| Oracle® Application Server Administrator's Guide 10g Release 3 (10.1.3) B25209-03 |
|
 Previous |
 Next |
| Oracle® Application Server Administrator's Guide 10g Release 3 (10.1.3) B25209-03 |
|
 Previous |
 Next |
This chapter provides procedures for changing the Infrastructure Services used by a middle-tier instance.
It contains the following topics:
Overview of Procedures for Changing Identity Management Services
Changing Oracle Internet Directory from Dual Mode to SSL Mode
For this release, you can associate a 10g Release 3 (10.1.3) middle-tier instance with Release 2 (10.1.2) or Release 9.0.4 Identity Management Services, as described in Section 6.5.
|
See: Oracle Application Server Upgrade and Compatibility Guide for information about the specific versions of Oracle Identity Management that are supported with 10g Release 3 (10.1.3). |
After you have associated the middle-tier instance with Identity Management Services, you may want to change the Identity Management Services used by the middle-tier instance. For example, you may want to use an Identity Management Service on a different host.
You can change Identity Management Services using the Identity Management page on the Application Server Control Console, shown in Figure 8-1.
Figure 8-1 Application Server Control Console Identity Management Page
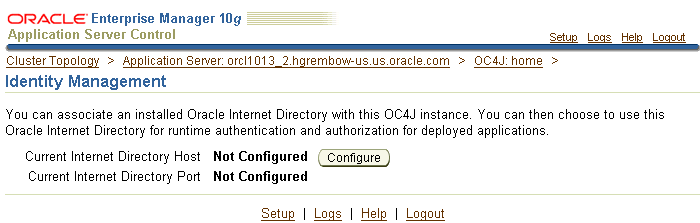
You must change Identity Management Services when you change any of the following:
The HTTP OracleAS Single Sign-On port number on an Identity Management installation
The Oracle Internet Directory non-SSL or SSL port number
The Oracle Internet Directory Mode (dual-mode or SSL)
The host on which Identity Management is installed
If you have disabled anonymous binds in Oracle Internet Directory, you must enable them before you make configuration changes. See Section 6.6, "Disabling and Enabling Anonymous Binds" for more information.
You cannot simply use the wizard to change from one Infrastructure service to another. You must first perform manual tasks to create and prepare the new Infrastructure service. This chapter describes the following supported procedures for changing Infrastructure Services:
Use this procedure if you need to change the Oracle Internet Directory listener port or the HTTP listener port for Oracle Internet Directory on an Identity Management installation. In addition to changing the port numbers, you must update middle-tier instances with the new port information, which requires changing Infrastructure Services.
Changing Oracle Internet Directory from Dual Mode to SSL Mode
Use this procedure if you want to change the Oracle Internet Directory mode from non-SSL to SSL. In addition to changing the mode, you must update middle-tier instances with the new mode, which requires changing Infrastructure Services.
Moving 10.1.2 or 9.0.4 Identity Management to a New Host
Use this procedure if you want to move your Identity Management installation, and its associated Metadata Repository, to a new host. After you perform the move, you must update middle-tier instances with the new host information for Identity Management, which requires changing Infrastructure Services.
To change the Release 2 (10.1.2) Oracle Internet Directory non-SSL or SSL port on an Identity Management installation, refer to Section 4.4.1, "Changing 10.1.2 Oracle Internet Directory Ports" for instructions.
To change the Oracle HTTP Server non-SSL or SSL Listen port on a Release 2 (10.1.2) Identity Management installation, which effectively changes the OracleAS Single Sign-On port, refer to Section 4.4.2, "Changing the HTTP Server Port on a 10.1.2 Identity Management Installation" for instructions.
When you install Release 2 (10.1.2) or 9.0.4 Identity Management, you are asked to choose a mode for Oracle Internet Directory. The default mode is dual mode, which allows some components to access Oracle Internet Directory using non-SSL connections. During the installation, you can choose SSL mode, which specifies that all components must use SSL when connecting to the directory.
If you did not choose SSL mode during the installation, and want to change to SSL mode after installation, follow the procedure in this section. It includes changing the mode of the Oracle Internet Directory, and updating middle-tier instances to use the new mode.
Before you begin this procedure, you must check that the security provider used by Application Server Control is a file-based security provider. If it is not, you need to take additional steps after changing the Oracle Internet Directory mode.
To check the type of security provider, take the following steps:
In Application Server Control Console, navigate to the OC4J home page.
Click Setup.
On the Setup page, select Security Provider.
The Security Provider page shows the type of security provider being used.
If it is not a file-based security provider and you want to change it, you can click Change Security Provider. Then, select File-Based Security Provider and specify a location for the XML file.
If the security provider is Oracle Internet Directory and you do not want to change it before running this procedure, you must take the steps in "Task 3: Change jazn.xml (Oracle Internet Directory Security Provider Only)".
To change Oracle Internet Directory to SSL mode, perform the following tasks:
Task 1: Stop Middle-Tier Processes and Start Application Server Control Console
Task 3: Change jazn.xml (Oracle Internet Directory Security Provider Only)
Task 1: Stop Middle-Tier Processes and Start Application Server Control Console
In all middle-tier instances that use Oracle Internet Directory, take the following steps:
Stop all middle-tier instances using the following command:
(UNIX) ORACLE_HOME/opmn/bin/opmnctl stopall (Windows) ORACLE_HOME\opmn\bin\opmnctl stopall
Because subsequent steps use Application Server Control Console, start OPMN and Application Server Control using the following commands. To start Application Server Control Console, you start the default OC4J instance, because Application Server Control Console runs as an application with the default OC4J instance.
On UNIX systems:
ORACLE_HOME/opmn/bin/opmnctl start ORACLE_HOME/opmn/bin/opmnctl startproc process-type=home
On Windows systems:
ORACLE_HOME\opmn\bin\opmnctl start ORACLE_HOME\opmn\bin\opmnctl startproc process-type=home
Task 2: Change the Oracle Internet Directory Mode
Perform this task on the Release 2 (10.1.2) Infrastructure that contains Oracle Internet Directory:
Create a file named mod.ldif and enter the following lines in the file:
dn:cn=configset0,cn=osdldapd,cn=subconfigsubentry changetype:modify replace:orclsslenable orclsslenable:1
Run the following command:
ldapmodify -D "cn=orcladmin" -w orcladmin_passwd -p oid_port -v -f mod.ldif
In the example, oid_port is the non-SSL Oracle Internet Directory port. This is listed as OIDport in ORACLE_HOME/config/ias.properties.
Note that if you are using OracleAS Cold Failover Cluster, you must use the following command:
ldapmodify -D cn=orcladmin -w orcladmin_passwd -h virtual_hostname -p oid_port -v -f mod.ldif
In the example, virtual_hostname is the virtual hostname of the OracleAS Cold Failover Cluster.
Stop the entire instance that contains Oracle Internet Directory:
On UNIX systems:
ORACLE_HOME/bin/emctl stop iasconsole ORACLE_HOME/opmn/bin/opmnctl stopall
On Windows systems:
ORACLE_HOME\bin\emctl stop iasconsole ORACLE_HOME\opmn\bin\opmnctl stopall
Edit the following file:
(UNIX) ORACLE_HOME/ldap/admin/ldap.ora (Windows) ORACLE_HOME\ldap\admin\ldap.ora
Modify the following line to remove the non-SSL port number:
DIRECTORY_SERVERS=(myhost.myco.com:nonsslport:sslport)
The resulting line looks similar to the following:
DIRECTORY_SERVERS=(myhost.myco.com::sslport)
Save and close the file.
If the OracleAS Metadata Repository was created using OracleAS RepCA, take the following steps:
Copy the ldap.ora file from the Identity Management Oracle home to the Oracle home for the OracleAS Metadata Repository. For example, for Release 2 (10.1.2), the location is:
(UNIX) ORACLE_HOME/ldap/admin (Windows) ORACLE_HOME\ldap\admin
Edit the sqlnet.ora file that is located in the following location in the Oracle home for the OracleAS Metadata Repository:
(UNIX) ORACLE_HOME/network/admin (Windows) ORACLE_HOME\network\admin
Add LDAP to the NAMES.DIRECTORY_PATH entry, as shown in the following example:
NAMES.DIRECTORY_PATH= (LDAP, TNSNAMES, ONAMES, HOSTNAME)
(UNIX) ORACLE_HOME/config/ias.properties (Windows) ORACLE_HOME\config\ias.properties
Change the SSLOnly parameter as follows:
SSLOnly=true
Save and close the file.
Restart the entire instance that contains Oracle Internet Directory:
On UNIX systems:
ORACLE_HOME/opmn/bin/opmnctl stopall ORACLE_HOME/bin/emctl stop iasconsole ORACLE_HOME/opmn/bin/opmnctl startall ORACLE_HOME/bin/emctl start iasconsole
On Windows systems:
ORACLE_HOME\opmn\bin\opmnctl stopall ORACLE_HOME\bin\emctl stop iasconsole ORACLE_HOME\opmn\bin\opmnctl startall ORACLE_HOME\bin\emctl start iasconsole
Task 3: Change jazn.xml (Oracle Internet Directory Security Provider Only)
If Oracle Internet Directory is the security provider for Application Server Control, you must make changes to jazn.xml for the instance that contains the active ascontrol application before you change that middle-tier instance to use SSL mode. (See Section 8.3.1 for information on determining the type of security provider used by Application Server Control.)
To make the changes, take the following steps for the instance that contains the active ascontrol application:
Edit the following file:
(Unix) ORACLE_HOME/j2ee/OC4J_InstanceName/config/jazn.xml (Windows) ORACLE_HOME\j2ee\OC4J_InstanceName\config\jazn.xml
Modify the location attribute to use the SSL port. For example:
location="ldap://myoid.us.oracle.com:636"
Modify the property value for ldap.protocol to be ssl. For example:
<property name=:ldap.protocol" value="ssl"/>
Save and close the file.
Task 4: Change Middle-Tier Instances to Use SSL Mode
In each middle-tier instance, run the Change Identity Management wizard and restart the instance:
Using the Application Server Control Console, navigate to the OC4J Home page for the middle-tier instance.
Click Administration.
In the Task Name column of the table, expand Security if it is not already expanded. Then, in the Identity Management row, click the Go to Task icon.
On the Identity Management page, click Change.
On the Change Identity Management page:
Oracle Internet Directory Host: Enter the fully-qualified name of the Oracle Internet Directory host.
Oracle Internet Directory User: Enter cn=orcladmin, or the distinguished name of a user in the iASAdmins group.
Password: Enter the password for the user.
This password will be used as the default password for the oc4jadmin user created in Oracle Internet Directory.
Use only SSL connections to the Internet Directory: Select this option.
Then, in the Oracle Internet Directory SSL Port field, enter the Oracle Internet Directory SSL port number.
Click OK.
When the operation is finished, you need to restart the OC4J instance. Do not click Restart on the Confirmation page. Instead, navigate to the Cluster Topology page, select the OC4J instance, and click Restart.
If you associated a 10g Release 3 (10.1.3) middle-tier instance with Release 2 (10.1.2) or Release 9.0.4 Identity Management Services, as described in Section 6.5, and you want to move Identity Management to a new host, follow the procedure in this section.
This procedure involves creating a replica (or copy) of the original Identity Management on a different host, along with its own new Metadata Repository, and then changing the middle-tier instance to use the new Identity Management.
See the Oracle Application Server Upgrade and Compatibility Guide for information about the specific versions of Oracle Identity Management that are supported with 10g Release 3 (10.1.3).
The following are sample uses for this procedure:
You have an existing Release 2 (10.1.2) or Release 9.0.4 Identity Management and associated Metadata Repository that is used by one or more 10g Release 3 (10.1.3) middle-tier instances. Your organization intends to replace the current Identity Management host with a new system. You can use this procedure to create a replica of the Identity Management, along with its own Metadata Repository, and change the middle-tier instances to use the new Identity Management. You can then retire the original host.
You want to create a failover environment for your Release 2 (10.1.2) or Release 9.0.4 Identity Management. You can use this procedure to create a replica of the current Identity Management, along with its own Metadata Repository. You can keep the replica running so it stays synchronized with the original Identity Management. You can perform regular exports of data in the original Metadata Repository and save them. In the event that you lose the original Identity Management, you can import the data to the new Metadata Repository, and change the 10g Release 3 (10.1.3) middle-tier instances to use the new Identity Management. Refer to Section 8.4.4, "Strategy for Performing Failover with This Procedure" for more information.
For both the original and new installations, the Identity Management and Metadata Repository can exist in the same Oracle home, or in separate Oracle homes (same or different host). If they are in separate Oracle homes, perform the operations on each in their own Oracle home.
For both the original and new installations, the Identity Management components (OracleAS Single Sign-On, Oracle Internet Directory, Delegated Administration Services, Directory Integration and Provisioning) may exist in the same Oracle home, or may exist in separate Oracle homes (same or different host). If they exist in separate Oracle homes, perform the operations on each in their own Oracle home.
This procedure does not take OracleAS Certificate Authority into consideration.
|
See Also: Oracle Application Server Certificate Authority Administrator's Guide for information on updating OracleAS Certificate Authority when changing Identity Management services |
This section describes how to move a Release 2 (10.1.2) or 9.0.4 Identity Management to a new host.
The following presents an overview of the procedure:
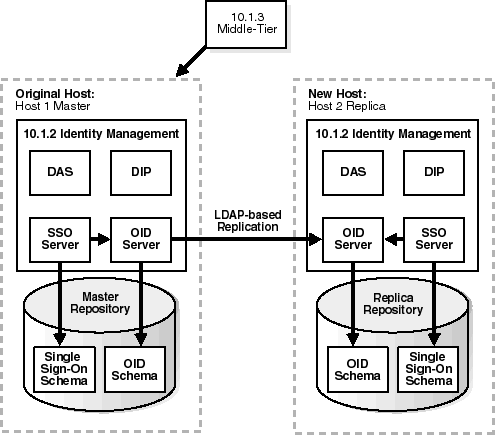
You have an original Release 2 (10.1.2) or 9.0.4 Identity Management (also called the Master) used by one or more middle-tier instances. The Identity Management has a Metadata Repository. You install and set up a new Identity Management (also called the Replica). This Identity Management has its own Metadata Repository. The Oracle Internet Directory in the new Identity Management is an LDAP-based replica of the original Oracle Internet Directory. Replication takes place constantly from the original Oracle Internet Directory to the new Oracle Internet Directory.
Figure 8-2 shows this setup with a Release 2 (10.1.2) Identity Management.
Figure 8-2 Original Host (Master) and New Host (Replica)
See: "Task 1: Install and Set Up the New Identity Management and Metadata Repository"
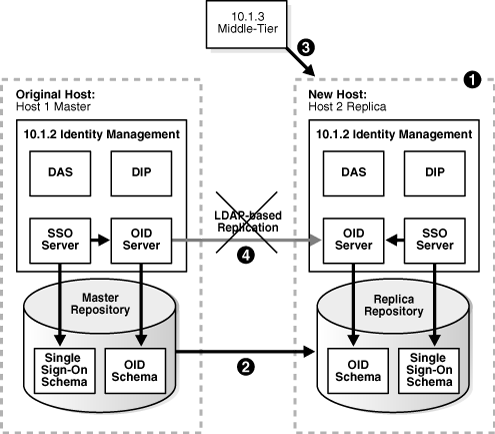
You migrate OracleAS Single Sign-On and Directory Integration and Provisioning data from the original Metadata Repository (Master) to the new Metadata Repository (Replica).
See: "Task 2: Migrate OracleAS Single Sign-On and Directory Integration and Provisioning Data"
You change the middle-tier instances to use the new Identity Management.
See: "Task 3: Change Middle-Tier Instances to the New Identity Management"
You stop the LDAP-based replication.
Figure 8-3 illustrates the steps described.
Figure 8-3 Changing from Original to New Identity Management
Task 1: Install and Set Up the New Identity Management and Metadata Repository
In this task, you install and set up the new Release 2 (10.1.2) or 9.0.4 Identity Management and its associated Metadata Repository. The new Identity Management is an LDAP-based replica of the original Identity Management.
Read Section F.1, "About LDAP-Based Replicas" to learn about LDAP-based replicas and how they are used for this procedure.
Follow the procedure in Section F.2, "Installing and Setting Up an LDAP-Based Replica" to install and set up the new Identity Management and Metadata Repository.
Task 2: Migrate OracleAS Single Sign-On and Directory Integration and Provisioning Data
In this task, you migrate the OracleAS Single Sign-On and Directory Integration and Provisioning Data from the original Metadata Repository to the new Metadata Repository. The source for the migration is the original Metadata Repository (Master) and the target for the migration is the new Metadata Repository (Replica).
This task contains the following subtasks:
Migrate the Directory Integration and Provisioning Data
|
Note: Make sure the ORACLE_HOME and ORACLE_SID environment variables are set before you begin. This applies to all platforms. |
Migrate the OracleAS Single Sign-On Data
To migrate the OracleAS Single Sign-On data:
Obtain the ORASSO schema password on the master:
MASTER_HOME/bin/ldapsearch -p master_oid_port -h master_host -D "cn=orcladmin" -w master_orcladmin_passwd -b "orclresourcename=orasso, orclreferencename=master_global_db_name, cn=ias infrastructure databases, cn=ias, cn=products, cn=oraclecontext" -s base "objectclass=*" orclpasswordattribute
This command prints the ORASSO password in a line similar to the following:
orclpasswordattribute=LAetjdQ5
Export the OracleAS Single Sign-On data from the master, ensuring that the ORACLE_HOME environment variable is set before you run this command:
MASTER_HOME/sso/bin/ssomig -export -s orasso -p master_orasso_passwd -c master_db_name -log_d $MASTER_HOME/sso/log
In the example, master_orasso_passwd is the ORASSO password obtained in the previous step.
Copy the ssomig.dmp and ssoconf.log files from the master to the replica, preserving the exact full path for each file.
Obtain the ORASSO schema password on the replica:
REPLICA_HOME/bin/ldapsearch -p replica_oid_port -h replica_host -D "cn=orcladmin" -w replica_orcladmin_password -b "orclresourcename=orasso, orclreferencename=replica_global_db_name, cn=ias infrastructure databases, cn=ias, cn=products, cn=oraclecontext" -s base "objectclass=*" orclpasswordattribute
Import the OracleAS Single Sign-On data to the replica:
REPLICA_HOME/sso/bin/ssomig -import -overwrite -s orasso -p replica_orasso_passwd -c replica_db_name -log_d $REPLICA_HOME/sso/log -discoforce
In the example, replica_orasso_passwd is the ORASSO password obtained in the previous step.
Verify that the export and import of OracleAS Single Sign-On succeeded.
Verify that the OracleAS Single Sign-On migration tool reported success. You can also check the following log files for errors:
MASTER_HOME/sso/log/ssomig.log REPLICA_HOME/sso/log/ssomig.log
|
See Also: Oracle Application Server Single Sign-On Administrator's Guide, Release 2 (10.1.2) for information on interpreting messages in the log files |
Migrate the Directory Integration and Provisioning Data
To migrate your Directory Integration and Provisioning Data:
|
See Also: Directory Integration and Provisioning Data documentation in the Oracle Internet Directory Administrator's Guide, Release 2 (10.1.2) for information about running the following commands using the HTTPS port in environments in which the Oracle Internet Directory HTTP port is disabled |
Stop the Directory Integration and Provisioning Data server on the master:
MASTER_HOME/bin/oidctl server=odisrv instance=1 stop
Migrate the Directory Integration and Provisioning Data:
MASTER_HOME/bin/dipassistant reassociate -src_ldap_host master_host -src_ldap_port master_oid_port -dst_ldap_host replica_host -dst_ldap_port replica_oid_port -src_ldap_passwd master_orcladmin_passwd -dst_ldap_passwd replica_orcladmin_passwd
This command prints log messages to:
MASTER_HOME/ldap/odi/log/reassociate.log
Stop the Directory Integration and Provisioning Data server on the replica:
REPLICA_HOME/bin/oidctl server=odisrv instance=1 stop
Register the Directory Integration and Provisioning Data server on the replica:
REPLICA_HOME/bin/odisrvreg -D "cn=orcladmin" -w replica_orcladmin_passwd -h replica_host -p replica_oid_port
Start the Directory Integration and Provisioning Data server on the replica:
REPLICA_HOME/bin/oidctl server=odisrv instance=1 flags="port=replica_oid_port" start
Task 3: Change Middle-Tier Instances to the New Identity Management
In each middle-tier instance, take the following steps:
Using the Application Server Control Console, navigate to the OC4J Home page for the middle-tier instance.
Click Administration.
In the Task Name column of the table, expand Security if it is not already expanded. Then, in the Identity Management row, click the Go to Task icon.
On the Identity Management page, click Change.
Follow the steps in the wizard for supplying the new Identity Management information. See Section 6.5 for more information.
When the operation is finished, you need to restart the OC4J instance. Do not click Restart on the Confirmation page. Instead, navigate to the Cluster Topology page, select the OC4J instance, and click Restart.
If you have a problem changing the middle-tier instances to the new host, check to make sure replication is running and try again.
Task 4: Stop Replication
Stop the replication between the original Identity Management and the new Identity Management (Replica) by running the following command in the new Identity Management Oracle home:
oidctl connect=global_db_name server=oidrepld instance=1 flags="-p oid_port" stop
In the example:
global_db_name is the global database name of the new Identity Management. (This is referred to as replica_db_name in Section F.2, "Installing and Setting Up an LDAP-Based Replica".)
oid_port is the non-SSL Oracle Internet Directory port in the new Identity Management.
As mentioned in Section 8.4.1, you can modify this procedure to perform failover for Identity Management. This enables you to move your middle-tier instances to the new Identity Management in case the original is lost.
Figure 8-4 Failover to New Identity Management
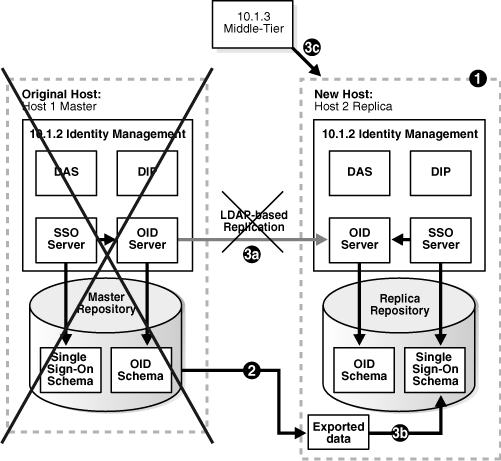
To set up the environment for failover:
Install and set up the new Identity Management as described in "Task 1: Install and Set Up the New Identity Management and Metadata Repository".
Export OracleAS Single Sign-On and Directory Integration and Provisioning data on a regular basis from the original Metadata Repository. You do not need to import the data into the new Metadata Repository. You only need to export the data and copy the files to the new Metadata Repository host. Refer to "Task 2: Migrate OracleAS Single Sign-On and Directory Integration and Provisioning Data".
If you lose the original Identity Management:
Stop replication, as described in "Task 4: Stop Replication".
Import your most recent copy of the OracleAS Single Sign-On and Directory Integration and Provisioning data into the new Identity Management repository. Refer to "Task 2: Migrate OracleAS Single Sign-On and Directory Integration and Provisioning Data".
Change the middle-tier instances to use the new Identity Management as described in "Task 3: Change Middle-Tier Instances to the New Identity Management".