, the Oracle Internet Directory management screen is displayed. See Figure 4-8, "Accessing Oracle Internet Directory with Oracle Directory Manager".
Figure 4-8 Accessing Oracle Internet Directory with Oracle Directory Manager
Expand Password Policy Management to display the policy management objects. You will see one entry called cn=PwdPolicyEntry, and one additional entry for each Realm in your deployment. Figure 4-9 shows the PwdPolicyEntry object.
Figure 4-9 Password Policy Management in Oracle Internet Directory
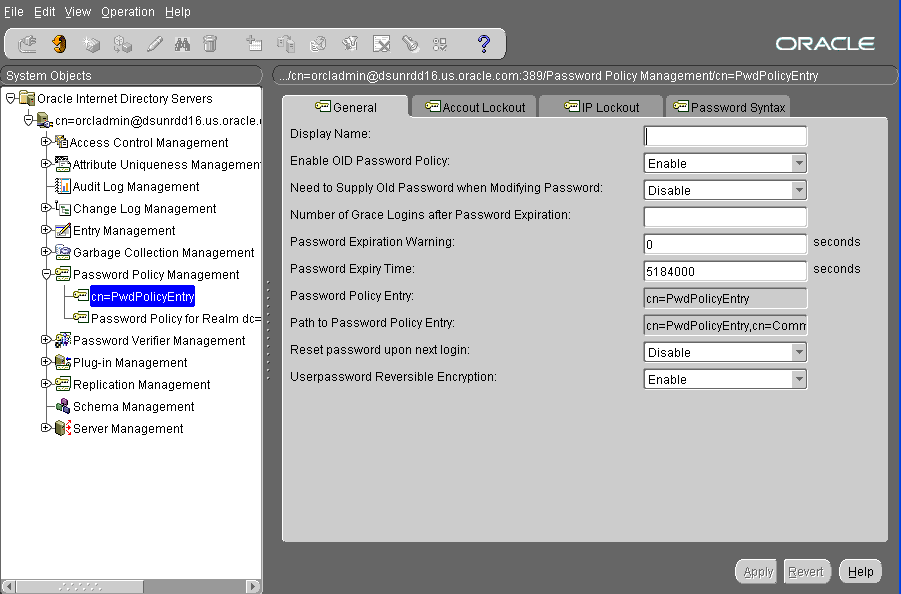
Make changes to the password policy fields as required. You can specify policies for all realms at once by editing the PwdPolicyEntry object, or you can specify specific policies for each realm by editing each Password Policy for Realm ... object. Password policies specified in the PwdPolicyEntry object do not override password policies specified in any specific realm. Therefore, if you make a change to the PwdPolicyEntry object, it may not affect one or more realms that already have existing password policies specified.
After making changes to the password policies, your changes will not appear in the Oracle Internet Directory Provisioning Console until you refresh the user entry page. To do this, from the Provisioning Console, select the Configuration tab, and then click User Entry. On the User Entry page, click the refresh icon to refresh the page. This will cause the Provisioning Console to read your changes to the password policies and update the page
The following tables provide descriptions of the fields in the password policy management objects.
Table 4-8 Fields in the Password Policies General Tab Page
| Field | Description |
|---|---|
|
Enable OID Password Policy |
To disable the default Oracle Collaboration Suite password policy, select Disable. The default is Enable. |
|
Need to Supply Old Password When Modifying Password |
Specify whether user must supply old password with new one when modifying password. By default, the old password is not required. |
|
Number of Grace Logins after Password Expiration |
Maximum number of grace logins allowed after a password expires. By default, no grace logins.are allowed. The default value is 3. |
|
Reset password upon next login |
Indicator of whether users must change their passwords after the first login, or after the password is reset by the administrator. Enabling this option requires users to change their passwords even if user-defined passwords are disabled. By default, users need not change their passwords after reset. |
|
Password Expiration Warning |
Enter the number of seconds in which users must modify their passwords before those passwords expire. The directory server sends a password expiration warning if these two conditions are met:
From that point, the user has a specified number of seconds in which to modify the password. If the user does not modify the password within the specified number of seconds, then the password expires and the user is locked out until the password is changed by the administrator. For example, suppose that:
In this example, if you log in during the last hour, then you receive a warning that your password is about to expire. If you do not modify your password during that time, then your password expires and you are locked out of your account until the administrator changes your password. For this feature to work, the client application must support it. The default is |
|
Password Expiry Time |
Enter the number of seconds that a given password is valid. For example, if you set the value of this attribute to If this attribute is not present, or if the value is 0, then the password does not expire. By default, passwords expire in 60 days. |
|
Password Policy Entry |
This field displays the RDN of the password policy entry. You cannot edit this field. |
|
Path to Password Policy Entry |
This field displays the full DN of the password policy entry. You cannot edit this field. |
Table 4-9 Fields in the Password Policies Account Lockout Tab Page
| Field | Description |
|---|---|
|
Global Lockout Duration |
Enter the number of seconds a user is locked out of the global directory if both of the following are true:
You can set user lockout for a specific duration, or until the administrator resets the user's password. The default value is 24 hours. A user account stays locked even after the lockout duration has passed unless the user logs in with the correct password. |
|
Password Failure Count Interval |
Enter the number of seconds after which the password failure times are purged from the user entry. |
|
Password Maximum Failure |
Enter the number of consecutive failed log in attempts after which a user account is locked. |
Table 4-10 Fields in the Password Policies IP Lockout Tab Page
| Field | Description |
|---|---|
|
IP Lockout Duration |
Specify the number of seconds you want to enforce account lockout for a specific IP address. A user account stays locked even after the lockout duration has passed unless the user logs in with the correct password. |
|
IP Lockout Maximum Failure |
Specify the maximum number of failed logins from a specific IP address after which the account is locked. |
Table 4-11 Fields in the Password Policies Password Syntax Tab Page
| Field | Description |
|---|---|
|
Minimum Number of Characters of Password |
Specify the minimum number of characters required in a password. |
|
Number of Numeric Characters in Password |
Specify the number of numeric characters required in a password. |
|
Number of Password History |
Specify how many of a user's previous passwords the directory server is to store. If a user attempts to reuse one of the passwords the directory server has stored, then the password is rejected. The directory server does not maintain a password history by default. |
|
Password Illegal Values |
Enter the common words and attribute types whose values cannot be used as a valid password. By default, all words are acceptable password values. |
This section describes how to use the Provisioning Console to search for user and group entries. It contains the following topics:
To search for user entries:
In the Oracle Internet Directory Self-Service Console, select the Directory tab, then select Users.
In the Search for User field, enter any part of one of the following:
First name
Last name
Login name
The e-mail identifier
For example, if you are searching for Anne Smith, you could enter Ann or Smi or ith.
To generate a list of all users in the directory, leave this field blank.
Select Go or press Enter to display the search results.
To search for a group entry:
Select the Directory tab, then select Groups. The Search for Groups window appears.
In the Search Group Name text box, enter any part of the name of the group for which you are searching.
To generate a list of all groups in the directory, leave this field blank.
Select Go or press Enter to display the entries that match the criteria you entered.
This section describes how to use the Provisioning Console to configure a realm, modify those configurations, and create additional realms. Identity management realms are useful for segregating users into multiple separate domains. For example, if you have two user populations, each with e-mail addresses resolving to two separate e-mail domains, you might wish to create two identity management realms to manage them.
This section contains the following topics:
Viewing Configuration Settings for an Identity Management Realm
Modifying Configuration Settings for an Identity Management Realm
Configuring the Parent Distinguished Name for Entries in a Realm
If you have the correct administrative privileges, then you can specify the following for an identity management realm:
The attribute by which you want users to identify themselves when they log in
The root entries of the user search base and of the group search base—that is, the locations in the directory information tree (DIT) containing entries for users and groups
The root entries for the user creation base and the group creation base—that is, the location in the DIT where users and groups are created. This can be the same as the user search base or a location under the user search base.
The display of realm and product logos
To configure an identity management realm:
Select the Configuration tab.
In the Identity Management Realm window, enter values for the various fields.
Choose Submit to save your changes.
Note:
Although you can enter more than one value in the User Search Base field, doing so can degrade performance.To view the configuration settings of an identity management realm:
Select the Configuration tab.
At the top right of the Self-Service Console, choose the Realm Management icon. This displays the Identity Management Realms window.
In the Identity Management Realms window, in the Search Identity Management Realm field, enter all or part of the name of the realm whose entry you want to view, then choose Go. This displays a list of realms that match your search criteria.
From the search results list, select the realm you want to modify, then choose View. This takes you to the Identity Management Realm window where you can view the configuration settings.
You can modify the settings of an identity management realm for which you are the administrator. To do this:
Select the Configuration tab.
In the Identity Management Realm window, enter values for the various fields.
Modify the fields, then choose Submit.
You can specify one or more parent distinguished names (DNs) for entries in a realm. If you specify more than one, then a delegated administrator can choose the one under which to place a new user entry.
There are two ways to specify a parent distinguished name (DN). The first is by specifying values for the user creation base, and the second is by specifying values for the organizational units (ou) attribute. If you specify a different set of values for each, then those for the ou attribute prevail.
To specify parent DNs by providing values for the User Creation Base:
Select the Configuration tab, then select Identity Management Realm.
In the User Creation Base field, enter one or more DNs, one line for each DN.
Choose Submit.
Alternatively, you can specify parent DNs by setting the value for the organizational unit (ou) attribute. If you do this, then a delegated administrator can choose the organization unit under which to place user entries. To specify a parent DN by using this method:
Select the Configuration tab, then select User Entry.
Choose Next. The Configure User Attributes window appears.
Choose Add New Attribute. The Add New Attribute window appears.
In the Add New Attributes window, from the Directory Attribute Name list, select the ou attribute.
From the UI Type list, select Predefined List.
In the LOV Values field, enter the display name of the parent DN, followed by three semicolons (;), followed by the DN itself.
For example:
Sales;;;cn=users,dc=us,dc=my_company,dc=com HR;;;cn=groups,dc=us,dc=my_company,dc=com
Following this example, when a delegated administrator chooses the organizational unit under which to place a user entry, she selects from a list displaying Sales and HR.
You can add more parents DNs, one line for each.
If you have the administrative privileges, then you create an entry for an identity management realm as follows:
Select the Configuration tab.
At the top right of the Oracle Internet Directory Self Service Console, choose the Realm Management icon. This displays the Identity Management Realms window.
In the Identity Management Realms window, choose Create. The Create Identity Management Realm window appears.
In the Create Identity Management Realm window, enter the appropriate values in the fields.
Choose Submit.