| Oracle® Access Manager Identity and Common Administration Guide 10g (10.1.4.0.1) Part Number B25343-01 |
|
|
View PDF |
| Oracle® Access Manager Identity and Common Administration Guide 10g (10.1.4.0.1) Part Number B25343-01 |
|
|
View PDF |
The User Manager, Group Manager, and Organization Manager are Identity System applications that enable end users to view and modify information about themselves, other people, groups, inventory, and any other item that you, the administrator, choose to make available.
The chapter on "Making Schema Data Available to the Identity System" describes how to make the Identity System aware of objects and attributes in your directory and in object template files, and how to configure the way that attributes are displayed on an application page. This chapter explains how to place attributes on specific application pages, and how to enable users to view and modify them. This chapter also touches on end use of these applications. You must be a Master Identity Administrator or Delegated Identity Administrator to configure the User Manager, Group Manager, and Organization Manager applications. See "Delegating Administration".
This chapter covers the following topics:
The User, Group, and Organization Manager are the primary Identity System applications:
People use the User Manager to view information about their identity, to modify information such as their home phone number, and to find information on other people.
People use the Group Manager to view groups, subscribe to groups, and to manage group subscriptions.
People use the Organization Manager to manage other objects.
Popular uses of the Organization Manager include viewing organization maps and searching for inventory items.
You control who is allowed to see what attributes and values on these applications. You also control what portion of the directory tree is accessed when users conduct searches. You can add filters so that when users search, the results conform to criteria specified on the filters.
When you first install, set up, and configure objects and attributes in the Identity System, the Identity System application pages are empty. You make information available on an Identity System application as follows.
Task overview: Displaying information on an application
Configure the objects and attributes to be used by the Identity System applications, as described in "Making Schema Data Available to the Identity System".
Configure the Identity System application pages, or tabs, as described in "Configuring Tabs".
Configure profile pages on each tab by arranging groups of attributes into panels, as described in "Configuring Tab Profile Pages and Panels".
Optionally, set the searchbase to control what portion of the directory tree is included in a search for LDAP attributes only, as described in "About the Searchbase".
Set permissions for users to view and modify the attributes you are displaying on the application tabs, as described in "About View and Modify Permissions" for details.
The Identity System applications each have one or more tabs, which are configured as follows:
When you work with the Group Manager Configuration tab in the Identity System Console, you are configuring the My Groups tab in the Group Manager application.
Similarly, the User Manager Configuration tab in the Identity System Console is used to configure the My Identity tab in the User Manager application.
Unlike the User Manager and the Group Manager, you can configure multiple tabs in the Organization Manager.
When you install the Identity System, a default structural object class Location is defined for the Organization Manager. The Organization Manager can manage objects defined in the Identity System as having a Generic or Location data type. See "Object Class Types" for details.
The tab in the User Manager is associated with the person structural object class. The tab in the Group Manager is associated with the group structural object class. The Organization Manager can have multiple tabs, each associated with a different object class. All tabs may have auxiliary LDAP object classes and template object classes associated with them.
You can view and modify characteristics of the tabs that are displayed on the User, Group, and Organization Manager pages.
To view or modify tab configuration information
Navigate to the Identity System Console and click User, Group, or Org. Manager Configuration.
The User, Group, or Organization Manager Configuration page appears.
Click Tabs.
The Configure Tab page appears, showing the name of the tab for the application. The Organization Manager may have more than one tab. 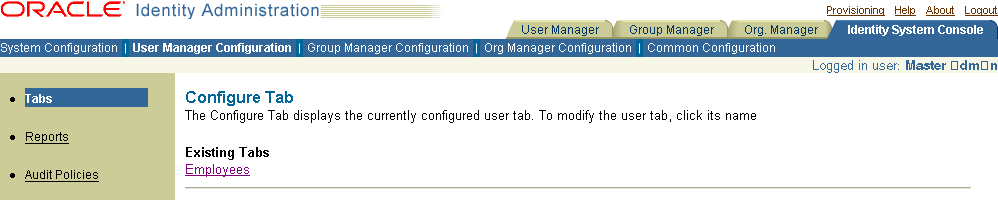
Click the link for the tab.
Since there is only one tab for User Manager and Group Manager, there can only be one link. For Organization Manager, there can be more than one tab.
The View Tab page appears.
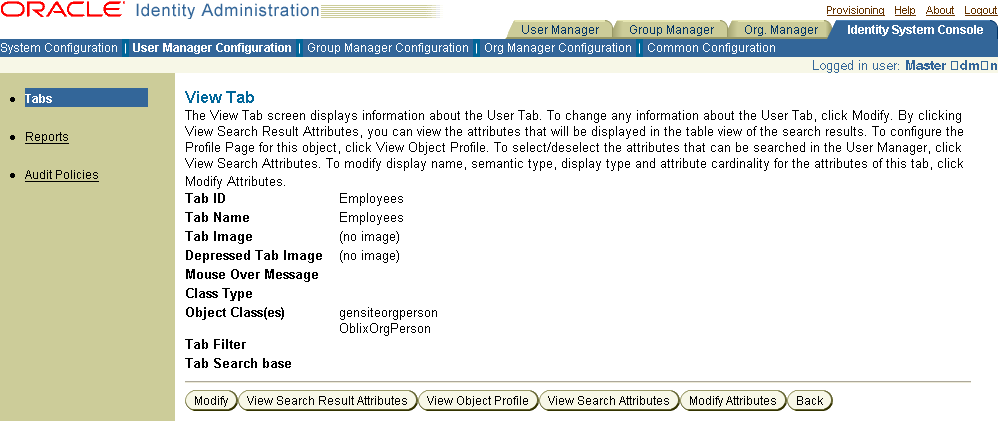
Table 4-1 describes the information on this page:
Table 4-1 Tab Information
| Field | Description |
|---|---|
|
Tab ID |
Unique identifier for the tab. |
|
Tab Name |
The name displayed on the application tab.You can localize this field. |
|
Tab Image |
GIF image for the tab. The GIF must be stored in WebPass_install_dir/identity/oblix/lang/langTag/style0 where WebPass_install_dir is the directory where you installed WebPass and langTag is the folder that contains the specific language that you are using.Enter only the name of the GIF file, not the full path. |
|
Depressed Tab Image |
GIF image displayed when a user clicks the tab image. |
|
Mouse Over Message |
Text displayed when the user passes the cursor over the tab.You can localize this field. |
|
Class Type |
The type associated with the structural class for this tab. See "Object Class Types" for details. |
|
The structural, auxiliary, and template object classes used by this tab. Template object classes are shown in fully qualified format, for example, miis.person. The format is read from the .tpl file where the class is defined. See "Sending Non-LDAP Data to External Applications".You cannot change the structural object class through Identity System Console. You can associate auxiliary object classes with the structural object class, as described in "Adding Auxiliary and Template Object Classes to a User or Org. Manager Tab".Note that some object classes may appear in a non-editable list on this page, and other object classes may appear in a text box on this page. The object classes in the text box have not yet been added to the tab. |
|
|
An LDAP filter that queries the directory and returns objects qualified by the filter. For examples of the types of LDAP filters you can write, see "Static LDAP Search Filters" and "Examples of Dynamic LDAP Search Filters". Tab filters do not support filter substitution. Tab filters affect searches, viewing and modifying profiles, and creating reports on the tab. The filter is used in an "and" relationship (with criteria specified during a search) and when creating reports. That is, the criteria from both the filter and the search are applied. View and modify operations use this filter to qualify the target object. |
|
|
Tab Searchbase |
Starting point in the directory tree (DIT) for user searches. See "About the Searchbase" for details. |
Click Modify.
Make the desired changes and click Save.
If you do not see your changes reflected in the Identity System application, go to Identity System Console, System Configuration, View Server Settings, and click Clear Cache to flush and reload the cache.
If you have installed more than one language pack, you can localize tab names to display them in those languages. You create, view, and modify localized tab names in the Administration Console.
See "Configuring Multiple Languages for Oracle Access Manager" for information on managing multiple languages.
|
Note: The Translate button appears only if more than one language has been installed. |
To create, view, and modify localized tab configuration
Log in to the Identity System Console and click User Manager Configuration (or Group Manager Configuration or Org. Manager Configuration).
The User, Group, or Organization Manager Configuration page appears.
Click the Tabs link in the left navigation pane.
The Tab page appears, showing the name of the tab or tabs for the application.
Click the link to an existing tab to view its details.
The View Tab page appears. Tab details such as the ID, name, class type, and object classes are displayed on this page.
Click Translate.
If this button does not appear on the page, you have only one language installed and you cannot localize the display names. Click Modify to change the display name for the single language that you have installed.
The Summary of Tab Label Display Names page appears. Display names, if any, that have been configured for the following language-specific fields appear on the page:
Tab Name
Mouse Over Message
Display names that have not been configured for a particular language are marked as Not Configured.
Click Modify to enter a tab display name or to modify an existing one.
The Tab Display Names page appears. This page contains fields for the tab display names and links for all the installed languages.
Click the language for which you want to localize the tab.
Enter the display names in the Tab Name and Mouse Over Message fields.
Click Save to save your changes.
The Organization Manager can contain more than one tab.
From the Identity System Console, click Org. Manager Configuration, then click Tabs.
The Configure Tabs page appears.
Click Add.
The Create Tab page appears.
Complete the fields in this page, as described in "Viewing and Modifying Tab Configuration Information".
Click Save.
At the top of the application page for the User Manager, Group Manager, and Organization Manager there are search fields. See "Adding Auxiliary and Template Object Classes to a Group Tab" for an example. You specify the attributes that you want to appear in the search function list. Note that search attributes can only be taken from an LDAP directory. Template attributes cannot be used as search attributes.
|
Note: You must configure attributes before they can appear on a tab. For more information, see "About Object Class Attributes". |
To specify what attribute can be used in a search
From the Identity System Console, click User Manager Configuration (or Group Manager Configuration or Org. Manager Configuration), and click the Tabs link in the left navigation pane.
Click the link for the tab.
Click View Search Attributes.
The View Search Attributes page appears.
Click the Modify button.
Select an attribute check box to make the attribute searchable.
Click Save.
You choose what attributes are to appear in the results of a search. If you have installed and configured multiple languages, you can localize search result attributes. This enables you to display search results in multiple languages.
To view the search result attributes
From the Identity System Console, click User Manager Configuration (or Group Manager Configuration or Org. Manager Configuration).
Click the Tabs link in the left navigation pane
Click the link for the tab.
Click View Search Result Attributes.
The View Search Result Attributes page appears.This page shows the attributes that appear when the results of a user's search are displayed. If you have configured the Identity System for more than one language, those languages are displayed on the page.
Click Modify to change the attributes.
The Modify Search Result Attributes page appears.
The first attribute is always the Class Attribute.
You cannot modify the class attribute Name from this page. It is displayed in bold and is not editable on this page. If you want to modify a class attribute, see "Selecting a Class Attribute" for details.
From the attribute lists, select new attributes for each search field you want to change.
The attribute's Display Name appears in the editable field to the right of the attribute list. This name appears in the Identity System user application. See "About Object Class Attributes" for details.
Click Add if you need additional attribute fields.
Click Save.
In the Identity System console, select User Manager Configuration (or Group Manager Configuration or Org. Manager Configuration).
In the left navigation pane, click Tabs then click a link.
The View Tab page appears.
Click View Search Result Attributes to display the View Search Result Attributes page.
Click Translate.
|
Note: The Translate button appears only if more than one language has been installed. |
The Summary of Search Results Attribute Display Names page appears. Existing display names in all the locales are listed on this page. Display names that have not been configured for a language are marked as Not Configured.
Click Modify to configure a display name for a language.
The Search Results Attribute Display Names page appears.
Click the language for which you want to configure a display name.
Enter the name in the Display Name field.
Click Save to save your changes.
You can use auxiliary object classes as mix-ins with structural object classes. For instance, if you have an auxiliary class for a person, and the auxiliary contains an attribute for the person's badge number, you might want to associate this auxiliary class with your structural object class. When you configure the User Manager, Group Manager, and Organization Manager applications, the more object classes you have at your disposal, the more information you can configure for users of those applications.
If you have created workflows as described in "Chaining Identity Functions Into Workflows", there are issues when associating an auxiliary object class with a tab:
If the tab has associated workflows with pending requests, you cannot attach an auxiliary object class.
If the auxiliary object class you are attempting to attach has any required attributes, you must edit all associated workflows to include those attributes.
You can also associate template objects with a tab. This is required if you plan to configure a workflow that makes use of the template object.
|
Note: You cannot remove an auxiliary object class you have added to a User Manager or Organization Manager tab. In Group Manager, under Group Types, you can remove an auxiliary class. |
To add an auxiliary or template object class to a User or Org. Manager tab
Ensure that you have configured the object class that you want to add in the Common Configuration tab.
See "Adding Object Classes" for details.
From the Identity System Console, select User Manager Configuration (or Org. Manager Configuration), and click Tabs.
The Tab page appears.
Click the link for the tab.
The View Tab page appears.
Click Modify.
The Modify Tab page appears.
In the menu on the far right of the Object Class(es) label, select an auxiliary or template object class or classes to associate with the tab.
Click Save.
The select object class or classes are added to the list on the left of the selection box when you save your changes.
Use Group Types to associate auxiliary object classes with the Group Manager. Oracle Access Manager provides the oblixAdvancedGroup auxiliary object class to enable you to configure attributes for subscribing members to groups, and for creating and expanding dynamic groups.
The following shows page that appears when you click the Group Manager tab and then click the My Group sub-tab. My Groups has been configured with multiple group type panels.
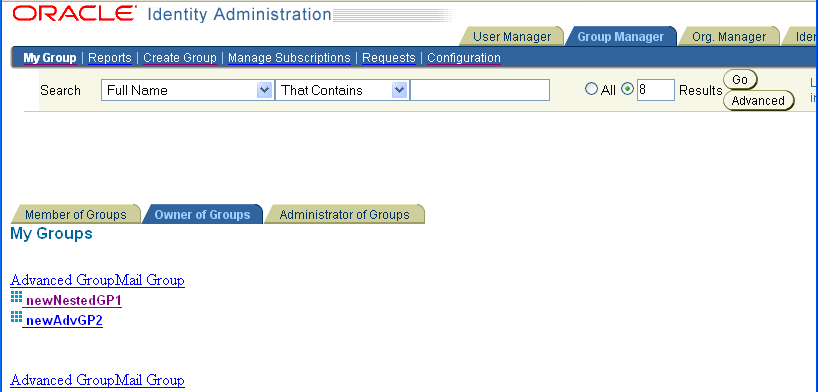
When you create a Group Type panel, the attributes from the associated object class are available in the Group Manager user application.
To add auxiliary and template object classes to the Group Manager
Ensure that you have configured the object class or classes that you want to add in the Common Configuration tab.
See "Adding Object Classes" for details.
From the Identity System Console, select Group Manager Configuration, then click Configure Group Type.
Click Configure Group Type Panels, then click Create.
In the topmost menu, select the object class that you want to add.
In the Panel Label field, enter the label that you want to display to end users when they view elements from this object class in the Group Manager.
Select the Panel Information Is Complete check box.
Click Save.
The object class is added. You can view this new object class by clicking the Tabs link in the left navigation pane for Group Manager Configuration.
To delete auxiliary and template object classes from the Group Manager
From the Identity System Console, select Group Manager Configuration, then click Configure Group Type.
Click Configure Group Type Panels.
Click the link for the group type that you want to delete.
Click the Delete button.
Use the Group Manager Options feature to select what users see in the My Groups and View Members Profile pages of the Group Manager application. This feature enables you to turn off expensive operations. This can be useful if you need to enhance Identity System performance.
To select what users see in My Groups and View Member Profiles
From Identity System Console, click Group Manager Configuration, and click Group Manager Options.
The Group Manager Options page appears.
Click Modify to display the Modify Group Manager Options page.
Table 4-2 describes each option.
Table 4-2 Group Manager Options
| Option | Description |
|---|---|
|
Displays or hides groups consisting of individual members. Applies to the My Groups page. |
|
|
Displays or hides groups containing individual members and other groups. Applies to the My Groups page. |
|
|
Displays or hides groups with members that are determined by a filter. Applies to the My Groups page. |
|
|
Displays the Member of Groups attribute on the My Groups page. You must also enable the Show static group, Show nested group, and Show dynamic group options to enable this function. |
|
|
Show groups you are an owner of |
Makes the Owner of Group attribute available on the My Groups page. You must also configure an attribute to be a Group Owner semantic type to use this feature. |
|
Makes the Administrator of Group attribute available on the My Groups page. You must also configure an attribute to be a Group Administrator semantic type to use this feature. |
|
|
Applies to the View Members page. You must configure an attribute to be a Group Static Member semantic type to use the static membership feature. |
|
|
Applies to the View Members page. |
|
|
Applies to the View Members page. You must configure an attribute to be a Group Dynamic Member semantic type to use the dynamic membership feature. |
|
|
Specifies whether or not the user can enter URL parameters to customize the Group Manager display options. Applies to the View Members page and My Groups page. |
Select each option you want to apply to Group Manager.
Click Save.
If you have more than one tab in Organization Manager, you can delete a tab.
From the Identity System Console, click Org. Manager Configuration, the click the Tabs link in the left navigation pane.
Click the link for the tab that you want to delete.
The View Tab page appears. If you have more than one tab defined for Organization Manager, a Delete button appears on this page.
Click Delete.
You are prompted to confirm your decision.
Click OK to delete the tab and all associated information.
You can change the order in which tabs appear in the Organization Manager when there is more than one tab listed.
To order the tabs in the Organization Manager
From the Identity System Console, click Org. Manager Configuration, Tabs.
Click the Order Tabs button at the bottom of the list of tabs.
The Order Tabs page appears listing Tab 1, Tab2, and so on. Beside each tab number is a list that contains the names of existing tabs.
Use the list beside each tab number to specify the order you would like, for example:
Tab 1: Site
Tab 2: Location
Click Save.
A profile page is a Web page that shows information about an object in an Identity System application. For example, when you search for information about a user in the User Manager, a profile page for that user is displayed. The profile page may contain data such as the user's:
Name
Address
Department
Manager
Phone number
The information on a profile page is based on objects and attributes in the LDAP directory that the Identity System communicates with, or it can be based on information in an object template file.
You can assemble profile pages from a collection of panels. For example, the profile page for a person may contain panels for personal, location, and project information. If you have configured an object template file for provisioning purposes, you may want to place the attributes from the template file on one particular panel.
Users can display profile pages in one of two ways:
A panel view organizes the data on the profile page into panels.
A page view organizes the data on the profile page into one long list.
When you configure LDAP attributes on a panel, the attribute labels and values are shown on the profile pages that use the panel. In contrast, template attributes do not actually appear on the profile page. Template attributes only appear on Modify Profile pages, and then only if you have defined a workflow that uses the attributes.See "Sending Non-LDAP Data to External Applications" for details.
The header panel appears at the top of a profile in the User Manager or Organization Manager. The header displays attributes with the semantic types of Full Name, Title, and Photo from the structural object class for the tab. You can turn the header off so that it is hidden from a user identity profile page.Here is a sample header panel for a user:

|
Note: You can configure only LDAP attributes from the structural object class for a tab in header panels. |
From the Identity System Console, click User or Org. Manager Configuration, Tabs.
The Configure Tab page appears. The Organization Manager may have multiple tabs.
Click a tab link, then click the View Object Profile button.
Click Header, which is listed across the top of the page.
The Header Panel page displays the attributes that appear in the Profile header. For example, Map Image, Location Name, Location Title.
Click the Modify button, then select each attribute to appear in the header panel.
If you want to display the Header Panel in user profiles, click Show Header Panel in User Manager.
Click Save.
Panels that you configure in the Identity System Console appear to the user as a collection of attributes on the User Manager, Group Manager, and Organization Manager pages.
The following table shows some examples of panels for a user profile:
Table 4-3 User Profile Panel Attributes
| Panel | Attributes |
|---|---|
|
Telecommunications |
Telephone number Fax number Cellular phone number |
|
Location |
Room Floor number Building number |
|
Personal |
Organization name Type Manager |
Before configuring a panel, be sure the object class for the attribute that you want to place on the panel is configured with the appropriate object class type. See"Object Class Types".
To view a panel in an end user Identity System application
From the User, Group, or Organization Manager, conduct a search for a user, group, or organization object.
Click one of the links returned on the search.
The profile page for that object appears.
If the application displays the profile in a page view, click the View Panels button.
You can create panels using the attributes configured during setup and when you performed the tasks described in "Making Schema Data Available to the Identity System". You can use an attribute once on a panel, and you can usually use the same attribute in more than one panel.
In earlier releases, the challenge phrase and response attributes were allowed on different panels of the User Profile page. In 10g (10.1.4.0.1), however, both the challenge phrase and response attributes must be on the same panel. In 10g (10.1.4.0.1), challenge phrases and responses are displayed one after the other even though these are not configured one after the other in the panel.
If a panel contains only the challenge attribute, it will be displayed in the User Profile page without a response. If the panel contains only the response (without the challenge attribute), the response will not be displayed in User Profile Page.
|
Note: You will probably want to configure one or more LDAP attributes or a combination of LDAP and template attributes on a panel. Since template attributes appear only in the context of workflow execution, a panel that consisted only of template attributes would appear to be empty. |
If you have configured the Identity System for more than one language, you can view or modify the panel fields for each language. You can localize display names for the following panel fields:
Panel Label
Description
Attributes
Mouse Over Message
From in the Identity System Console, click User, Group, or Org. Manager Configuration, then click Tabs.
Click the link to the tab.
The View Tab page appears.
Click View Object Profile.
Click the appropriate button at the top of the page:
For the User Manager and Organization Manager, click Configure Panels.
For the Group Manager, click Configure Group Profile Panels.
The Panels page appears. Currently defined panels are displayed.
Choose an operation:
To add a panel, click Create.
To modify a panel, click a panel link and then click Modify.
To delete a panel, click a panel link and then click Delete.
If you selected Create, the Create Panel page appears.
Edit the fields.
The Modify Panel page is similar to the Create Panel page. In both pages, the following fields are available:
| Label | Description | Label |
|---|---|---|
| Panel Label | A name for this panel in the user application.This name can be localized. | Panel Label |
| Description | Text displayed in the View Panel page.This text can be localized. | Description |
| Attributes | Attributes selected from the lists. If you need additional attribute fields, click Add at the right side of the page. Note that if you select template attributes, the attribute label will not appear on this panel. Template attributes are only displayed in the context of a workflow.These Attributes can be localized. | Attributes |
| Title Image | You can view a user profile as a tab-separated page or as a single page. The Title Image is a GIF image that is used for the panel title when viewing a profile as a single page. The GIF must be stored in WebPass_install_dir/identity/oblix/lang/langTag/style0 where WebPass_install_dir is the directory where you installed WebPass and langTag is the folder that contains the specific language that you are using.Enter the name of the GIF file, not the path. A Title Image can be modified as described in "Configuring Styles for Identity System Applications". | Title Image |
| Tab Image and Tab Image (Bottom) | You can view a user profile as a tab-separated page or as a single page. The Tab Image is a GIF image that is used when viewing a profile as a tab-separated page. The Tab Image usually matches the Panel Label. Until you define a Tab Image, the Panel Label appears as a link on user profile pages. Clicking the link or the Tab Image opens a panel. The (Bottom) version is displayed at the bottom of user profile pages. | Tab Image and Tab Image (Bottom) |
| Depressed Tab Image | The image used when a user clicks a panel tab in a user profile. | Depressed Tab Image |
When this panel is ready for use, select Panel information is complete at the bottom of the page.
Click Save.
|
Note: Checking the box beside ÒPanel information is completeÓ saves the panel definition. However, a user's ability to see the contents of a panel is governed by read permissions. The options are described in "Allowing Users to View and Change LDAP Data". |
To view or modify a panel's configuration
From the Identity System Console, click User, Group, or Org. Manager Configuration.
Click the Tabs link in the left navigation pane.
Click the link for the tab.
The View Tab page appears.
Click the View Object Profile button.
The Profile page appears.
Click Configure Panels at the top of the page.
The appropriate Panels page appears. Links for each of the configured panels are displayed on the page.
Click a panel link to view its details.
Click Modify to display the Modify Panel page.
Modify the information as needed.
Click Save to save your changes.
From the Identity System Console, click User, Group, or Org. Manager Configuration, then click the Tabs link in the left navigation pane.
The existing tabs appear on the page.
Click the link for the tab.
Click the View Object Profile button to display the Profile page.
Click Configure Panels to display links for each of the configured panels.
Click a link to display the View Panel page.
Click Translate.
If the Translate button does not appear, you have only one language installed and you cannot localize the panel. Click Modify to edit display names for panel elements in the one language that you have installed.
If you click Translate, the Summary of Panel Display Names page appears. This page displays all configured language-specific display names for the following fields:
Panel LabelDescriptionAttributesMouse Over Message
Display names that have not been configured are marked Not Configured.
Click Modify to create or modify a display name.
The Panel Display Names page appears. This page contains fields for the panel display names and links for all the installed languages.
Click the language of your choice.
Enter the display name in the appropriate field.
Click Save to save your changes.
Panels appear in a particular order on a profile page. You can change the order in which they appear in the Group Manager.
To change the order in which panels are displayed
From the Identity System Console, click Group Manager Configuration.
Click Group Types, then click the Order Group Type Panels at the top of the page.
|
Note: You can also select User Manager Configuration, Group Manager Configuration, or Organization Manager Configuration then select Tabs, point to link, View Object Profile, and Order Panels. In the Group Manager Configuration, the option at the top of the page is Order Group Profile Panels. |
The Order Panels page appears.
Use the lists beside each panel number to identify the name of the panel to display.
Click Save.
Group Type panels allow you to organize attributes on the My Groups tab. For example, if you have configured groupOfUniqueNames as a structural object class and oblixAdvancedGroup as an auxiliary class, you can organize attributes from these classes on the My Groups tab by creating Group Type panels. Note that Group Type panels are reserved for LDAP attributes. You should not configure template attributes on a Group Type panel. Each object class identified as a Group Type (as described in "Object Class Types" in the Identity System can be associated with a Group Type panel.
In the Identity System Console, click Group Manager Configuration, Group Types, then the Configure Group Type Panels link.
The Panels page displays a list of configured Group Type panels.
Click its link to view a Group Type's settings.
The View Panel page appears showing the settings for the selected panel.
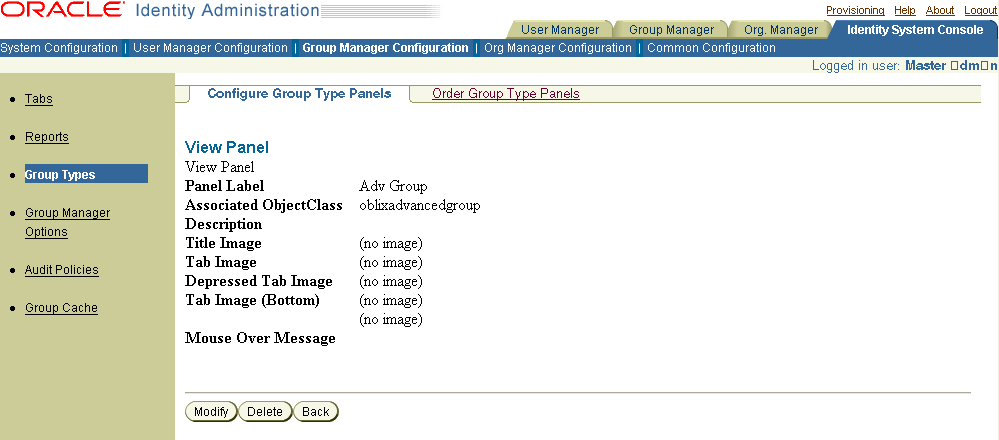
You must configure a Group Type panel to organize the attributes for a group object class. At least one panel should be created for the group structural object class. This enables you to view groups that contain only the group structural object class attributes on the My Groups profile page.If you have installed and configured multiple languages, you can localize display names for the following panel fields:
Panel Label
Description
Mouse Over Message
To add, modify, or delete a Group Type panel
From the Identity System Console, click Group Manager Configuration, Group Types.
The Group Types page displays a list of Group Types.
Click Configure Group Type Panels to display the Panels page.
Choose an operation:
To add a Group Type panel, click Create.
To modify an existing panel, click a panel link and from the View Panel page click Modify.
To delete an existing panel, click a panel link and from the View Panel page click Delete.
In the field labeled Select the Group Type, select the object class to associate with the Group Type.
|
Note: Select only auxiliary object classes that extend the group structural object class or are attached to the group structural object class in the schema. Only configured auxiliary classes can be selected from this page. For more information, see "Adding Object Classes". |
In the remaining fields, enter values as described in "To create or add a panel".
Select the box beside Panel information is complete.
Click Save.
|
Note: Selecting Tab information is complete saves the panel definition, but a user's ability to see the contents of a panel is governed by read permissions, as described in "Allowing Users to View and Change LDAP Data". |
To localize panel display names
In the Identity System Console, click Group Manager Configuration.
Click Configure Group Types in the left navigation pane.
Click Configure Group Type Panels.S
The Panels page displays a list of configured Group Type panels.
Click the panel for which you want to configure display names.
The View Panel page appears.
Click Translate.
This button only appears if you have more than one language installed. If you only have one language installed, click Modify to configure display names for panels elements.
The Summary of Panel Display Names page appears. This page lists all the configured display names for the following fields:
Panel Label
Description
Mouse Over Message
Display names that have not been configured for a particular language are marked as Not Configured.
Click Modify.
The Panel Display Names page appears.
Click the language for which you want to configure display names.
Enter the display names for the panel fields.
Click Save to save your changes.
The attributes you configure through Common Configuration pages are used in each application using that object class. For instance, through common configuration you can set the display name for the cn attribute to be Full Name. This is what appears on a user Profile page. If you then configure the cn attribute to display as Legal Name from the User Manager configuration screen, it is displayed by default as Legal Name on the user Profile page. See "Making Schema Data Available to the Identity System" for details. You can also localize display names of attributes that are displayed on a panel. This enables you to present attributes in the user's native language. See "Configuring Multiple Languages for Oracle Access Manager" for information on managing multiple languages.
|
Note: The only way to change the display type or semantic type of an attribute once it has been assigned to a panel is to delete and then re-create the panel. |
However, as described in the following paragraphs, you can override the information configured for the attribute at the object class level.
Each Identity System application (User, Group, and Org. Manager), provides an application-specific Configuration tab with a Tabs function. Using the application-specific Tabs function, you can provide a different display name or display type for an attribute on that application-specific Configuration tab only (different than what is configured at the object class level). For example, you may have a different display name for the "description" attribute on the User Manager Configuration tab.
For proper localization when you have more than one language installed, when you reconfigure an attribute at the tab level you must provide display names for that attribute in all installed languages. For example, suppose you have two installed languages. To provide translations for the "description" attribute on the User Manager Configuration tab (for example) in both languages, you must specify the display name for the attribute in the installed languages at the same tab level. The Translate button appears only when more than one language is installed.
The following procedures illustrate how to reconfigure an attribute at the tab level to override the information configured for the attribute at the object class level.
To modify attributes specific to the User, Group, or Organization Manager
From the Identity System Console, click the User, Group, or Organization Manager Configuration tab.
Click the Tabs link in the left navigation pane.
The Tab page appears. There may be multiple tabs for the Organization Manager.
Click the link for the tab.
The View Tab page appears.
Click Modify Attributes.
The Modify Attributes page appears.
Details on modifying an attribute are provided in "Configuring Attributes". You can localize attribute display names as described next.
To localize attribute display names
From the Identity System Console, click User, Group, or Organization Manager Configuration.
Click the Tabs link in the left navigation pane.
The Configure Tab page appears. There may be multiple tabs for the Organization Manager.
Click the link for the tab.
The View Tab page appears.
Click Translate.
|
Note: The Translate button appears only if more than one language has been installed. |
The Summary of Attribute Display Names page appears. This page lists all configured attribute display names for all languages. Display names that have not been configured are marked Not Configured.
Click Modify.
The Attribute Display Names page appears. This page lists display name fields for attributes and links for the installed languages.
Click the language for which you want to configure display names.
Enter the name in the Display Name field.
Click Save to save your changes.
You can think of configuring objects and attributes and assembling attributes into panels on application tabs as being like playing with building blocks. Once you have arranged your building blocks, you can determine who is allowed to play with them. You must configure the Identity System to allow people to search for and view the LDAP attributes you have configured on the application panels. To do this, you:
Determine the level of the directory tree that users are permitted to search.
Set View and Modify permissions for specific attributes in the directory tree.
|
Note: The following section discusses setting the searchbase as a method of configuring view and modify permissions. The searchbase refers to searching the LDAP directory tree. Template attributes are not relevant to setting a searchbase. To give users the ability to enter values for template attributes, the users must be participants in a workflow where these attributes are used. See "Chaining Identity Functions Into Workflows" for details. |
A searchbase is a branch in the directory tree, or it can be the top node of the tree. At installation time, you select the default searchbase. The default searchbase is the node in the directory tree under which all user data is stored and the highest possible base for all user data searches.The searchbase determines the part of the directory tree that is available to a user during a search. You must set a searchbase for each structural object class configured for the Identity System before a user can view its entries. You can set multiple searchbases for each structural object class.When you set a searchbase, you determine who can search what (an object class, at a particular level of the directory tree), optionally using a search filter. Before setting a searchbase you need to determine the following:
What object class (users or groups) do I want to set the searchbase for?
Where will the search begin?
Who can search there?
For example, you can configure one searchbase for employees and another for customers to ensure that customers cannot see employee information.
As another example, if two competing suppliers provide you with parts, you can set the searchbase so that users from each supplier can view only their own portion of the DIT.
|
Note: You set the searchbase from the User Manager application. This is the end user application rather than the User Manager Configuration function. You also need to configure read permissions for your group profile pages for the group class. |
When you set a searchbase, you have the option to define a filter to identify what branch of a searchbase a logged-in user can view. If your directory tree is particularly flat, so that selecting a node does little to filter the searchbase, the filter feature helps narrow searches. The filter is also useful if your directory tree has a large number of branches, for instance, if you have 10,000 dealerships, you probably want to narrow down searches within the dealerships.However, a filter can affect performance if it yields a large number of entries. Instead of using a searchbase filter, you can set read permissions for the class attribute, as described in "Selecting a Class Attribute". The class attribute is used for attribute access and to link search results to a Profile page.For example, suppose you remove the resource filter from the searchbase, allowing the role of Anyone to access the person object class. Instead of setting the searchbase, you define read permissions for the class attribute, using a rule to specify who can access this attribute. This can reduce the number of directory searches that the Identity System conducts. See "Setting and Modifying LDAP Attribute Permissions" for details.
|
Note: You can set several searchbases for the same user or group if specific users need to access different parts of the directory tree. For example, if employees need to search both the employee and the customer branches of the tree, you can define searchbases for employees and for customers, and give employees permission to view both. However, be sparing when configuring multiple searchbases for a particular object class. Where possible, define read and write permissions for attributes instead. Multiple searchbases for the same object class can degrade performance. |
If you change the levels being searched in the directory tree or if you change the search attribute, you cannot directly modify a searchbase. If you attempt to do so, the Identity System treats the modified searchbase as a newly defined searchbase. The only way to modify a searchbase is to delete it and create a new one.
|
Note: You can modify a searchbase if the changes are other than those described in this section. |
Searches of the directory are a significant factor in system performance. See the Oracle Access Manager Deployment Guide for guidelines on indexing.
Oracle Internet Directory returns an error when un-indexed attributes are used in a search. For example, suppose that you define a derived attribute using an un-indexed "Match Attribute" and add the attribute to a profile page in Oracle Access Manager. When the page is displayed, Oracle Internet Directory returns an error and no values are displayed for the derived attribute in the profile page. In the Oracle Access Manager log file, an error message "Operation not supported" is logged.
To use additional attributes in search filters, you must add them to the catalog entry. You can index only those attributes that have:
An equality matching rule
Matching rules supported by Oracle Internet Directory as listed in "About LDAP Attribute Matching Rules" in Oracle Identity Management User Reference.
No more than 128 characters in their names.
You can index a new attribute—that is, one for which no data exists in the directory—using the ldapmodify tool. You can index an attribute for which data already exists in the directory by using the Catalog Management tool. You can drop an index from an attribute by using ldapmodify, but Oracle recommends that you use the Catalog Management tool.
Once you have defined a new attribute in the schema, you can add it to the catalog entry by using ldapmodify.
To add an attribute for which no directory data exists, import an LDIF file by using ldapmodify. For example, to add a new attribute foo that has already been defined in the schema, import the following LDIF file to Oracle Internet Directory using ldapmodify:
dn: cn=catalogs changetype: modify add: orclindexedattribute orclindexedattribute: foo
Do not use this method to index an attribute for which data exists in the directory. To index such an attribute, use the Catalog Management tool.
The following procedure describes the steps for setting the searchbase.
In the User Manager application, click the Configuration sub-tab.
The Configuration page appears.
Click Set Searchbase.
On some browsers you may receive a prompt asking if you trust the certificate of the application. If this happens, select the Trust Always option.
The Set Searchbase page appears.
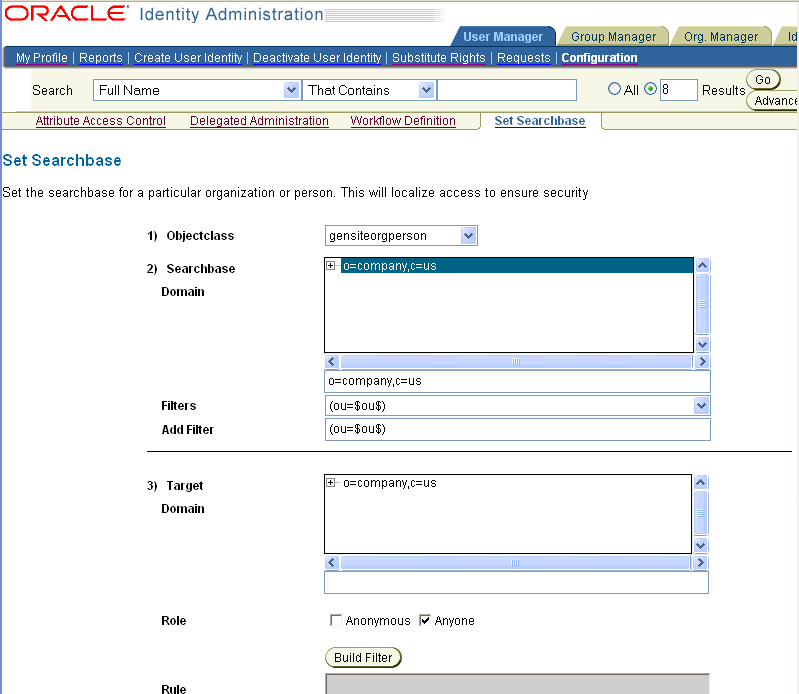
In the Object Class list, select an object class.
The object class you select defines what is being searched. For instance, to set a searchbase for widgets, you would select the widget object class. The Searchbase Domain box indicates the top node for the search. The field beneath the Searchbase Domain box is where you enter or edit information.
In the field under the Searchbase Domain box, specify the part of the directory tree where the search for the object may be conducted.
For instance, if you want to define a searchbase for widgets in the Manufacturing Department, you might select the Manufacturing branch of the searchbase.Selecting the top level of the directory tree indicates that the entire domain is available for searches. You can refine the searchbase by selecting a node further down the tree or by entering a filter. For example, to restrict searches to North America, you could select the top node and enter region=North America as the filter. This example assumes there is a branch called North America in your directory tree. See "Usage of Rules and Filters" for details on writing a filter. The Filters box indicates the current filters for the search. You use the Add Filter field, beneath the Filters box, to enter another filter.
Optional: In the Add Filters field, enter another filter.
Click Save.
The new filter appears in a field under the previous filter.Users and groups permitted to search this portion of the directory tree are defined in the next panel.
Specify the user or group that is permitted to search this portion of the directory tree.
For Example:
Target Domain: Any user object in the tree under the node you select.
Do not use full LDAP URL while specifying the filter for target domain (or workflow domain) while creating the workflow. Only the LDAP filter is expected. For example, cn=Shutterbug Canavan is expected rather than ldap:///ou=Partners,o=Company,c=US??sub?(cn=Shutterbug Canavan).
Role: The role of the users.
If you want to give this right to everyone whether they have logged in or not. select Anonymous. If you want to give this right to anyone who has logged in to the User Manager, Group Manager, or Organization Manager, select Anyone.
|
Note: Anonymous access is used only in the Self Registration function in User Manager and Organization Manager. Also, anonymous access applies only to display type attributes (a check box, radio button, or list) that are configured as a Rule. For example, suppose you configure the ou attribute as a list display type with a rule that uses the LDAP filter (objectclass=organizationalunit). To configure this attribute for self registration, you would access the Organization Manager tab for organizationalUnit, configure attribute access for the class attribute (as described in "Setting and Modifying LDAP Attribute Permissions", and grant Anonymous access. |
Rule: Any person you specify with an LDAP filter. Click Build Filter and use the Query Builder to create a rule. See "Writing LDAP Filters Using Query Builder" for details.
Person(s): Any person you select. Click Select User and use the Selector to choose individuals.
Group(): Any group you select. Click Select Group and use the Selector to choose one or more groups.
To copy users and groups from one searchbase to another, click Copy, click Reset, select another Searchbase Domain and Target Domain, and click Paste. The users and groups appear in their respective boxes.
|
Note: If you specify users by more than one means (for instance, by a rule and by selecting individual users), both methods apply. The only exception is when Anyone is selected. Anyone supersedes all other methods. |
Click one of these buttons to take the appropriate action:
Save: Save and implement changes.
Reset: Clear all selections.
Delete: Clear all rule, group, and user specifications.
Report: Generate a report summarizing the configured searchbases.
You can set the searchbase for the groupOfUniqueNames object class and select the groups for which you are defining the searchbase. Before people in the group can view entries in a searchbase for a group, you need to configure read permissions for your group profile pages for the group class, as described in "Setting and Modifying LDAP Attribute Permissions".
A disjoint searchbase is a searchbase that supplements the one you selected when you set up the Identity System. You create a disjoint searchbase to identify an additional LDAP directory tree under which user data can exist.You can add multiple disjoint searchbases to a domain. The following procedures describe how to add and delete a disjoint searchbase.
For more information on managing disjoint searchbases, see "Working With Multiple Directory Searchbases".
To add a disjoint searchbase for a disjoint domain
From the Identity System Console, click System Configuration, Directory Profiles.
Click the Directory Server link.
Add a disjoint searchbase in the Disjoint Search Base field and click Save.
From the Identity System Console, click User Manager Configuration.
From the left navigation pane, select Tabs.
The Configure Tab page appears.
Select the tab link.
Click Modify.
Make sure there is no value in the Tab Search base field.
Save your changes, if necessary.
To delete a disjoint searchbase
Disable all directory profiles that use this searchbase.
You can view the searchbases that are configured for a directory profile in the Name Space field for the profile. There will be one directory profile for each searchbase in the disjoint domain. See "Creating an LDAP Directory Server Profile""Creating an LDAP Directory Server Profile" and on page 7-33 for details.
Remove all access control policies for the disjoint searchbase.
If there are policies defined for the deleted searchbase, a user who has this searchbase on this node will be able to create a filter using Query Builder whose base is this searchbase.
From the Identity System Console, select System Configuration, then Directory Profiles.
Click the Directory Server link.
Remove the information in the Disjoint_domain field, then click Save.
The Query Builder enables you to write LDAP filters when you perform activities such as setting the searchbase. The Identity System enforces a limit of 20 hits for a query. This applies to both Selector and Query Builder. If you perform a search or query that results in more than 20 hits, you receive truncated results. For instructions on changing the search limit, refer to the cookieBustLimit parameter in the Oracle Access Manager Customization Guide.You access the Query Builder function from the Build Filter button. For example, this function is available when setting a searchbase. See "Setting the Searchbase" for details.
|
Note: If you choose the Is Present or Is Not Present operator when building a query, the value specified for the display type is not taken into consideration, since the filter that is used is a presence filter. |
Click the User Manager application tab.
These are the Identity System applications.
Click the Configuration sub-tab.
Click Set Searchbase.
From the Set Searchbase page, locate and click the Build Filter button.
The Query Builder page appears. By default, the Basic query page is displayed.
In the Attribute list, select an attribute you want to use as search criteria.
For example:
Admin
Click Add.
The attribute is added to the filter.
From the list beside the new attribute, select a matching method.
For example:greater than or equalsThe available methods depend on the attribute. See "Methods for Retrieving Matches" on page 4-28 for details.
In the field beside the method, select or type the query string.
For example:January 22 2003
Click Add to add other attributes.
From the list to the left of the attribute, select the relationship between attributes:
And: Results must match criteria in all rows.
Or: Results can match criteria in one row.
For example, you can search for everyone with the Administrator attribute and a start date after (greater than) January 22, 2003.
Click Test to test your filter.
If too many or too few results are received, make your criteria more or less restrictive.
Click Delete next to an attribute to remove it from the filter (or click Delete All to delete all attributes).
Click Save.
When you Save, the filter appears in the previous page under the Build Filter button.
|
Note: If you receive a Bad Request message when you save, your query string is too long for your browser. Browsers handle the filters as URLs, and they generate an error if the query string exceeds their maximum URL length. |
The matching methods that you can select in the Query Builder depend on the display type of the attribute. For instance, the display type of an attribute may be a list or a set of radio buttons. See "Attribute Display Types" for details. When you use the Query Builder to create a filter for an attribute with a display type that contains multiple values, for example, a list, the query returns a match even if only one value satisfies the filter.
When building a filter, you can select multiple values for an attribute in one row only if the attribute display type is a check box or a radio button.
Table 4-4 lists the matching methods that the Query Builder uses:
Table 4-4 Matching Methods in the Query Builder
| Method | Description |
|---|---|
|
equals |
Results are an exact match of the value. |
|
does not equal |
Results do not include the specified value. |
|
less than or equals |
Results are less than or equal to the specified value. For example, specifying k for a full name query returns people whose name begins with a letter from A to K. |
|
greater than or equals |
Results are greater than or equal to the specified value. For example, specifying k for a full name query returns people whose name begins with a letter from K to Z. |
|
less than |
Returns any directory entry with a value that is less than the specified value. When filtering a text string, a value of less than returns entries that precede the specified value alphabetically. For example, specifying k for a full name query returns people whose name begins with the letters from A to J. |
|
greater than |
Returns any directory entry with a value that is greater than the specified value. When filtering a text string, a value of less than returns entries that follow the specified value alphabetically. For example, specifying k for a full name query returns people whose name begins with the letters from L to Z. |
|
contains |
Returns any directory entry that contains the specified string anywhere in the value of the entry. For example, an entry of st might return values of street or best. |
|
does not contain |
Returns any directory entry that does not contain the specified string anywhere in the value of the entry. |
|
is present |
Returns any directory entry that contains this attribute. For instance, if you select the Administrator attribute and the is present method, all administrators are returned. |
|
is not present |
Returns any directory entry that does not contain this attribute. |
|
begins with |
Returns any directory entry that begins with the specified value. |
|
ends with |
Returns any directory entry that ends with the specified value. |
|
does not begin with |
Returns any directory entry that does not begin with the specified value. |
|
does not end with |
Returns any directory entry that does not end with the specified value. |
|
sounds like |
Results approximate the sound of the specified value. Use this option if you are unsure of the spelling of your desired search object. Use phonetic spelling. For example, specifying kiero might return values for cairo.This option is not supported by Novell Directory Services. |
|
does not sound like |
Results display entries that do not approximate the sound of the specified value. Use your best phonetic spelling.This option is not supported by Novell Directory Services. |
Filters can work on multiple attributes and use logical operators such as And, Or, and Not.
From the Identity System Console, click the tab for the User Manager application.
Click the Configuration sub-tab.
Click Set Searchbase.
Click the Build Filter button.
In the Query Builder page, click the Advanced tab.
If you switch from Basic to Advanced, and you choose OK, you lose the current filter (click Cancel to keep the displayed filter).
The Advanced page appears.
If the Advanced page does not appear after you click the Advanced tab, the URL could be too long. The length of the URL is determined by the browser.
In the Select Attribute list, select the attribute you want to use as the search criteria.
In the associated list select a matching method, and in the associated text entry field add a query string.
See "Writing LDAP Filters Using Query Builder" for details.
Click Add.
The attribute is added to the Constructed Visual Filter box.
You can perform the following optional steps:
To add to your LDAP commands, use the And, Or, or ( ) buttons.
To remove an attribute from the Constructed Visual Filter box, select it, and click Delete (or Delete All to remove all attributes).
To modify an entry in the Constructed Visual Filter box:
Select the entry.Make your changes to the query characteristics at the top of the page.Click Modify.
Click Show LDAP Filter to view the filter you are building.
The LDAP string displays in the LDAP Filter box. You can edit the text in this box and click Update Visual Filter. For examples of LDAP filters, see "Static LDAP Search Filters" and "Examples of Dynamic LDAP Search Filters".If you manually enter a very complex filter, the Constructed Visual Filter box may not be able to interpret it correctly. However, the filter will work correctly.
Click Test to view the results of your query.
the Identity System displays output that conforms to your filter.
Click Save to save and apply your filter.
If you receive a "Bad request" message when you click Save, your query string is too long for your browser. Browsers handle the filters as URLs, and they generate an error if the query string exceeds their maximum URL length.
Until you configure permissions for an attribute, no users can see attributes displayed in the User Manager, Group Manager, and Organization Manager. For example you can allow all users to view employee work phone numbers in the User Manager, but allow only managers to view home phone numbers. If you are a Master Identity Administrator or a delegated administrator with appropriate permissions, you can configure user permissions. By default, Master Administrators specified during Identity Server installation have full access to all attributes. You can change the default by setting the BypassAccessControlForDirAdmin parameter to false in:
IdentityServer_install_dir/identity/oblix/apps/common/bin
The Attribute Access Control function lets you specify permissions that determine who can read and modify the values for each LDAP attribute. It also lets you create a list of users or groups to be notified when an attribute is changed. As with setting the searchbase, this functionality only applies to LDAP attributes. You configure permissions for template objects when you add participants to workflow steps. See "Chaining Identity Functions Into Workflows" for details.Users must have a searchbase defined as well as read permissions to be able to view an attribute. For instance, to be able to view the class attribute on the User Manger, Group Manager, or Organization Manager tab, a user must be a trustee of the appropriate searchbase domain for the class attribute, and they must have read permissions for this attribute.
To set or modify attribute permissions
In User, Group, or Organization Manager, click Configuration at the top of the page.
The Configuration page appears.
Click Attribute Access Control.
If you receive a prompt asking if you trust the certificate of the application, select the Trust Always option.
The Attribute Access Control page appears.
In the Management Domain box, specify the scope of the Directory Information Tree (DIT) that this permission applies to.
Initially, this field displays the searchbase set during product setup. This searchbase can only be changed by performing setup again. Selecting a lower level in the tree applies access control for that branch. For example, if you select the Full Name attribute, and then select a lower level department such as Sales, you are applying access control to all of the people in Sales with Full Name in their profile.
Optional—Use the Filters field to enter an LDAP rule to specify the objects and attributes more precisely.
A filter refines the attributes you are allowed to read or modify. If you do not use a filter, the Identity System uses objectclass=*.
|
Note: A filter is useful if your database design is particularly flat or has a particularly large number of branches. |
Add the Filter in the Add Filter field. Once the configuration is saved, the filter is added to the Filters list. If you later want a different filter, you must delete the original searchbase and create a new configuration. For more information on filters, see "Usage of Rules and Filters".
Specify the Right:
Read—Selected users can view the attribute and its value on a profile page.
Modify—Selected users can change the attribute value. Note that you must confer read permissions for these users to be able to see the attribute value.
Notify—Sends an email to the specified users when an attribute value is changed.
For example, you can give read and modify permissions to the Title attribute for a manager. Then you can set notification to be sent to the HR department when the value for this attribute is modified in a user profile. For details about email post-notification for a self registration step, see "Descriptions of Step Actions".
In the Attribute box, select the attribute to associate with this right.
If you want to make multiple selections, see "Keys for Selecting Multiple Attributes".
|
Note: If an attribute in your multi-select range has a different set of trustees, an error appears. This prevents you from inadvertently allowing access to incorrect trustees (participants). |
Confer this right to one or more of the following:
Role: Assigns the right based on the user's role. Any attribute with a data type of DN and a display type of Object Selector appears in the Role area. Self and Anonymous are shipped with the Identity System. Each application contains different roles, largely dependent on your configured attributes. For example, the User Manager may have the Manager role, but not any role based on the secretary attribute, depending on your configuration. Common roles include the following:
| Role | Description |
|---|---|
| Anyone | All users who log in to the User, Group, or Organization Manager can either view or modify the attribute at the selected level. For example, all logged-in users can view the phone number attribute at the specified level in the directory. |
| Anonymous | All users can view entries, whether they are logged in or not. Anonymous access is only used for self-registration. |
| Self | The user logged into the User Manager application can view or modify the attribute for his or her own identity, assuming the read and write permissions for attributes is high enough on the directory tree to include the user's profile. For example, if you select Self to be able to view the Name attribute at the top level, then you, as a person logged into the User, Group, or Organization Manager, are able to view your name. But if you specify ou=Marketing as the level on the directory tree, and the user is not in Marketing, then you cannot view your name. |
| Manager | The user logged in to the User Manager application can either view or modify the attribute for their direct reports. |
| Secretary | If the user logged in to the User Manager is an administrative assistant, he or she can view or modify the attribute for the people they support. |
| Group Owner | The user logged in to the Group Manager can view or modify the attribute for the group that he or she is an owner of. |
| Group Administrator | The user logged in to the Group Manager can view or modify the attribute for the group that he or she administers. |
| Group Member | The user logged in to the Group Manager can view or modify the attribute for the group that he or she is a member of. |
Rule: Click Build Filter and use the Query Builder to create a rule. See "Writing LDAP Filters Using Query Builder" for details.
Person(s): Click Select User and use the Selector to specify one or more users.
Group(s): Click Select Group and use the Selector to specify one or more groups.See "Evaluation of LDAP Attribute Permissions" for information on the order for evaluating permissions.
Click Copy, click Reset, select a new attribute, and click Paste to copy users and groups from one attribute to another.
Click one of these buttons:
Save: Save and implement your changes.
Reset: Clear all selections.
Delete: Clear all rule, role, group, and user specifications.
Report: Generate a report of attributes and their access permissions in the domain.
You can configure access control for multiple attributes at one time using the following keyboard combinations:
Ctrl + Home: Selects all attributes above and including the highlighted attribute.
Ctrl + End: Selects all attributes following and including the highlighted attribute.
Ctrl + Page Up: Selects only attributes above the highlighted attribute.
Ctrl + Page Down: Selects only attributes following the highlighted attribute.
|
Note: If an attribute in your multi-select range has a different set of trustees (participants), you receive an error. This prevents you from granting access to incorrect trustees. |
Platform-specific key combinations are as follows:
| Browser Type | Function |
|---|---|
| Windows Browsers |
|
| Unix Browsers |
|
When you assign multiple methods for view and modify permissions, the Identity System evaluates the methods in this order:
Users
Roles
Groups
Rules (LDAP filters)
When the Identity System finds a match, it stops checking. For example, suppose you grant read permission for the Name attribute for User=Lou Reed, but you also have a rule that says (&(!(cn=Lou Reed)) objectclass=person object class), which allows everyone except Lou Reed. Lou Reed has access because he is a User, which precedes Rule in the evaluation order. As another example, if you specified a rule denying access to the Human Resources department but used the people selector to specify an individual employee in Human Resources, the union of the rule and people categories would allow access to the specified employee.
|
Note: If you select the Anyone role, all users, roles, groups, and filters are superseded. |
The following sections describe different scenarios for configuring an application. Separate examples are provided for the User Manager, Group Manager, and Organization Manger.
Photos appear in the header panel of a user profile. Users with self-service permissions on relevant attributes can manage their own photos.
There are two ways you can store photos in the Identity System:
In an LDAP directory
Referencing photos in a file system.
You cannot use both methods. All of your photos must be stored in either a directory or a file system.
When you want to store your photos or other images in a directory, place the photos on the Identity Server and use the Identity System to import the photos into the directory and to configure an attribute to be the photo attribute. You can create your own attribute, or you can use an attribute that already exists. This attribute must be defined as a binary type in your directory, and in the Identity System the attribute must be defined as a Photo semantic type with a GIF display type. The GIF display type supports GIF and JPEG formats, and other image file formats that are supported by your Web server. Before associating a photo with a user's identity, be sure the photo's file name is based on the value of the attribute with the Login semantic type. For example, if your Login semantic type is assigned to the uid attribute, you would use the following file name conventions:
attribute_value_of_uid.giforattribute_value_of_uid.jpgorattribute_value_of_uid.jpeg
If your login semantic type is something other than uid, use that instead for your file name. For example, if the Login semantic type is assigned to the email attribute, your photo file names must be the following:
attribute_value_of_mail.giforattribute_value_of_mail.jpgorattribute_value_of_mail.jpeg
The file extension must be compatible with a graphic file format that your Web servers can support.
When the Identity System imports photos and images, it converts the files into Base64 format. This data becomes the value of the Photo attribute. the Identity System uses the Login attribute and the photo or image file name to determine which photo belongs to which user entry.Steps for configuring the Identity System to use the photos are described in the following discussions.
To configure photos for importing to a directory
From the Identity System Console, click Common Configuration, then click Object Classes.
Select your person object class from the list.
Click Modify Attributes.
Modify the Photo attribute as follows:
Attribute: Photo
DisplayName: Photo
Semantic Type: Photo
Data Type: Binary
Attribute Value: This is always a single value attribute
Display Type: GIF Image
Save your changes.
In the User Manager, under Attribute Access Controls, assign Read and Write permissions to this attribute.
To import photos to the directory
From the Identity System Console, click System Configuration, and click Photos.
Specify the path to the photos stored on the Identity Server.
Click Save.
This imports all of the GIF and JPEG images into your directory.
Another method for storing images and photos for user identities is to store the photos in a location other than the directory. This method is appropriate for GIF and JPEG images, and other image file formats that are supported by your Web server. The Identity Server's WebPass must be able to access this location. You can name the photo or image file using any valid file name that the Web server recognizes and supports. Avoid using special characters such as spaces in the file name. The Web server may not recognize file names that use special characters.
To reference photos that reside in a file system
In the Identity System Console, click Common Configuration, Object Classes.
Click the person object class in the Object Class list.
Click Modify Attributes.
Modify the Photo Path attribute as follows:
Attribute: Photo Path
DisplayName: Photo
Semantic Type: Photo
Data Type: String (case-sensitive)
Attribute Value(s): Single or multi-valued
Display Type: GIF image URL
Assign read and write permissions for this attribute.
Store the images in GIF or JPEG format in the following directory:
WebPass_install_dir/identity/oblix/lan/langTag/style0
where WebPass_install_dir is the directory where WebPass is installed and langTag is the folder that contains the specific language you are using.
Enter the photo location URL in the User Profile Page for each user.
For example, if the image location is:
c:\COREid\WebComponent\identity\oblix\apps\lang\en-us\style0\user1.gif
you set the photo location to:
user1.gif
More than one GIF image can be displayed by setting the photo URL attribute to be multi-valued.
the Identity System provides a Location tab by default in the Organization Manager. This tab enables you to create maps and associate users or objects with locations on those maps.
Task overview: Enabling Location functionality
The Master Identity Administrator modifies the Location tab and adds location attributes to Profile pages for the User and Organization Manager applications.
The Master Identity Administrator configures access controls for location attributes.
The Master Identity Administrator or Delegated Identity Administrator configures workflows for creating a location. See "Chaining Identity Functions Into Workflows" for details.
The Delegated Identity Administrator creates a new location and establishes the location's hierarchy in relation to other locations, if applicable.
The Delegated Identity Administrator or user assigns a value for the location attribute for a user or object profile.
Any user with appropriate permissions can now view the user or object location.
You assign users the right to create a group when you define a Create Group workflow. Only users designated as participants in the workflow can create the group. See "Chaining Identity Functions Into Workflows" for information about creating workflows.A user can be assigned the right to modify a group type if the user is a participant in a Create Group workflow for that group type. The user must also have write access for the group type attribute. See "Adding Auxiliary and Template Object Classes to a Group Tab" for information about group types. Also see "Setting and Modifying LDAP Attribute Permissions" for information about assigning the modify right to the Group Type attribute. If you run the Identity System with multiple Active Directory instances and use a dynamic filter to create a group, the filter attribute must be a multi-value attribute.
If you run the Identity System with the NDS directory, the users you select as members of the group are cleared from the page when you click Save. To prevent this from happening, go into the NDS directory and switch the order of the attributes so uniquemember is read first. Also make sure the userCertificate attribute comes before the NDS userCertificate;binary attribute.
The following sections describe how an end user interacts with the Group Manager application once it has been configured:
You can view and manage group members from the Group Profile page if the Master Identity Administrator selected a group-member attribute to display on the group profile page. See "Configuring Tab Profile Pages and Panels" for more information. If your group contains a large list of members, this can negatively impact system performance. The Master Identity Administrator can choose not to display group members on the Group Profile page. See "Configuring Group Manager Tab Options".
|
Note: You can also view and manage group members from the Manage Group Members page. When managing large static groups, Oracle recommends using the Manage Group Members page because it is optimized to manage groups with 1000 or more members. This will significantly improve performance when managing large groups (as opposed to defining the member semantic attribute as part of the Group Profile page). |
The Manage Group Members page enables you to view the members of a group based on criteria that you provide. This page shows tables for:
Static members
Dynamic members
Nested members
Search results are subject to searchbase and attribute access controls configured for the Group and User Manager applications. See "Setting and Modifying LDAP Attribute Permissions" for details. If a user does not have read access to the dynamic member attribute for a group, nothing appears in the dynamic member table and the following error message is shown, "You don't have read access for a dynamic member." In the nested members table, if the group contains dynamic nested groups and the user does not have read access to the dynamic member attribute for some of the nested groups, the dynamic members are not shown. In this case, no error message is displayed.
In the Identity System Console, click the Group Manager tab.
In the Search field at the top of the page, enter search criteria.
Click Go. A list of groups appears.
Click the link for the name of the group that you want to view.
In the Group Manager, click My Group.
Conduct a search on groups and click the desired link.
The group profile appears.
Click Manage Group Members.
Select the Member Type you are searching for in this group:
Select People to search for users. Search results can include static, nested, and dynamic users.
Select Groups to search for groups. Search results can include static and dynamic nested groups.
From the Search Members By list, select an attribute as the basis for the search.
Select a search operator.
Enter search criteria.
Click Go.
The Manage Group Members page displays two levels of nested groups and their members in the search results. This includes a child nested group, its members, and its children.
You can delete group members displayed in the search results from the Manage Group Members page. You can only delete static members. You cannot delete dynamic or nested members.
Search for group members from the Manage Group Members page.
From the results that are returned on the search, click the link for the user or group that you want to delete.
Click Save on the Manage Group Members page.
You can add members to a group.
Go to the Manage Group Members page, as described in "Searching for Group Members".
From the Manage Group Members page, click the Select Member button beside the Members To Add field.
The Selector page appears. See "The Selector" for details.
From the Selector page:
If you want to add users to this group, select the person member type.
If you want to add nested groups to this group, select the group member type.
Click Add for each member you want to add.
Click Done.
Click Save on the Manage Group Members page.
The Group Manager provides the ability for users to subscribe and unsubscribe to groups. Only groups configured as Advanced Groups can include a subscription policy. The oblixAdvancedGroup is provided by the Identity System to give you attributes that you might need when working with groups. Table 4-5 shows the contents of oblixAdvancedGroup:
Table 4-5 Contents of oblixAdvancedGroup
| Attribute | Characteristics |
|---|---|
|
obGroupAdministrator |
Display Name: Group Administrator Semantic Type: Group Administrator Display Type: Object Selector |
|
obGroupDynamicFilter |
Display Name: Dynamic Filter Semantic Type: Group Dynamic Member Display Type: Filter Builder |
|
obGroupExpandedDynamic |
Display Name: Group Expansion Semantic Type: None Display Type: Radio Buttons Comment: This attribute is used for expanded dynamic groups. |
|
obGroupPureDynamic |
Display Name: Dynamic Members Only Semantic Type: None Display Type: Radio Buttons Comment: This attribute indicates whether the group is purely a dynamic group. It affects subscriptions. |
|
obGroupSimplifiedAccess Control |
Display Name: Group Access Semantic Type: None Display Type: Radio Buttons Comment: This attribute is used for creating a group workflow. It controls the simplified access control feature. |
|
obGroupSubscribeMessage |
Display Name: Subscription Message Semantic Type: None Display Type: Multi-Line Text Comment: This attribute is used for subscription notification. |
|
obGroupSubscribe Notification |
Display Name: Notification Semantic Type: None Display Type: Check Box Comment: This attribute is used for subscription notification. |
|
obGroupSubscriptionFilter |
Display Name: Subscription Filter Semantic Type: None Display Type: Filter Builder Comment: This attribute is used for group subscriptions using a filter. |
|
obGroupSubscriptionType |
Display Name: Subscription Policy Semantic Type: None Display Type: Selection Menu Comment: This attribute is used for group subscriptions. |
|
obGroupUnsubscribe Message |
Display Name: Unsubscription Message Semantic Type: None Display Type: Multi-Line Text |
There are three ways a user can subscribe to a group, assuming the Master Identity Administrator configured a group subscription policy for that group:
From the Group Profile page in Group Manager
This enables users to subscribe to the selected group displayed in the profile.
As the last step of a Create User workflow
Users can subscribe to multiple groups during the last step of a create user workflow. See "Chaining Identity Functions Into Workflows" for more information.
From the Manage Subscriptions page in Group Manager
This enables users to subscribe to multiple groups from the Manage Subscriptions page.
From the Identity System Console, click the Group Manager tab.
Conduct a search for groups using the search bar.
Click the link for the group to which you want to subscribe.
Click Subscribe.
To subscribe to multiple groups
From the Group Manager application, click Manage Subscriptions.
Conduct a search for groups using the search bar.
In the Groups for Subscription page, check the box next to each group to which you want to subscribe.
Click Save Subscriptions at the bottom of the Manage Subscriptions page.
A list of groups to which you are subscribed appears. This includes:
All groups with an open subscription policy.All groups with filter subscription policy, and you satisfy the filter criteria.All groups controlled through a workflow subscription policy where you are a participant in the initiating step of the change-attribute workflow that applies to these groups.
You can capture information about user actions performed in each Identity application. Captured information is stored as audits of Identity System events. You configure auditing policies for each application. These settings determine the data that is captured in an audit file. You configure where audit files are written for each Identity Server. For information about changing the audit file path, see "Managing Identity Servers".
You can view auditing policies from each Identity System application.
In the Identity System Console, click User, Group, or Org. Manager Configuration, then click Audit Policies.
The Application Auditing Policy page appears, displaying the following information:
| Item | Description |
|---|---|
| Profile Attributes | Appears only if they have been configured for this application. |
| Event Name | the Identity System operation being audited |
| Application Auditing Enabled | Indicates whether or not auditing is enabled for this event |
| Audit Success | Indicates whether or not event successes are audited |
| Audit Failure | Indicates whether or not event failures are audited |
If you have appropriate permissions, you can change any auditing policy that you can view. These settings do not overlap with the Global Auditing Policies feature found in the Identity System Console, Common Configuration, Global Auditing Policies. -- needs clarification
To set or modify auditing policies
In the Identity System Console, click User, Group, or Organization Manager Configuration, Audit Policies.
Click Modify.
The Modify Auditing Policy page appears.
In the Profile Attributes lists, select the attributes that can trigger events you want to audit.
In the Application Auditing Enabled column, select each event you want to enable for auditing.
In the Audit Success and Audit Failure columns, select each event you want to audit.
For example, you can audit every Modify Location event, but audit only View Profile failures.
Click Save.
You return to the previous page.
Reports enable you to view information about an object class. Reports provide an alternative to searches and enable you to report on attributes that are not available from a search.
Master Identity Administrators must define a report from the Identity System Console before users can view the report in the User Manager application.For example, after configuring an Employees tab for User Manager, as described in "Viewing and Modifying Tab Configuration Information", you can create reports listing employees in a specific building, employees with specific job titles, or employees in a particular department.
The report functionality uses QueryBuilder to enable you to define complex search criteria that are not possible using a basic search. This provides richer support for searching on various types of attributes that a basic search does not allow.There are two types of reports:
Ad-hoc Reports: Created by end users in the User Manager, Group Manager, and Org. Manager applications. In this case, the Query Builder includes searchable attributes configured in the tab along with other supported display types (see the note).
Pre-defined Reports: Created by an administrator from the System Console. In this case, the Query Builder includes all attributes (whether they are marked as searchable in the tab or not) for all supported display types.
|
Note: The Query Builder supports building filters on attributes with the following display types: Single line text, Multi-line text, Radio, Select list, Checkbox, Boolean, Date, Mail address, Telephone number, Selector, Postal address and Numeric String. |
From the Identity System Console, click User Manager Configuration, Reports, then click List Reports.
The following page appears the first time you create a report.
Click Add to display the Query Builder on the Configure Reports page.
Select the first Attribute for the basis of your report criteria, then click Add.
In the field beside the attribute, select the appropriate method.
Enter the report criteria.
The format of this criteria depends on the attribute display type.
Repeat steps 3-6 for any additional attributes you want added to this report.
|
Note: When you select more than one attribute for a report, you must select whether this is an And or an Or operation. See the sample page in this procedure. |
Click Test to verify that the report generates data correctly.
A verification page appears.
Click Save.
A page like the following one appears. Several buttons become available and are highlighted in the following screen shot. These will be used in the next procedure.
Click Next to see additional report results, or click Publish to save the report.
To change the formatting of a report
From the Reports page, click Customize to customize the report column headings.
Customize the column names in the form that appears, then click Save.
Click the Publish button.
Enter a Name and an optional description for this report.
Click Save to make this report available in the User Manager application, under the Reports tab.
Viewing reports is subject to access control and searchbase settings.
You can display a report's name and description in more than one language if you install the appropriate language packs and configure them for those languages. See "Configuring Multiple Languages for Oracle Access Manager" for more information.
When you export a generated report in an Identity System application and the values contain non-ASCII characters, you must rename the file with a .txt extension. It will pass through Excel's Import Wizard and non-ASCII characters will display properly.
Note that .csv files opened in OpenOffice will pass through the Import Wizard. In this application, encoding can be chosen without renaming the file to *.txt.
From the Identity System Console, click User Manager Configuration, then click Reports.
Select the type of report you want to view or modify from the list.
Click List Reports.
Select the link to the report you wish to view.
Click the Customize button to change the report criteria.
Click Save to save the new report format.
See "Configuring Reports" for more information on publishing reports for others to view.
From Identity System Console, click User Manager Configuration, then click Reports.
Click List Reports.
All existing reports are listed on the page.
Click the report that you want to localize.
The report details appear on the page.
Click Publish.
The Publish Report page appears. This page contains the links for all the installed languages.
Click the language in which you want to publish the report.
In the Report Name field, enter a display name in the selected language.
In the Report Description field, enter a brief description of the report.
This information is optional.
Click Save to save your changes.
The reports are displayed in the User Manager.
From Identity System Console, click User Manager Configuration, then click Reports.
Select the tab that contains the report you want to delete.
Click List Reports.
Select the (-) icon next to the report name to delete it.
The following sections describe expanding dynamic groups, limiting the scope of a directory search, and editing an XML file to configure attribute permissions.
If a group's membership is determined by an LDAP filter, you can generate a static membership list by expanding the group. Generating a static list saves the Identity System from having to run the LDAP filter with every group access. Group expansion updates the static list by running the LDAP rule that specifies dynamic membership, then storing the results in the static member attribute. Many Identity System functions test a group for membership. Since testing static membership is faster than testing dynamic membership, it is preferable to find a member in a static list. Also, third-party applications may only be able to check static membership. Frequent expansion keeps static membership accurate for third-party applications.The group expansion operation itself is an expensive process. However, you can expand a group as a background process so the impact is hidden from users.
|
Note: If you have static members in a dynamic group and you expand the group, the original list of static members is overwritten with the members who currently satisfy the filter criteria. This is true even if you have set the flag for dynamic members only to false. The filter overrides other group settings. |
Before a user can expand a group, two conditions must be met:
The obgroupexpandeddynamic attribute must be set to true.
The person expanding the group must have Read permission for two attributes, obgroupexpandeddynamic and obgroupdynamicfilter. The user also must have Write permission for the attribute assigned the Group Static Member semantic type.
See the table in "Managing Group Subscriptions" for a breakdown of the Identity System-supplied group attributes.
In Group Manager, click the Configuration option at the top of the page.
The Configuration page appears.
Click Expand Dynamic Groups.
The Expand Dynamic Group page appears.
Select one of these options:
Select By Group and click Select Group to choose one or more groups
Select All to expand all groups
Click Expand.
The Expanded Groups page displays a list of all groups that have been expanded.
Click the group link to display the Group Profile page for that group.
Click Done.
Some portions of the Identity System call out to external XML files to get configuration information. The globalparams.xml file is one such file. This file controls search scope among other things.By default, the search scope is set to subtree for the Identity System, meaning that the search begins at the starting point of the searchbase and includes its children. Depending on the size of your directory, you may want to change the default search scope using the ResourceFilterSearchScope parameter. The possible values for this parameter are:
1: Search the top node of the searchbase and the first level under it.
2: Start at the top node of the searchbase and proceed to the bottom node.
Figure 4-1 shows that setting ResourceFilterSearchScope to 1 could limit results to just a few returned entries, while setting it to 2 could return thousands of entries.
To set the globalparams.xml file
Locate the globalparams.xml file in the following directory:
IdentityServer_install_dir/identity/oblix/apps/common/bin
Back up the file.
Open the file in an ASCII editor (for instance, Notepad) or an XML editor.
Find the ResourceFilterSearchScope parameter and change the value.
Restart WebPass and the Identity Server.
Simplified attribute permissions lets a group creator select Read, Write, and Notify permissions without having to set permissions for each attribute as described under "Setting and Modifying LDAP Attribute Permissions". Simplified permissions are applied to newly created groups where the management domain of the policies is the DN of the new group. Later, these policies can be modified through the access control feature.
An administrator can configure as many sets of simplified permissions as needed. The administrator creates permissions in the IdentityServer_install_dir/oblix/apps/groupservcenter/bin/gscaclparams.xml file. This file contains embedded compound lists to define the roles, users, and groups the model applies to, the rights assigned, and the attributes to which the rights apply. When this file is applied to a new group, an access control entry is created for each right in the file.
The following is a sample set of permissions within a gscaclparams.xml file. The model name is Public:
In entry 1, the role is ob_any, the right is read, and the attributes are description, uniquemember, and owner.
In entry 2, the role is owner, the right is write, and the attributes are description, uniquemember, and owner.
Example 4-1
<?xml version="1.0"?><ParamsCtlg xmlns="http(s)://www.oblix.com" CtlgName="gscaclparams"><!--#----------------------------------------------------><!-- # Access Control Functions --><!--#----------------------------------------------------><!--#----------------------------------------------------><!-- # Public access --><!--#----------------------------------------------------><CompoundList ListName=""><CompoundList ListName="Public"><CompoundList ListName="entry1"><ValList ListName="roles" > <ValListMember Value="ob_any"></ValList><ValList ListName="rights" > <ValListMember Value="READ" Operation="Add"/></ValList> <ValList ListName="attributes" > <ValListMember Value="description"/> <ValListMember Value="cn"/> <ValListMember Value="uniquemember"/> <ValListMember Value="owner"/></ValList> </CompoundList><CompoundList ListName="entry2"><ValList ListName="roles" > <ValListMember Value="owner" Operation="Add"/></ValList><ValList ListName="rights" > <ValListMember Value="WRITE" Operation="Add"/></ValList> <ValList ListName="attributes" > <ValListMember Value="description" Operation="Add"/> <ValListMember Value="cn" Operation="Add"/> <ValListMember Value="uniquemember" Operation="Add"/> <ValListMember Value="owner" Operation="Add"/></ValList></CompoundList>
The following table summarizes the reserved words for simplified permissions.
| Reserved Word | When Used | Description |
|---|---|---|
| rights | Once for an entry | Specifies the right: read, modify, or notify. |
| attributes | Once for an entry | List that specifies the attributes. Any group object attribute can be added to the list. |
| roles | Once for an entry | Roles to which entry applies. Roles can be any pre-defined role, such as uniquemember, owner, ob_any, or ob_anonymous. |
| people | Once for an entry | Specifies the distinguished names to which this entry applies. |
| source | Once for a model | Specifies the base uid of the users who will see this model. If a base uid is not specified, everyone can see this entry. |
| target | Once for a model | Specifies the base uid of the target where this model applies. If the group is not part of this base, the rights cannot be set. |
Use the Container Limits function to control the number of objects and child objects for an organizational unit and its object classes. You can define who receives notifications when the limit is about to be exceeded. For example, you can have organizational units in your directory tree that you use for storing extranet customers. You can limit to 10,000 the number of customers with access to your extranet portal.
|
Note: The Container Limits feature counts the number of objects from the directory. If the number of objects is very large, performance can be affected. |
To view and add container limits
From the Identity System Console, click the Org. Manager tab, then click Configuration, then click Container Limits.
The Container Limits page appears.
In this example, the Current Count table on this page indicates that the gensiteOrgPerson object class has 9 children stored at the current level of the DIT and 718 total children at or under this level.
In the Management Domain box, select a DIT entry you want to view.
The Current Count box displays all configured structural classes associated with the entry and the number of their children.
The Objectclass table displays the container limit, enforcement, and notification policies for the selected DIT entry, listed according to object class.
Select an object class and click Add to add a container limit, in the Objectclass list.
A second Container Limits page appears showing the Management Domain and Object class you selected in the previous screen.
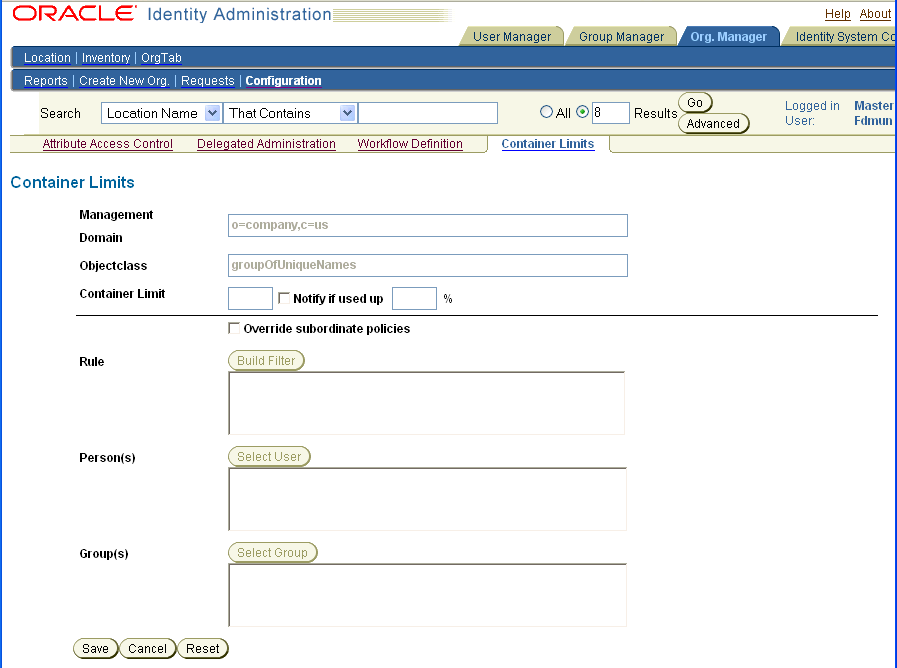
In the Container Limit box, specify the maximum number of children this object class can contain at this DIT level.
When you want to notify someone by email that your object class is nearing its container limit, select Notify if used up, and specify the limit percentage when you want the email sent.
Select Override subordinate policies to create a container limit that cannot be overridden by a lower policy on the DIT.
Use one or more of the following to specify the persons to receive container limit warnings:
Select Build Filter, then use the Query Builder to create a rule.
Click Select User, then use the Selector to specify one or more users.
Click Select Group, then use the Selector to specify one or more groups.
The Users, Roles, and Rules fields have an or relationship. Users specified in any of the fields are notified.
Click Save to save your container limit and add it to the Objectclass table.
You can copy container limits from one domain to another.
To copy container limits from one domain to another
From the Organization Manager, click Configuration, then click Container Limits.
The Container Limit screen appears (as shown on
In the Management Domain box, select the directory information tree (DIT) entry you want to view.
The Current Count box displays the structural classes associated with the entry and the number of their children.
The table Add Container Limit to Objectclass displays the container limit, enforcement, and notification policies for the currently selected DIT entry, listed according to object class.
Click Copy.
In the Management Domain box, locate the destination entry where you want to add the container limits.
Click Paste.
The container limit policies are added to the selected DIT entry.
You can change container limits. See "Setting Container Limits in Organization Manager".
In the Organization Manager, click Configuration.
The Configuration screen appears.
Click Container Limits.
The Container Limits screen appears.
In the Management Domain box, select the DIT entry you want to view.
The Current Count box displays all configured structural classes associated with the entry and the number of their children.
In the Add Container Limit to Objectclass panel, select an object class from the Objectclass column.
Click Modify.
The second Container Limits screen appears.
Make your changes.
See "Setting Container Limits in Organization Manager" for information about these fields.
Click Save.
You can delete a container limit.
In the Organization Manager, click Configuration, then click Container Limits.
In the Management Domain box, select a directory information tree (DIT) entry.
The Current Count box displays all configured structural classes associated with the entry and the number of their children.
In the Add Container Limit to Objectclass panel, select an object class.
Click Delete.
The object class container limit is deleted.
|
Note: Click Delete All to delete all container limits for a DIT entry. |