| Oracle® Collaboration Suite Security Guide 10g Release 1 (10.1.2) Part Number B25494-10 |
|
|
View PDF |
| Oracle® Collaboration Suite Security Guide 10g Release 1 (10.1.2) Part Number B25494-10 |
|
|
View PDF |
Oracle Collaboration Suite is a secure and reliable communications solution that enables individuals and teams to communicate and work together using an integrated suite of applications. This chapter provides an overview of Oracle Collaboration Suite and discusses the security objectives and security architecture of Oracle Collaboration Suite. It contains the following topics:
Oracle Collaboration Suite is a messaging and collaboration system, with a standards-based integrated suite built on Oracle Database 10g. Oracle Collaboration Suite contains the following tiers:
Oracle Collaboration Suite Infrastructure provides centralized product metadata, security and management services, configuration information, and data repositories for the Applications tier. Oracle Collaboration Suite Infrastructure consists of the following tiers:
Oracle Collaboration Suite Database contains schemas for Oracle Application Server components, such as Oracle Internet Directory, OracleAS Single Sign-On, Oracle Wireless, and OracleAS Portal, and for Oracle Collaboration Suite components, such as Oracle Calendar, Oracle Mail, and Oracle Content Services. There can be one or several Oracle Collaboration Suite databases, each of which contains one or more sets of schemas, for Oracle Collaboration Suite and Oracle Application Server. This means that each database will contain either all the Oracle Application Server schemas or all the Oracle Collaboration Suite schemas. However, not every instance of each database will be used for each component. For example, if a customer deploys Oracle Mail in database DB1 and Oracle Content Services in database DB2, then each database contains schemas for all Oracle Collaboration Suite components, even though only one schema in each database is actually being used.
Oracle Internet Directory is a general-purpose directory service that enables fast retrieval and centralized management of information across distributed network resources. It combines Lightweight Directory Access Protocol (LDAP) Version 3 with the high performance, scalability, robustness, and availability features of Oracle Database 10g.
Oracle Internet Directory runs as an application on an Oracle Database. It communicates with the database by using Oracle Net Services, which is an operating system-independent Oracle database connectivity solution. The database may or may not be on the same host. Figure 1-1 illustrates this relationship.
OracleAS Single Sign-On enables you to use a single user name, password, and optionally, a realm ID, to access all the features of Oracle Collaboration Suite and other Web applications.
Nonadministrative users first gain access to the Single Sign-On server by entering the URL of a partner application such as OracleAS Portal. Entering such a URL invokes the single sign-on login screen. Once you have entered the correct user name and password, you can gain access to other partner applications and to external applications without having to provide your credentials again.
Administrative users can access the administration home page for single sign-on by typing a URL of the form:
http://host:port/pls/orasso
where host is the computer where the Single Sign-On server is located, port is the port number of the server, and orasso is the database access descriptor for the single sign-on schema. If the server is enabled for SSL, https must be substituted for http. If the port number is 80 or 443 (SSL), it may be omitted from the URL. These numbers are the defaults.
Accessing a Partner Application
Figure 1-2 shows what happens when you request the URL of a partner application that is protected by mod_osso. mod_osso is an Oracle module that examines incoming requests and determines whether the resource requested is protected.
When you try to access a partner application:
You are redirected to the Single Sign-On server. The server prompts you to enter your credentials. After verifying these credentials in Oracle Internet Directory, the server passes these credentials on to the partner application.
The application serves the requested content.
Oracle Collaboration Suite Applications consists of the following components:
Oracle Calendar
Oracle Content Services
Oracle Mail
Oracle Mobile Collaboration
Oracle Real-Time Collaboration
Oracle Voicemail & Fax
Using these integrated application components, you can manage cross-suite business processes. Because Oracle Collaboration Suite is standards-based and not client-dependent, you can access it through any standards-based access method.
|
See Also: Oracle Collaboration Suite Concepts Guide for more information about the various components of Oracle Collaboration Suite |
The security objectives of Oracle Collaboration Suite are based on the range of operational environments and risk scenarios in which Oracle Collaboration Suite may be deployed. The security objectives are:
Oracle Collaboration Suite provides the following security services required in a multiuser, networked environment:
This service enables a system to verify the identity of users who request access to services or data. Authentication is a prerequisite for other security services, such as access control, authorization, and accountability.
Authorization and Access Control
Authorization ensures that a system grants access to resources in compliance with the security policies defined for those resources. Access decisions are based on the authenticated identity and the privileges given to the requesting user.
Accountability and Intrusion Detection
Accountability ensures that users who access the system can be held accountable for their usage of the system and system resources. This enables you to monitor system usage to identify unauthorized users. Intrusion detection services are similar to accountability services, but they also detect and react to unauthorized usage, including unauthorized usage by authorized users, in real time.
Data Protection
This service prevents unauthorized users from accessing sensitive data. You can protect the confidentiality of data sent through a public network by using encryption. You can also use encryption to protect highly sensitive data from users who bypass access control mechanisms of a system.
Oracle Collaboration Suite is based on open standards. It complies with the J2EE framework and supports standard protocols, such as HTTP, and markup languages, such as HTML and XML. Oracle Collaboration Suite security services also comply with relevant standards, facilitating interoperability with third-party products. For example, most Oracle Collaboration Suite applications support browser-based clients. Oracle Collaboration Suite supports security standards, such as SSL and X.509v3, which these browsers implement.
Oracle Collaboration Suite security services are designed to support the full range of product deployment options. Security mechanisms in Oracle Collaboration Suite are aimed at ensuring that practical, real-world constraints on deployment can be met. These constraints include the need to deploy certain components of Oracle Collaboration Suite in the Demilitarized Zone (DMZ), others in the corporate intranet, and enable those components to communicate across a firewall.
As systems grow in size, there will be a breaking point where an entire, new, expensive server is required because of the overall workload. With Oracle Collaboration Suite, adding resources to the servers will smooth the breaking point because the entire system is designed from the ground up to be deployed on multiple computers. This allows Oracle Collaboration Suite to serve even the largest organizations.
Oracle Collaboration Suite can also scale out to include very large data volumes, with database sizes in excess of 5 terabytes common in implementations, because it is based on Oracle Database 10g.
Oracle Collaboration Suite provides rational IT planning by consolidating servers, making it easy to plan for storage, networking, backup, and other key requirements, and reducing costs in the process.
Figure 1-3 illustrates the elements of the Oracle Collaboration Suite security architecture.
Figure 1-3 Oracle Collaboration Suite Security Architecture
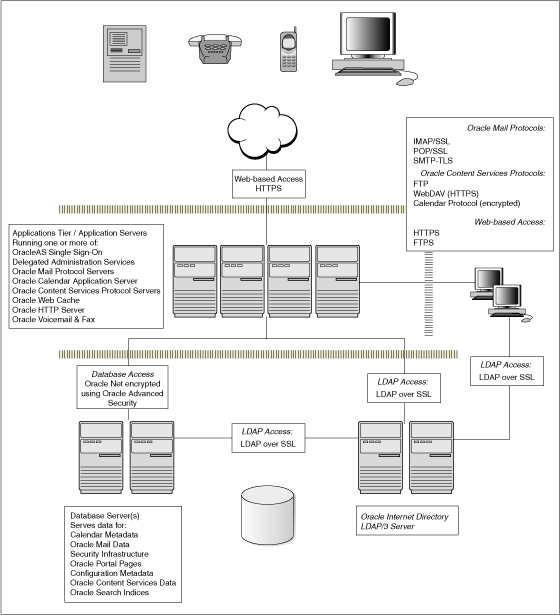
Oracle Collaboration Suite provides a solid framework for building and deploying Web applications by using the Apache-based Oracle HTTP Server, Oracle Application Server Containers for J2EE (OC4J), and OracleAS Portal, which use the advanced security functionality provided by Oracle Collaboration Suite Infrastructure. Oracle Collaboration Suite Infrastructure consists of Oracle Application Server Metadata Repository and Oracle Identity Management.
Oracle Collaboration Suite security starts from the Web security services provided by Oracle HTTP Server, adds a comprehensive set of Web single sign-on services, and extends them further with centralized user provisioning that is available in Oracle Internet Directory.
Secure Sockets Layer (SSL) is an industry-standard protocol for securing network connections. SSL uses RSA public key cryptography in conjunction with symmetric key cryptography to provide authentication, encryption, and data integrity features. This section contains the following topics:
Although SSL was primarily developed by Netscape Communications Corporation, the Internet Engineering Task Force (IETF) took over development of it and renamed it Transport Layer Security (TLS). Essentially, TLS is an incremental improvement to SSL version 3.0.
When you start a network connection over SSL, the client and server perform an SSL handshake. This process includes the following steps:
The client and server establish which cipher suite to use and which encryption algorithm to use for data transfers.
The server sends its certificate to the client, and the client checks whether the certificate of the server is signed by a trusted certificate authority (CA). A Certificate Authority (CA) is a trusted third party that certifies the identity of entities such as users, administrators, clients, and servers. If client authentication is required, then the client sends its own certificate to the server, and the server verifies whether the certificate of the client is signed by a trusted CA.
The client and server exchange information using public key cryptography. Based on this information, each generates a session key. All subsequent communications between the client and the server is encrypted and decrypted by using this set of session keys.
The authentication process consists of the following steps:
On the client, you initiate an Oracle Net connection to the server by using SSL.
The client and the server perform the SSL handshake.
If the handshake is successful, then you can transfer the data across the network.
A Public Key Infrastructure (PKI) is a set of network components that provide security based on trust assertions for the entire organization. PKI enables disparate network entities to access security services, which use public key cryptography, on an as-needed basis.
This section presents the following basic concepts of PKI:
Table 1-1 describes the security features of PKI:
Table 1-1 Security Features of PKI
| Feature | Explanation |
|---|---|
| Authentication | The importance of authentication, verifying the identity of users and computers, becomes crucial when an organization opens its doors to the Internet. Strong authentication mechanisms ensure that users and computers are the entities they claim to be. |
| Encryption | Encryption algorithms are used to secure communications and ensure the privacy of data sent from one computer to another. |
| Nonrepudiation | PKI can be used to provide nonrepudiation through digital signatures. This proves that a specific user performed certain operations at a given time. |
Together, these features can be combined to provide a secure environment for deploying e-commerce. Such an environment can support any type of electronic transaction, from corporate intranets to Web-based e-business applications.
The following advantages of PKI have led to its emergence as an industry standard for securing e-commerce applications:
Standards-based technology.
Enables you to select the trust provider.
Highly scalable.
Users maintain their own certificates, and certificate authentication involves exchange of data between client and server only. This means that no third-party authentication server needs to be online.
Enables delegated trust.
Users who have obtained certificates from a recognized and trusted certificate authority can authenticate themselves to a server the very first time they connect to that server, without having previously been registered with the server.
Although PKI is not a single sign-on service, it can be implemented in such a way as to enable single sign-on.
PKI components include the following:
When an entity requests certification, the CA verifies its identity and grants it a certificate, which is signed with the private key of the CA.
Different CAs may have different identification criteria. Some CAs may verify a requester's identity with a driver's license or the requester's fingerprints, and some may require that requesters have their certificate request form notarized.
The CA publishes its own certificate, which includes its public key. Each network entity has a list of trusted CA certificates. Before communicating with each other, network entities exchange certificates and check whether the other's certificate is signed by one of the CAs on their respective trusted CA certificate lists.
Network entities can obtain their certificates from the same or different CAs. By default, when you create a wallet, Oracle Advanced Security automatically installs trusted certificates from VeriSign, RSA, Entrust, and GTE CyberTrust. A wallet is a container that is used to store authentication and signing credentials, including private keys, certificates, and trusted certificates needed by SSL.
When a network entity receives a certificate, it verifies that it is a trusted certificate, that is, one that has been issued and signed by a trusted certificate authority. A certificate remains valid until it expires or until it is revoked.
A certificate is created when an entity's public key is signed by a trusted CA. A certificate ensures that an entity's identification information is correct and that the public key actually belongs to that entity.
A certificate contains the entity's name, public key, and an expiry date, a serial number and certificate chain information. It might also contain information about the privileges associated with the certificate.
A certificate issued by a CA is valid only for a specified period of time. However, certain events, such as user name changes or compromised private keys, can render a certificate invalid before the validity period expires. When this happens, the CA revokes the certificate and adds its serial number to a Certificate Revocation List (CRL). CAs periodically publish CRLs to inform the users about invalid certificates.
In an Oracle environment, when a server or client receives user certificates, it can validate the certificate by checking the expiry date, signature, and revocation status. The certificate revocation status is checked by validating the status against published CRLs. If certificate revocation status checking is enabled, then the server searches for the CRL depending on how this feature has been configured. The server searches for CRLs in the following locations:
Local file system
Oracle Internet Directory
CRL Distribution Point
In an Oracle environment, every entity that communicates over SSL must have a wallet containing an X.509v3 certificate, a private key, and a list of trusted certificates.
You can use Oracle Wallet Manager to perform the following:
Generate a public and private key pair and create a certificate request
Store a user certificate that matches with the private key
Configure trusted certificates
Security administrators use Oracle Wallet Manager to manage security credentials on the server. Wallet owners use Oracle Wallet Manager to manage security credentials on clients.
Cryptographic information can be stored on two types of hardware devices:
Hardware boxes on the server side
Smart card readers on the client side
An Oracle environment supports hardware devices using Application Programming Interfaces (APIs) that conform to the RSA Security Inc., Public Key Cryptography Standards (PKCS) #11 specification.
Public key cryptography requires that entities that want to communicate in a secure manner should possess certain security credentials. These security credentials are stored in a wallet. Security credentials consist of a public and private key pair, a user certificate, a certificate chain, and trusted certificates.
The secrecy of encrypted data generally depends on the existence of a secret key that is shared between the communicating parties. Providing and distributing such secret keys is one aspect of key management. In a multiuser environment, secure key distribution may be difficult. Public key cryptography was invented to solve this problem.
Public key cryptography is based on a secure key pair. Each key, one half of the pair, can only decrypt information encrypted by its corresponding key. A key pair includes:
A private key, which is known only to its owner
A public key, which is associated with its owner but distributed widely
Use of the cryptographic key pair to set up a secure, encrypted channel ensures the privacy of the message passing through the channel and validates the authenticity of the sender of the message. It also enables distributing the public key on a server, or in a central directory, without putting at risk the integrity of the private key component of the key pair. This eliminates the need to transmit the public key to every user in the system.
Each entity in a public key system must have a public and private key pair. The public key for an entity is published by a CA in a user certificate. Entities that want to send secure information to this entity can encrypt the information with the public key of the recipient entity. A public key can also enable the receiving entity to validate the organizational affiliation of the sending entity.
Establishing user identity is of primary concern in distributed environments. Otherwise, there can be little confidence in limiting privileges by user. The use of passwords is the most common authentication method, but to protect highly sensitive data, you need to employ strong authentication services. This section describes the authentication methods that can be used with PKI.
The authentication methods that are used with PKI include:
SSL provides authentication through the exchange of certificates that are verified by trusted certificate authorities. SSL uses digital certificates (X.509v3), and a public and private key pair to authenticate users and systems.
PKI relies on X.509 certificates, also called digital certificates, or public-key certificates, for public-key authentication. The most widely used public-key certificates comply with the X.509 format. The X.509v3 certificate is the current industry standard format.
X.509v3 digital certificates contain the following:
The certificate owner's distinguished name (DN), which uniquely identifies the owner
The DN of the certificate issuer, which uniquely identifies the certificate authority
The certificate owner's public key
The issuer's signature
The date up to which the certificate is valid
The serial number of the certificate
Entrust Technologies, Inc. provides PKI solutions through their Entrust/PKI software. Entrust/PKI includes products, such as Entrust Profile, which secures user PKI credentials, and Entrust Authority, Entrust's CA product. Oracle Corporation has modified its SSL implementation so that it integrates with Entrust/PKI.
With PKI, secure credentials such as digital certificates can be stored in wallets. A wallet is a transparent database used to manage authentication data such as keys, certificates, and trusted certificates needed by SSL. Wallets can be stored in an LDAP-compliant directory. This implementation enables you to centrally manage users.
This section describes recommended architectures for deploying Oracle Collaboration Suite products to secure Internet access.
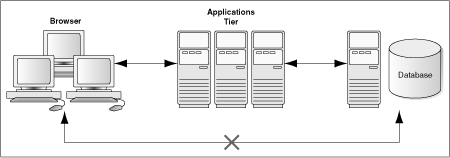
The simplest deployment architecture is the one shown in Figure 1-4. This single-computer deployment may be cost effective for small organizations, however it provides high availability because all components are stored on the same computer.
The general architectural recommendation is to use the well-known and generally accepted Internet-Firewall-DMZ-Firewall-Intranet architecture shown in Figure 1-5.
|
Note: The term demilitarized zone (DMZ) refers to a server that is isolated by firewalls from both the Internet and the intranet, thus forming a buffer between the two. |
Firewalls separating DMZ zones provide two essential functions:
Blocking any traffic types that are known to be illegal
Providing intrusion containment, should successful intrusions take over processes or processors
Small organizations that cannot invest huge amounts on firewalls can opt for the architecture in Figure 1-6.
Figure 1-6 Deployment Architecture for Small Organizations
In addition to enhanced security requirements, Internet-accessible applications often have much higher scale and availability requirements than do intranet-only applications. Internet applications may be accessed by thousands of times more users, while requiring 24x7 operation to accommodate worldwide access. In response to these requirements, hardware load balancers have been developed to meet both the scale and high availability requirements of Internet-accessible applications.
Hardware load balancers provide both scalability and high availability and are highly recommended when either of these requirements exists. Because load balancers and HTTPS-to-HTTP appliances are required in a high percentage of production sites, they are described in this chapter.
Generally, load balancers are needed only in front of OracleAS Web Cache, non-cached HTTP servers (including the OracleAS Single Sign-On Web server), and Oracle Internet Directory processes. This is because the Oracle infrastructure provides high scalability and high availability elsewhere.
Load balancers are often used with or contain HTTPS-to-HTTP protocol-converting appliances. These devices can be purchased from a number of vendors and can achieve rates of thousands of SSL key exchange sessions per second or higher. (By comparison, 500MHz Intel/UNIX systems can achieve only 20-30 SSL key exchanges per second, 60-90 exchanges if cryptography accelerator boards are used.) Oracle recommends HTTPS-to-HTTP protocol converting devices. Without these devices, as much as two-thirds of the CPU of a site's HTTP CPU cycles can be consumed by SSL operations.
|
Note: We can use HTTPS tunneling with OracleAS Web Cache only if OracleAS Web Cache is installed on the local Applications tier. |
Compliance is the process of adhering to a set of established guidelines or rules established by external bodies such as government agencies or by internal corporate bodies. Regulatory compliance has gained increasing attention both due to the number and complexity of regulations that must be addressed and the cost of noncompliance. Through a combination of regulatory changes and increased public awareness of corporate behavior, the cost of noncompliance has dramatically increased. Steep fines, possible jail time for executives, damage to brand reputation, negative impact on stock price or even de-listing from stock exchanges, and risk of shareholder lawsuits are only a few of the possible consequences of compliance failures today.
One of most significant risk management challenges pertains to unstructured content such as electronic documents, e-mail, instant messages, and paper documents. While most businesses keep their financial, employee, or customer records in a secure database, unstructured content that often contains critical information supporting these records is scattered across hundreds or even thousands of minimally secure file and e-mail servers. This section describes how to manage unstructured content in Oracle Collaboration Suite and contains the following topics:
Most organizations store data, for example Personally Identifiable Information (PII), as structured elements in a database. However, unstructured content represents over 80% of all data in an organization, and most companies have a difficult task of getting this data under consistent control. Unstructured content is often the result of collaboration or interactions between employees and customers and may contain information, such as PII. Unstructured content can also consist of scanned paper records such as purchase orders and contracts, which also may contain PII, for example.
Unstructured content is scattered across multiple e-mail and file servers and on desktops and laptop computers. Unlike the records managed in the database, unstructured content is typically not well organized, not easily found, and controlled only under ad hoc security and access control policies. Organizations will need to carefully assess whether the unstructured content repositories contain any information, for example PII, that puts the organization at risk.
Oracle Collaboration Suite provides e-mail, document management, calendar, voicemail and fax, Web conferencing, and wireless access on one integrated platform that allows customers to consolidate unstructured content onto a single database infrastructure.
Gaining Control Over Unstructured Content
When content is scattered across hundreds of servers, meeting the common requirements for compliance and legal risk management becomes a difficult task. This is largely due to a phenomenon known as server drift. In response to the rapid proliferation of information, individual departments and workgroups often set up their own servers. While this is a reasonable way to address immediate localized needs, it also means that IT departments lose control of these servers and, therefore, cannot manage them effectively. Rapid, reliable access to content is complicated by issues, such as not knowing which server the content stored on, what kind of server it is, what version of software the server is running, or even whether the server and its content exist.
In addition, establishment of consistent management policies with regard to such critical activities as folder organization, retention and disposition management, secure access control, action tracking and logging, and even backup planning becomes virtually impossible.
Oracle Records Management is a records management application that ships with Oracle Content Services. Records Management Administrators can use Oracle Records Management to set records management properties for folders, including record declaration and policy management properties.
Because Oracle Records Management enables universal access to a single records management policy and repository through Web services, it can be used in a variety of collaborative environments, portals, and business applications.
Oracle Records Management identifies and selects data, and creates records from that data in two ways:
Manual Record Creation: Explicitly declaring that the identified data is a record. The user browses the file plan and selects a record category to apply to the data. The data is declared a record and is managed by the management policy for that record category.
Enforced Record Creation: Enforcing the records management properties of a record category or a records folder to an Oracle Content Services folder. All subsequent data or documents uploaded to that folder will automatically be declared as records, subject to the applied records management properties.
Using Oracle Records Management, enterprises can do all of the following:
Declare records: Records can be declared manually, automatically, or programmatically through Web services. Once a record has been declared, the records management policy controls the disposition of the document.
Delete records: Records Management Administrators can configure Oracle Content Services to conform to the records management retention policy for their enterprise, which then automatically retains or deletes appropriate records.
Manage records management policy: File plans control the operating restrictions on records. The records management policy creates the file plan operating hierarchy and manages operations applied to records, such as establishing cutoff and retention periods, record disposition, record freezes, and record searches.
When Oracle Content Services is installed, Oracle Records Management is installed automatically, but the application is disabled by default. See Oracle Content Services Administrator's Guide for information about how to enable Oracle Records Management. See Oracle Records Management Administrator's Guide for more information about how to use Oracle Records Management.
The most important preventive measure that organizations can implement when using Oracle Collaboration Suite is a comprehensive corporate policy and employee education on the use of electronic communication systems and unstructured data containing important information, for example PII. Other preventive measures include access controls. Oracle recommends using Oracle Internet Directory to manage and provision all users of Oracle Collaboration Suite. The preventive measures for the components of Oracle Collaboration Suite are:
Oracle Mail
Use server-side rules to implement filters that can retain e-mail with certain risk words such as Social Security Number.
Educate users on the appropriate use and security implications of using e-mail.
Oracle Content Services
Implement a company policy to ensure that users never store confidential files in public workspaces and only add users to workspaces on a need-to-know basis.
Use the administrator search functionality to proactively search for documents containing risk words
Oracle Real-Time Collaboration
Ensure that users notify conference participants when a conference is recorded.
Ensure that every conference is protected by an adequate password.
Ensure that users never reveal confidential information, PII for example, in Web conferencing chat.
Ensure that users are trained on appropriate usage of language in instant messaging.
When deploying Oracle Messenger, ensure that the default setting does not turn on instant message archiving on the user desktop. Instead, you may consider creating a server-side message archive, if required by your records retention policy.
Ensure that users only turn on Oracle Messenger archiving in accordance with your records retention policy.
Oracle Collaboration Suite contains many additional security and auditing features that will help companies investigate breaches involving information stored in unstructured content. Oracle recommends that organizations carefully assess their collaborative environment to find an adequate balance between useful collaboration and carefully managing the risk from noncompliance.